Agent-Based Decision Support Systems for the
... and any transport protocol data reassembly, emulating the traffic received by the endsystem(s) being protected. By reassembling these packets before they hit the intended target CCSS will be providing new levels of protection. CCSS will modify or remove any traffic protocol ambiguities, protecting t ...
... and any transport protocol data reassembly, emulating the traffic received by the endsystem(s) being protected. By reassembling these packets before they hit the intended target CCSS will be providing new levels of protection. CCSS will modify or remove any traffic protocol ambiguities, protecting t ...
No Slide Title
... Department of Computer Engineering, Kasetsart University 204421 Computer Networks ...
... Department of Computer Engineering, Kasetsart University 204421 Computer Networks ...
slides - network systems lab @ sfu
... sending to receiving host on sending side encapsulates segments into datagrams on receiving side, delivers segments to transport layer network layer protocols in every host, router ...
... sending to receiving host on sending side encapsulates segments into datagrams on receiving side, delivers segments to transport layer network layer protocols in every host, router ...
Transmitter, Amplifier and Receiver Design
... Presentation layer protocol: formatting, encoding (It is concerned with the format of data exchanged between peers, for example, whether an integer is 16, 32 or 64 bits long and whether the most significant bit is transmitted first or last.) Session layer protocol: logical level session initializat ...
... Presentation layer protocol: formatting, encoding (It is concerned with the format of data exchanged between peers, for example, whether an integer is 16, 32 or 64 bits long and whether the most significant bit is transmitted first or last.) Session layer protocol: logical level session initializat ...
ns - Pattern
... kinds of ad hoc routing protocols are implemented. •Based on the libpcap library and on the use of RAW sockets. •Integrated with a statistic module (performance indexes). ...
... kinds of ad hoc routing protocols are implemented. •Based on the libpcap library and on the use of RAW sockets. •Integrated with a statistic module (performance indexes). ...
Networking - The Art of Zombie
... Your router isn't the only thing that determines wireless speed: you also need the correct kind of wireless card in your computer. If you have an older laptop, it might have an older wireless G card inside, meaning it can't take advantage of wireless N speeds. If you have a mix of N- and G-capable c ...
... Your router isn't the only thing that determines wireless speed: you also need the correct kind of wireless card in your computer. If you have an older laptop, it might have an older wireless G card inside, meaning it can't take advantage of wireless N speeds. If you have a mix of N- and G-capable c ...
wireless
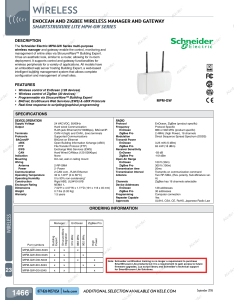
... DESCRIPTION The Schneider Electric MPM-GW Series multi-purpose wireless manager and gateway enable the control, monitoring and management of entire sites via StruxureWare™ Building Expert. It has an aesthetic look, similar to a router, allowing for in-room deployment. It supports control and gateway ...
... DESCRIPTION The Schneider Electric MPM-GW Series multi-purpose wireless manager and gateway enable the control, monitoring and management of entire sites via StruxureWare™ Building Expert. It has an aesthetic look, similar to a router, allowing for in-room deployment. It supports control and gateway ...
30403002 Presentation on IP Network Model
... QoS controlled Edge Routing Route Flapping Link Failure Load Sharing Time Drift MTU Size Packet Loss Background Traffic (Congestion, Bandwidth, Utilization, Network Load) One Way Delay ...
... QoS controlled Edge Routing Route Flapping Link Failure Load Sharing Time Drift MTU Size Packet Loss Background Traffic (Congestion, Bandwidth, Utilization, Network Load) One Way Delay ...
Chapter 4 - LAN Design
... using hubs, the bandwidth of each switched port is shared by all the devices. Therefore, they also share the same collision domain. To determine the bandwidth per host, simply divide the port’s bandwidth by the number of hosts ...
... using hubs, the bandwidth of each switched port is shared by all the devices. Therefore, they also share the same collision domain. To determine the bandwidth per host, simply divide the port’s bandwidth by the number of hosts ...
Voice Over IP
... To ensure quality of service before the call is set up, one group under IETF has developed the Resource Reservation Protocol (RSVP). It aims at ensuring each flow’s QoS requirements through the complete path from the sender to the receiver. Each component involved along the path is responsible for t ...
... To ensure quality of service before the call is set up, one group under IETF has developed the Resource Reservation Protocol (RSVP). It aims at ensuring each flow’s QoS requirements through the complete path from the sender to the receiver. Each component involved along the path is responsible for t ...
An Introduction To Networking
... networks, and distributed multi-server networks. In peer-to-peer networks, the individual users or clients directly interact and share resources, without benefit of a central repository or server. This level of connection is common in small office or home networks. Sharing hard drives or directories ...
... networks, and distributed multi-server networks. In peer-to-peer networks, the individual users or clients directly interact and share resources, without benefit of a central repository or server. This level of connection is common in small office or home networks. Sharing hard drives or directories ...
Security Incidents Response in China
... exhaust the bandwidth resources so that it could not respond to the requests normally. ...
... exhaust the bandwidth resources so that it could not respond to the requests normally. ...
DeltaV™ Network Time Synchronization
... Using Stratum 1 NTP Time Servers Directly Connected to the DeltaV ACN If a Stratum 1 NTP time server is installed on the ACN, then the DeltaV workstations and embedded nodes will automatically get their time from this server instead. Even the workstations that are defined as master/backup time serve ...
... Using Stratum 1 NTP Time Servers Directly Connected to the DeltaV ACN If a Stratum 1 NTP time server is installed on the ACN, then the DeltaV workstations and embedded nodes will automatically get their time from this server instead. Even the workstations that are defined as master/backup time serve ...
pptx - University of Cambridge Computer Laboratory
... • understand principles behind network layer services: – network layer service models – forwarding versus routing (versus switching) – how a router works – routing (path selection) – IPv6 ...
... • understand principles behind network layer services: – network layer service models – forwarding versus routing (versus switching) – how a router works – routing (path selection) – IPv6 ...
Slide 1
... TG4.3 Network protocols Protocol. The set of rules and procedures governing transmission across a network Ethernet. The most common network protocol. ...
... TG4.3 Network protocols Protocol. The set of rules and procedures governing transmission across a network Ethernet. The most common network protocol. ...
IP-based LAN/WAN solution enables point-to
... integrated support for back-racked PCs and virtual desktops. In particular, the design addresses applications with a mix of both worlds — without changing the front end for the user. Desktop virtualization is deployed through a PC or server that hosts multiple virtual desktops. The workstations can ...
... integrated support for back-racked PCs and virtual desktops. In particular, the design addresses applications with a mix of both worlds — without changing the front end for the user. Desktop virtualization is deployed through a PC or server that hosts multiple virtual desktops. The workstations can ...
PCI and ISA Network cards
... • PCI BIOS decides base address of PCI cards. • PCI BIOS : Address port - 0xCf8 and Data port - 0xCfC . • 256 - bytes for each PCI device. • Network card - Device ID : 0x02. • Base Addr. and IRQ in 256 bytes. ...
... • PCI BIOS decides base address of PCI cards. • PCI BIOS : Address port - 0xCf8 and Data port - 0xCfC . • 256 - bytes for each PCI device. • Network card - Device ID : 0x02. • Base Addr. and IRQ in 256 bytes. ...
How the TCP/IP Protocol Works
... • Since assigned contiguously, class C CIDR has same most significant bits & so only needs one routing table entry • CIDR block represented by a prefix and prefix length – Prefix = single address representing block of nets, e.g • 192.32.136.0 = 11000000 00100000 10001000 00000000 while ...
... • Since assigned contiguously, class C CIDR has same most significant bits & so only needs one routing table entry • CIDR block represented by a prefix and prefix length – Prefix = single address representing block of nets, e.g • 192.32.136.0 = 11000000 00100000 10001000 00000000 while ...
Chapter 4 Introduction to Network Layer
... packet-switch network using the destination address of the packet and a routing table. To discuss how routers forward packets in a connection-oriented packet-switch network using the label on the packet and a routing table. To discuss services already provided in the network layer such as logica ...
... packet-switch network using the destination address of the packet and a routing table. To discuss how routers forward packets in a connection-oriented packet-switch network using the label on the packet and a routing table. To discuss services already provided in the network layer such as logica ...
CMPT 371: Chapter 1 - Simon Fraser University
... sending to receiving host on sending side encapsulates segments into datagrams on receiving side, delivers segments to transport layer network layer protocols in every host, router ...
... sending to receiving host on sending side encapsulates segments into datagrams on receiving side, delivers segments to transport layer network layer protocols in every host, router ...
Lesson Plan Network Design
... Diagram - An illustration of a plan, in networking it describes a design. Fiber Distributed Data Interface (FDDI) Hub -used to connect segments of a LAN that uses multiple ports. Hybrid hub - a device used to interconnect different types of cables and to maximize network efficiency. Layout ...
... Diagram - An illustration of a plan, in networking it describes a design. Fiber Distributed Data Interface (FDDI) Hub -used to connect segments of a LAN that uses multiple ports. Hybrid hub - a device used to interconnect different types of cables and to maximize network efficiency. Layout ...
Using the Remote Socket Architecture as NAT Replacement Michael Eyrich, Tobias Poschwatta,
... With the constantly growing Internet, globally valid addresses of the IP version 4 addressing scheme are on their way to get a scarce resource. Although the total number of available addresses is huge—nearly 231 ≈ 2.41 ∗ 109 minus the number of addresses needed to define networks and broadcasts with ...
... With the constantly growing Internet, globally valid addresses of the IP version 4 addressing scheme are on their way to get a scarce resource. Although the total number of available addresses is huge—nearly 231 ≈ 2.41 ∗ 109 minus the number of addresses needed to define networks and broadcasts with ...
Network Measurement
... Depends on what interval you use!! Traffic may be self-similar: bursts exist across a wide range of time scales Defining burstiness (precisely) is difficult ...
... Depends on what interval you use!! Traffic may be self-similar: bursts exist across a wide range of time scales Defining burstiness (precisely) is difficult ...