Lecture 3: Slides
... DVRMP and PIM-DM initially flood the n/wk Each multicast router requires a lot of state The sender runs the risk of getting traffic back from a large group of recipients [PAS1998] provides a summary of approaches emphasizing different goals ...
... DVRMP and PIM-DM initially flood the n/wk Each multicast router requires a lot of state The sender runs the risk of getting traffic back from a large group of recipients [PAS1998] provides a summary of approaches emphasizing different goals ...
ch02
... processes at this time with port addresses a, b, and c. The receiving computer is running two processes at this time with port addresses j and k. Process a in the sending computer needs to communicate with process j in the receiving computer. Note that although physical addresses change from hop to ...
... processes at this time with port addresses a, b, and c. The receiving computer is running two processes at this time with port addresses j and k. Process a in the sending computer needs to communicate with process j in the receiving computer. Note that although physical addresses change from hop to ...
Network Engineer (1994 – 1995)
... Testing and Certification of new Hardware, Software, patches and features for new functionality as well as regression testing. Proven success in providing design solutions, project management, system analysis, pre-sale technical support, implementation/deployment and post-implementation support and ...
... Testing and Certification of new Hardware, Software, patches and features for new functionality as well as regression testing. Proven success in providing design solutions, project management, system analysis, pre-sale technical support, implementation/deployment and post-implementation support and ...
CSC311_UNIT1_Part2
... processes at this time with port addresses a, b, and c. The receiving computer is running two processes at this time with port addresses j and k. Process a in the sending computer needs to communicate with process j in the receiving computer. Note that although physical addresses change from hop to ...
... processes at this time with port addresses a, b, and c. The receiving computer is running two processes at this time with port addresses j and k. Process a in the sending computer needs to communicate with process j in the receiving computer. Note that although physical addresses change from hop to ...
What are the Advantages and Disadvantages of a Policy
... The customer server was then implemented by creating a VLAN which would later connect to the core switches, this is the same scenario for the company server, and the only difference would be that the VLAN would have a separate ID. Once the customer server and company server have their VLANs set up, ...
... The customer server was then implemented by creating a VLAN which would later connect to the core switches, this is the same scenario for the company server, and the only difference would be that the VLAN would have a separate ID. Once the customer server and company server have their VLANs set up, ...
Module 4 unit 3, 4
... The IP datagram header contains the following fields: •Version: Identifies the version of IP used to generate the datagram. For IPv4, this is of course the number 4. The purpose of this field is to ensure compatibility between devices that may be running different versions of IP. In general, a devi ...
... The IP datagram header contains the following fields: •Version: Identifies the version of IP used to generate the datagram. For IPv4, this is of course the number 4. The purpose of this field is to ensure compatibility between devices that may be running different versions of IP. In general, a devi ...
With the help of this diagram, try to describe the function of these
... A bridge is a hardware and software combination (use) to connect the same type of networks. A backbone is a network transmission path (handle) major data traffic. A router is a special computer (direct) messages when several networks are linked. A network is a number of computers and peripherals (li ...
... A bridge is a hardware and software combination (use) to connect the same type of networks. A backbone is a network transmission path (handle) major data traffic. A router is a special computer (direct) messages when several networks are linked. A network is a number of computers and peripherals (li ...
Ethernet - GITAM University
... Defines how TCP/IP application protocols and how host programs interface with transport layer services to use the network. protocols regarding this layer are FTP,HTTP,SMTP,TELNET,SNMP. Transport layer: Provides communication session management between host computers. Defines the level of service and ...
... Defines how TCP/IP application protocols and how host programs interface with transport layer services to use the network. protocols regarding this layer are FTP,HTTP,SMTP,TELNET,SNMP. Transport layer: Provides communication session management between host computers. Defines the level of service and ...
comp4_unit7_self-assess_key
... Objective(s): List and describe the various types of network communications and network addressing. Lecture(s)/Slide(s): 1/ 11 5. _____ is the number of bits sent across the media at any one time that represent your computer’s actual communication. a. Mbps b. Throughput c. Goodput d. Bandwidth Answe ...
... Objective(s): List and describe the various types of network communications and network addressing. Lecture(s)/Slide(s): 1/ 11 5. _____ is the number of bits sent across the media at any one time that represent your computer’s actual communication. a. Mbps b. Throughput c. Goodput d. Bandwidth Answe ...
TCP/IP and Other Transports for High Bandwidth Applications
... The aim is to give you a picture of how researchers are using high performance networks to support their work. Back to Basics Simple Introduction to Networking TCP/IP on High Bandwidth Long Distance Networks But TCP/IP works ! The effect of packet loss ...
... The aim is to give you a picture of how researchers are using high performance networks to support their work. Back to Basics Simple Introduction to Networking TCP/IP on High Bandwidth Long Distance Networks But TCP/IP works ! The effect of packet loss ...
SO WHAT IS VOIP - Xtranet internet service provider
... Protocol is the set of standard rules for data representation, signaling, authentication and error detection required to send information over a communications channel. An example of a simple communications protocol adapted to voice communication is the case of a radio dispatcher talking to mobile s ...
... Protocol is the set of standard rules for data representation, signaling, authentication and error detection required to send information over a communications channel. An example of a simple communications protocol adapted to voice communication is the case of a radio dispatcher talking to mobile s ...
lecture 9 - Philadelphia University
... The information is passed from the Application layer to the Transport layer. The Transport layer protocols consider the Application layer information as the payload (or data) that needs to be delivered and create a header that contains information such as source and destination port, to help with de ...
... The information is passed from the Application layer to the Transport layer. The Transport layer protocols consider the Application layer information as the payload (or data) that needs to be delivered and create a header that contains information such as source and destination port, to help with de ...
The Network Layer
... • Congestion is a problem when too many packets are present in the subnet, performance degrades • Congestions can be brought on by several factors: – All of a sudden, streams of packets arrive on multiple input lines and all of them need the same output line, a queue is built up. Allocating more mem ...
... • Congestion is a problem when too many packets are present in the subnet, performance degrades • Congestions can be brought on by several factors: – All of a sudden, streams of packets arrive on multiple input lines and all of them need the same output line, a queue is built up. Allocating more mem ...
HP 6200-24G-mGBIC yl Switch
... – IEEE 802.1X users per port provides authentication of multiple IEEE 802.1X users per port – Web-based authentication authenticates from Web browser for clients that do not support IEEE 802.1X supplicant – MAC-based authentication authenticates client with the RADIUS server based on client's MAC ad ...
... – IEEE 802.1X users per port provides authentication of multiple IEEE 802.1X users per port – Web-based authentication authenticates from Web browser for clients that do not support IEEE 802.1X supplicant – MAC-based authentication authenticates client with the RADIUS server based on client's MAC ad ...
IxNetwork
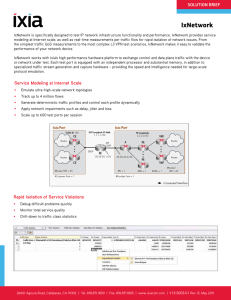
... IxNetwork is specifically designed to test IP network infrastructure functionality and performance. IxNetwork provides service modeling at Internet scale, as well as real-time measurements per traffic flow for rapid isolation of network issues. From the simplest traffic QoS measurements to the most ...
... IxNetwork is specifically designed to test IP network infrastructure functionality and performance. IxNetwork provides service modeling at Internet scale, as well as real-time measurements per traffic flow for rapid isolation of network issues. From the simplest traffic QoS measurements to the most ...
Document
... where source and destination are hosts identified by fixed-length addresses • Datagrams can be as large as 64 KB, but usually the are ~1500 bytes long. • IP also provides for fragmentation and reassembly of long datagrams, if necessary, for transmission through small packet networks. • IP basically ...
... where source and destination are hosts identified by fixed-length addresses • Datagrams can be as large as 64 KB, but usually the are ~1500 bytes long. • IP also provides for fragmentation and reassembly of long datagrams, if necessary, for transmission through small packet networks. • IP basically ...
Scale and Performance in a Distributed File
... Several Problem Areas in high speed neworks Multicast distribution: What techniques should be used to efficiently implement logical channels for multicast switching in a network with many subscribers, in order to support applications ranging from selective distribution to dynamically reconfigurabl ...
... Several Problem Areas in high speed neworks Multicast distribution: What techniques should be used to efficiently implement logical channels for multicast switching in a network with many subscribers, in order to support applications ranging from selective distribution to dynamically reconfigurabl ...
Multi-Site Clustering with Windows Server 2008 R2
... SVR208 Gaining Higher Availability with Windows Server 2008 R2 Failover Clustering SVR319 Multi-Site Clustering with Windows Server 2008 R2 DAT312 All You Needed to Know about Microsoft SQL Server 2008 Failover Clustering UNC307 Microsoft Exchange Server 2010 High Availability SVR211 The Challenges ...
... SVR208 Gaining Higher Availability with Windows Server 2008 R2 Failover Clustering SVR319 Multi-Site Clustering with Windows Server 2008 R2 DAT312 All You Needed to Know about Microsoft SQL Server 2008 Failover Clustering UNC307 Microsoft Exchange Server 2010 High Availability SVR211 The Challenges ...
Network - Storr Consulting
... SNA - Systems Network Architecture Proprietary IBM architecture and set of implementing products for their network computing within an enterprise. It became part of IBM’s System Application Architecture (SAA) and it is currently part of IBM’s Open Blueprint. IBM is finding ways to combine its ...
... SNA - Systems Network Architecture Proprietary IBM architecture and set of implementing products for their network computing within an enterprise. It became part of IBM’s System Application Architecture (SAA) and it is currently part of IBM’s Open Blueprint. IBM is finding ways to combine its ...
ppt
... Excessive congestion: packet delay and loss protocols needed for reliable data transfer, ...
... Excessive congestion: packet delay and loss protocols needed for reliable data transfer, ...
Proposal to Intel for research support
... if not impossible, job. Users commonly experience painfully slow access to networked file systems in the local area, and loss of connectivity to web sites due to route flapping in the wide area. In time, the situation is only going to get worse. Networks are being added to the Internet at a rapid cl ...
... if not impossible, job. Users commonly experience painfully slow access to networked file systems in the local area, and loss of connectivity to web sites due to route flapping in the wide area. In time, the situation is only going to get worse. Networks are being added to the Internet at a rapid cl ...