IP CIP compared to other NonStop TCP/IP products – Technical
... just one network, but can run multiple TCP/IP processes and then connect the system to multiple independent networks, where the hosts on each network have routes to all other hosts in the network, but there are no routes between the networks. Each process connects to a separate network and is separa ...
... just one network, but can run multiple TCP/IP processes and then connect the system to multiple independent networks, where the hosts on each network have routes to all other hosts in the network, but there are no routes between the networks. Each process connects to a separate network and is separa ...
“Winds of Aiolos”: How connect the Greek Schools
... • The use of the advanced network services. • The formation of a flexible administrative scheme, which can ensure the minimum acceptable Quality of Service level for the education. The incorporation of Greek Schools in the “Information Society” relates with the “Operational Program for the Education ...
... • The use of the advanced network services. • The formation of a flexible administrative scheme, which can ensure the minimum acceptable Quality of Service level for the education. The incorporation of Greek Schools in the “Information Society” relates with the “Operational Program for the Education ...
PPT - EECS
... 2. Host A uses ARP to determine the LAN address for 111.111.111.002, namely 22-2222-22-22-22. 3. The adapter in A creates an Ethernet packet with destination address of 22-22-2222-22-22 4. The first router receives the packet and extracts the datagram. The forwarding table in this router indicates t ...
... 2. Host A uses ARP to determine the LAN address for 111.111.111.002, namely 22-2222-22-22-22. 3. The adapter in A creates an Ethernet packet with destination address of 22-22-2222-22-22 4. The first router receives the packet and extracts the datagram. The forwarding table in this router indicates t ...
SNMPv1 Message
... associated with it. Staring with the most abstract attributes of the object we searching for, we will begin to descend down the tree structure. The MIB “logically organizes management information in a hierarchical tree-like structure.”1 “The top-level MIB object Ids belong to different standards org ...
... associated with it. Staring with the most abstract attributes of the object we searching for, we will begin to descend down the tree structure. The MIB “logically organizes management information in a hierarchical tree-like structure.”1 “The top-level MIB object Ids belong to different standards org ...
Document
... Effects of multitasking and SCHED_RR scheduling • When the VCMTP process is running with other processes on the receiver node, packet loss may occur due to resource sharing (CPU, I/O, etc.) • Our solution: run the VCMTP process in higher priority than other processes • Linux provides support for pr ...
... Effects of multitasking and SCHED_RR scheduling • When the VCMTP process is running with other processes on the receiver node, packet loss may occur due to resource sharing (CPU, I/O, etc.) • Our solution: run the VCMTP process in higher priority than other processes • Linux provides support for pr ...
Terms of using WI-FI
... delays in the Internet network, which could have an impact on the actual transfer to and from the Terminal, b) Shall be inttled to impose on the connection time, capacity, limit of transferred data and other transmission parameters, restrict and block access to selec ...
... delays in the Internet network, which could have an impact on the actual transfer to and from the Terminal, b) Shall be inttled to impose on the connection time, capacity, limit of transferred data and other transmission parameters, restrict and block access to selec ...
IP Address - ECSE - Rensselaer Polytechnic Institute
... Recognize that destination IP address is not on same network. [1] Look up destination IP address in a (L3 forwarding) table to find a match, called the next hop router IP address. Send packet encapsulated in a LAN frame to the LAN address corresponding to the IP address of the next-hop router. ...
... Recognize that destination IP address is not on same network. [1] Look up destination IP address in a (L3 forwarding) table to find a match, called the next hop router IP address. Send packet encapsulated in a LAN frame to the LAN address corresponding to the IP address of the next-hop router. ...
Cloud Computing and Fog Computing
... and independent evolution. These worlds are very different from each other and, even better, their characteristics are often complementary. ...
... and independent evolution. These worlds are very different from each other and, even better, their characteristics are often complementary. ...
www2004.org
... which block is to be fetched from which neighbor. A simple scheduling algorithm is given as below, where the demanded blocks is transferred from the neighbors in a round-robin fashion. This enables balanced data delivery among the neighbors. Moreover, during streaming, a node should also notify all ...
... which block is to be fetched from which neighbor. A simple scheduling algorithm is given as below, where the demanded blocks is transferred from the neighbors in a round-robin fashion. This enables balanced data delivery among the neighbors. Moreover, during streaming, a node should also notify all ...
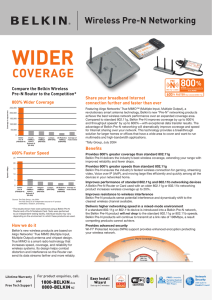
coverage
... Source: The Tolly Group, July 2004. The Tolly Group is an independent source for IT product certification, research, and testing. ...
... Source: The Tolly Group, July 2004. The Tolly Group is an independent source for IT product certification, research, and testing. ...
LANMAR: Landmark Routing for Large Scale Wireless Ad Hoc
... to know in advance the quality of the path (e.g., bandwidth, delay, etc) prior to call setup. Such a priori knowledge (which can be easily obtained from proactive schemes) is very desirable in multimedia applications, as it enables effective call acceptance control without probing the network each t ...
... to know in advance the quality of the path (e.g., bandwidth, delay, etc) prior to call setup. Such a priori knowledge (which can be easily obtained from proactive schemes) is very desirable in multimedia applications, as it enables effective call acceptance control without probing the network each t ...
ppt
... Slice: a set of d vservers, each on a different node A node can concurrently support many slices (experiments) Figure 3-15. The basic organization of a PlanetLab node. Tanenbaum & Van Steen, Distributed Systems: Principles and Paradigms, 2e, (c) 2007 Prentice-Hall, Inc. All rights reserved. 0-13-239 ...
... Slice: a set of d vservers, each on a different node A node can concurrently support many slices (experiments) Figure 3-15. The basic organization of a PlanetLab node. Tanenbaum & Van Steen, Distributed Systems: Principles and Paradigms, 2e, (c) 2007 Prentice-Hall, Inc. All rights reserved. 0-13-239 ...
IP_2
... • Inter-AS: admin wants control over how its traffic routed, who routes through its net. • Intra-AS: single admin, so no policy decisions needed ...
... • Inter-AS: admin wants control over how its traffic routed, who routes through its net. • Intra-AS: single admin, so no policy decisions needed ...
Network coding for data dissemination: it is not what you
... this approach has the advantage that more devices can be reached and that those missing information are now closer to the source, which in turn will lead to lower packet loss probability. This scheme will perform as well as or better than the Base Station Centered scheme . • Greater Impact at each t ...
... this approach has the advantage that more devices can be reached and that those missing information are now closer to the source, which in turn will lead to lower packet loss probability. This scheme will perform as well as or better than the Base Station Centered scheme . • Greater Impact at each t ...
Class Extra Switching, etc for
... • Query is sent to LAN’s broadcast MAC address • Each host or router has an ARP table – Checks IP address of query against its IP address – Replies with ARP address if there is a match Potential problems with this approach? ...
... • Query is sent to LAN’s broadcast MAC address • Each host or router has an ARP table – Checks IP address of query against its IP address – Replies with ARP address if there is a match Potential problems with this approach? ...
Chapter 1: A First Look at Windows 2000 Professional
... In a network with multiple paths, router determines best path for packet to take to reach destination RIP protocol lets routers learn and advertise paths available to them Brouters incorporate best functions of bridges and routers Gateways are most intricate networking devices ...
... In a network with multiple paths, router determines best path for packet to take to reach destination RIP protocol lets routers learn and advertise paths available to them Brouters incorporate best functions of bridges and routers Gateways are most intricate networking devices ...
two-graph building interior representation for
... Any graph algorithm may be applied on the network presented in the previous section. In this research, for the sake of presentation clarity, we use a simple path-finding algorithm – Dijkstra’s algorithm – but other, more efficient algorithms can be readily implemented. The standard Dijkstra’s algori ...
... Any graph algorithm may be applied on the network presented in the previous section. In this research, for the sake of presentation clarity, we use a simple path-finding algorithm – Dijkstra’s algorithm – but other, more efficient algorithms can be readily implemented. The standard Dijkstra’s algori ...
Spacecraft Onboard Interface Systems—Low Data
... operational working environments, and the long-term reliability of the spacecraft. These data are also highly significant when compiling lessons learned that will be applied to building better space systems and increasing the reliability of future space components. (Refer to reference [3] for a comp ...
... operational working environments, and the long-term reliability of the spacecraft. These data are also highly significant when compiling lessons learned that will be applied to building better space systems and increasing the reliability of future space components. (Refer to reference [3] for a comp ...
COMNET III: A Network Simulation Laboratory Environment For A
... computers in end systems. The Router Node models routers, hubs, and switches. The ATM Switch Node is used for routing traffic. Unlike the C&C and Router nodes, this node cannot be a source or sink for traffic. The library of link objects include two classes: pointto-point links that represent a cha ...
... computers in end systems. The Router Node models routers, hubs, and switches. The ATM Switch Node is used for routing traffic. Unlike the C&C and Router nodes, this node cannot be a source or sink for traffic. The library of link objects include two classes: pointto-point links that represent a cha ...
V4VSockets: low-overhead intra
... In the HPC context, applications often scale to a large number of nodes, leading to the need for a high-performance interconnect to provide low-latency and high-bandwidth communication. In the cloud context, distributed applications are executed in a set of Virtual Machines (VMs) that are placed in ...
... In the HPC context, applications often scale to a large number of nodes, leading to the need for a high-performance interconnect to provide low-latency and high-bandwidth communication. In the cloud context, distributed applications are executed in a set of Virtual Machines (VMs) that are placed in ...
Ch11
... 11-7 DISTANCE VECTOR ROUTING Distance vector and link state routing are both interior routing protocols. They can be used inside an autonomous system. Both of these routing protocols become intractable when the domain of operation becomes large. Distance vector routing is subject to instability if ...
... 11-7 DISTANCE VECTOR ROUTING Distance vector and link state routing are both interior routing protocols. They can be used inside an autonomous system. Both of these routing protocols become intractable when the domain of operation becomes large. Distance vector routing is subject to instability if ...
Cluster Booting Issues
... If you want to use a network to provide configuration information for a node, then you better have a network card (NIC). Since you must have a network card, it seems reasonable to put the PXE client on the network card, and have the bios treat network cards as a bootable device. ...
... If you want to use a network to provide configuration information for a node, then you better have a network card (NIC). Since you must have a network card, it seems reasonable to put the PXE client on the network card, and have the bios treat network cards as a bootable device. ...
L19
... • Flexibility: Client IPs can be scattered throughout dark space within a large /8 – Same sender usually returns with different IP addresses ...
... • Flexibility: Client IPs can be scattered throughout dark space within a large /8 – Same sender usually returns with different IP addresses ...
Recursive InterNetwork Architecture (RINA)

The Recursive InterNetwork Architecture (RINA) is a computer network architecture that unifies distributed computing and telecommunications. RINA's fundamental principle is that computer networking is just Inter-Process Communication or IPC. RINA reconstructs the overall structure of the Internet, forming a model that comprises a single repeating layer, the DIF (Distributed IPC Facility), which is the minimal set of components required to allow distributed IPC between application processes. RINA inherently supports mobility, multi-homing and Quality of Service without the need for extra mechanisms, provides a secure and programmable environment, motivates for a more competitive marketplace, and allows for a seamless adoption.