Brief Annoucement: On Local Representation of Distances in Trees
... global information on the graph (like its matrix) can be removed. The goal is to minimize the maximum length of a label associated with a vertex while keeping fast adjacency queries. Implicit representation of graphs with short labels have been investigated by Kannan, Naor and Rudich [3] and is wide ...
... global information on the graph (like its matrix) can be removed. The goal is to minimize the maximum length of a label associated with a vertex while keeping fast adjacency queries. Implicit representation of graphs with short labels have been investigated by Kannan, Naor and Rudich [3] and is wide ...
DeltaV™ Network Time Synchronization
... Using Stratum 1 NTP Time Servers Directly Connected to the DeltaV ACN If a Stratum 1 NTP time server is installed on the ACN, then the DeltaV workstations and embedded nodes will automatically get their time from this server instead. Even the workstations that are defined as master/backup time serve ...
... Using Stratum 1 NTP Time Servers Directly Connected to the DeltaV ACN If a Stratum 1 NTP time server is installed on the ACN, then the DeltaV workstations and embedded nodes will automatically get their time from this server instead. Even the workstations that are defined as master/backup time serve ...
P2P Applications on Smart Phones using Cellular Communications
... large number of PC applications can already be downscaled. As the computing and communication capabilities of smart phones evolve, the set of potential application types widens. The rapid evolution of smart phones was our starting point when we in late 2001 started to investigate the use of P2P appl ...
... large number of PC applications can already be downscaled. As the computing and communication capabilities of smart phones evolve, the set of potential application types widens. The rapid evolution of smart phones was our starting point when we in late 2001 started to investigate the use of P2P appl ...
SDN in Wireless Cellular Networks: White Paper Technology Business Unit
... The explosive growth in devices and the corresponding increase in the need for higher bandwidth are compelling cellular service providers to look beyond traditional technologies. In addition, wireless networks have been riddled with several issues such as inter-cell interference and mobility managem ...
... The explosive growth in devices and the corresponding increase in the need for higher bandwidth are compelling cellular service providers to look beyond traditional technologies. In addition, wireless networks have been riddled with several issues such as inter-cell interference and mobility managem ...
nGenius Subscriber Intelligence
... and handset identity information that will be displayed according to the network technology under analysis. The session duration, start and end times, status, source and destination address along with failure reason are included in the session overview. ...
... and handset identity information that will be displayed according to the network technology under analysis. The session duration, start and end times, status, source and destination address along with failure reason are included in the session overview. ...
Multicasting
... hosts, and is written in the same way: A.B.C.D. – Multicast addresses will never clash with host addresses because a portion of the IP address space is specifically reserved for multicast. 224.0.0.0 to 239.255.255.255. – Multicast addresses from 224.0.0.0 to 224.0.0.255 are reserved for multicast ro ...
... hosts, and is written in the same way: A.B.C.D. – Multicast addresses will never clash with host addresses because a portion of the IP address space is specifically reserved for multicast. 224.0.0.0 to 239.255.255.255. – Multicast addresses from 224.0.0.0 to 224.0.0.255 are reserved for multicast ro ...
PresentationMobileIP
... – Has no geographical limitations – Requires no modifications to IP addresses or IP address format – Supports security • Could be even more important than physically connected routing ...
... – Has no geographical limitations – Requires no modifications to IP addresses or IP address format – Supports security • Could be even more important than physically connected routing ...
A Measurement-Based Algorithm to Maximize the Utility of Wireless
... There are some situations where wireless networks fail to achieve both efficiency and fairness. This is the case for instance when the devices have unequal channel conditions and need to use different physical modulation rates. The nodes using slower modulation rates need more time to transmit a pac ...
... There are some situations where wireless networks fail to achieve both efficiency and fairness. This is the case for instance when the devices have unequal channel conditions and need to use different physical modulation rates. The nodes using slower modulation rates need more time to transmit a pac ...
Document
... chatting between two users is P2P centralized service: client presence detection/location • user registers its IP address with central server when it comes online • user contacts central server to find IP addresses of buddies Network services ...
... chatting between two users is P2P centralized service: client presence detection/location • user registers its IP address with central server when it comes online • user contacts central server to find IP addresses of buddies Network services ...
Network architecture, operations, services info sheet
... operations and connectivity services Through the GÉANT Project (GN4-1), the GÉANT network provides the high-speed connectivity needed to share, access and process the massive volumes of data generated by research and education communities. It now reaches over 100 countries worldwide and continues to ...
... operations and connectivity services Through the GÉANT Project (GN4-1), the GÉANT network provides the high-speed connectivity needed to share, access and process the massive volumes of data generated by research and education communities. It now reaches over 100 countries worldwide and continues to ...
Establishing Mobile Ad-Hoc Networks in 802.11 Infrastructure Mode
... designated gateway or name servers in the network. Just as in one-hop Wi-Fi networks, these services are provided by the local RON, serving as the AP in this network. These services can be provided in a distributed or centralized fashion. A RON may either serve as an independent DHCP server or may s ...
... designated gateway or name servers in the network. Just as in one-hop Wi-Fi networks, these services are provided by the local RON, serving as the AP in this network. These services can be provided in a distributed or centralized fashion. A RON may either serve as an independent DHCP server or may s ...
Network+ (N10-005) Cram Notes
... APIPA (Short for Automatic Private IP Addressing), is a feature that allows DHCP clients to automatically self-configure an IP address and subnet mask when a DHCP server isn't available. When a DHCP client boots up, it first looks for a DHCP server in order to obtain an IP address and subnet mask. I ...
... APIPA (Short for Automatic Private IP Addressing), is a feature that allows DHCP clients to automatically self-configure an IP address and subnet mask when a DHCP server isn't available. When a DHCP client boots up, it first looks for a DHCP server in order to obtain an IP address and subnet mask. I ...
Document
... Potential MPLS Networks Current Design Practices and Market Forces Requirements Met by Current Designs Product Functionality by Product Constraints of Current Design ...
... Potential MPLS Networks Current Design Practices and Market Forces Requirements Met by Current Designs Product Functionality by Product Constraints of Current Design ...
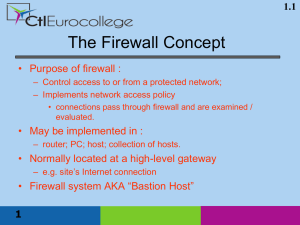
Firewall - theodoros christophides site
... Firewall Hardware • Routers – Many come equipped with basic packet-filtering capabilities; others come with fully-functioning firewalls ...
... Firewall Hardware • Routers – Many come equipped with basic packet-filtering capabilities; others come with fully-functioning firewalls ...
Efficient Micro-Mobility using Intra-domain Multicast
... We follow a different approach to IP mobility using multicast-based mobility (M&M). In such architecture, each mobile node is assigned a multicast address to which it joins through the access routers it visits during its movement. Handover is performed through standard IP-multicast join/prune mechan ...
... We follow a different approach to IP mobility using multicast-based mobility (M&M). In such architecture, each mobile node is assigned a multicast address to which it joins through the access routers it visits during its movement. Handover is performed through standard IP-multicast join/prune mechan ...
Implementing PRIME for Robust and Reliable Power Line
... smart meter deployments. These firsthand experiences are helpful for other utility companies who are currently engaged in or planning future smart grid and smart meter deployments. The model deployed in Castellon will be extended to other grids all over the world. Iberdrola continues its deployment ...
... smart meter deployments. These firsthand experiences are helpful for other utility companies who are currently engaged in or planning future smart grid and smart meter deployments. The model deployed in Castellon will be extended to other grids all over the world. Iberdrola continues its deployment ...
Guide to Firewalls and Network Security with Intrusion Detection and
... private reserved blocks not usually routable over the Internet ...
... private reserved blocks not usually routable over the Internet ...
Part I: Introduction
... and video into a single stream during the encoding process. When the audio and video are bundled by the encoder, then only one RTP stream is generated in each direction. For a many-to-many multicast session, all of the ...
... and video into a single stream during the encoding process. When the audio and video are bundled by the encoder, then only one RTP stream is generated in each direction. For a many-to-many multicast session, all of the ...
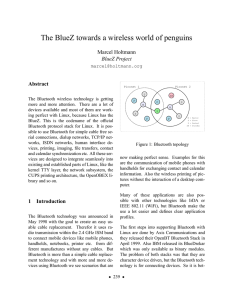
The BlueZ towards a wireless world of penguins
... into the Linux kernel as part of the network subsystem. It provides its own protocol family and uses the socket interface. This basic design makes it easy for application to adapt the Bluetooth technology and the integration is simple and straight forward. The use of different Bluetooth hardware is ...
... into the Linux kernel as part of the network subsystem. It provides its own protocol family and uses the socket interface. This basic design makes it easy for application to adapt the Bluetooth technology and the integration is simple and straight forward. The use of different Bluetooth hardware is ...
S7C9 - Multicasts
... • Use distribution centers and construct single multicast tree – Low-overhead and higher end-to-end delay – Single delivery tree shared by all group members – Devices wanting to receive traffic must explicitly join the shared delivery tree – Multicast traffic sent over same tree regardless of source ...
... • Use distribution centers and construct single multicast tree – Low-overhead and higher end-to-end delay – Single delivery tree shared by all group members – Devices wanting to receive traffic must explicitly join the shared delivery tree – Multicast traffic sent over same tree regardless of source ...
S-RIP: A Secure Distance Vector Routing Protocol
... integrity only. However, after a route update is verified to be “authentic”, the routing information conveyed in the update is trusted and used to update the recipient’s routing table. This is risky since data origin authentication, which includes data integrity [17], cannot guarantee the factual c ...
... integrity only. However, after a route update is verified to be “authentic”, the routing information conveyed in the update is trusted and used to update the recipient’s routing table. This is risky since data origin authentication, which includes data integrity [17], cannot guarantee the factual c ...
Securing Wireless Networks for HIPAA Compliance
... buildings to keep the radio waves from penetrating to the outside world 2. However, this is quite costly and requires major renovations to the physical structure. In an effort to address these issues, included in the 802.11x protocol suite is Wired Equivalent Privacy (WEP). There have been many flaw ...
... buildings to keep the radio waves from penetrating to the outside world 2. However, this is quite costly and requires major renovations to the physical structure. In an effort to address these issues, included in the 802.11x protocol suite is Wired Equivalent Privacy (WEP). There have been many flaw ...
Multiple ENUM registries will exist
... Multiple registries exist to meet the needs of multiple user-groups defined by geography, network-type, interconnect-model, etc. October 2007 ...
... Multiple registries exist to meet the needs of multiple user-groups defined by geography, network-type, interconnect-model, etc. October 2007 ...
Network Topologies
... Netmask – isolates sub-nets within a network. Gateway – a router that also translates between routing protocols like IP or Appletalk. Usually at the edge of a network it often hosts the network firewall. A default gateway is used to send any packets destined for an IP network not explicitly defined ...
... Netmask – isolates sub-nets within a network. Gateway – a router that also translates between routing protocols like IP or Appletalk. Usually at the edge of a network it often hosts the network firewall. A default gateway is used to send any packets destined for an IP network not explicitly defined ...
Recursive InterNetwork Architecture (RINA)

The Recursive InterNetwork Architecture (RINA) is a computer network architecture that unifies distributed computing and telecommunications. RINA's fundamental principle is that computer networking is just Inter-Process Communication or IPC. RINA reconstructs the overall structure of the Internet, forming a model that comprises a single repeating layer, the DIF (Distributed IPC Facility), which is the minimal set of components required to allow distributed IPC between application processes. RINA inherently supports mobility, multi-homing and Quality of Service without the need for extra mechanisms, provides a secure and programmable environment, motivates for a more competitive marketplace, and allows for a seamless adoption.