Avaya External Template 31607
... • Back-to-back user agent (B2BUA) - A call-control device that provides routing similar to a proxy server, but allows centralized control of the network call flows; this device allows SIP networks to replicate certain traditional telephony services that require centralized knowledge of device state, ...
... • Back-to-back user agent (B2BUA) - A call-control device that provides routing similar to a proxy server, but allows centralized control of the network call flows; this device allows SIP networks to replicate certain traditional telephony services that require centralized knowledge of device state, ...
PDF - Complete Book (2.17 MB)
... The following information is for FCC compliance of Class A devices: This equipment has been tested and found to comply with the limits for a Class A digital device, pursuant to part 15 of the FCC rules. These limits are designed to provide reasonable protection against harmful interference when the ...
... The following information is for FCC compliance of Class A devices: This equipment has been tested and found to comply with the limits for a Class A digital device, pursuant to part 15 of the FCC rules. These limits are designed to provide reasonable protection against harmful interference when the ...
Lenovo RackSwitch G8124-E Application Guide
... Note: Before using this information and the product it supports, read the general information in the Safety information and Environmental Notices and User Guide documents on the Lenovo Documentation CD and the Warranty Information document that comes with the product. ...
... Note: Before using this information and the product it supports, read the general information in the Safety information and Environmental Notices and User Guide documents on the Lenovo Documentation CD and the Warranty Information document that comes with the product. ...
PDF - Complete Book (3.07 MB)
... • A Cisco Virtual Security Gateway (VSG) zone-based firewall to control and monitor segmentation policies within the networks. • A server load balancer (SLB) to scale up the application capacity. A Cisco prime Network Services Controller (PNSC) that defines and monitors the zone policies. A PNSC can ...
... • A Cisco Virtual Security Gateway (VSG) zone-based firewall to control and monitor segmentation policies within the networks. • A server load balancer (SLB) to scale up the application capacity. A Cisco prime Network Services Controller (PNSC) that defines and monitors the zone policies. A PNSC can ...
NGN_internship
... Diallog), and others as they put and help me to choose the next coming future of Next Generation Network (NGN). I am very thankful to Engineer Mr.Muhammad Yameen (IN PTCL), who solve my problems by giving brief concepts on SS7. I greatly appreciate the help provided by Engineer Mr. Muhammad Hanif Ja ...
... Diallog), and others as they put and help me to choose the next coming future of Next Generation Network (NGN). I am very thankful to Engineer Mr.Muhammad Yameen (IN PTCL), who solve my problems by giving brief concepts on SS7. I greatly appreciate the help provided by Engineer Mr. Muhammad Hanif Ja ...
Fit AP networking
... management, customers are advised to purchase wireless access controllers (ACs) to perform centralized management on the APs and set the APs to work as Fit APs. ...
... management, customers are advised to purchase wireless access controllers (ACs) to perform centralized management on the APs and set the APs to work as Fit APs. ...
User Guide V3.0
... provides all the information that you need to configure and set up the CoreBuilder® 9000 ATM Enterprise Switch in ATM networking environments. It also provides information about how the CoreBuilder 9000 ATM Enterprise Switch operates in an ATM network. This guide is intended for the system administr ...
... provides all the information that you need to configure and set up the CoreBuilder® 9000 ATM Enterprise Switch in ATM networking environments. It also provides information about how the CoreBuilder 9000 ATM Enterprise Switch operates in an ATM network. This guide is intended for the system administr ...
Thwarting E-mail Spam Laundering - Computer Science
... to be used as spam proxies to pump out e-mail spam. Without serious performance degradation, most nonprofessional Windows users are not aware of the ongoing spamming. Recent research on the network-level behavior of spammers [Ramachandran and Feamster 2006] also confirms that most sinked spam is ori ...
... to be used as spam proxies to pump out e-mail spam. Without serious performance degradation, most nonprofessional Windows users are not aware of the ongoing spamming. Recent research on the network-level behavior of spammers [Ramachandran and Feamster 2006] also confirms that most sinked spam is ori ...
Cloud and Network Services
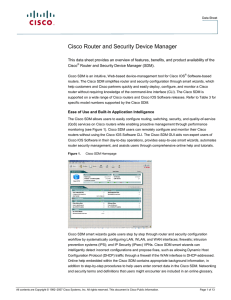
... (PPP), and High-Level Data Link Control (HDLC) encapsulation. Cisco SDM also allows configuration of static routing and common dynamic routing protocols such as Open Shortest Path First (OSPF), Routing Information Protocol (RIP) Version 2, and Enhanced Interior Gateway ...
... (PPP), and High-Level Data Link Control (HDLC) encapsulation. Cisco SDM also allows configuration of static routing and common dynamic routing protocols such as Open Shortest Path First (OSPF), Routing Information Protocol (RIP) Version 2, and Enhanced Interior Gateway ...
SelfTest.70-640.925Questions
... universal group can contain users from otherdomains, and it can be applied to access control lists (ACLs) on objects in all domains in the forest. Therefore,universal group memberships must be ascertained at domain logon so that the user has appropriate access inthe domain and in other domains durin ...
... universal group can contain users from otherdomains, and it can be applied to access control lists (ACLs) on objects in all domains in the forest. Therefore,universal group memberships must be ascertained at domain logon so that the user has appropriate access inthe domain and in other domains durin ...
Brocade ICX 7450 Switch Data Sheet
... and scalability required for enterprise Gigabit Ethernet (GbE) access deployment. It offers market-leading stacking density with up to 12 switches (576 1 GbE and 48 1/10 GbE ports) per stack and combines chassis-level performance and reliability with the flexibility, costeffectiveness, and “pay as y ...
... and scalability required for enterprise Gigabit Ethernet (GbE) access deployment. It offers market-leading stacking density with up to 12 switches (576 1 GbE and 48 1/10 GbE ports) per stack and combines chassis-level performance and reliability with the flexibility, costeffectiveness, and “pay as y ...
ATOS 6.1.12
... dest host [max 128 char] Ip address or name of the destination host (only if a DNS is configured in the device). ...
... dest host [max 128 char] Ip address or name of the destination host (only if a DNS is configured in the device). ...
Brocade 5600 vRouter LAN Interfaces Reference Guide, v3.5R6
... Communications Systems, Inc., in the United States and/or in other countries. Other brands, products, or service names mentioned may be trademarks of others. Notice: This document is for informational purposes only and does not set forth any warranty, expressed or implied, concerning any equipment, ...
... Communications Systems, Inc., in the United States and/or in other countries. Other brands, products, or service names mentioned may be trademarks of others. Notice: This document is for informational purposes only and does not set forth any warranty, expressed or implied, concerning any equipment, ...
PDF - Complete Book (655.0 KB)
... Configuration Guides, Command References, and Supplementary Resources Table 1 lists, in alphabetical order, Cisco IOS and Cisco IOS XE software configuration guides and command references, including brief descriptions of the contents of the documents. The Cisco IOS command references are comprehensi ...
... Configuration Guides, Command References, and Supplementary Resources Table 1 lists, in alphabetical order, Cisco IOS and Cisco IOS XE software configuration guides and command references, including brief descriptions of the contents of the documents. The Cisco IOS command references are comprehensi ...
view pdf - Christoph Sommer and Falko Dressler: Vehicular
... ▪ These slides are designed to accompany a lecture based on the textbook “Vehicular Networking” by Christoph Sommer and Falko Dressler, published in December 2014 by Cambridge University Press. ▪ Except where otherwise noted (e.g., logos and cited works) this slide deck is Copyright © 2009‐2015 C ...
... ▪ These slides are designed to accompany a lecture based on the textbook “Vehicular Networking” by Christoph Sommer and Falko Dressler, published in December 2014 by Cambridge University Press. ▪ Except where otherwise noted (e.g., logos and cited works) this slide deck is Copyright © 2009‐2015 C ...
PDF
... different switches (Figure 5). If the primary connection fails, it can switch transparently to its secondary link. However, if the primary link to the switch remains up, even though the corresponding uplink ports on the switch are down, the dual NIC device will not know that it may need to switch to ...
... different switches (Figure 5). If the primary connection fails, it can switch transparently to its secondary link. However, if the primary link to the switch remains up, even though the corresponding uplink ports on the switch are down, the dual NIC device will not know that it may need to switch to ...
Clavister Virtual Core
... Splunk for Clavister cOS Core is a comprehensive Webbased reporting system that offers enterprise-level reporting with tight integration with all Clavister cOS Core-based products. Splunk supports real-time data analysis, with Key Performance Indicators (KPI), graphs, tables and long-term trending, ...
... Splunk for Clavister cOS Core is a comprehensive Webbased reporting system that offers enterprise-level reporting with tight integration with all Clavister cOS Core-based products. Splunk supports real-time data analysis, with Key Performance Indicators (KPI), graphs, tables and long-term trending, ...
2.3.1 Establishing the Configuration Task
... 1 IP Multicast Configuration Guide.............................................................................................1 1.1 IP Multicast Overview........................................................................................................................................2 1.2 IP M ...
... 1 IP Multicast Configuration Guide.............................................................................................1 1.1 IP Multicast Overview........................................................................................................................................2 1.2 IP M ...
OSPF
... – This is an IP address used to identify a router – 3 criteria for deriving the router ID • Use IP address configured with OSPF router-id command – Takes precedence over loopback and physical interface ...
... – This is an IP address used to identify a router – 3 criteria for deriving the router ID • Use IP address configured with OSPF router-id command – Takes precedence over loopback and physical interface ...
Cisco Industrial Ethernet 3000 Layer 2/Layer 3 Series Switches Data
... v2 certification, with PROFINET conformance class B compliance. ● Simple Network Management Protocol (SNMP) (v1/v2/v3) support allows for management using traditional IT-based management tools, including CiscoWorks. ● Device Manager allows web-based switch configurations. ● DHCP port-based allocatio ...
... v2 certification, with PROFINET conformance class B compliance. ● Simple Network Management Protocol (SNMP) (v1/v2/v3) support allows for management using traditional IT-based management tools, including CiscoWorks. ● Device Manager allows web-based switch configurations. ● DHCP port-based allocatio ...
Auto Dedicated NIC Feature in iDRAC7
... Auto Dedicated NIC Feature in iDRAC7 You can adjust the time allowed to scan and detect a cable connected or disconnected to the dedicated NIC port from 5 to 255 seconds. By default, cable connection is detected within 5 seconds and disconnection is detected within 30 seconds. The time it takes to ...
... Auto Dedicated NIC Feature in iDRAC7 You can adjust the time allowed to scan and detect a cable connected or disconnected to the dedicated NIC port from 5 to 255 seconds. By default, cable connection is detected within 5 seconds and disconnection is detected within 30 seconds. The time it takes to ...
Comparative firewall study - Torsten Hoefler - Qucosa
... proxy is not transparent for the user. The sender must adjust explicitly the proxy. Direct access of the client to the server has to be suppressed by blocking ports in the packet filter or disabling routing completely. In the second case the proxy is also called dual-homed gateway. You can achieve a ...
... proxy is not transparent for the user. The sender must adjust explicitly the proxy. Direct access of the client to the server has to be suppressed by blocking ports in the packet filter or disabling routing completely. In the second case the proxy is also called dual-homed gateway. You can achieve a ...
CISCO CATALYST 3750 SERIES SWITCHES
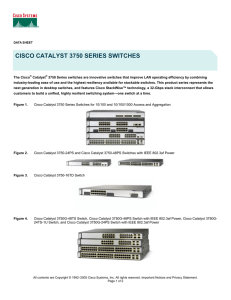
... 10/100/1000 ports or PoE 10/100/1000 ports, or nine 10 Gigabit Ethernet ports. Individual 10/100, 10/100/1000, and 10 Gigabit Ethernet units may be joined in any combination to evolve with network needs. Return on Investment through Lower Operations Costs The automatic Cisco IOS Software version che ...
... 10/100/1000 ports or PoE 10/100/1000 ports, or nine 10 Gigabit Ethernet ports. Individual 10/100, 10/100/1000, and 10 Gigabit Ethernet units may be joined in any combination to evolve with network needs. Return on Investment through Lower Operations Costs The automatic Cisco IOS Software version che ...
8 Security
... The present document has not been subject to any approval process by the 3GPP Organisational Partners and shall not be implemented. This Specification is provided for future development work within 3GPP only. The Organisational Partners accept no liability for any use of this Specification. Specific ...
... The present document has not been subject to any approval process by the 3GPP Organisational Partners and shall not be implemented. This Specification is provided for future development work within 3GPP only. The Organisational Partners accept no liability for any use of this Specification. Specific ...
PDF
... Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of t ...
... Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of t ...