Performance Evaluation and Comparison of Facsimile Transmission
... network using the FoIP (Fax over IP) gateways [11]. The sending device segments the data into individual packets. Each packet is independent and has unique identifier. The packets may use different routes to reach the destination. So the individual packets that are part of the same transmission may ...
... network using the FoIP (Fax over IP) gateways [11]. The sending device segments the data into individual packets. Each packet is independent and has unique identifier. The packets may use different routes to reach the destination. So the individual packets that are part of the same transmission may ...
Chapter 8: Advanced Routing Protocols
... – Allow EIGRP to discover neighbors and keep track of their status – EIGRP must be able to keep updates bounded, sent only to those peers that need the information – EIGRP must build a neighbor table of directly connected peers CCNA Guide to Cisco Networking Fundamentals, Fourth Edition ...
... – Allow EIGRP to discover neighbors and keep track of their status – EIGRP must be able to keep updates bounded, sent only to those peers that need the information – EIGRP must build a neighbor table of directly connected peers CCNA Guide to Cisco Networking Fundamentals, Fourth Edition ...
wireless mesh networks
... ETX of a link is the expected number of transmissions before a packet is successfully delivered on a link For a route, the ETX is the sum of the ETXs on all links Captures the link quality and packet loss on both directions of a link The route ETX can detect interference among links of the s ...
... ETX of a link is the expected number of transmissions before a packet is successfully delivered on a link For a route, the ETX is the sum of the ETXs on all links Captures the link quality and packet loss on both directions of a link The route ETX can detect interference among links of the s ...
ATF_Best Practice Design for an Avaya Fabric Connect Campus
... No visible effect to users – even while link was bouncing for 21/2 hours Simply disabled link over weekend until optic could be changed the next Monday Proved during cutover that even with a VSP 7000 failing, the alternate switch and path would work to maintain the network VSP 7000 that was ...
... No visible effect to users – even while link was bouncing for 21/2 hours Simply disabled link over weekend until optic could be changed the next Monday Proved during cutover that even with a VSP 7000 failing, the alternate switch and path would work to maintain the network VSP 7000 that was ...
TCP
... – Unlike TCP and UDP, it offers new delivery options that are particularly desirable for telephony signaling and multimedia applications ...
... – Unlike TCP and UDP, it offers new delivery options that are particularly desirable for telephony signaling and multimedia applications ...
SonicWALL TZ 170 Getting Started Guide Page 7
... not display, verify the following configurations: • Did you correctly enter the SonicWALL TZ 170 management IP address, 192.168.168.168, in your Web browser? • Is your computer running pop-up blocking software? • Are the Local Area Connection settings on your computer set to obtain an IP address dyn ...
... not display, verify the following configurations: • Did you correctly enter the SonicWALL TZ 170 management IP address, 192.168.168.168, in your Web browser? • Is your computer running pop-up blocking software? • Are the Local Area Connection settings on your computer set to obtain an IP address dyn ...
Attack of Slammer worm - A practical case study - Pen Test
... • Shared infrastructure and independency • Insecure third party connection • Weak IP management. ...
... • Shared infrastructure and independency • Insecure third party connection • Weak IP management. ...
DSL-G624T Wireless ADSL Router User Guide
... will be stored in its memory. For some users, only their account information (Username and Password) is required. For others, various parameters that control and define the Internet connection will be required. You can print out the two pages below and use the tables to list this information. This w ...
... will be stored in its memory. For some users, only their account information (Username and Password) is required. For others, various parameters that control and define the Internet connection will be required. You can print out the two pages below and use the tables to list this information. This w ...
Chromecast Deployment Guide, Release 7.6 Introduction
... Multicast applications, such as Chromecast, require special consideration when being deployed over a wireless network because a multicast in 802.11 is sent out as a broadcast so that all clients can hear it. The actual data rate used by the AP in order to transmit the Chromecast frames is the highes ...
... Multicast applications, such as Chromecast, require special consideration when being deployed over a wireless network because a multicast in 802.11 is sent out as a broadcast so that all clients can hear it. The actual data rate used by the AP in order to transmit the Chromecast frames is the highes ...
D23 - Report on Integrated Test Scenarios
... The Monitoring and Measurement Cluster MOME has contacted a lot of research projects in Europe, which have some activities related to it. One of the interfaces of the Monitoring and Measurement MOME Cluster to IST projects is through the MOME Database, which is accessible through the MOME Web page. ...
... The Monitoring and Measurement Cluster MOME has contacted a lot of research projects in Europe, which have some activities related to it. One of the interfaces of the Monitoring and Measurement MOME Cluster to IST projects is through the MOME Database, which is accessible through the MOME Web page. ...
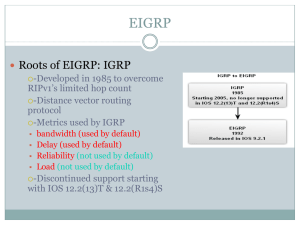
EIGRP
... • The IP-EIGRP module is responsible for sending and receiving EIGRP packets that are encapsulated in IP and for using DUAL to build and maintain the IP routing table. • The IPX EIGRP module is responsible for exchanging routing information about IPX networks with other IPX EIGRP routers. • Apple-Ta ...
... • The IP-EIGRP module is responsible for sending and receiving EIGRP packets that are encapsulated in IP and for using DUAL to build and maintain the IP routing table. • The IPX EIGRP module is responsible for exchanging routing information about IPX networks with other IPX EIGRP routers. • Apple-Ta ...
Cost_Calculation
... • Distributed RAN architecture saves backhaul cost (less than half of the cost of existing architecture ) • Distributed RAN architecture supports 99.999% service-level availability compared to conventional network. In fact, full mesh is not required for realizing the 99.999% availability. Even parti ...
... • Distributed RAN architecture saves backhaul cost (less than half of the cost of existing architecture ) • Distributed RAN architecture supports 99.999% service-level availability compared to conventional network. In fact, full mesh is not required for realizing the 99.999% availability. Even parti ...
PlanetSeer: Internet Path Failure Monitoring and Characterization in Wide-Area Services
... such as BGP [16], OSPF [15] and IS-IS [12] update messages to identify inter-domain and intra-domain routing failures. This approach usually requires collecting routing updates from multiple vantage points, which may not be easily accessible for normal end users. Other researchers have relied on som ...
... such as BGP [16], OSPF [15] and IS-IS [12] update messages to identify inter-domain and intra-domain routing failures. This approach usually requires collecting routing updates from multiple vantage points, which may not be easily accessible for normal end users. Other researchers have relied on som ...
Gnutella2: A Better Gnutella?
... nodes on the path to it) must be forwarded the request! • The reach is determined by n (# connections to other hosts) and TTL (# hops each request is permitted to ...
... nodes on the path to it) must be forwarded the request! • The reach is determined by n (# connections to other hosts) and TTL (# hops each request is permitted to ...
BACnet Router FS-ROUTER-BAC
... solution for BACnet/IP, BACnet Ethernet, and BACnet MS/TP networks. This is the first standalone BACnet Router that has been certified by BTL to ensure the highest standard for BACnet integration. The FieldServer BACnet Router is available in two models: The FS-ROUTER-BAC has two RS-485 ports enab ...
... solution for BACnet/IP, BACnet Ethernet, and BACnet MS/TP networks. This is the first standalone BACnet Router that has been certified by BTL to ensure the highest standard for BACnet integration. The FieldServer BACnet Router is available in two models: The FS-ROUTER-BAC has two RS-485 ports enab ...
Data types
... For each computer with another address, a member of the own network (computer or router) must be found that can send the data into the right direction • This is sometimes wrong • Understanding of network addresses becomes important ...
... For each computer with another address, a member of the own network (computer or router) must be found that can send the data into the right direction • This is sometimes wrong • Understanding of network addresses becomes important ...
Impact of Delay in Voice over IP Services
... The IP Network delay is generally the round trip delay for an IP packet within the IP network. This may be measured using tools such as “ping” or protocols such as RTCP. It is important to note that some IP networks treat the RTP packets used to transport voice with higher priority than other packet ...
... The IP Network delay is generally the round trip delay for an IP packet within the IP network. This may be measured using tools such as “ping” or protocols such as RTCP. It is important to note that some IP networks treat the RTP packets used to transport voice with higher priority than other packet ...
Communications Server for z/OS V1R2 TCP/IP
... When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. © Copyright International Business Machines Corporation 2002. All rights reserved. Note to U.S Government Users - Doc ...
... When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. © Copyright International Business Machines Corporation 2002. All rights reserved. Note to U.S Government Users - Doc ...
TCP operations
... acknowledged by receiver within given time. Thus sending TCP must keep the sent data in memory until it has received the acknowledgements of sent data. TCP assumes that IP is inherently unreliable, so TCP adds services to ensure end-toend delivery of data. TCP has very few expectations on the servic ...
... acknowledged by receiver within given time. Thus sending TCP must keep the sent data in memory until it has received the acknowledgements of sent data. TCP assumes that IP is inherently unreliable, so TCP adds services to ensure end-toend delivery of data. TCP has very few expectations on the servic ...
Performance Evaluation of a QoS-Aware Handover Mechanism Steffen Sroka , Holger Karl
... are possible over a wireless channel). Providing such guarantees using IP-based networks is still a challenging task: Much research has been done on QoS in fixed IP networks, but how to support QoS guarantees in a mobile IP network is not clear; even the precise notion of such a requirement is not e ...
... are possible over a wireless channel). Providing such guarantees using IP-based networks is still a challenging task: Much research has been done on QoS in fixed IP networks, but how to support QoS guarantees in a mobile IP network is not clear; even the precise notion of such a requirement is not e ...
Cisco Inter-network Operating System (IOS) A short guide for the
... 4. The "Operating System Image" is loaded into RAM. (Random Access Memory) 5. The "Configuration File" saved in NVRAM is loaded into the RAM. The Configuration File is then executed one line at a time. 6. If no "Configuration File" is found in NVRAM, the Cisco IOS will offer you the chance to use th ...
... 4. The "Operating System Image" is loaded into RAM. (Random Access Memory) 5. The "Configuration File" saved in NVRAM is loaded into the RAM. The Configuration File is then executed one line at a time. 6. If no "Configuration File" is found in NVRAM, the Cisco IOS will offer you the chance to use th ...