Snímek 1 - UNINETT Openwiki
... – ICMP and PING are still the most important – The problem is how to monitor broken paths (routing protocol usually covers any problem) ...
... – ICMP and PING are still the most important – The problem is how to monitor broken paths (routing protocol usually covers any problem) ...
CS4514 Course Objectives
... Preliminary Definitions computer network :: [Tanenbaum] a collection of “autonomous” computers interconnected by a single technology. [LG&W] communications network ::a set of equipment and facilities that provide a service. ...
... Preliminary Definitions computer network :: [Tanenbaum] a collection of “autonomous” computers interconnected by a single technology. [LG&W] communications network ::a set of equipment and facilities that provide a service. ...
Week6LectureNote
... connected networks. • If the entry was not in the table, Router C would need to send a query out fa0/0 that says, “What is the MAC address for this IP address?” • Host Y would send back a reply that says, “This is the MAC address that matches the IP Address you sent.” CCNA1-50 ...
... connected networks. • If the entry was not in the table, Router C would need to send a query out fa0/0 that says, “What is the MAC address for this IP address?” • Host Y would send back a reply that says, “This is the MAC address that matches the IP Address you sent.” CCNA1-50 ...
ECE544 - WINLAB
... – concept of multiple “logical IP subnets” (LIS) • Divided a large ATM into a number of LISs connected by routers ...
... – concept of multiple “logical IP subnets” (LIS) • Divided a large ATM into a number of LISs connected by routers ...
milcom 2004 - Institute for Human and Machine Cognition
... minimum QoS capabilities as necessary. The middleware benefits from lower level information such as the set of neighbor nodes, the link quality and reliability to each neighbor. This information can be used by the middleware, for instance, to identify candidate peer nodes for service deployment or t ...
... minimum QoS capabilities as necessary. The middleware benefits from lower level information such as the set of neighbor nodes, the link quality and reliability to each neighbor. This information can be used by the middleware, for instance, to identify candidate peer nodes for service deployment or t ...
Chapter 7—packet
... transfer of information between users, not too much different • But from internal view, very different: – A broadcast network (such as LANs) is small, addressing is simple, frame transferred in one hop so no routing is needed – In a packet-switching network, addressing must accommodate large-scale n ...
... transfer of information between users, not too much different • But from internal view, very different: – A broadcast network (such as LANs) is small, addressing is simple, frame transferred in one hop so no routing is needed – In a packet-switching network, addressing must accommodate large-scale n ...
1 - Cisco Support Community
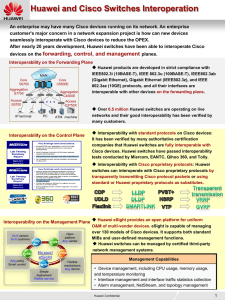
... Huawei &Cisco Interoperation Success Stories Turkey AveA's campus network project: Huawei S9700 interoperated with Cisco C6509E through OSPF and used BFD to speed up OSPF convergence. Huawei S5700 and Cisco 3560 ran VRRP to implement redundancy protection. S5700 and Cisco 2960/3560 ran standard MST ...
... Huawei &Cisco Interoperation Success Stories Turkey AveA's campus network project: Huawei S9700 interoperated with Cisco C6509E through OSPF and used BFD to speed up OSPF convergence. Huawei S5700 and Cisco 3560 ran VRRP to implement redundancy protection. S5700 and Cisco 2960/3560 ran standard MST ...
Chapter 6_vN.2 - WordPress.com
... Apple Computers has designed a protocol suite known as AppleTalk The network components of AppleTalk are sockets, nodes, network and zones Attached Resource Computer NETwork (ARCNET), the first LAN system and supports up to 255 nodes The different types of devices used in ARCnet are, active hub, pas ...
... Apple Computers has designed a protocol suite known as AppleTalk The network components of AppleTalk are sockets, nodes, network and zones Attached Resource Computer NETwork (ARCNET), the first LAN system and supports up to 255 nodes The different types of devices used in ARCnet are, active hub, pas ...
Redundant Network Architecture
... Load sharing can be a powerful redundancy technique, since it provides an alternate path should a router/path ...
... Load sharing can be a powerful redundancy technique, since it provides an alternate path should a router/path ...
DHCP snooping
... Rogue DHCP Server Set up a rogue DHCP server serving clients with false details E.g. giving them its own IP as default router Result in all the traffic passing through the attacker’s computer ...
... Rogue DHCP Server Set up a rogue DHCP server serving clients with false details E.g. giving them its own IP as default router Result in all the traffic passing through the attacker’s computer ...
ppt
... Each packet is passed through the network from node to node along some path (Routing) At each node the entire packet is received, stored briefly, and then forwarded to the next node (Store-and-Forward Networks) Typically no capacity is allocated for packets ...
... Each packet is passed through the network from node to node along some path (Routing) At each node the entire packet is received, stored briefly, and then forwarded to the next node (Store-and-Forward Networks) Typically no capacity is allocated for packets ...
Library Operating System with Mainline Linux Network Stack
... event in time, resulting a deterministic scheduler with arbitrary kind of tasks. Timestamp in kernel (i.e., jiffies) is accordingly updated on an entry and exit of LibOS space and any time related function in kernel space like system calls, timer, or interrupts refers this value as the source. Netwo ...
... event in time, resulting a deterministic scheduler with arbitrary kind of tasks. Timestamp in kernel (i.e., jiffies) is accordingly updated on an entry and exit of LibOS space and any time related function in kernel space like system calls, timer, or interrupts refers this value as the source. Netwo ...
DC1Slides
... Number of channels is NOT scalable. For N sites there are N! channels. • Sites connected in a ring. # of channels IS scalable. (N channels for N sites) ...
... Number of channels is NOT scalable. For N sites there are N! channels. • Sites connected in a ring. # of channels IS scalable. (N channels for N sites) ...
Telecomm and Networks
... Network Switching Devices • Private branch exchange (PBX): an on-premise switching system owned or leased by a private enterprise that interconnects its telephones and provides access to the public telephone system • Bridge: a device used to connect two or more networks that use the same communicat ...
... Network Switching Devices • Private branch exchange (PBX): an on-premise switching system owned or leased by a private enterprise that interconnects its telephones and provides access to the public telephone system • Bridge: a device used to connect two or more networks that use the same communicat ...
3rd Edition: Chapter 4
... Chapter 4: outline 4.1 introduction 4.2 virtual circuit and datagram networks 4.3 what’s inside a router 4.4 IP: Internet Protocol ...
... Chapter 4: outline 4.1 introduction 4.2 virtual circuit and datagram networks 4.3 what’s inside a router 4.4 IP: Internet Protocol ...
Mobile Wireless Ad Hoc Network (MANET)
... The big topic in many research projects Far more than 50 different proposals exist The most simplest one: Flooding! Flooding is a simple routing technique in computer networks where a source or node sends packets through every outgoing link. Flooding, which is similar to broadcasting, occu ...
... The big topic in many research projects Far more than 50 different proposals exist The most simplest one: Flooding! Flooding is a simple routing technique in computer networks where a source or node sends packets through every outgoing link. Flooding, which is similar to broadcasting, occu ...
1.2 C - TRENDnet
... Compared to the conventional camera, this Video Encoder features a built-in CPU and web-based solutions that can provide a cost-effective solution to transmit the real-time high-quality video images and sounds synchronously for monitoring. The Video Encoder can be managed remotely, so that you can u ...
... Compared to the conventional camera, this Video Encoder features a built-in CPU and web-based solutions that can provide a cost-effective solution to transmit the real-time high-quality video images and sounds synchronously for monitoring. The Video Encoder can be managed remotely, so that you can u ...
Chapter 6
... • Router R1 (in Fig. 6.15) is connected to networks of 4 organizations. R1’s routing table contains 4 entries (or, routes) for these 4 networks. • In router R2’s routing table, these 4 separate route entries are aggregated into a single route entry. • As the 4 blocks of addresses for the 4 organizat ...
... • Router R1 (in Fig. 6.15) is connected to networks of 4 organizations. R1’s routing table contains 4 entries (or, routes) for these 4 networks. • In router R2’s routing table, these 4 separate route entries are aggregated into a single route entry. • As the 4 blocks of addresses for the 4 organizat ...
Test Your Tech
... EtherNet—for physical connection in a LAN TCP/IP—for Internet—transmission control protocol / internet protocol HTTP—for Web—hypertext transfer protocol ...
... EtherNet—for physical connection in a LAN TCP/IP—for Internet—transmission control protocol / internet protocol HTTP—for Web—hypertext transfer protocol ...
1 - Ohio State Computer Science and Engineering
... transfer of data. Over the past few years, it has had trouble adapting to the new generation of multimedia applications that require stringent QoS guarantees. This paper explores various new architectures that strive to provide native support for multimedia Internet traffic. IPv6 and Multiprotocol L ...
... transfer of data. Over the past few years, it has had trouble adapting to the new generation of multimedia applications that require stringent QoS guarantees. This paper explores various new architectures that strive to provide native support for multimedia Internet traffic. IPv6 and Multiprotocol L ...
Fast Channel Change
... upgrades. This enables IPTV operators to attract new subscribers and reduce churn while reaching a larger part of its existing subscriber base with a premium HD quality pay-TV service. As operators increasingly deliver their video services over IP, guaranteeing pay-TV quality is essential. The Edgew ...
... upgrades. This enables IPTV operators to attract new subscribers and reduce churn while reaching a larger part of its existing subscriber base with a premium HD quality pay-TV service. As operators increasingly deliver their video services over IP, guaranteeing pay-TV quality is essential. The Edgew ...
GComm
... Replaces point-to-point communication with group communication as the fundamental abstraction, which is provided by stacking protocol modules that have a uniform (upcall, downcall) interface Not every sort of protocol blocks make sense HCPI Stability of messages membership ...
... Replaces point-to-point communication with group communication as the fundamental abstraction, which is provided by stacking protocol modules that have a uniform (upcall, downcall) interface Not every sort of protocol blocks make sense HCPI Stability of messages membership ...