PicOS Overview WHITEPAPER
... accordingly. The vASIC manages the forwarding path—anything that needs to touch every packet—and provides APIs for the higher level to access. The goal is for almost all of the higher-level code to be agnostic as to the details of the forwarding path. For user-level routing protocols, we’ve develope ...
... accordingly. The vASIC manages the forwarding path—anything that needs to touch every packet—and provides APIs for the higher level to access. The goal is for almost all of the higher-level code to be agnostic as to the details of the forwarding path. For user-level routing protocols, we’ve develope ...
Guide to Firewalls and Network Security with Intrusion Detection and
... packets of information based on criteria such as port, IP address, and protocol Review the header, strip it off, and replace it with a new header before sending it to a specific location within the network Fundamental components of firewalls ...
... packets of information based on criteria such as port, IP address, and protocol Review the header, strip it off, and replace it with a new header before sending it to a specific location within the network Fundamental components of firewalls ...
Routing and Forwarding
... Introduction Network resources - link bandwidth and buffer space at routers Resource allocation - process by with network elements effectively and fairly allocates their resources for the competing traffic flows Overprovisiong - is not practically possible Evaluating resource allocation mechanisms E ...
... Introduction Network resources - link bandwidth and buffer space at routers Resource allocation - process by with network elements effectively and fairly allocates their resources for the competing traffic flows Overprovisiong - is not practically possible Evaluating resource allocation mechanisms E ...
ISP Help Desk - Metcalfe County Schools
... conversation from a customer with a computer or network issue (you decide the issue and how complex you want it to be) and both level 1 and level 2 ISP technicians. Include suggestions, processes, test and other measures that might be recommended by the technician to fix the problem. After the scrip ...
... conversation from a customer with a computer or network issue (you decide the issue and how complex you want it to be) and both level 1 and level 2 ISP technicians. Include suggestions, processes, test and other measures that might be recommended by the technician to fix the problem. After the scrip ...
Internet Multimedia Architecture
... – Network server - a proxy request to another server can “fork” request to multiple servers, creating a search tree ...
... – Network server - a proxy request to another server can “fork” request to multiple servers, creating a search tree ...
Chapter 18 - Personal.kent.edu
... Disconnect cable modem or DSL modem from host Connect host computer to the router Connect network computers to the router Optional switch/hub provides multiple ports Plug in router and power on Sign in to router utility using a default password ...
... Disconnect cable modem or DSL modem from host Connect host computer to the router Connect network computers to the router Optional switch/hub provides multiple ports Plug in router and power on Sign in to router utility using a default password ...
What is a Firewall
... •Check Point has developed Content Vectoring Protocol (CVP), which defines how a firewall forwards packets and data to specialized servers •An administrator can configure and monitor Firewall-1 on the firewall itself or from anywhere on the network •Any unauthorized use can trigger a visible or audi ...
... •Check Point has developed Content Vectoring Protocol (CVP), which defines how a firewall forwards packets and data to specialized servers •An administrator can configure and monitor Firewall-1 on the firewall itself or from anywhere on the network •Any unauthorized use can trigger a visible or audi ...
RCS Network Injector
... on the same network under monitor, to be able to reach the Target with its own IP address, since the packets will be injected with the same IP address of the Target as identified on the monitor link. NOTE ...
... on the same network under monitor, to be able to reach the Target with its own IP address, since the packets will be injected with the same IP address of the Target as identified on the monitor link. NOTE ...
wi-Five-O - Ohio State ECE
... • Hardwiring all smoke alarms together • Current Market – Single product available (Europe Only) – Prototype design based on ZigBee protocol – Strong product demand in existing homes wi Five-O ...
... • Hardwiring all smoke alarms together • Current Market – Single product available (Europe Only) – Prototype design based on ZigBee protocol – Strong product demand in existing homes wi Five-O ...
TCP/IP Protocol Suite
... Ethernet on Network 1 to token-ring on Network 2, the Layer 3 addressing for source and destination remains the same. In the Figure, the destination address remains Network 2, Host 5, regardless of the different lower-layer encapsulations. ...
... Ethernet on Network 1 to token-ring on Network 2, the Layer 3 addressing for source and destination remains the same. In the Figure, the destination address remains Network 2, Host 5, regardless of the different lower-layer encapsulations. ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... microcontroller and a CS8900A Ethernet chip from Crystal Semiconductor Corp. As a starting point for the firmware developed for this platform we used the basic TCP/IP implementation provided by TI and extended its capabilities to allow two-way communication. This solution is fully functional, but th ...
... microcontroller and a CS8900A Ethernet chip from Crystal Semiconductor Corp. As a starting point for the firmware developed for this platform we used the basic TCP/IP implementation provided by TI and extended its capabilities to allow two-way communication. This solution is fully functional, but th ...
Chapter 9: Applications
... – Type = A: indicates that the Value is an IP address. » Thus, A records implement the name-to-address mapping – Type =NS: The Value field gives the domain name for a host that is running a name server that knows how to resolve names within the specified domain. – Type= CNAME: The Value field gives ...
... – Type = A: indicates that the Value is an IP address. » Thus, A records implement the name-to-address mapping – Type =NS: The Value field gives the domain name for a host that is running a name server that knows how to resolve names within the specified domain. – Type= CNAME: The Value field gives ...
CS 291 Special Topics on Network Security
... Architecture (Layer); Algorithm; Protocol Why it is built this way? Is it good/the best to build it this way? What if I build it? Network Usage, Management, Analysis How to use the networking service? Application Development Existing Network Applications/Tools ...
... Architecture (Layer); Algorithm; Protocol Why it is built this way? Is it good/the best to build it this way? What if I build it? Network Usage, Management, Analysis How to use the networking service? Application Development Existing Network Applications/Tools ...
IP Address
... • CIDR slows down the growth of routing tables (current 130K entries in core routers) • Short term solution to solve routing problem • limitation: not all host/router software allows supernet mask ...
... • CIDR slows down the growth of routing tables (current 130K entries in core routers) • Short term solution to solve routing problem • limitation: not all host/router software allows supernet mask ...
IEEE C802.16ppc-10/0055r1 Project Title
... The analysis shown in the previous sections indicate the need for a significant reduction in signaling and protocol overhead incurred by M2M devices attempting to send short bursts of data while being forced to reside in the idle state. We suggest that the following functional requirements be added ...
... The analysis shown in the previous sections indicate the need for a significant reduction in signaling and protocol overhead incurred by M2M devices attempting to send short bursts of data while being forced to reside in the idle state. We suggest that the following functional requirements be added ...
SybilGuard Overview
... – Using a permutation as the routing table further guarantees that the random routes are back-traceable ...
... – Using a permutation as the routing table further guarantees that the random routes are back-traceable ...
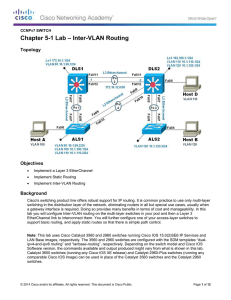
Lab 5-1 Inter-VLAN Routing
... Cisco's switching product line offers robust support for IP routing. It is common practice to use only multi-layer switching in the distribution layer of the network, eliminating routers in all but special use cases, usually when a gateway interface is required. Doing so provides many benefits in te ...
... Cisco's switching product line offers robust support for IP routing. It is common practice to use only multi-layer switching in the distribution layer of the network, eliminating routers in all but special use cases, usually when a gateway interface is required. Doing so provides many benefits in te ...
Decentralised Service Composition using Potential Fields in Internet
... 1877-0509 © 2015 The Authors. Published by Elsevier B.V. This is an open access article under the CC BY-NC-ND license (http://creativecommons.org/licenses/by-nc-nd/4.0/). Peer-review under responsibility of the Conference Program Chairs doi:10.1016/j.procs.2015.05.079 ...
... 1877-0509 © 2015 The Authors. Published by Elsevier B.V. This is an open access article under the CC BY-NC-ND license (http://creativecommons.org/licenses/by-nc-nd/4.0/). Peer-review under responsibility of the Conference Program Chairs doi:10.1016/j.procs.2015.05.079 ...
Hybrid Architectures: Accounting for Networks Exuding DTN and
... B is the first DTN node in the path from O to T. It maintains a timer that kicks off after getting the RREQ and listens for an RREP from T. If node T fails and does not send an RREP before B’s timer expires, B sends a special “DTN-Only” RREP to allow nodes to still learn the DTN overlay network. ...
... B is the first DTN node in the path from O to T. It maintains a timer that kicks off after getting the RREQ and listens for an RREP from T. If node T fails and does not send an RREP before B’s timer expires, B sends a special “DTN-Only” RREP to allow nodes to still learn the DTN overlay network. ...
Recursive InterNetwork Architecture (RINA)

The Recursive InterNetwork Architecture (RINA) is a computer network architecture that unifies distributed computing and telecommunications. RINA's fundamental principle is that computer networking is just Inter-Process Communication or IPC. RINA reconstructs the overall structure of the Internet, forming a model that comprises a single repeating layer, the DIF (Distributed IPC Facility), which is the minimal set of components required to allow distributed IPC between application processes. RINA inherently supports mobility, multi-homing and Quality of Service without the need for extra mechanisms, provides a secure and programmable environment, motivates for a more competitive marketplace, and allows for a seamless adoption.