ECE 4400:427/527 - Computer Networks Spring 2012
... Basic Elements of Network Divided into two main categories: ...
... Basic Elements of Network Divided into two main categories: ...
NetBIOS name resolution
... The ZoneID option specifies the scope or zone of the destination for the ICMPv6 Echo Request messages. For link-local addresses, the zone identifier (ID) is typically equal to the interface index, as displayed in the output of the netsh interface ipv6 show interface command. For site-local addresses ...
... The ZoneID option specifies the scope or zone of the destination for the ICMPv6 Echo Request messages. For link-local addresses, the zone identifier (ID) is typically equal to the interface index, as displayed in the output of the netsh interface ipv6 show interface command. For site-local addresses ...
M.Tech - Telecommunication Networks
... Threats of a Network - Limitations of Mobile Environment - Mobility and Security - Attacks in Mobile Environment - Security Issues in Mobile Environment Overview of IEEE 802.11, Brief History, Architecture & layers - Security of IEEE 802.11; 4.2.1 Bluetooth Overview - Architecture and Components - S ...
... Threats of a Network - Limitations of Mobile Environment - Mobility and Security - Attacks in Mobile Environment - Security Issues in Mobile Environment Overview of IEEE 802.11, Brief History, Architecture & layers - Security of IEEE 802.11; 4.2.1 Bluetooth Overview - Architecture and Components - S ...
Chapter 1. Introduction to Data Communications
... voice and data traffic over WANs. It is also used in backbone networks. • In the WAN, ATM almost always uses SONET as its hardware layer. In backbones, ATM is often implemented as a standalone protocol. • On order to interconnect with the TCP/IP world, an ATM gateway is used that converts TCP/IP and ...
... voice and data traffic over WANs. It is also used in backbone networks. • In the WAN, ATM almost always uses SONET as its hardware layer. In backbones, ATM is often implemented as a standalone protocol. • On order to interconnect with the TCP/IP world, an ATM gateway is used that converts TCP/IP and ...
Slide 1
... – By running stress tests on the client machine. • Use a single method CPU intensive task • Use UI thread to do intensive DOM manipulations and run a few web workers for CPU intensive tasks in the background • Calculate CPU clock speed and the number of processors ...
... – By running stress tests on the client machine. • Use a single method CPU intensive task • Use UI thread to do intensive DOM manipulations and run a few web workers for CPU intensive tasks in the background • Calculate CPU clock speed and the number of processors ...
Printed_Networks and Protocols CE00997-3 WEEK 6..
... WiMAX Vs WiFi •WiMAX is a long-range system, covering many kilometers that typically uses licensed spectrum (although it is also possible to use unlicensed spectrum) to deliver a point-topoint connection to the Internet from an ISP to an end user. Different 802.16 standards provide different types ...
... WiMAX Vs WiFi •WiMAX is a long-range system, covering many kilometers that typically uses licensed spectrum (although it is also possible to use unlicensed spectrum) to deliver a point-topoint connection to the Internet from an ISP to an end user. Different 802.16 standards provide different types ...
MPLS networking at PSP Co Multi
... • Needed a single infrastructure that supports multitude of applications in a secure manner • Provide a highly scalable mechanism that was topology driven rather than flow driven • Load balance traffic to utilize network bandwidth efficiently • Allow core routers/networking devices to switch packets ...
... • Needed a single infrastructure that supports multitude of applications in a secure manner • Provide a highly scalable mechanism that was topology driven rather than flow driven • Load balance traffic to utilize network bandwidth efficiently • Allow core routers/networking devices to switch packets ...
Introduction to Computer Networking
... problem: how can you initialize both A and B such that the communication can take place. One solution is to manually start A, then B, but this defeats the purpose of networking. The only way we have found so far is to request that one of the two, say B, is started and immediately puts itself in a li ...
... problem: how can you initialize both A and B such that the communication can take place. One solution is to manually start A, then B, but this defeats the purpose of networking. The only way we have found so far is to request that one of the two, say B, is started and immediately puts itself in a li ...
InfiniBand
... » remove all possible down link following up links in each node » find one output port for each destination – Other solutions: destination renaming ...
... » remove all possible down link following up links in each node » find one output port for each destination – Other solutions: destination renaming ...
A Decentralized Recommendation System Based on Self
... on top of Gnutella, which connect users sharing at least m common files, and proving that they show small world topologies; (2) a practical recommendation scheme is proposed to the file sharing community, that takes advantage of the high clustering coefficient of the previously introduced Preference ...
... on top of Gnutella, which connect users sharing at least m common files, and proving that they show small world topologies; (2) a practical recommendation scheme is proposed to the file sharing community, that takes advantage of the high clustering coefficient of the previously introduced Preference ...
PDF
... Broadcast protocols, of which P5 is a scalable variant, are the only other approach that offer comparable or stronger anonymity guarantees, but even P5 has never been implemented, partly because of the performance limitations and resource consumption of constant broadcast. The Herbivore prototype de ...
... Broadcast protocols, of which P5 is a scalable variant, are the only other approach that offer comparable or stronger anonymity guarantees, but even P5 has never been implemented, partly because of the performance limitations and resource consumption of constant broadcast. The Herbivore prototype de ...
Unit 3- Mobile Network layer
... Firewalls at the foreign network may not allow that Multicasting: if a MN is to participate in a multicast group, it needs to use a reverse tunnel to maintain its association with the home network. TTL: a MN might have a TTL that is suitable for communication when it is in its HM. This TTL may n ...
... Firewalls at the foreign network may not allow that Multicasting: if a MN is to participate in a multicast group, it needs to use a reverse tunnel to maintain its association with the home network. TTL: a MN might have a TTL that is suitable for communication when it is in its HM. This TTL may n ...
The Basics of Application Monitoring
... road goes where. In general, routes can be categorized as: 1. Learned routes - learned from receiving routing information from other routers and applying that information to the routing protocol. 2. Local segments - The router knows these because the network or subnet is directly connected to the ro ...
... road goes where. In general, routes can be categorized as: 1. Learned routes - learned from receiving routing information from other routers and applying that information to the routing protocol. 2. Local segments - The router knows these because the network or subnet is directly connected to the ro ...
Chapter 8 Internet Protocols
... • Need unique address for each device interface on network —MAC address on IEEE 802 network and ATM host address —Enables network to route data units through network and deliver to intended system —Network attachment point address ...
... • Need unique address for each device interface on network —MAC address on IEEE 802 network and ATM host address —Enables network to route data units through network and deliver to intended system —Network attachment point address ...
3rd Edition: Chapter 4
... Input Port Queuing r Fabric slower than input ports combined -> queueing ...
... Input Port Queuing r Fabric slower than input ports combined -> queueing ...
dhs-aug2006 - Princeton University
... – Easy to inject false information – Easy to trigger routing instability ...
... – Easy to inject false information – Easy to trigger routing instability ...
N:Y - The ACIS Lab - University of Florida
... router LSUGrid users – DoS attacks, viruses router ...
... router LSUGrid users – DoS attacks, viruses router ...
Carrier
... Management, security and scalability reasons. Layer3 between VLANs 4094 available VLANs not enough for an SP! Transparency problem within the SP backbone network! A failure in the customer’s domain still affects the spanning-tree of the provider’s core (transport) network ...
... Management, security and scalability reasons. Layer3 between VLANs 4094 available VLANs not enough for an SP! Transparency problem within the SP backbone network! A failure in the customer’s domain still affects the spanning-tree of the provider’s core (transport) network ...
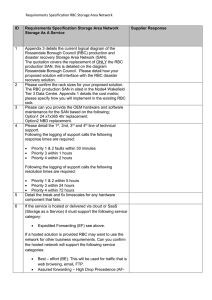
Appendix 2. Requirements Specification RBC Storage Area Network
... onsite engineer support. Covering activities such as manual reboots to any devices or typing in specific commands in order to deal with any priority 1 issues where the Telephony is down. This support will include the continuous monitoring of all network communications infrastructure including SIPS, ...
... onsite engineer support. Covering activities such as manual reboots to any devices or typing in specific commands in order to deal with any priority 1 issues where the Telephony is down. This support will include the continuous monitoring of all network communications infrastructure including SIPS, ...
Networks
... Implements an internet protocol (i.e., set of rules) that governs how hosts and routers should cooperate when they transfer data from network to network. ...
... Implements an internet protocol (i.e., set of rules) that governs how hosts and routers should cooperate when they transfer data from network to network. ...
Lecture12
... Virtual circuits Cross between circuit and packet switching Resources are reserved to a logical connection, but are not dedicated to the connection Fixed path between peers for the duration of the connection ...
... Virtual circuits Cross between circuit and packet switching Resources are reserved to a logical connection, but are not dedicated to the connection Fixed path between peers for the duration of the connection ...