Introduction
... application-level message e.g. A web server would put header information (information about the server & the document) as well as the document itself into its application-level ...
... application-level message e.g. A web server would put header information (information about the server & the document) as well as the document itself into its application-level ...
ppt
... Randomization: Dropping Packets Early • Better to give early feedback – Get a few connections to slow down – … before it is too late ...
... Randomization: Dropping Packets Early • Better to give early feedback – Get a few connections to slow down – … before it is too late ...
FPGA Research Design Platform Fuels Network Advances
... blocks of IP that may each use varied types of communication interfaces (streaming, byte-addressable and so on), with varied bandwidth and latency requirements. In its essence, OpenCPI is a highly configurable framework that provides the critical communication “glue” between IP that is needed to rea ...
... blocks of IP that may each use varied types of communication interfaces (streaming, byte-addressable and so on), with varied bandwidth and latency requirements. In its essence, OpenCPI is a highly configurable framework that provides the critical communication “glue” between IP that is needed to rea ...
60-367: Computer Networks
... application-level message e.g. A web server would put header information (information about the server & the document) as well as the document itself into its application-level ...
... application-level message e.g. A web server would put header information (information about the server & the document) as well as the document itself into its application-level ...
copyrighted material - Beck-Shop
... A campus area network (CAN) includes a set of interconnected LANs, is basically a smaller version of a wide area network (WAN) within an office or school campus, and is usually within a limited geographical area. Each building within the campus would have a separate LAN, and the LANs are often conne ...
... A campus area network (CAN) includes a set of interconnected LANs, is basically a smaller version of a wide area network (WAN) within an office or school campus, and is usually within a limited geographical area. Each building within the campus would have a separate LAN, and the LANs are often conne ...
VOIP Reports.pdf - 123SeminarsOnly.com
... responds to Bill's phone with a call proceeding message. When Sally lifts the handset the phone sends a connect message to Bill's phone. The two phones will now exchange the data packets containing the speech. At the end of the call Bill replaces his handset and phone stops sending voice data sends ...
... responds to Bill's phone with a call proceeding message. When Sally lifts the handset the phone sends a connect message to Bill's phone. The two phones will now exchange the data packets containing the speech. At the end of the call Bill replaces his handset and phone stops sending voice data sends ...
Paper - Asee peer logo
... This lab deals with UNIX networking utilities like ping, traceroute, netstat, and nslookup. Students are asked to read the man pages to learn about each of these utilities. They use ping to determine the RTT to various hosts in the Internet. Students use netstat to display the current IP routing tab ...
... This lab deals with UNIX networking utilities like ping, traceroute, netstat, and nslookup. Students are asked to read the man pages to learn about each of these utilities. They use ping to determine the RTT to various hosts in the Internet. Students use netstat to display the current IP routing tab ...
100-101 (ICND1) - Galaxy Computer Education
... with the CCENT certification and a tangible first step in achieving the CCNA Routing and Switching certification. Candidates can prepare for this exam by taking the Interconnecting Cisco Networking Devices Part 1 (ICND1) course. This exam tests a candidate's knowledge and skills required to successf ...
... with the CCENT certification and a tangible first step in achieving the CCNA Routing and Switching certification. Candidates can prepare for this exam by taking the Interconnecting Cisco Networking Devices Part 1 (ICND1) course. This exam tests a candidate's knowledge and skills required to successf ...
TACTICALL MCI LAND MOBILE COMMUNICATION
... T-MCI provides extensive network monitoring information capabilities via both the management and application interfaces. ...
... T-MCI provides extensive network monitoring information capabilities via both the management and application interfaces. ...
No Slide Title
... fixed-length packets which are sent to the destination. Each packet may take a different path through the network. The packets must be reassembled into messages as they arrive. ...
... fixed-length packets which are sent to the destination. Each packet may take a different path through the network. The packets must be reassembled into messages as they arrive. ...
The machine learning mechanism can be used to intelligently
... NMLRG will work on potential approaches that apply machine learning technologies in network control, network management, and supplying network data for upper-layer applications • The initial focus of the NMLRG will be on higher-layer concepts, use cases • The NMLRG is expected to identify and docume ...
... NMLRG will work on potential approaches that apply machine learning technologies in network control, network management, and supplying network data for upper-layer applications • The initial focus of the NMLRG will be on higher-layer concepts, use cases • The NMLRG is expected to identify and docume ...
siskiyous.edu
... Gain experience with networking equipment Follow general guidelines for each device type Devices most disruptive and complex to add or ...
... Gain experience with networking equipment Follow general guidelines for each device type Devices most disruptive and complex to add or ...
October 1, 2003
... • All designs must fit into the IP security architecture ?? • Authentication and confidentiality are the responsibility of end users, not the network • Security protocols should allow different cryptographic algorithms. • Choose a well-known/studied cryptographic algorithm, do NOT invent a new one u ...
... • All designs must fit into the IP security architecture ?? • Authentication and confidentiality are the responsibility of end users, not the network • Security protocols should allow different cryptographic algorithms. • Choose a well-known/studied cryptographic algorithm, do NOT invent a new one u ...
PPT
... coordinate and control sensors in real-time over an unreliable network connection • MAC – Bandwidth, power consumption, contention, network connectivity, real-time requirement ...
... coordinate and control sensors in real-time over an unreliable network connection • MAC – Bandwidth, power consumption, contention, network connectivity, real-time requirement ...
Formal Methods for Intrusion Detection - MSU CSE
... Responses range from e-mails to reconfiguring the network Just because the system detects an intrusion, may be legitimate Severe (or even simple) responses can be utilized by attackers to create new attacks ...
... Responses range from e-mails to reconfiguring the network Just because the system detects an intrusion, may be legitimate Severe (or even simple) responses can be utilized by attackers to create new attacks ...
Active Networks: Applications, Security, Safety
... system. Packets travel as capsules carrying code. • Some code is comprised of well-known routines that reside at every active node. • Rest of the application specific code is transferred by mobile code distribution techniques. Department of Computer Science, Purdue University ...
... system. Packets travel as capsules carrying code. • Some code is comprised of well-known routines that reside at every active node. • Rest of the application specific code is transferred by mobile code distribution techniques. Department of Computer Science, Purdue University ...
Lecture No. 4
... software computer can examine any frame on LAN. In this way the communication across LAN is guaranteed to be private. This computer receives and displays (but does not respond to) frames on the LAN. Network analyzer can be configured to filter and process frames. It can count frames of specific typ ...
... software computer can examine any frame on LAN. In this way the communication across LAN is guaranteed to be private. This computer receives and displays (but does not respond to) frames on the LAN. Network analyzer can be configured to filter and process frames. It can count frames of specific typ ...
TCP
... • A layer should be created where a different level of abstraction is needed; • Each layer should perform a well defined function; • The function of each layer should be chosen with an eye toward defining internationally standardised protocols; • The layer boundaries should be chosen to minimise the ...
... • A layer should be created where a different level of abstraction is needed; • Each layer should perform a well defined function; • The function of each layer should be chosen with an eye toward defining internationally standardised protocols; • The layer boundaries should be chosen to minimise the ...
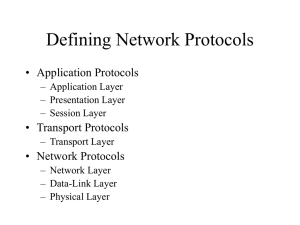
Defining Network Protocols
... Ethernet source Address (last 32 bits) Type Code or Length of packet IP header, TCP header, then your data ...
... Ethernet source Address (last 32 bits) Type Code or Length of packet IP header, TCP header, then your data ...
xilinx vertical market backgrounder
... Enabling Migration to 40G and 100G Network Infrastructure As the telecommunications market undergoes its current cycle of consolidation following the last decade’s explosive growth in capacity, the demands of the Internet continue to push the need for innovation. Today’s rapid rise of residential vi ...
... Enabling Migration to 40G and 100G Network Infrastructure As the telecommunications market undergoes its current cycle of consolidation following the last decade’s explosive growth in capacity, the demands of the Internet continue to push the need for innovation. Today’s rapid rise of residential vi ...