08_chapter 1
... Computer network consists of two or more autonomous computers that are linked together in order to share the resources and allow electronic communication to increase the productivity. There are two broad categories of computer networks, namely, wired networks and wireless networks. In wired networks ...
... Computer network consists of two or more autonomous computers that are linked together in order to share the resources and allow electronic communication to increase the productivity. There are two broad categories of computer networks, namely, wired networks and wireless networks. In wired networks ...
Internet Business Foundations Powerpoint
... • Server administrator – manages and maintains network servers • Network engineer – manages and maintains network infrastructure • Security manager – manages the security measures used to protect electronic data • Security analyst/consultant – determines the infrastructure required for an organizati ...
... • Server administrator – manages and maintains network servers • Network engineer – manages and maintains network infrastructure • Security manager – manages the security measures used to protect electronic data • Security analyst/consultant – determines the infrastructure required for an organizati ...
SNMP - Personal Web Pages
... a scalar object that contains a single object instance An integer value Indicates the total number of input AppleTalk packets on a router interface ...
... a scalar object that contains a single object instance An integer value Indicates the total number of input AppleTalk packets on a router interface ...
PowerPoint - University of Calgary
... do they work and what are their strengths and weaknesses • How IP addresses are used to direct information on the Internet • What are some of the domains on the Internet • How to decipher Internet addresses • What is static vs. dynamic addressing and the strengths and weaknesses of each approach • W ...
... do they work and what are their strengths and weaknesses • How IP addresses are used to direct information on the Internet • What are some of the domains on the Internet • How to decipher Internet addresses • What is static vs. dynamic addressing and the strengths and weaknesses of each approach • W ...
Internet Business Foundations Powerpoint
... • Server administrator – manages and maintains network servers • Network engineer – manages and maintains network infrastructure • Security manager – manages the security measures used to protect electronic data • Security analyst/consultant – determines the infrastructure required for an organizati ...
... • Server administrator – manages and maintains network servers • Network engineer – manages and maintains network infrastructure • Security manager – manages the security measures used to protect electronic data • Security analyst/consultant – determines the infrastructure required for an organizati ...
Reclaiming Network-wide Visibility Using Ubiquitous Endsystem Monitors Evan Cooke University of Michigan
... cols and ports that are expensive to differentiate from other traffic [9]. This is particularly notable in modern enterprise networks where many services are provided over dynamically allocated ports. As a result, collecting all the packets at an upstream router is often no longer sufficient to report ...
... cols and ports that are expensive to differentiate from other traffic [9]. This is particularly notable in modern enterprise networks where many services are provided over dynamically allocated ports. As a result, collecting all the packets at an upstream router is often no longer sufficient to report ...
Design of Shortest Path Algorithm Based on Adjacency Matrix
... Abstract— Ad-hoc networks are basically selfconfiguring networks with no backbone infrastructure and all the nodes are connected to each other through wireless links. Each device in Ad-hoc (mobile) network is free to move independently in any direction, and will therefore change its links to other d ...
... Abstract— Ad-hoc networks are basically selfconfiguring networks with no backbone infrastructure and all the nodes are connected to each other through wireless links. Each device in Ad-hoc (mobile) network is free to move independently in any direction, and will therefore change its links to other d ...
... The wast number of academic contributions to the area of ad-hoc wireless networking has left a surprisingly tiny footprint in the practical world. For once, the industry is not much smarter. The problem is that the popular and acknowledged routing schemes, as well as programmer-friendly application ...
Using Servicom GRIP over BGAN and Fleet Broadband
... If you are not already connected to the GRIP server, select FILE then CONNECT and your system will automatically log on to the server. This should show you a display with folders of the Internet radio channels that have been set up for your use The general configuration is to have a Main Control Cha ...
... If you are not already connected to the GRIP server, select FILE then CONNECT and your system will automatically log on to the server. This should show you a display with folders of the Internet radio channels that have been set up for your use The general configuration is to have a Main Control Cha ...
ID Layer for Internet of Things Based on Name
... The Veil-VIRO solution [7] introduces a uniform convergence layer on the top of the link layer to ensure connectivity for large number of heterogeneous physical devices. This convergence layer provides support for underlying networks with dynamic structure and various layer 2 technologies, including ...
... The Veil-VIRO solution [7] introduces a uniform convergence layer on the top of the link layer to ensure connectivity for large number of heterogeneous physical devices. This convergence layer provides support for underlying networks with dynamic structure and various layer 2 technologies, including ...
VLSM and CIDR 04/01/2008 Modified by Tony Chen – Chapter 6
... Classful and Classless IP Addressing For example, the networks 172.16.0.0/16, 172.17.0.0/16, 172.18.0.0/16 and 172.19.0.0/16 can be summarized as 172.16.0.0/14. –If R2 sends the 172.16.0.0 summary route without the /14 mask, R3 only knows to apply the default classful mask of /16. –In a classful ...
... Classful and Classless IP Addressing For example, the networks 172.16.0.0/16, 172.17.0.0/16, 172.18.0.0/16 and 172.19.0.0/16 can be summarized as 172.16.0.0/14. –If R2 sends the 172.16.0.0 summary route without the /14 mask, R3 only knows to apply the default classful mask of /16. –In a classful ...
Chapter 1. Introduction to Data Communications
... • Two approaches to implementing multi-switch VLANs are now in use. In one case proprietary protocols are used to envelope the Ethernet frame, which is then sent to its destination switch, where the Ethernet packet is released and sent to its destination computer. • The other approach is to modify t ...
... • Two approaches to implementing multi-switch VLANs are now in use. In one case proprietary protocols are used to envelope the Ethernet frame, which is then sent to its destination switch, where the Ethernet packet is released and sent to its destination computer. • The other approach is to modify t ...
PPT Version
... mobile node, to the HoA address, and you ranged it into a "generic issue" because it can apply to a fixed node with multiple interfaces, right? I think this is a problem in which SHIM6 is qualified (how to change the locator, but not the identifier). I agree that our text in draftmontavont should be ...
... mobile node, to the HoA address, and you ranged it into a "generic issue" because it can apply to a fixed node with multiple interfaces, right? I think this is a problem in which SHIM6 is qualified (how to change the locator, but not the identifier). I agree that our text in draftmontavont should be ...
docx 152851_networking
... This is achieved by making to be switching and high-speed. Also, no manipulation of packets is done here to avoid slowing them down. It is the distribution layer that acts as separator between the core layer and the access layer. This serves to differentiate between services done on the access layer ...
... This is achieved by making to be switching and high-speed. Also, no manipulation of packets is done here to avoid slowing them down. It is the distribution layer that acts as separator between the core layer and the access layer. This serves to differentiate between services done on the access layer ...
installation manual
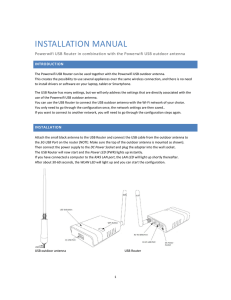
... selected network should be stated as “None”. In such a situation you don’t fill a password during configuration of the router in the next step but you will continue with Next immediately. After you’ve properly configured the USB router you should automatically be redirected to the Hotspot login page ...
... selected network should be stated as “None”. In such a situation you don’t fill a password during configuration of the router in the next step but you will continue with Next immediately. After you’ve properly configured the USB router you should automatically be redirected to the Hotspot login page ...
Managing Ad Hoc Networks of Smartphones
... Anzaldi is an example of this approach on Android OS [7]. It is a standalone Android application and does not provide any API for third party applications to use it. Ad hoc on Android aims to implement an ad hoc networking library that can be included in Android applications [8]. The implementation ...
... Anzaldi is an example of this approach on Android OS [7]. It is a standalone Android application and does not provide any API for third party applications to use it. Ad hoc on Android aims to implement an ad hoc networking library that can be included in Android applications [8]. The implementation ...
Chapter8 Phase3: Gaining Access Using Network Attacks
... Attacker interacts with targeted trusting server to determine predictability of initial sequence number Attacker launches a denial-of-service attack (eg. SYN flood or smurf attack) against trusted system to force it not to respond to a spoofed TCP connection Attacker rsh to targeted trusting server ...
... Attacker interacts with targeted trusting server to determine predictability of initial sequence number Attacker launches a denial-of-service attack (eg. SYN flood or smurf attack) against trusted system to force it not to respond to a spoofed TCP connection Attacker rsh to targeted trusting server ...
Slide 1
... must be able to scale to billions of nodes and users must be able to adapt to diverse and dynamic network conditions. must be secure and highly available should require minimal human configuration and management ...
... must be able to scale to billions of nodes and users must be able to adapt to diverse and dynamic network conditions. must be secure and highly available should require minimal human configuration and management ...
ch07
... • Two approaches to implementing multi-switch VLANs are now in use. In one case proprietary protocols are used to envelope the Ethernet frame, which is then sent to its destination switch, where the Ethernet packet is released and sent to its destination computer. • The other approach is to modify t ...
... • Two approaches to implementing multi-switch VLANs are now in use. In one case proprietary protocols are used to envelope the Ethernet frame, which is then sent to its destination switch, where the Ethernet packet is released and sent to its destination computer. • The other approach is to modify t ...
1 - Cyber-Physical Systems Integration Group @ DGIST
... • With advances in micro-electromechanical systems (MEMS), sensor devices are getting even tinier in size and changing the traditional way of measuring human physiological parameters ...
... • With advances in micro-electromechanical systems (MEMS), sensor devices are getting even tinier in size and changing the traditional way of measuring human physiological parameters ...
Network Layer
... traditional computers with switching under direct control of CPU packet copied to system’s memory speed limited by memory bandwidth (2 bus crossings ...
... traditional computers with switching under direct control of CPU packet copied to system’s memory speed limited by memory bandwidth (2 bus crossings ...