Template
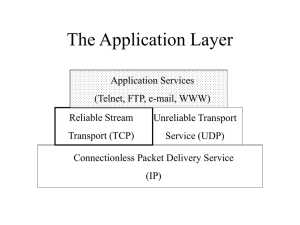
... • The source and destination addresses • For TCP and UDP—the source and destination port numbers • For ICMP—the message types ...
... • The source and destination addresses • For TCP and UDP—the source and destination port numbers • For ICMP—the message types ...
Document
... File containing user/app data (binary, text, whatever) OS does not know anything about the format ...
... File containing user/app data (binary, text, whatever) OS does not know anything about the format ...
now
... • The issue is not with the cost of the hardware, but because there is a theoretical limit of less than 1,000 VCs per link. In practice, the limit is less than that. • For this reason, larger networks are generally configured in a partial mesh topology. • With partial mesh, there are more interconne ...
... • The issue is not with the cost of the hardware, but because there is a theoretical limit of less than 1,000 VCs per link. In practice, the limit is less than that. • For this reason, larger networks are generally configured in a partial mesh topology. • With partial mesh, there are more interconne ...
A+ Guide to Managing and Maintaining Your PC, 5e
... A+ Guide to Managing and Maintaining Your PC, Fifth Edition ...
... A+ Guide to Managing and Maintaining Your PC, Fifth Edition ...
document
... • A process can use select to communicate over more than one socket at a time • Typically each socket provides a distinct service ...
... • A process can use select to communicate over more than one socket at a time • Typically each socket provides a distinct service ...
Optical Fibre Communication Systems
... the application of an electric field to an electro-optical material changes the refractive index of the material). The result is a 2x2 optical switching element whose state is determined by an electrical control signal. Can be fabricated using LiNbO3 as well as other materials. ...
... the application of an electric field to an electro-optical material changes the refractive index of the material). The result is a 2x2 optical switching element whose state is determined by an electrical control signal. Can be fabricated using LiNbO3 as well as other materials. ...
A Tool For Large Scale Network Analysis, Modeling and Visualization
... easy way to extend a tool by adding new algorithms as needed or to customize a tool so that it exactly fits the needs of a specific user (group). ...
... easy way to extend a tool by adding new algorithms as needed or to customize a tool so that it exactly fits the needs of a specific user (group). ...
Chap10_Peer-to-Peer_Team4
... The participated Hosts are fully self organizing and obtaining the data need to construct a routing table and other required state from existing members in O(log N) messages, where N is the number of hosts participating in the overlay When a node fails, the remaining nodes can detect its absence and ...
... The participated Hosts are fully self organizing and obtaining the data need to construct a routing table and other required state from existing members in O(log N) messages, where N is the number of hosts participating in the overlay When a node fails, the remaining nodes can detect its absence and ...
Multicasting
... •IP multicast packet is encapsulated in an Ethernet broadcast frame and transmitted on the bus. •Every host picks up the Ethernet frame and does filtering at the IP layer to decide whether to keep or discard the frame. •Redundant reception by many hosts. 2. Link-layer (Ethernet) multicast •Requires ...
... •IP multicast packet is encapsulated in an Ethernet broadcast frame and transmitted on the bus. •Every host picks up the Ethernet frame and does filtering at the IP layer to decide whether to keep or discard the frame. •Redundant reception by many hosts. 2. Link-layer (Ethernet) multicast •Requires ...
MA-100 Media Adaptor
... yy Wall mount yy DIN rail yy Viavi shelf yy OSP enclosure The MA-100 includes a DB-9 craft access port and a USB port that enable initial commissioning of some attributes, while other attributes are configured by and managed in-band (over the Ethernet network) by a remote EMS. ...
... yy Wall mount yy DIN rail yy Viavi shelf yy OSP enclosure The MA-100 includes a DB-9 craft access port and a USB port that enable initial commissioning of some attributes, while other attributes are configured by and managed in-band (over the Ethernet network) by a remote EMS. ...
chap_19_1
... •IP multicast packet is encapsulated in an Ethernet broadcast frame and transmitted on the bus. •Every host picks up the Ethernet frame and does filtering at the IP layer to decide whether to keep or discard the frame. •Redundant reception by many hosts. 2. Link-layer (Ethernet) multicast •Requires ...
... •IP multicast packet is encapsulated in an Ethernet broadcast frame and transmitted on the bus. •Every host picks up the Ethernet frame and does filtering at the IP layer to decide whether to keep or discard the frame. •Redundant reception by many hosts. 2. Link-layer (Ethernet) multicast •Requires ...
telecommunication and information networks the network services
... difficulties can work with firewall and network address translation systems (NAT). – Skype proposes high-quality voice codec, what allows to receive characteristics, that are compatible with traditional telephone networks, only if a Skype-client has high-speed Internet access. – In addition to voice ...
... difficulties can work with firewall and network address translation systems (NAT). – Skype proposes high-quality voice codec, what allows to receive characteristics, that are compatible with traditional telephone networks, only if a Skype-client has high-speed Internet access. – In addition to voice ...
CONEX BoF
... The purpose of the CONEX working group is to develop a mechanism to allow senders to inform the network of the level of congestion they expect their packets to encounter. This information is currently only visible at the transport layer. With the output of CONEX, it will be possible to provide suffi ...
... The purpose of the CONEX working group is to develop a mechanism to allow senders to inform the network of the level of congestion they expect their packets to encounter. This information is currently only visible at the transport layer. With the output of CONEX, it will be possible to provide suffi ...
Week 6: Course Notes
... The use of private addresses need not be unique among outside networks. Hosts that do not require access to the Internet at large may make unrestricted use of private addresses. However, the internal networks still must design network address schemes to ensure that the hosts in the private network ...
... The use of private addresses need not be unique among outside networks. Hosts that do not require access to the Internet at large may make unrestricted use of private addresses. However, the internal networks still must design network address schemes to ensure that the hosts in the private network ...
paper
... this node to the rest of the WAN. Note that these fibers may carry traffic from other transport mechanisms besides OFS (e.g., EPS). An OFS MAN node comprises an OXC with direct connections to adjacent MAN nodes as well as one or more access networks based on optical distribution network (DN) archite ...
... this node to the rest of the WAN. Note that these fibers may carry traffic from other transport mechanisms besides OFS (e.g., EPS). An OFS MAN node comprises an OXC with direct connections to adjacent MAN nodes as well as one or more access networks based on optical distribution network (DN) archite ...
SONA Enterprise Architecture Presentation
... and cross-sell opportunities) Foster technical and business relationships (bottom-up and top-down selling) Sell a system, not a product (competitive edge; remove ...
... and cross-sell opportunities) Foster technical and business relationships (bottom-up and top-down selling) Sell a system, not a product (competitive edge; remove ...
Optimizing Multiple Distributed Stream Queries Using Hierarchical Network Partitions
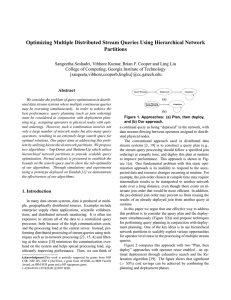
... the number of possible plan and deployment combinations can grow exponentially. The cost of considering all possibilities exhaustively is prohibitive. Consider Figure 2. With a network of 64 nodes, combining query plans and plan deployments simultaneously required us to examine 2.88 × 109 plans for ...
... the number of possible plan and deployment combinations can grow exponentially. The cost of considering all possibilities exhaustively is prohibitive. Consider Figure 2. With a network of 64 nodes, combining query plans and plan deployments simultaneously required us to examine 2.88 × 109 plans for ...
Stirling-Photonic ne.. - School of Electrical Engineering and
... Individually reserved slots (reservation requires round-trip delay between edge node and switch) Statistical multiplexing without reservation with contention for the outgoing link ...
... Individually reserved slots (reservation requires round-trip delay between edge node and switch) Statistical multiplexing without reservation with contention for the outgoing link ...
Decentralized Resource Management for a Distributed
... telecommunication infrastructure. Therefore, the network topology and the resource management middleware are the two main components that characterize a DCMS architecture. In [25], we studied the former by extending the pure hierarchy to a new topology termed Redundant Hierarchy or, briefly, RedHi ( ...
... telecommunication infrastructure. Therefore, the network topology and the resource management middleware are the two main components that characterize a DCMS architecture. In [25], we studied the former by extending the pure hierarchy to a new topology termed Redundant Hierarchy or, briefly, RedHi ( ...
Scheduler
... QoS (Quality of Service) mechanisms are becoming increasingly popular in current networks. This is mainly due to the varied type of applications (such as voice, video, real-time streaming data) concurrently using the network. These applications typically require different levels of performance in te ...
... QoS (Quality of Service) mechanisms are becoming increasingly popular in current networks. This is mainly due to the varied type of applications (such as voice, video, real-time streaming data) concurrently using the network. These applications typically require different levels of performance in te ...
McAfee Labs: Combating Aurora
... Internet Explorer vulnerability. The attack was initially targeted at several large companies, including Google. It is now public and is available on the web. The public release significantly increases the possibility of widespread attacks exploiting the vulnerability, putting Internet Explorer user ...
... Internet Explorer vulnerability. The attack was initially targeted at several large companies, including Google. It is now public and is available on the web. The public release significantly increases the possibility of widespread attacks exploiting the vulnerability, putting Internet Explorer user ...
Recursive InterNetwork Architecture (RINA)

The Recursive InterNetwork Architecture (RINA) is a computer network architecture that unifies distributed computing and telecommunications. RINA's fundamental principle is that computer networking is just Inter-Process Communication or IPC. RINA reconstructs the overall structure of the Internet, forming a model that comprises a single repeating layer, the DIF (Distributed IPC Facility), which is the minimal set of components required to allow distributed IPC between application processes. RINA inherently supports mobility, multi-homing and Quality of Service without the need for extra mechanisms, provides a secure and programmable environment, motivates for a more competitive marketplace, and allows for a seamless adoption.