Full Text - MECS Publisher
... IMS adopted the Policy based QOS model proposed by IETF RFC [7] to provide the Quality of services for its UMTS based IMS network. The Policy based network is based on two elements, the Policy Decision Point (PDP) and the Policy Enforcement Point (PEP). The role of PEP is to enforce that only author ...
... IMS adopted the Policy based QOS model proposed by IETF RFC [7] to provide the Quality of services for its UMTS based IMS network. The Policy based network is based on two elements, the Policy Decision Point (PDP) and the Policy Enforcement Point (PEP). The role of PEP is to enforce that only author ...
Power Control in Ad
... Figure 1 to broadcast at 30mW to send a packet to the neighboring N2, since N2 is within range even at 1mW. Thus it can save on battery power. For the second point, suppose that in the same figure, N3 also wishes to broadcast a packet at the same time to N4 at 1mW. If N1 broadcasts at 1mW to N2, the ...
... Figure 1 to broadcast at 30mW to send a packet to the neighboring N2, since N2 is within range even at 1mW. Thus it can save on battery power. For the second point, suppose that in the same figure, N3 also wishes to broadcast a packet at the same time to N4 at 1mW. If N1 broadcasts at 1mW to N2, the ...
QoS Guarantee in Wirless Network
... A node forwards the updates emanating from source u only for links (u,v) such that node v is not a leaf of the broadcast tree rooted at node u, i.e., such that children(u) is nonempty. A node reports only updates for links in the node’s source tree (consisting of min-hop paths to all other nodes). T ...
... A node forwards the updates emanating from source u only for links (u,v) such that node v is not a leaf of the broadcast tree rooted at node u, i.e., such that children(u) is nonempty. A node reports only updates for links in the node’s source tree (consisting of min-hop paths to all other nodes). T ...
Visual Mining of Multi-Modal Social Networks at Different Abstraction
... visualization clarity and prior to running an expensive graph mining algorithm for evaluation and prediction. For example, the user may choose to display nodes having a specific descriptive attribute value, thereby potentially reducing the number of relevant nodes and edges by one or more orders of ...
... visualization clarity and prior to running an expensive graph mining algorithm for evaluation and prediction. For example, the user may choose to display nodes having a specific descriptive attribute value, thereby potentially reducing the number of relevant nodes and edges by one or more orders of ...
Lecture 7: Distributed Operating Systems
... A site determines whether another message is currently being transmitted over that link. If two or more sites begin transmitting at exactly the same time, time then they will register a CD and will stop transmitting. ...
... A site determines whether another message is currently being transmitted over that link. If two or more sites begin transmitting at exactly the same time, time then they will register a CD and will stop transmitting. ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... controls the congestion packets in a sub-network. Devices that are assigned to this task are called routers. A router is a device that works at layer3 which is responsible for sending datagrams from one network to another network directly connected, and it is in charge of interpreting the routing pr ...
... controls the congestion packets in a sub-network. Devices that are assigned to this task are called routers. A router is a device that works at layer3 which is responsible for sending datagrams from one network to another network directly connected, and it is in charge of interpreting the routing pr ...
Optical Networking Leader Supports IEEE Standard PBB
... on software-simple elements – that have allowed service providers to build profitable, scalable network businesses. The end result is an efficient solution that aggregates and transports Ethernet connections to core IP/MPLS/VPLS networks while simultaneously supporting native E-Line services.” Fujit ...
... on software-simple elements – that have allowed service providers to build profitable, scalable network businesses. The end result is an efficient solution that aggregates and transports Ethernet connections to core IP/MPLS/VPLS networks while simultaneously supporting native E-Line services.” Fujit ...
R. Bruno, M. Conti, E. Gregori, “Traffic Integration in Personal, Local
... interface is a standard interface that enables high-layer protocols to access the services provided by the Bluetooth device. The L2CAP services are used only for data transmissions. The main features supported by L2CAP are: protocol multiplexing (the L2CAP uses a protocol-type field to distinguish b ...
... interface is a standard interface that enables high-layer protocols to access the services provided by the Bluetooth device. The L2CAP services are used only for data transmissions. The main features supported by L2CAP are: protocol multiplexing (the L2CAP uses a protocol-type field to distinguish b ...
Chord: A Scalable Peer-to-peer Lookup Service for Internet
... underlying IP path latency Several optimizations to reduce lookup latency also improve robustness in terms of routing and data availability Approach: reduce the path length, reduce the per-hop latency, and add load balancing Simulated CAN design on Transit-Stub (TS) topologies using the ...
... underlying IP path latency Several optimizations to reduce lookup latency also improve robustness in terms of routing and data availability Approach: reduce the path length, reduce the per-hop latency, and add load balancing Simulated CAN design on Transit-Stub (TS) topologies using the ...
Network Layer
... NAT: Network Address Translation Implementation: NAT router must: - outgoing datagrams: replace (source IP address, port #) of every outgoing datagram to (NAT IP address, new port #) ...
... NAT: Network Address Translation Implementation: NAT router must: - outgoing datagrams: replace (source IP address, port #) of every outgoing datagram to (NAT IP address, new port #) ...
Network Automation and Orchestration
... provisioning the network is not only time-consuming, but also error-prone. This initial process can clearly benefit from automation where switches are able to download the correct image and configuration as soon as they are racked, stacked and powered on. • Management: Once a switch is provisioned, ...
... provisioning the network is not only time-consuming, but also error-prone. This initial process can clearly benefit from automation where switches are able to download the correct image and configuration as soon as they are racked, stacked and powered on. • Management: Once a switch is provisioned, ...
Real firewall rule-bases have a large degree of structure
... so that filtering decisions would not only be based on administrator-defined rules, but also on context that has been built by previous connections as well as previous packets belonging to the same connection. The most CPU intensive checking is performed at the time of setup of the connection. Entri ...
... so that filtering decisions would not only be based on administrator-defined rules, but also on context that has been built by previous connections as well as previous packets belonging to the same connection. The most CPU intensive checking is performed at the time of setup of the connection. Entri ...
Dynamic Time-domain Duplexing for Self
... duplexing schedule and utility for that subtree. The procedure operates recursively, where at each level of the tree, it attempts to allocate additional subframes in either the DL and UL (by switching the TX/RX mode of nodes at that level) and calling the inner optimizer, here denoted as Opt(), to t ...
... duplexing schedule and utility for that subtree. The procedure operates recursively, where at each level of the tree, it attempts to allocate additional subframes in either the DL and UL (by switching the TX/RX mode of nodes at that level) and calling the inner optimizer, here denoted as Opt(), to t ...
MCi250 Quick Start Guide
... the information you need below. Next, you will be asked to enter – the IP address for the Streamium – the netmask: Make sure all computers in your network as well as the Streamium have the same netmask. If you are not sure, try 255.255.255.000. – Default Gateway: The “IP address” of your router – tw ...
... the information you need below. Next, you will be asked to enter – the IP address for the Streamium – the netmask: Make sure all computers in your network as well as the Streamium have the same netmask. If you are not sure, try 255.255.255.000. – Default Gateway: The “IP address” of your router – tw ...
Notes for Lecture 10
... Packets from several sources can share a single channel Each sender/receiver pair appears to have a channel to itself Receiving computer can process an entire block of data instead of a character or byte at a time Simplifies synchronization of the sending and receiving systems by providing c ...
... Packets from several sources can share a single channel Each sender/receiver pair appears to have a channel to itself Receiving computer can process an entire block of data instead of a character or byte at a time Simplifies synchronization of the sending and receiving systems by providing c ...
Chapter 12: Networks and Data Communications
... Packets from several sources can share a single channel Each sender/receiver pair appears to have a channel to itself Receiving computer can process an entire block of data instead of a character or byte at a time Simplifies synchronization of the sending and receiving systems by providing c ...
... Packets from several sources can share a single channel Each sender/receiver pair appears to have a channel to itself Receiving computer can process an entire block of data instead of a character or byte at a time Simplifies synchronization of the sending and receiving systems by providing c ...
Data Centric, Position-Based Routing In Space Networks
... This paper tries to solve the communication difficulties in space network by emphasizing the data-centric and positionbased routing approach. The data to be communicated between the earth and the Mars is only the telemetry type. Also didn’t address the issues of real time and bulk load (picture, vid ...
... This paper tries to solve the communication difficulties in space network by emphasizing the data-centric and positionbased routing approach. The data to be communicated between the earth and the Mars is only the telemetry type. Also didn’t address the issues of real time and bulk load (picture, vid ...
IntServ, DiffServ, RSVP
... inefficient use of bandwidth if one of the flows does not use its allocation. • PRINCIPLE 3: While providing isolation, it is desirable to use resources as efficiently as possible. ...
... inefficient use of bandwidth if one of the flows does not use its allocation. • PRINCIPLE 3: While providing isolation, it is desirable to use resources as efficiently as possible. ...
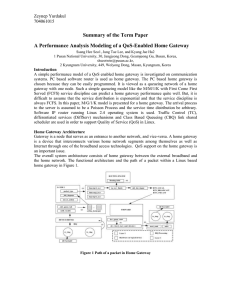
A performance analysis modeling of a QoS
... 4. The destination IP address is extracted and the route cache is inspected. If the entry is not present in cache, a look up is performed in the routing table. The next hop information is recorded in the structure. 5. According to the routing decision, the forwarder is then queued to the correct out ...
... 4. The destination IP address is extracted and the route cache is inspected. If the entry is not present in cache, a look up is performed in the routing table. The next hop information is recorded in the structure. 5. According to the routing decision, the forwarder is then queued to the correct out ...
Ipv6 addressing
... Global unicast- like a reg. IPv4 public address Link-local- stays within LAN; not routable Loopback- tests your NIC/if IP is working; ::1 Unique local- like NAT, unroutable ...
... Global unicast- like a reg. IPv4 public address Link-local- stays within LAN; not routable Loopback- tests your NIC/if IP is working; ::1 Unique local- like NAT, unroutable ...
A Review on Routing Information Protocol (RIP) and Open Shortest
... On the network the communication through a huge number of IP address can be work. The communication of distributing information from one single computer to another computer from different networks. The invention of protocols provides the better communication at long distances. The traffic request of ...
... On the network the communication through a huge number of IP address can be work. The communication of distributing information from one single computer to another computer from different networks. The invention of protocols provides the better communication at long distances. The traffic request of ...
Networking Topologies - Edupedia Publications
... ABSTRACTA computer network consists of two or more computers that are linked in order to share resources exchange files, or allow electronic communications. Now in real life scenario several networks with different protocols and architectures are need to be Interconnected for efficient communication ...
... ABSTRACTA computer network consists of two or more computers that are linked in order to share resources exchange files, or allow electronic communications. Now in real life scenario several networks with different protocols and architectures are need to be Interconnected for efficient communication ...
Review Strategies and Analysis of Mobile Ad Hoc
... addressing scheme used in the Internet, MANETs have a completely flat addressing model. In fact, Ad Hoc routing protocol such as AODV does not employ the concept of IP subnet. They assume that a node in a MANET may use any IP address provided that it is not duplicated. In fact, Ad Hoc routing protoc ...
... addressing scheme used in the Internet, MANETs have a completely flat addressing model. In fact, Ad Hoc routing protocol such as AODV does not employ the concept of IP subnet. They assume that a node in a MANET may use any IP address provided that it is not duplicated. In fact, Ad Hoc routing protoc ...
Recursive InterNetwork Architecture (RINA)

The Recursive InterNetwork Architecture (RINA) is a computer network architecture that unifies distributed computing and telecommunications. RINA's fundamental principle is that computer networking is just Inter-Process Communication or IPC. RINA reconstructs the overall structure of the Internet, forming a model that comprises a single repeating layer, the DIF (Distributed IPC Facility), which is the minimal set of components required to allow distributed IPC between application processes. RINA inherently supports mobility, multi-homing and Quality of Service without the need for extra mechanisms, provides a secure and programmable environment, motivates for a more competitive marketplace, and allows for a seamless adoption.