Chapter 15 Local Area Networks
... loops — Only one path between any two devices — Impossible in standards-based implementation to provide multiple paths through multiple switches between devices • Limits both performance and reliability. ...
... loops — Only one path between any two devices — Impossible in standards-based implementation to provide multiple paths through multiple switches between devices • Limits both performance and reliability. ...
Network Simulator Tutorial
... real-system not available, is complex/costly or dangerous (eg: space simulations, flight simulations) quickly evaluate design alternatives (eg: different system configurations) evaluate complex functions for which closed form formulas or numerical techniques not available ...
... real-system not available, is complex/costly or dangerous (eg: space simulations, flight simulations) quickly evaluate design alternatives (eg: different system configurations) evaluate complex functions for which closed form formulas or numerical techniques not available ...
Chapter 15 Local Area Networks
... loops — Only one path between any two devices — Impossible in standards-based implementation to provide multiple paths through multiple switches between devices • Limits both performance and reliability. ...
... loops — Only one path between any two devices — Impossible in standards-based implementation to provide multiple paths through multiple switches between devices • Limits both performance and reliability. ...
Associative Learning in Hierarchical Self
... The hierarchical structure appears advantageous. Using equal number of bits for features and class IDs gives better rate. Performance further improved to 86% with mixed feature/classification bits. ...
... The hierarchical structure appears advantageous. Using equal number of bits for features and class IDs gives better rate. Performance further improved to 86% with mixed feature/classification bits. ...
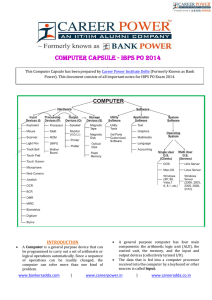
COMPUTER CAPSULE - IBPS PO 2014 . INTRODUCTION
... The set of instructions, which control the sequence of operations, are known as Program. It is a sequence of instructions, written to perform a specified task with a computer. A Software instructs the computer what to do and how to do it. It is a set of instructions that tells the computer about the ...
... The set of instructions, which control the sequence of operations, are known as Program. It is a sequence of instructions, written to perform a specified task with a computer. A Software instructs the computer what to do and how to do it. It is a set of instructions that tells the computer about the ...
Chapter 8 - Weber State University
... 10.10.10.1/32 is directly connected, FastEthernet0/1 S* 0.0.0.0/0 is directly connected, FastEthernet0/0 The C in the routing table output means that the networks listed are “directly connected,” and until we add a routing protocol like RIPv2, OSPF, etc. to the routers in our internetwork, or enter ...
... 10.10.10.1/32 is directly connected, FastEthernet0/1 S* 0.0.0.0/0 is directly connected, FastEthernet0/0 The C in the routing table output means that the networks listed are “directly connected,” and until we add a routing protocol like RIPv2, OSPF, etc. to the routers in our internetwork, or enter ...
downloading
... The VM disk image has to be accessible from the new host after the migration Just copy the image across? ...
... The VM disk image has to be accessible from the new host after the migration Just copy the image across? ...
A High-Throughput Overlay Multicast Infrastructure
... to destination k by δ = fk − fmax . We initiate the flow reduction process by reducing the flow on each feedback link by δ. The reduction algorithm is presented in Table 2. 3.3 Data Dissemination Each transmission topology computed by the min-cost flow algorithm provides information not only on the ...
... to destination k by δ = fk − fmax . We initiate the flow reduction process by reducing the flow on each feedback link by δ. The reduction algorithm is presented in Table 2. 3.3 Data Dissemination Each transmission topology computed by the min-cost flow algorithm provides information not only on the ...
network topology
... The solution of a given linear network problem requires the formation of a set of equations describing the response of the network. The mathematical model so derived, must describe the characteristics of the individual network components, as well as the relationship which governs the interconnection ...
... The solution of a given linear network problem requires the formation of a set of equations describing the response of the network. The mathematical model so derived, must describe the characteristics of the individual network components, as well as the relationship which governs the interconnection ...
mm.aueb.gr
... Key Communication Paradigms (3) Not covered in this tutorial mm wave communications (30 to 300 GHz) ...
... Key Communication Paradigms (3) Not covered in this tutorial mm wave communications (30 to 300 GHz) ...
TCP/IP for Security Administrators
... Can come only from host’s existing DG Must be tied to an existing connection Can’t be used for unsolicited route table updates ...
... Can come only from host’s existing DG Must be tied to an existing connection Can’t be used for unsolicited route table updates ...
Document
... by the ACL on R1? Refer to the exhibit. The network engineer for the company that is shown wants to use the primary ISP connection for all external connectivity. The backup ISP connection is used only if the ...
... by the ACL on R1? Refer to the exhibit. The network engineer for the company that is shown wants to use the primary ISP connection for all external connectivity. The backup ISP connection is used only if the ...
Optical Networks - Basic Concepts (Part 1) by Prof. Subir
... Transmitter – convert data to a modulated optical signal Receiver – Convert a modulated optical signal to data Multiplexer – to combine multiple optical signals Demultiplexer – to separate signals having different carrier wavelengths Routers – to direct the signals from the source to the destination ...
... Transmitter – convert data to a modulated optical signal Receiver – Convert a modulated optical signal to data Multiplexer – to combine multiple optical signals Demultiplexer – to separate signals having different carrier wavelengths Routers – to direct the signals from the source to the destination ...
"A Mesh based Robust Topology Discovery Algorithm for Hybrid Wireless Networks"
... several disadvantages to this approach. For example, in certain applications there might be no such preexisting infrastructure available. Also, in many other applications, e.g., home and office or sensor applications, the devices might be battery operated, and the limited power consumption therefore ...
... several disadvantages to this approach. For example, in certain applications there might be no such preexisting infrastructure available. Also, in many other applications, e.g., home and office or sensor applications, the devices might be battery operated, and the limited power consumption therefore ...
Data Sheet - Engage Communication, Inc.
... In Layer 1 operating mode every bit is encapsulated into an IP packet. The size and frequency of the IP packets can be set with data bit rates from 75 bits to 256 kilobits per second. Isochronous serial protocols, such as Conitel, are transported synchronously to maintain message alignment. A config ...
... In Layer 1 operating mode every bit is encapsulated into an IP packet. The size and frequency of the IP packets can be set with data bit rates from 75 bits to 256 kilobits per second. Isochronous serial protocols, such as Conitel, are transported synchronously to maintain message alignment. A config ...
Guide to Network Defense and Countermeasures
... • SYN scan – a progression of packets with only the SYN flag set • FIN scan –only packets with the FIN flag set • ACK scan –only packets with the ACK flag set • Null scan – sequence of packets that have no flags set • Xmas scan – sequence of packets that have the FIN PSH URG flags set Guide to Netwo ...
... • SYN scan – a progression of packets with only the SYN flag set • FIN scan –only packets with the FIN flag set • ACK scan –only packets with the ACK flag set • Null scan – sequence of packets that have no flags set • Xmas scan – sequence of packets that have the FIN PSH URG flags set Guide to Netwo ...
slides
... – One of many compe;ng physical layers – Most popular, but others s;ll important • Eg for long-‐haul cables ...
... – One of many compe;ng physical layers – Most popular, but others s;ll important • Eg for long-‐haul cables ...
Operating Systems and Networks - Summaries
... Arrival rate distribution .....................................................................................................................22 ...
... Arrival rate distribution .....................................................................................................................22 ...
Chapter 4 slides
... 4.4.4 IP fragmentation 4.4.5 ICMP: Internet Control Message Protocol 4.4.6 DHCP: Dynamic Host Configuration Protocol 4.4.7 NAT: Network Address Translation 4.5 Routing in the Internet 4.6 What’s Inside a Router 4.7 IPv6 4.8 Multicast Routing 4.9 Mobility Network Layer 4-22 ...
... 4.4.4 IP fragmentation 4.4.5 ICMP: Internet Control Message Protocol 4.4.6 DHCP: Dynamic Host Configuration Protocol 4.4.7 NAT: Network Address Translation 4.5 Routing in the Internet 4.6 What’s Inside a Router 4.7 IPv6 4.8 Multicast Routing 4.9 Mobility Network Layer 4-22 ...
Chapter 5
... Each connection point on a network is referred to as a node To connect to a LAN, a computer requires network circuitry, sometimes referred to as a network interface card (NIC) A networked peripheral, or network-enabled peripheral, is any device that contains network circuitry to directly connect ...
... Each connection point on a network is referred to as a node To connect to a LAN, a computer requires network circuitry, sometimes referred to as a network interface card (NIC) A networked peripheral, or network-enabled peripheral, is any device that contains network circuitry to directly connect ...
www2.cit.cornell.edu
... Assistant Vice President, Student & Academic Services Associate Dean for Business Administration, Hotel Administration Accounting Services Director, Computing Facility, Laboratory of Nuclear Studies Customer Services Director, Cornell Information Technologies ...
... Assistant Vice President, Student & Academic Services Associate Dean for Business Administration, Hotel Administration Accounting Services Director, Computing Facility, Laboratory of Nuclear Studies Customer Services Director, Cornell Information Technologies ...
DumpsReview
... A. Configure the NAT to use dynamic DNS. B. Configure the NAT to route the 64.124.0.0/16 network to the Internet. C. Reconfigure the internal network to use an accepted private network address. D. Add a static route from the 64.124.0.0/16 network to the Symantec LiveUpdate servers. Answer: C NO.2 Wh ...
... A. Configure the NAT to use dynamic DNS. B. Configure the NAT to route the 64.124.0.0/16 network to the Internet. C. Reconfigure the internal network to use an accepted private network address. D. Add a static route from the 64.124.0.0/16 network to the Symantec LiveUpdate servers. Answer: C NO.2 Wh ...
Visual management of Sags and Incidents gathered in Management
... On the other hand, protective systems based on digital relays are capable to report trips. Both registers are provoked by the presence of perturbations in the network, resulting in complementary information gathered by equipment far away from each other. Information related to protective system oper ...
... On the other hand, protective systems based on digital relays are capable to report trips. Both registers are provoked by the presence of perturbations in the network, resulting in complementary information gathered by equipment far away from each other. Information related to protective system oper ...