slides - SmartLab
... • Link duration is used as a mobility feedback mechanism • Neighbour establishment used to assess stability of local links • Select routing algorithm based on perceived stability – Proactive algorithm: stable enough to elect relay nodes – Reactive algorithm: in all other cases MPAC 2004 ...
... • Link duration is used as a mobility feedback mechanism • Neighbour establishment used to assess stability of local links • Select routing algorithm based on perceived stability – Proactive algorithm: stable enough to elect relay nodes – Reactive algorithm: in all other cases MPAC 2004 ...
Chapter 6 slides, Computer Networking, 3rd edition
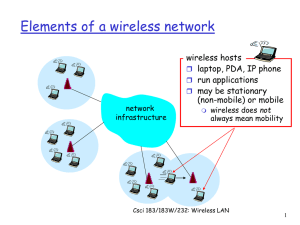
... wireless hosts laptop, PDA, IP phone run applications may be stationary (non-mobile) or mobile ...
... wireless hosts laptop, PDA, IP phone run applications may be stationary (non-mobile) or mobile ...
11-BGP
... R2 can only find these prefixes through a direct connection to R1 Result: I-BGP routers must be fully connected (via TCP)! •contrast with E-BGP sessions that map to physical links ...
... R2 can only find these prefixes through a direct connection to R1 Result: I-BGP routers must be fully connected (via TCP)! •contrast with E-BGP sessions that map to physical links ...
Pathport QUATTRO Node Spec
... 10.4 Nodes shall support industry standard ANSI E1.31 Streaming ACN. 10.5 Nodes shall also support ETCNet3, Pathport Protocol, Art-Net, and Strand ShowNet. 10.6 Nodes shall be capable of accepting DMX level data from any or all of the above named protocols simultaneously. 11.0 Management Software 11 ...
... 10.4 Nodes shall support industry standard ANSI E1.31 Streaming ACN. 10.5 Nodes shall also support ETCNet3, Pathport Protocol, Art-Net, and Strand ShowNet. 10.6 Nodes shall be capable of accepting DMX level data from any or all of the above named protocols simultaneously. 11.0 Management Software 11 ...
Chapter 5
... • Local Area Networks use multiple access protocols extensively • Ethernet is the most common random access protocol • Token Ring had a slight speed advantage, so it was popular in the late 1980’s – A node sends a frame around the network, and it’s read by the recipient node – The sender removes it ...
... • Local Area Networks use multiple access protocols extensively • Ethernet is the most common random access protocol • Token Ring had a slight speed advantage, so it was popular in the late 1980’s – A node sends a frame around the network, and it’s read by the recipient node – The sender removes it ...
TCP/IP Protocol Suite
... – An entry that is used twice in 2 minutes is automatically given a 10-minute time-to-live. ...
... – An entry that is used twice in 2 minutes is automatically given a 10-minute time-to-live. ...
l4-1 - Heyook Lab
... • Arriving packets are copied to main memory via direct memory access (DMA) • Switching fabric is a backplane (shared bus) • All IP forwarding functions are performed in the central processor. • Routing cache at processor can accelerate the routing table ...
... • Arriving packets are copied to main memory via direct memory access (DMA) • Switching fabric is a backplane (shared bus) • All IP forwarding functions are performed in the central processor. • Routing cache at processor can accelerate the routing table ...
Peer-to-Peer Systems
... HHU – Technology of Social Networks – JProf. Dr. Kalman Graffi – Peer-to-Peer Systems – http://tsn.hhu.de/teaching/lectures/2014ws/p2p.html ...
... HHU – Technology of Social Networks – JProf. Dr. Kalman Graffi – Peer-to-Peer Systems – http://tsn.hhu.de/teaching/lectures/2014ws/p2p.html ...
Addressing the Network – IPv4
... Given a diagram of a multi-layered network, address range, number of hosts in each network and the ranges for each network, create a network scheme that assigns addressing ranges to each network ...
... Given a diagram of a multi-layered network, address range, number of hosts in each network and the ranges for each network, create a network scheme that assigns addressing ranges to each network ...
Reward-based training of recurrent neural networks for cognitive
... Figure 1. Recurrent neural networks for reinforcement learning. (A) Task structure for a simple perceptual decision-making task with variable stimulus duration. The agent must maintain fixation (at ¼ F) until the go cue, which indicates the start of a decision period during which choosing the correc ...
... Figure 1. Recurrent neural networks for reinforcement learning. (A) Task structure for a simple perceptual decision-making task with variable stimulus duration. The agent must maintain fixation (at ¼ F) until the go cue, which indicates the start of a decision period during which choosing the correc ...
IP MULTICAST
... – Independence from Unicast Routing • PIM implementations do require the presence of some unicast routing protocol to provide routing table information and adapt to topology changes. ...
... – Independence from Unicast Routing • PIM implementations do require the presence of some unicast routing protocol to provide routing table information and adapt to topology changes. ...
Network Health Monitoring Overview
... Monitoring overall network health helps you to avoid or mitigate potential operational disruptions or downtime. In addition to the dashboards and dashlets that you can use to monitor various targeted aspects of the network, you can monitor and evaluate the overall health of the entire enterprise net ...
... Monitoring overall network health helps you to avoid or mitigate potential operational disruptions or downtime. In addition to the dashboards and dashlets that you can use to monitor various targeted aspects of the network, you can monitor and evaluate the overall health of the entire enterprise net ...
A Denial of Service Attack in Advanced Metering
... a 1000 meter by 1000 meter flat space. The total duration of the simulations is 400 seconds. Each data point on a graph represents the average value of 30 runs. We use packet delivery rate to indicate the performance of puppet attack. Packet delivery rate is the ratio between the number of packets or ...
... a 1000 meter by 1000 meter flat space. The total duration of the simulations is 400 seconds. Each data point on a graph represents the average value of 30 runs. We use packet delivery rate to indicate the performance of puppet attack. Packet delivery rate is the ratio between the number of packets or ...
ad hoc networks - BWN-Lab
... – limited bandwidth of the system is reduced even more due to the exchange of routing information – links can be asymmetric, i.e., they can have a direction ...
... – limited bandwidth of the system is reduced even more due to the exchange of routing information – links can be asymmetric, i.e., they can have a direction ...
MuON: Epidemic Based Mutual Anonymity
... directions, from initiator to responder and vice-versa. Finally, it describes how the message sending protocol is used for communication between the initiator and responder. ...
... directions, from initiator to responder and vice-versa. Finally, it describes how the message sending protocol is used for communication between the initiator and responder. ...
Chapter 3 review
... - overall moderate congestion: - severe congestion in some nodes - dynamics of the network/routing and overhead of protocol adaptation decreases the network Tput - severe congestion: - loss of packets and increased discards - extended delays leading to timeouts ...
... - overall moderate congestion: - severe congestion in some nodes - dynamics of the network/routing and overhead of protocol adaptation decreases the network Tput - severe congestion: - loss of packets and increased discards - extended delays leading to timeouts ...
MIHIN Convert Syndromics UCA v7 05-29-14
... Admit Discharge Transfer (ADT) means an HL7 message type used to communicate hospital admissions and discharges as well as transfers within the hospital or outside of the hospital to another healthcare facility. ADT messages are part of the Patient Administration transaction set and provide for the ...
... Admit Discharge Transfer (ADT) means an HL7 message type used to communicate hospital admissions and discharges as well as transfers within the hospital or outside of the hospital to another healthcare facility. ADT messages are part of the Patient Administration transaction set and provide for the ...
Internet
... If client first sends SYN, but does not then send ACK, this TCP connection is left hanging... SCTP uses a 4-way handshake with a signed cookie, in this way preventing DoS (Denial-of-Service) attacks like SYN flooding. ...
... If client first sends SYN, but does not then send ACK, this TCP connection is left hanging... SCTP uses a 4-way handshake with a signed cookie, in this way preventing DoS (Denial-of-Service) attacks like SYN flooding. ...
T R ECHNICAL ESEARCH
... than in QoS Routing. The routing protocol provides a route between the source and destination of the ow. The signaling mechanism provides feedback to the routing protocol regarding the route chosen and asks the routing protocol for alternate routes if the route provided doesn't satisfy the QoS requ ...
... than in QoS Routing. The routing protocol provides a route between the source and destination of the ow. The signaling mechanism provides feedback to the routing protocol regarding the route chosen and asks the routing protocol for alternate routes if the route provided doesn't satisfy the QoS requ ...
ITE PC v4.0 Chapter 1
... protocols; however, static routes can require more maintenance if the topology is constantly changing or is unstable. Dynamic routing protocols automatically adjust to changes without any intervention from the network administrator. Dynamic routing protocols require more CPU processing and also us ...
... protocols; however, static routes can require more maintenance if the topology is constantly changing or is unstable. Dynamic routing protocols automatically adjust to changes without any intervention from the network administrator. Dynamic routing protocols require more CPU processing and also us ...