Modeling and Simulation to Study Wired/Wireless Network
... – there is clear and distinct separation of protocol stack layers – packets in GTNets consist of protocol data units (PDUs) that are appended and removed from the packet as it moves down and up the protocol stack – simulation objects representing network nodes have one or more interfaces, each of wh ...
... – there is clear and distinct separation of protocol stack layers – packets in GTNets consist of protocol data units (PDUs) that are appended and removed from the packet as it moves down and up the protocol stack – simulation objects representing network nodes have one or more interfaces, each of wh ...
DYNAMIC BUFFER ALLOCATION FOR TIME CRITICAL DATA IN
... [email protected],[email protected],[email protected] ABSTRACT Adhoc network is a collection of wireless mobile nodes dynamically forming a temporary network without the use of existing network infrastructure or centralized administration. Each node acts as a router by itself and forwards ...
... [email protected],[email protected],[email protected] ABSTRACT Adhoc network is a collection of wireless mobile nodes dynamically forming a temporary network without the use of existing network infrastructure or centralized administration. Each node acts as a router by itself and forwards ...
Routing IP Datagrams - Computing Science
... Routing IP Datagrams – by Roozbeh Farahbod, [email protected] ...
... Routing IP Datagrams – by Roozbeh Farahbod, [email protected] ...
i. introduction
... needed to reach other nodes, due to the limited range of the nodes. Each and every node in an ad hoc network must be keen to forward packets for other ...
... needed to reach other nodes, due to the limited range of the nodes. Each and every node in an ad hoc network must be keen to forward packets for other ...
Chapter 6 slides, Computer Networking, 3rd edition
... laptop, smartphone run applications may be stationary (nonmobile) or mobile wireless does not always mean mobility ...
... laptop, smartphone run applications may be stationary (nonmobile) or mobile wireless does not always mean mobility ...
ECE 4400:427/527 - Computer Networks Spring 2012
... • With a significant increase in the number of users, providers, and services, the Internet of the future is facing many problems: • How to manage/design a very large system with limited resources • Yet still provide a guaranteed performance ...
... • With a significant increase in the number of users, providers, and services, the Internet of the future is facing many problems: • How to manage/design a very large system with limited resources • Yet still provide a guaranteed performance ...
Layer
... • network layer is provided by Internet Protocol • found in all end-systems and intermediate systems • provides abstraction of end-to-end link • segmentation and reassembly • packet-forwarding, routing, scheduling ...
... • network layer is provided by Internet Protocol • found in all end-systems and intermediate systems • provides abstraction of end-to-end link • segmentation and reassembly • packet-forwarding, routing, scheduling ...
Internet Architecture
... transport transport network link physical application transport network link physical ...
... transport transport network link physical application transport network link physical ...
ANN, genetic algorithm, state estimation, electricity markets, market
... B. Radial Basis Function Neural Network Model The Radial Function is similar to the Gaussian function, which is defined by a centre and a width parameter. The parameters of the RBF units are determined in three steps of the training activity. First, the unit centers are determined by some form of cl ...
... B. Radial Basis Function Neural Network Model The Radial Function is similar to the Gaussian function, which is defined by a centre and a width parameter. The parameters of the RBF units are determined in three steps of the training activity. First, the unit centers are determined by some form of cl ...
Configuration Note 3020 Ver. C (7/98)
... Digital Networking allows for the delivery of voice and fax messages over an existing LAN/WAN network using TCP/IP protocols between Octel Overture 250/350 Message Servers. Digital Networking works with existing OctelNet and AMIS features to allow for a complete networking solution. Digital Networki ...
... Digital Networking allows for the delivery of voice and fax messages over an existing LAN/WAN network using TCP/IP protocols between Octel Overture 250/350 Message Servers. Digital Networking works with existing OctelNet and AMIS features to allow for a complete networking solution. Digital Networki ...
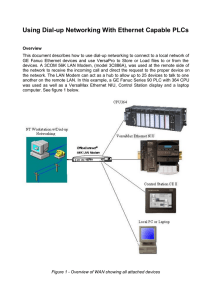
Using Dial-up Networking With Ethernet Capable PLCs
... create a new entry in the phone book using your PC’s modem as the dial-out device. Specify a user name and password for authentication. Dial-up server type is PPP, network protocol is TCP/IP. Next, configure the LAN Modem. As the LAN Modem is currently shipped, it is not set up to answer an incoming ...
... create a new entry in the phone book using your PC’s modem as the dial-out device. Specify a user name and password for authentication. Dial-up server type is PPP, network protocol is TCP/IP. Next, configure the LAN Modem. As the LAN Modem is currently shipped, it is not set up to answer an incoming ...
Mobile Communications
... more than 970.8 million subscribers (Dec 2003) more than 73% of all digital mobile phones use GSM over 10 billion SMS (Short Message Service) per month in Germany, > 360 billion/year worldwide ...
... more than 970.8 million subscribers (Dec 2003) more than 73% of all digital mobile phones use GSM over 10 billion SMS (Short Message Service) per month in Germany, > 360 billion/year worldwide ...
Slides
... Need to design policy on when to purge LIFO queues, and how many LIFO queues Parameters of policy set by messages from sink Given vehicle dynamics, sink can determine how ...
... Need to design policy on when to purge LIFO queues, and how many LIFO queues Parameters of policy set by messages from sink Given vehicle dynamics, sink can determine how ...
Document
... compliant with the P802.15.4 PAR. It is intended to support both master-slave and virtual peer-to-peer communications for low data rate networks. It is designed to support ultra low power consumption for battery operated nodes at very low implementation cost. The network is capable of supporting 254 ...
... compliant with the P802.15.4 PAR. It is intended to support both master-slave and virtual peer-to-peer communications for low data rate networks. It is designed to support ultra low power consumption for battery operated nodes at very low implementation cost. The network is capable of supporting 254 ...
Telework Connectivity Guide
... Some types of jobs, where the individual largely works alone are particularly suitable, such as data analysis, data processing, planning, project-oriented work, reviewing reports and literature, and making phone calls. Increasingly, today's knowledge worker can communicate and collaborate with cowor ...
... Some types of jobs, where the individual largely works alone are particularly suitable, such as data analysis, data processing, planning, project-oriented work, reviewing reports and literature, and making phone calls. Increasingly, today's knowledge worker can communicate and collaborate with cowor ...
IPTV Technology
... “IPTV is defined as multimedia services such as television/video/audio/text/graphics/data delivered over IP based networks managed to provide the required level of quality of service and experience, security, interactivity and reliability.” ...
... “IPTV is defined as multimedia services such as television/video/audio/text/graphics/data delivered over IP based networks managed to provide the required level of quality of service and experience, security, interactivity and reliability.” ...
Classful IP Addresses
... • Adoption of IPv6 is driven by IPv4 exhaustion: – There have been numerous predictions of imminent IPv4 exhaustion – People have been creative with slowing down IPv4 exhaustion through policies and protocols – IPv4 exhaustion will occur gradually, but is increasingly urgent ...
... • Adoption of IPv6 is driven by IPv4 exhaustion: – There have been numerous predictions of imminent IPv4 exhaustion – People have been creative with slowing down IPv4 exhaustion through policies and protocols – IPv4 exhaustion will occur gradually, but is increasingly urgent ...
Lab 9.2.4 IP Addressing Basics
... octets, can be used for hosts. Each Class A network can have 2 , or over 16 million hosts. It is common to subdivide the network into smaller groupings called subnets by using a custom subnet mask, which is discussed in the next lab. Network and host address The network or host portion of the addres ...
... octets, can be used for hosts. Each Class A network can have 2 , or over 16 million hosts. It is common to subdivide the network into smaller groupings called subnets by using a custom subnet mask, which is discussed in the next lab. Network and host address The network or host portion of the addres ...
Document
... – Unix approach: a host can be both clients and servers – NT approach: server machines are separated from client machines TELE 301 Lecture 10: Scheduled … ...
... – Unix approach: a host can be both clients and servers – NT approach: server machines are separated from client machines TELE 301 Lecture 10: Scheduled … ...
P2P
... Definition of P2P “P2P is a way of structuring distributed applications such that the individual nodes have symmetric roles. Rather than being divided into clients and servers each with quite distinct roles, in P2P applications a node may act as both a client and a server.” Excerpt from the Charter ...
... Definition of P2P “P2P is a way of structuring distributed applications such that the individual nodes have symmetric roles. Rather than being divided into clients and servers each with quite distinct roles, in P2P applications a node may act as both a client and a server.” Excerpt from the Charter ...
Assessment of the Internet Protocol Routing in Space—Joint Capability Technology Demonstration
... available only recently.2 Although some of the regenerative satellites provide layer-2 packet-switching functions (e.g., asynchronous transfer mode switch), an IPR as a communications network node in space did not exist until IRIS. [Note that some of the IRIS capabilities resemble those of DoD’s Tra ...
... available only recently.2 Although some of the regenerative satellites provide layer-2 packet-switching functions (e.g., asynchronous transfer mode switch), an IPR as a communications network node in space did not exist until IRIS. [Note that some of the IRIS capabilities resemble those of DoD’s Tra ...
A Comparative Study of Related Technologies of Intrusion Detection
... from hackers. Up to the moment, researchers have developed Intrusion Detection Systems (IDS) capable of detecting attacks in several available environments. A boundlessness of methods for misuse detection as well as anomaly detection has been applied. Intrusion Prevention Systems (IPS) evolved after ...
... from hackers. Up to the moment, researchers have developed Intrusion Detection Systems (IDS) capable of detecting attacks in several available environments. A boundlessness of methods for misuse detection as well as anomaly detection has been applied. Intrusion Prevention Systems (IPS) evolved after ...
41.Applied.Recursion
... PathFrom() is not very efficient, and the path it returns may not be the shortest path from i to j. The graph (a set of nodes and a set of edges connecting them) is often used to model networks. Efficient solutions have been devised for many graphtheory problems (e.g., the shortest path problem), pr ...
... PathFrom() is not very efficient, and the path it returns may not be the shortest path from i to j. The graph (a set of nodes and a set of edges connecting them) is often used to model networks. Efficient solutions have been devised for many graphtheory problems (e.g., the shortest path problem), pr ...