ROB: Route Optimization Assisted by BGP
... ROB: Route Optimization Assisted by BGP • BGP is a highly robust and scalable routing protocol, as evidenced by its wide use in the Internet. – An entry in the BGP routing table (Network, Next Hop, Path) • Network field: the network destination address. • Next Hop field: the BR’s IP address that sh ...
... ROB: Route Optimization Assisted by BGP • BGP is a highly robust and scalable routing protocol, as evidenced by its wide use in the Internet. – An entry in the BGP routing table (Network, Next Hop, Path) • Network field: the network destination address. • Next Hop field: the BR’s IP address that sh ...
CSE331-35
... • The attacking system sends forged SYN messages to the victim server system • These appear to be legitimate but actually reference a client unable to respond to the SYN-ACK. • The source addresses in the SYN packets are forged. – No way to determine its true source. ...
... • The attacking system sends forged SYN messages to the victim server system • These appear to be legitimate but actually reference a client unable to respond to the SYN-ACK. • The source addresses in the SYN packets are forged. – No way to determine its true source. ...
Telecommunication Transmission and Switching System
... Which are made up by interconnecting Customer ...
... Which are made up by interconnecting Customer ...
04 – Future Ad Hoc Network
... • There are various factors which can differentiate wireless mesh network from Ad-hoc Network. The major differences between these two types of network are the network topology and mobility of node ...
... • There are various factors which can differentiate wireless mesh network from Ad-hoc Network. The major differences between these two types of network are the network topology and mobility of node ...
Week_Five_ppt
... hop-by-hop, individually routed packet model with a connection-oriented model that establishes ‘paths’ to destinations. Instead of routing each packet based upon its destination address, each packet is labeled such that it can be switched along a pre-defined path. In addition, MPLS defines traffic e ...
... hop-by-hop, individually routed packet model with a connection-oriented model that establishes ‘paths’ to destinations. Instead of routing each packet based upon its destination address, each packet is labeled such that it can be switched along a pre-defined path. In addition, MPLS defines traffic e ...
Chapter 3 OSI Model Worksheet In class lecture and handout.
... to another user and explain what the corresponding OSI layer does to prepare the data to be sent over the network. ...
... to another user and explain what the corresponding OSI layer does to prepare the data to be sent over the network. ...
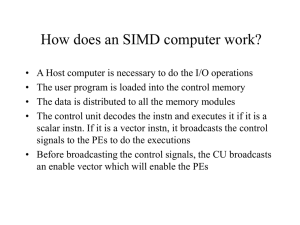
How does an SIMD computer work?
... • LDB: Local Data Buffer 64, 64-bit each • PEM: 2K X 64 bits memory ...
... • LDB: Local Data Buffer 64, 64-bit each • PEM: 2K X 64 bits memory ...
NRENs serving the Health Sector - a possibility if we go for it
... YES – We can now manage the increased complexity of the explosion of many types of connections between organizations YES – Trans-national networks can be established with preserved security YES – NRENs are able to choose to provide a broad set of services to the health care sector NO – Network inter ...
... YES – We can now manage the increased complexity of the explosion of many types of connections between organizations YES – Trans-national networks can be established with preserved security YES – NRENs are able to choose to provide a broad set of services to the health care sector NO – Network inter ...
Changes in Power System Communications
... Developed in 1978, the Open System Interconnection has 7 layers each performing part of the communications. 1) The physical level controls the physical connections between devices, network topology, voltage levels to define 0’s and 1’s.RS232, RS485, and USB are 3 examples 2) Data link level provide ...
... Developed in 1978, the Open System Interconnection has 7 layers each performing part of the communications. 1) The physical level controls the physical connections between devices, network topology, voltage levels to define 0’s and 1’s.RS232, RS485, and USB are 3 examples 2) Data link level provide ...
Intro To Networking Part B Chapter 3
... – equipment obtained from ISP through a lease – all updates, maintenance, etc. of equipment are the responsibility of the ISP –Network upgrade and maintenance costs will become predictable (no surprises). –The company will not need to spend a large amount of money to purchase the equipment upfront. ...
... – equipment obtained from ISP through a lease – all updates, maintenance, etc. of equipment are the responsibility of the ISP –Network upgrade and maintenance costs will become predictable (no surprises). –The company will not need to spend a large amount of money to purchase the equipment upfront. ...
NW PPT - Dublin City Schools
... A protocol is a set of rules that govern the connection, communication, and data transfer between computers on a network These rules include guidelines that regulate the following characteristics of a network: access method, allowed physical topologies, types of cabling, and speed of data transf ...
... A protocol is a set of rules that govern the connection, communication, and data transfer between computers on a network These rules include guidelines that regulate the following characteristics of a network: access method, allowed physical topologies, types of cabling, and speed of data transf ...
Computer Networks
... different type). They operate in the physical, data link and network layers. They contain software that enable them to determine which of the several possible paths is the best for a particular transmission. Gateways: They relay packets among networks that have different protocols (e.g. between a LA ...
... different type). They operate in the physical, data link and network layers. They contain software that enable them to determine which of the several possible paths is the best for a particular transmission. Gateways: They relay packets among networks that have different protocols (e.g. between a LA ...
A Scalable, Commodity Data Center Network Architecture
... Desired properties in a DC Architecture Fat tree based solution Monsoon: layer 2 flat routing ...
... Desired properties in a DC Architecture Fat tree based solution Monsoon: layer 2 flat routing ...
02. Network Hardware..
... • Routers can hear the output from the satellite, in some cases they can also hear the upward transmissions of other routers to the satellite • Sometimes the routers are connected to a substantial point-to-point subnet, with only some of them having a satellite antenna • Satellite networks are inher ...
... • Routers can hear the output from the satellite, in some cases they can also hear the upward transmissions of other routers to the satellite • Sometimes the routers are connected to a substantial point-to-point subnet, with only some of them having a satellite antenna • Satellite networks are inher ...
View Sample PDF - IRMA
... Information collected this way is then shared over the ALN to increase the security of all peers, which can then make the necessary protection steps, for example, blocking network traffic by their own firewall. Different kinds of security software utilizing the network were also written previously ( ...
... Information collected this way is then shared over the ALN to increase the security of all peers, which can then make the necessary protection steps, for example, blocking network traffic by their own firewall. Different kinds of security software utilizing the network were also written previously ( ...
Part II. Project Information, to be completed by the proposer (Faculty
... that filter traffic between two or more networks. Host-based firewalls provide a layer of software on one host that controls network traffic in and out of that single machine. Routers that pass data between networks contain firewall components and can often perform basic routing functions as well, F ...
... that filter traffic between two or more networks. Host-based firewalls provide a layer of software on one host that controls network traffic in and out of that single machine. Routers that pass data between networks contain firewall components and can often perform basic routing functions as well, F ...
ATC-2000 TCP/IP TO RS
... connect an Ethernet cable to 93A00-1 server (Fig 1) ■ When connecting directly to a PC, connect a crossover cable to the 93A00-1 server (Fig 2) ...
... connect an Ethernet cable to 93A00-1 server (Fig 1) ■ When connecting directly to a PC, connect a crossover cable to the 93A00-1 server (Fig 2) ...
Computer and multimedia networks (FM)
... • An end-to-end circuit must be established that is dedicated for the entire duration of the connection at a guaranteed bandwidth. • Initially designed for voice communications, ...
... • An end-to-end circuit must be established that is dedicated for the entire duration of the connection at a guaranteed bandwidth. • Initially designed for voice communications, ...
Introduction to Networking
... A protocol is a set of rules that govern the connection, communication, and data transfer between computers on a network These rules include guidelines that regulate the following characteristics of a network: access method, allowed physical topologies, types of cabling, and speed of data transf ...
... A protocol is a set of rules that govern the connection, communication, and data transfer between computers on a network These rules include guidelines that regulate the following characteristics of a network: access method, allowed physical topologies, types of cabling, and speed of data transf ...
Networking Basics - Walton County School District
... A protocol is a set of rules that govern the connection, communication, and data transfer between computers on a network These rules include guidelines that regulate the following characteristics of a network: access method, allowed physical topologies, types of cabling, and speed of data transf ...
... A protocol is a set of rules that govern the connection, communication, and data transfer between computers on a network These rules include guidelines that regulate the following characteristics of a network: access method, allowed physical topologies, types of cabling, and speed of data transf ...
Learning in Neural Networks and Defect Tolerant Classifiers
... - Nodes connect back to other nodes or themselves - Information flow is bidirectional • Fully recurrent network: there is a pair of directed connections between every pair of neurons in the network ...
... - Nodes connect back to other nodes or themselves - Information flow is bidirectional • Fully recurrent network: there is a pair of directed connections between every pair of neurons in the network ...