H3C SR8800 10G Core Routers
... H3C SR8800 10G Core Routers (hereinafter referred to as the SR8800) are developed by Hangzhou H3C Technologies Co., Ltd., based on its thorough research and deep understanding of user needs. The SR8800 can be widely deployed at IP backbone networks, metropolitan area networks (MANs) and the core and ...
... H3C SR8800 10G Core Routers (hereinafter referred to as the SR8800) are developed by Hangzhou H3C Technologies Co., Ltd., based on its thorough research and deep understanding of user needs. The SR8800 can be widely deployed at IP backbone networks, metropolitan area networks (MANs) and the core and ...
3rd Edition, Chapter 5
... sharing a broadcast channel: multiple access link layer addressing instantiation and implementation of various link ...
... sharing a broadcast channel: multiple access link layer addressing instantiation and implementation of various link ...
tutorial7
... • After the router computed the tree it finds its place in the tree and decides about next targets for packet sending • To prevent repeated generation of the same tree, the results of the computations are saved in the Forwarding Cache, including: source address, multicast group, upstream and downstr ...
... • After the router computed the tree it finds its place in the tree and decides about next targets for packet sending • To prevent repeated generation of the same tree, the results of the computations are saved in the Forwarding Cache, including: source address, multicast group, upstream and downstr ...
Samantha - SSI Robotics
... • The newer Samantha units work the same as the older units. The connectors seem to be a bit more rugged. • CAUTION – If you are loading new network information (re-flashing the unit). Do not attempt to only change the encryption type for a network. The Samantha does not seem to correctly update if ...
... • The newer Samantha units work the same as the older units. The connectors seem to be a bit more rugged. • CAUTION – If you are loading new network information (re-flashing the unit). Do not attempt to only change the encryption type for a network. The Samantha does not seem to correctly update if ...
AFDX for Airplanes
... AFDX is the main avionics databus network onboard the A380 and is based on commercial 10/100-Mbit, full duplex switched Ethernet. It uses a special protocol providing deterministic timing and redundancy management which ensures secure and reliable communication of critical and noncritical data. AFDX ...
... AFDX is the main avionics databus network onboard the A380 and is based on commercial 10/100-Mbit, full duplex switched Ethernet. It uses a special protocol providing deterministic timing and redundancy management which ensures secure and reliable communication of critical and noncritical data. AFDX ...
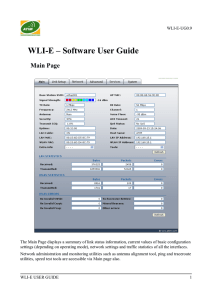
WLI-E – Software User Guide
... Transmit CCQ: This is an index of which evaluates the wireless Client Connection Quality. It takes into account transmit errors, latency, and throughput while evaluating the ratio of successfully transmitted packets against the re-transmitted ones and taking into account current rate ratio against t ...
... Transmit CCQ: This is an index of which evaluates the wireless Client Connection Quality. It takes into account transmit errors, latency, and throughput while evaluating the ratio of successfully transmitted packets against the re-transmitted ones and taking into account current rate ratio against t ...
Understanding Network Access Control
... using this method if no directory or RADIUS framework is available. The advantage is clearly the out-of-band management, compatible with all SNMP devices, but this compatibility is also one of the main problems. Many vendors deliver imprecise or faulty information via SNMP where a correct outcome ca ...
... using this method if no directory or RADIUS framework is available. The advantage is clearly the out-of-band management, compatible with all SNMP devices, but this compatibility is also one of the main problems. Many vendors deliver imprecise or faulty information via SNMP where a correct outcome ca ...
Internetworking Between ZigBee/802.15.4 and IPv6/802.3 Network
... It is operative not only between ZigBee/802.15.4 and IPv6/802.3 but also multiple ZigBee/802.15.4 networks connected by IPv6/802.3 networks. ...
... It is operative not only between ZigBee/802.15.4 and IPv6/802.3 but also multiple ZigBee/802.15.4 networks connected by IPv6/802.3 networks. ...
Chapter 4 Lecture Presentation
... When http request arrives, think of it as as a data-plane packet with an implicit signaling call setup request If web proxy's secondary NIC (into the circuitswitched) network is tied up in circuits to other web proxy servers distinct from the one identified as best parent for this request, call is e ...
... When http request arrives, think of it as as a data-plane packet with an implicit signaling call setup request If web proxy's secondary NIC (into the circuitswitched) network is tied up in circuits to other web proxy servers distinct from the one identified as best parent for this request, call is e ...
Transport Control Protocol
... Data is collected from the stream (and stored into memory), until a certain amount has been obtained This data is packaged into one or more network packets (e.g. IP datagrams) and sent to the destination using connectionless delivery The destination should send an acknowledgement back to the source ...
... Data is collected from the stream (and stored into memory), until a certain amount has been obtained This data is packaged into one or more network packets (e.g. IP datagrams) and sent to the destination using connectionless delivery The destination should send an acknowledgement back to the source ...
subnetting - WordPress.com
... it specifies a broadcast that is sent to all hosts on the network. 140.179.255.255 specifies the example broadcast address. ...
... it specifies a broadcast that is sent to all hosts on the network. 140.179.255.255 specifies the example broadcast address. ...
Chapter 3: Internetworking - ¡Bienvenido a paloalto.unileon.es!
... bridge checks to see if the new message is better than the current best configuration message recorded for that port ...
... bridge checks to see if the new message is better than the current best configuration message recorded for that port ...
Congestion Control Outline: Queuing Discipline
... • How to fairly allocate resources (link bandwidths and switch buffers) among users. • Two sides of the same coin: – Resource allocation so as to avoid congestion (difficult with any precision) – Congestion control if (and when) it occurs ...
... • How to fairly allocate resources (link bandwidths and switch buffers) among users. • Two sides of the same coin: – Resource allocation so as to avoid congestion (difficult with any precision) – Congestion control if (and when) it occurs ...
More on the IP
... – Routers cannot store decision rules for reaching each address individually – So router simply asks if a destination IP address is that of a host on one one of the networks or subnets connected to the router or must be passed on to another router – This is the router forwarding decision ...
... – Routers cannot store decision rules for reaching each address individually – So router simply asks if a destination IP address is that of a host on one one of the networks or subnets connected to the router or must be passed on to another router – This is the router forwarding decision ...
RT-WiFi: Real-Time High Speed Communication Protocol for
... actuators in a control systems. For instance, a communication protocol is required to support an aggregate 2KHz sampling rate for a control system with one sensor and one actuator, if both of them demands 1KHz sampling rate. For supporting a wide range of control applications, the design of RT-WiFi ...
... actuators in a control systems. For instance, a communication protocol is required to support an aggregate 2KHz sampling rate for a control system with one sensor and one actuator, if both of them demands 1KHz sampling rate. For supporting a wide range of control applications, the design of RT-WiFi ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... directly, if they are in other’s wireless links radio range. In order to enable data transfer they either communicate through single hop or through multiple hops with the help of intermediate nodes. Since MANETs allow ubiquitous service access, anywhere, anytime without any fixed infrastructure they ...
... directly, if they are in other’s wireless links radio range. In order to enable data transfer they either communicate through single hop or through multiple hops with the help of intermediate nodes. Since MANETs allow ubiquitous service access, anywhere, anytime without any fixed infrastructure they ...
GPSDTN: Predictive Velocity-Enabled Delay-Tolerant
... greater than 40,000 km resulting in delays of approximately one quarter of a second of round-trip travel time (RTT) [11]. Long cables, routers, switches and signal processing can increase this delay. These delays are significant because standard TCP/IP [12,13] does not perform well over highlatency ...
... greater than 40,000 km resulting in delays of approximately one quarter of a second of round-trip travel time (RTT) [11]. Long cables, routers, switches and signal processing can increase this delay. These delays are significant because standard TCP/IP [12,13] does not perform well over highlatency ...
6420A_11
... VPN Protocol Point-to-Point Tunneling Protocol (PPTP) Layer 2 Tunneling Protocol (L2TP) Secure Socket Tunneling Protocol (SSTP) ...
... VPN Protocol Point-to-Point Tunneling Protocol (PPTP) Layer 2 Tunneling Protocol (L2TP) Secure Socket Tunneling Protocol (SSTP) ...
CS335 Networking & Network Administration
... tightly integrated with IP. ICMP messages, delivered in IP packets, are used for out-of-band messages related to network operation or misoperation. Of course, since ICMP uses IP, ICMP packet delivery is unreliable, so hosts can't count on receiving ICMP packets for any network problem. Some of ICMP' ...
... tightly integrated with IP. ICMP messages, delivered in IP packets, are used for out-of-band messages related to network operation or misoperation. Of course, since ICMP uses IP, ICMP packet delivery is unreliable, so hosts can't count on receiving ICMP packets for any network problem. Some of ICMP' ...
Network Access Security – It`s Broke, Now What?
... Client Broker "Middleware" that runs on the client and talks to the Posture Collectors, collecting their data, and passing it down to Network Access Requestor. In product form, this is generally bundled with the Network Access Requestor. ...
... Client Broker "Middleware" that runs on the client and talks to the Posture Collectors, collecting their data, and passing it down to Network Access Requestor. In product form, this is generally bundled with the Network Access Requestor. ...
NetworkingTheory
... › Ports from 0-1023 (inclusively) are reserved for well-known applications, so root or administrator access is required to run an program on a port in that range › Ports from 1024-49151 (inclusively) are registered ports and can be used by any application › Ports from 49152-65535 are dynamic or priv ...
... › Ports from 0-1023 (inclusively) are reserved for well-known applications, so root or administrator access is required to run an program on a port in that range › Ports from 1024-49151 (inclusively) are registered ports and can be used by any application › Ports from 49152-65535 are dynamic or priv ...
Networking Theory
... › Ports from 0-1023 (inclusively) are reserved for well-known applications, so root or administrator access is required to run an program on a port in that range › Ports from 1024-49151 (inclusively) are registered ports and can be used by any application › Ports from 49152-65535 are dynamic or priv ...
... › Ports from 0-1023 (inclusively) are reserved for well-known applications, so root or administrator access is required to run an program on a port in that range › Ports from 1024-49151 (inclusively) are registered ports and can be used by any application › Ports from 49152-65535 are dynamic or priv ...