Lecture 23
... Messages arrive faster than the hardware can process them… Messages are lost, and retransmitted,… And this problem can compound if the overload is not transient ...
... Messages arrive faster than the hardware can process them… Messages are lost, and retransmitted,… And this problem can compound if the overload is not transient ...
Different Network Equipment
... sent through the network, including how bits are electrically signaled by hardware devices that interface directly with a network medium, such as coaxial cable, optical fiber, or twisted-pair copper wire. Protocols:Ethernet, Token Ring, FDDI, X.25, Frame Relay, RS-232, v.35 ...
... sent through the network, including how bits are electrically signaled by hardware devices that interface directly with a network medium, such as coaxial cable, optical fiber, or twisted-pair copper wire. Protocols:Ethernet, Token Ring, FDDI, X.25, Frame Relay, RS-232, v.35 ...
15-744: Computer Networking
... • Perform computation based on their internal state and control information carried in packet • Forward zero or more packets to end points depending on result of the computation ...
... • Perform computation based on their internal state and control information carried in packet • Forward zero or more packets to end points depending on result of the computation ...
Our Team is Proud to Deliver the Best Network Solutions
... Formerly, PT IDN born with brand “ID-Networkers”. ID-Networkers was established in 2008, we are a group of young people who have the spirit and idea to increase skill and number of certified network engineer in Indonesia and Asia Pacific. We are proud to have helped thousands of students to learn ne ...
... Formerly, PT IDN born with brand “ID-Networkers”. ID-Networkers was established in 2008, we are a group of young people who have the spirit and idea to increase skill and number of certified network engineer in Indonesia and Asia Pacific. We are proud to have helped thousands of students to learn ne ...
Local Area Networks
... •Sometimes necessary to connect local area network to another LAN or to wide area network •Local area network to local area network connections often performed with bridge-like device •Local area network to wide area network connections usually performed with router •Switch - can be used to intercon ...
... •Sometimes necessary to connect local area network to another LAN or to wide area network •Local area network to local area network connections often performed with bridge-like device •Local area network to wide area network connections usually performed with router •Switch - can be used to intercon ...
COMP 535 Multicasting Simon Foucher (260 223 197) McGill
... interest and is now built into every IP router and often deployed within enterprise networks. However there is little crossprovider global deployment of multicast because the demand for multicast applications does not justify the complexity of its deployment. Multicasting is the ability for a commun ...
... interest and is now built into every IP router and often deployed within enterprise networks. However there is little crossprovider global deployment of multicast because the demand for multicast applications does not justify the complexity of its deployment. Multicasting is the ability for a commun ...
802.11 frame - Department of Computer and Information Science
... allow sender to “reserve” channel rather than random access of data frames: avoid collisions of long data frames sender first transmits small request-to-send (RTS) packets to BS using CSMA RTS may still collide with each other (but they’re short) BS broadcasts clear-to-send (CTS) in response to RTS ...
... allow sender to “reserve” channel rather than random access of data frames: avoid collisions of long data frames sender first transmits small request-to-send (RTS) packets to BS using CSMA RTS may still collide with each other (but they’re short) BS broadcasts clear-to-send (CTS) in response to RTS ...
No Slide Title - University of Delaware
... Simultaneously optimizing large networks across multiple network functions, layers, and levels of hierarchy. Faster Simulated Annealing and other techniques to optimize more complex cost functions over more nodes. Better local maintenance algorithms based on the reclustering cost functions. Optimize ...
... Simultaneously optimizing large networks across multiple network functions, layers, and levels of hierarchy. Faster Simulated Annealing and other techniques to optimize more complex cost functions over more nodes. Better local maintenance algorithms based on the reclustering cost functions. Optimize ...
PDF (Updated 1/18)
... Protocols at this level transmit data in a network representation that is independent of the representations used in individual computers, which may differ. Encryption is also performed in this layer, if required. At this level reliability and adaptation are performed, such as detection of failures ...
... Protocols at this level transmit data in a network representation that is independent of the representations used in individual computers, which may differ. Encryption is also performed in this layer, if required. At this level reliability and adaptation are performed, such as detection of failures ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... enforcement point in and out, policy decision point and controller. Based on this, the simulation configured the send and receives function to achieve the functionality of this component policy. Decision point is used to share source code to achieve the functionality of component in all nodes. Contr ...
... enforcement point in and out, policy decision point and controller. Based on this, the simulation configured the send and receives function to achieve the functionality of this component policy. Decision point is used to share source code to achieve the functionality of component in all nodes. Contr ...
SpeedStream® Residential Gateway Family
... Seamless, standards-based wireless networking interoperates with other 802.11g or 802.11b compliant networks and devices. Available 10/100 Ethernet, USB, HPNA and Powerline connectivity options provide the solution for almost every subscriber need. ...
... Seamless, standards-based wireless networking interoperates with other 802.11g or 802.11b compliant networks and devices. Available 10/100 Ethernet, USB, HPNA and Powerline connectivity options provide the solution for almost every subscriber need. ...
Chapter No. 08
... on continuous data and produce approximate results Digital Computers – General purpose Computers based on discrete date and produce accurate results Hybrid – Combination of Digital and Analog computers. ICMAP-Shakeel ...
... on continuous data and produce approximate results Digital Computers – General purpose Computers based on discrete date and produce accurate results Hybrid – Combination of Digital and Analog computers. ICMAP-Shakeel ...
RAFI ULLAH KHAN - Agricultural University Peshawar
... Stack I and II and Foundry Big Iron 8000 and 2400 CF series), Configuring VLANs, Private VLANs, HSRP, VRRP GLBP, VTP etc Management of Huge Subnets for reliable Networking Maintenance & Management of Network graphs using MRTG Maintenance & Management of Firewall (PIX Firewall and ASA) Access L ...
... Stack I and II and Foundry Big Iron 8000 and 2400 CF series), Configuring VLANs, Private VLANs, HSRP, VRRP GLBP, VTP etc Management of Huge Subnets for reliable Networking Maintenance & Management of Network graphs using MRTG Maintenance & Management of Firewall (PIX Firewall and ASA) Access L ...
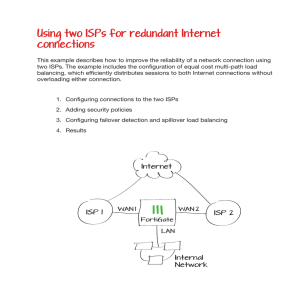
Using two ISPs for redundant Internet connections
... This example describes how to improve the reliability of a network connection using two ISPs. The example includes the configuration of equal cost multi-path load balancing, which efficiently distributes sessions to both Internet connections without overloading either connection. ...
... This example describes how to improve the reliability of a network connection using two ISPs. The example includes the configuration of equal cost multi-path load balancing, which efficiently distributes sessions to both Internet connections without overloading either connection. ...
Neural Networks in Computer Science
... – perfect learning: error = 0 – can be misleading, especially if there are relatively few patterns that give bad results • e.g. Quicksort average vs. worst-case behavior – avg. time for 1 million names: 20,000,000 ops. – worst-case: 1,000,000,000,000 (1 trillion) ops. ...
... – perfect learning: error = 0 – can be misleading, especially if there are relatively few patterns that give bad results • e.g. Quicksort average vs. worst-case behavior – avg. time for 1 million names: 20,000,000 ops. – worst-case: 1,000,000,000,000 (1 trillion) ops. ...
Academic Network of Albania
... – Centralized system, in addition to the current setup • The Universities will still keep their current system • Some preconfigured VoIP phones could be given out to Universities • The VoIP phones can be seen as new, separate lines ...
... – Centralized system, in addition to the current setup • The Universities will still keep their current system • Some preconfigured VoIP phones could be given out to Universities • The VoIP phones can be seen as new, separate lines ...
Chapter 1 Outline
... Hubs segment the network; a break in any of the cables attached to the hub would bring only that segment down. The remainder of the network will continue to work. ...
... Hubs segment the network; a break in any of the cables attached to the hub would bring only that segment down. The remainder of the network will continue to work. ...
Modernization as a key to lower production costs
... PROFINET, with its low protocol overhead and simple communication structures allow cooperation of standard TCP/IP services for non-deterministic behavior but large data amounts side-by-side with highspeed, highly deterministic I/O data exchange with limited data amounts as found on the machine level ...
... PROFINET, with its low protocol overhead and simple communication structures allow cooperation of standard TCP/IP services for non-deterministic behavior but large data amounts side-by-side with highspeed, highly deterministic I/O data exchange with limited data amounts as found on the machine level ...
cs4513 Distributed Computer Systems
... Inconsistencies in view make NOSes harder, in general for users than DOSes. – But easier to scale by adding computers ...
... Inconsistencies in view make NOSes harder, in general for users than DOSes. – But easier to scale by adding computers ...
Internet
... from an address pool (stored in a DHCP server) and after usage is returned to the address pool. ...
... from an address pool (stored in a DHCP server) and after usage is returned to the address pool. ...
Campus Networks - Department of Computing & Immersive
... details into an understandable model Hierarchy, when used properly, makes network more predictable The Cisco hierarchical model can help you design, implement, and maintain a scalable, reliable, cost-effective hierarchical internetwork RD-CSY2001-09/10 ...
... details into an understandable model Hierarchy, when used properly, makes network more predictable The Cisco hierarchical model can help you design, implement, and maintain a scalable, reliable, cost-effective hierarchical internetwork RD-CSY2001-09/10 ...
Routing
... – Each source uses different source specific shortest path tree for data forwarding – Cost of group formation with these schemes: join/prune information store per source per group per interface in each router. – Both suffer from scaling problems.Building trees installs state in the routers. It is ea ...
... – Each source uses different source specific shortest path tree for data forwarding – Cost of group formation with these schemes: join/prune information store per source per group per interface in each router. – Both suffer from scaling problems.Building trees installs state in the routers. It is ea ...
1 Distributed Systems What are distributed systems? How would you
... modified time before reading cached copy. Tradeoff? More simple and robust, less efficient. What about writes? Write-through or write-back policy? 2. Partition state onto 2 servers. How? E.g. different users can be assigned different servers. But how to ensure good load balancing? ...
... modified time before reading cached copy. Tradeoff? More simple and robust, less efficient. What about writes? Write-through or write-back policy? 2. Partition state onto 2 servers. How? E.g. different users can be assigned different servers. But how to ensure good load balancing? ...
Topic 5 - Networking - St Andrew`s High School
... Computer networks can be categorised by the rate at which data can be transferred between machines (bandwidth), and the physical distance between them. Usually there is a relationship between these factors - the greater the distance, the lower the bandwidth, although of course if you have the resour ...
... Computer networks can be categorised by the rate at which data can be transferred between machines (bandwidth), and the physical distance between them. Usually there is a relationship between these factors - the greater the distance, the lower the bandwidth, although of course if you have the resour ...
Network Layer
... Class D addresses were designed for multicasting. Each address in this class is used to define one group of hosts on the Internet. The Internet authorities wrongly predicted a need for 268,435,456 groups. This never happened and many addresses were wasted here too. And lastly, the class E addresses ...
... Class D addresses were designed for multicasting. Each address in this class is used to define one group of hosts on the Internet. The Internet authorities wrongly predicted a need for 268,435,456 groups. This never happened and many addresses were wasted here too. And lastly, the class E addresses ...