SNMPv3 Fundamentals
... The course details how an SNMP Management Information Base (MIB), which stores network information, is organized and also how the protocol works to collect and store network information. The RMON standard uses SNMP with its own MIB format to collect statistics about a network. The detailed descripti ...
... The course details how an SNMP Management Information Base (MIB), which stores network information, is organized and also how the protocol works to collect and store network information. The RMON standard uses SNMP with its own MIB format to collect statistics about a network. The detailed descripti ...
hw3 - OpenLab
... Current demand for internet trafic in the world is growing due to the high take up of voice and bandwidth-intensive applications such as streaming and interactive video, plus the growing number of mobile devices equipped for Internet access. The other big problem is the problem of uncertainty, the i ...
... Current demand for internet trafic in the world is growing due to the high take up of voice and bandwidth-intensive applications such as streaming and interactive video, plus the growing number of mobile devices equipped for Internet access. The other big problem is the problem of uncertainty, the i ...
Lec6
... • First byte 0-127 • 8 bits for network ID , 24 bit for host ID – Class B • Allow 16382 networks and 64,000 host each. • Addresses are assigned to large- and medium-sized ...
... • First byte 0-127 • 8 bits for network ID , 24 bit for host ID – Class B • Allow 16382 networks and 64,000 host each. • Addresses are assigned to large- and medium-sized ...
Protecting Cyber-TA Contributors
... How to do collaborative analysis if networks don’t trust each other? • Intrusion detection data • Security alerts • Firewall data ...
... How to do collaborative analysis if networks don’t trust each other? • Intrusion detection data • Security alerts • Firewall data ...
The Basics of Application Monitoring
... Before we dive into the details of what IP addresses are, how there are assigned and how they are routed we should make sure some of the basic concepts are covered. For computing purposes, one of three notations is normally used to represent numbers. These are Hexadecimal, a base 16 system, decimal, ...
... Before we dive into the details of what IP addresses are, how there are assigned and how they are routed we should make sure some of the basic concepts are covered. For computing purposes, one of three notations is normally used to represent numbers. These are Hexadecimal, a base 16 system, decimal, ...
Week 5
... dest. network unreachable dest host unreachable dest protocol unreachable dest port unreachable dest network unknown dest host unknown source quench (congestion control - not used) ...
... dest. network unreachable dest host unreachable dest protocol unreachable dest port unreachable dest network unknown dest host unknown source quench (congestion control - not used) ...
Chapter Three
... provide communications between hosts on a network Each IP address is a unique 32-bit number, divided into four groups of octets separated by periods ...
... provide communications between hosts on a network Each IP address is a unique 32-bit number, divided into four groups of octets separated by periods ...
PPT - web.iiit.ac.in
... routers are devices which do this – Used for global addressing • MAC (or LAN or physical or Ethernet) address: – Used to get frame from one interface to another physicallyconnected interface (same network) – 48 bit MAC address, typically burned in the adapter ROM • ARP: Address Resolution Protocol – ...
... routers are devices which do this – Used for global addressing • MAC (or LAN or physical or Ethernet) address: – Used to get frame from one interface to another physicallyconnected interface (same network) – 48 bit MAC address, typically burned in the adapter ROM • ARP: Address Resolution Protocol – ...
District/School Network Secondary Backup Student Response Save Location
... Browser based Java dependent tool that can: Evaluate Windows and Mac OS X testing workstation readiness Evaluates bandwidth from Pearson and Proctor Caching devices Will not work on iPads and Chromebooks ...
... Browser based Java dependent tool that can: Evaluate Windows and Mac OS X testing workstation readiness Evaluates bandwidth from Pearson and Proctor Caching devices Will not work on iPads and Chromebooks ...
Document
... However, the actual number of translations supported is approximately 4,000 local addresses per global address Network Architecture and Design ...
... However, the actual number of translations supported is approximately 4,000 local addresses per global address Network Architecture and Design ...
ch01 - Montana State University
... • A common way of thinking about networks is by the scale of the network. 4 common network types are: – Local Area Networks (LANs) which typically occupy a room or building, usually include a group of PCs that share a circuit. – Backbone Networks, have a scale of a few hundred meters to a few kilome ...
... • A common way of thinking about networks is by the scale of the network. 4 common network types are: – Local Area Networks (LANs) which typically occupy a room or building, usually include a group of PCs that share a circuit. – Backbone Networks, have a scale of a few hundred meters to a few kilome ...
File Transfer Protocol (FTP)
... transfers displayable Web pages and related files, and the Simple Mail Transfer Protocol (SMTP), which transfers e-mail, FTP is an application protocol that uses the Internet's TCP/IP protocols. FTP is commonly used to transfer Web page files from their creator to the computer that acts as their ser ...
... transfers displayable Web pages and related files, and the Simple Mail Transfer Protocol (SMTP), which transfers e-mail, FTP is an application protocol that uses the Internet's TCP/IP protocols. FTP is commonly used to transfer Web page files from their creator to the computer that acts as their ser ...
- Magni5 Technology
... for industrial device control applications using RS-485 COMMUNICATION. This technology has several benefits for these applications in term of noise immunity, wide common-mode voltage range, adequate data rate, and multipoint capability. Other applications also use RS-485 signaling to take advantage ...
... for industrial device control applications using RS-485 COMMUNICATION. This technology has several benefits for these applications in term of noise immunity, wide common-mode voltage range, adequate data rate, and multipoint capability. Other applications also use RS-485 signaling to take advantage ...
9. telecommunications
... – Files and messages are broken down into packets, which are electronically labeled with their origin and destination – The destination computer collects the packets and reassembles the data from the pieces in each packet – Each computer the packet encounters decides the best route towards its desti ...
... – Files and messages are broken down into packets, which are electronically labeled with their origin and destination – The destination computer collects the packets and reassembles the data from the pieces in each packet – Each computer the packet encounters decides the best route towards its desti ...
Security Overview
... •A security attack is any action that compromises the security of information (i.e. stored or in ...
... •A security attack is any action that compromises the security of information (i.e. stored or in ...
R7200 SDSL Routers
... inbound traffic originated from the Internet; preconfigured NetBIOS filters to optimize performance of DSL link. Includes IP & IPX (RIP and SAP) filtering; Filter packets on a per-connection profile basis for source/destination address, service, and protocol. Up to 255 rules in up to 8 filter sets. ...
... inbound traffic originated from the Internet; preconfigured NetBIOS filters to optimize performance of DSL link. Includes IP & IPX (RIP and SAP) filtering; Filter packets on a per-connection profile basis for source/destination address, service, and protocol. Up to 255 rules in up to 8 filter sets. ...
ip-basics
... computers address each other and send data to each other Is a suite of protocols named after the two most important protocols TCP and IP but includes other protocols such as UDP, RTP, etc ...
... computers address each other and send data to each other Is a suite of protocols named after the two most important protocols TCP and IP but includes other protocols such as UDP, RTP, etc ...
Slide - Computer Science
... It is the job of the DNS to convert symbolic names to a sequence of 32 binary bits DNS is a massive distributed database If local name server does not recognize host name, it is forwarded to a remote name servers until one locates its name. ...
... It is the job of the DNS to convert symbolic names to a sequence of 32 binary bits DNS is a massive distributed database If local name server does not recognize host name, it is forwarded to a remote name servers until one locates its name. ...
COMS 4995-1 Networking Laboratory
... Since ARP does not authenticate requests or replies, ARP Requests and Replies can be forged ARP is stateless: ARP Replies can be sent without a corresponding ARP Request According to the ARP protocol specification, a node receiving an ARP packet (Request or Reply) must update its local ARP cache wit ...
... Since ARP does not authenticate requests or replies, ARP Requests and Replies can be forged ARP is stateless: ARP Replies can be sent without a corresponding ARP Request According to the ARP protocol specification, a node receiving an ARP packet (Request or Reply) must update its local ARP cache wit ...
B.Sc. Math Science - Department of Computer Science
... ADTs and Arrays: Single and Multidimensional arrays, Sequential Allocation Stacks : Definition of stack, array implementation of stack, conversion of infix expression to prefix, postfix expressions, evaluation of postfix expression. Queues : Definition of Queue, circular queues, priority queues, arr ...
... ADTs and Arrays: Single and Multidimensional arrays, Sequential Allocation Stacks : Definition of stack, array implementation of stack, conversion of infix expression to prefix, postfix expressions, evaluation of postfix expression. Queues : Definition of Queue, circular queues, priority queues, arr ...
Systems Area: OS and Networking
... Large variety of traffic patterns (most not point-to-point): - Any-to-any, many-to-one, many-to-few, one-to-many - Inneficient to impl. these patterns over point-to-point ...
... Large variety of traffic patterns (most not point-to-point): - Any-to-any, many-to-one, many-to-few, one-to-many - Inneficient to impl. these patterns over point-to-point ...
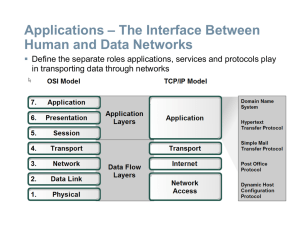
Application Layer Functionality and Protocols
... Name the three types of communication in the Network Layer and describe the characteristics of each type ...
... Name the three types of communication in the Network Layer and describe the characteristics of each type ...
What is a Computer Network?
... • Due to loss of signal strength it is often necessary to use a repeater to boost the signal. • A repeater is a hardware device to link together two cable segments. • The repeater amplifies the signal it receives before passing it on. ...
... • Due to loss of signal strength it is often necessary to use a repeater to boost the signal. • A repeater is a hardware device to link together two cable segments. • The repeater amplifies the signal it receives before passing it on. ...