SYSTEM ADMINISTRATION Chapter 8 Internet Protocol (IP) Addressing
... There are five steps to subnetting: 1. Determine the number of subnetworks needed and the maximum number of hosts on any subnetwork. 2. Determine the number of bits to “steal” from the host bit portion of the IP address. Use the formula 2N – 2 = the maximum number of subnets available, where N = the ...
... There are five steps to subnetting: 1. Determine the number of subnetworks needed and the maximum number of hosts on any subnetwork. 2. Determine the number of bits to “steal” from the host bit portion of the IP address. Use the formula 2N – 2 = the maximum number of subnets available, where N = the ...
Network Operating System
... Each packet may take a different path through the network The packets must be reassembled into messages as they arrive ...
... Each packet may take a different path through the network The packets must be reassembled into messages as they arrive ...
Document
... making the decision which router to use, and forwarding. One can think of a router as having two processes inside it. One of them handles each packet as it arrives, looking up the outgoing line to use for it in the routing tables. This process is forwarding. The other process is responsible for fill ...
... making the decision which router to use, and forwarding. One can think of a router as having two processes inside it. One of them handles each packet as it arrives, looking up the outgoing line to use for it in the routing tables. This process is forwarding. The other process is responsible for fill ...
Why MPLS multicast?
... mLDP: no support in protocol Can be achieved via network planning & IGP modelling RSVP-TE: support via explicit routes mLDP: no support in protocol Can be achieved via network planning & IGP modelling RSVP-TE: support via TE metrics and explicit routes ...
... mLDP: no support in protocol Can be achieved via network planning & IGP modelling RSVP-TE: support via explicit routes mLDP: no support in protocol Can be achieved via network planning & IGP modelling RSVP-TE: support via TE metrics and explicit routes ...
Computer Networks I Laboratory Exercise 5
... 1. On the R1 router, use the show ip eigrp neighbors command to view the neighbor table and verify that EIGRP has established an adjacency with the R2 and R3 routers. You should be able to see the IP address of each adjacent router and the interface that R1 uses to reach that EIGRP neighbor. R1#show ...
... 1. On the R1 router, use the show ip eigrp neighbors command to view the neighbor table and verify that EIGRP has established an adjacency with the R2 and R3 routers. You should be able to see the IP address of each adjacent router and the interface that R1 uses to reach that EIGRP neighbor. R1#show ...
What applications are supported on the network?
... users and other applications. Risk – The possible loss or malfunction related to user of a corporate asset. Access Control – Controlling access to a network by using network device to limit the type, and amount of data allowed to be transmitted across the network. Intrusion – an action taken by some ...
... users and other applications. Risk – The possible loss or malfunction related to user of a corporate asset. Access Control – Controlling access to a network by using network device to limit the type, and amount of data allowed to be transmitted across the network. Intrusion – an action taken by some ...
Brochure
... avoids the need for backhauling all the data traffic to a single place, thus averting a choke point. All access points in the network controlled by one NOC not only brings convenience to network management but also enables mobile users to avail easy roaming facility. Roaming users can cross over sea ...
... avoids the need for backhauling all the data traffic to a single place, thus averting a choke point. All access points in the network controlled by one NOC not only brings convenience to network management but also enables mobile users to avail easy roaming facility. Roaming users can cross over sea ...
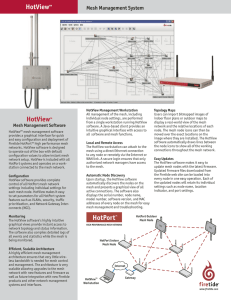
HotViewTM HotView™
... Add your own bitmapped background images of street maps, floor plans, or any other networking environments to provide a real world layout of the mesh network showing the relative location of each node. Graphical Device Management The main HotView screen provides a graphical view of the mesh network, ...
... Add your own bitmapped background images of street maps, floor plans, or any other networking environments to provide a real world layout of the mesh network showing the relative location of each node. Graphical Device Management The main HotView screen provides a graphical view of the mesh network, ...
Mobile Ad-hoc Network Routing and Security Environment
... the RERR(Route Error) messages to the source node and launch processing of route research [10]. After that, the mobile node received the RERR message deletes routing information related to links which occur errors. 2.2. Security Environment in Mobile Ad-hoc Network 2.1.1. Threat and Attack Pattern: ...
... the RERR(Route Error) messages to the source node and launch processing of route research [10]. After that, the mobile node received the RERR message deletes routing information related to links which occur errors. 2.2. Security Environment in Mobile Ad-hoc Network 2.1.1. Threat and Attack Pattern: ...
Subnets Benefits of subnets
... address format: a.b.c.d/x, where x is # bits in subnet portion of address subnet part ...
... address format: a.b.c.d/x, where x is # bits in subnet portion of address subnet part ...
Identifying Performance Bottlenecks in CDNs through TCP-Level Monitoring
... the server. As such, directing clients to the closest Coral proxy (in terms of RTT) is critically important for improving performance. In addition, the network stack can use a larger initial congestion window, as some commercial content providers do [4]. (3) Some connections have significant packet ...
... the server. As such, directing clients to the closest Coral proxy (in terms of RTT) is critically important for improving performance. In addition, the network stack can use a larger initial congestion window, as some commercial content providers do [4]. (3) Some connections have significant packet ...
SNMP Simple Network Management Protocol
... A community string is a password that allows access to a network device. It defines what "community of people" can access the SNMP information that is on the device. ...
... A community string is a password that allows access to a network device. It defines what "community of people" can access the SNMP information that is on the device. ...
02-Distributed System Structure
... Each packet may take a different path through the network The packets must be reassembled into messages as they arrive ...
... Each packet may take a different path through the network The packets must be reassembled into messages as they arrive ...
ch16
... Each packet may take a different path through the network The packets must be reassembled into messages as they arrive ...
... Each packet may take a different path through the network The packets must be reassembled into messages as they arrive ...
Review for Quiz-1 - Georgia Institute of Technology
... – Application-Level Recovery • Freeze picture • Extrapolate across gap ...
... – Application-Level Recovery • Freeze picture • Extrapolate across gap ...
The Effect of Network Structure on Preference Formation Samara
... A lower clustered network should therefore facilitate greater exposure to both sides of an issue, which are known to permeate different and distant parts of a network (Conover et al. 2011; Smith et al. 2014). We thus expect that individuals who are embedded in a low-clustered network are more likel ...
... A lower clustered network should therefore facilitate greater exposure to both sides of an issue, which are known to permeate different and distant parts of a network (Conover et al. 2011; Smith et al. 2014). We thus expect that individuals who are embedded in a low-clustered network are more likel ...
6.M. Rehena Sulthana.pmd
... IPV4 for a long time. The Internet Engineering Task force (IETF) has been working on the IPV6 specifications in order to address the limitations caused by IPV4. IPV6 is also referred as Next Generation Internet Protocol (IPng). ZigBee is a low-cost, low-power, wireless mesh networking standard. Firs ...
... IPV4 for a long time. The Internet Engineering Task force (IETF) has been working on the IPV6 specifications in order to address the limitations caused by IPV4. IPV6 is also referred as Next Generation Internet Protocol (IPng). ZigBee is a low-cost, low-power, wireless mesh networking standard. Firs ...
Event Detection
... schemes for local processing and data transmission, known as the centralized option, the distributed option, and the quantized option. • To be specific, the centralized option transmits all the information contained in the observed data to the control center, which results in a simple binary hypothe ...
... schemes for local processing and data transmission, known as the centralized option, the distributed option, and the quantized option. • To be specific, the centralized option transmits all the information contained in the observed data to the control center, which results in a simple binary hypothe ...
Ch4_3ed
... (max.transfer size) - largest possible link-level frame. The links on a route can use different link types, different link-layer protocols, and different MTUs large IP datagram are divided (“fragmented”) within network one datagram becomes several datagrams “reassembled” only at final destin ...
... (max.transfer size) - largest possible link-level frame. The links on a route can use different link types, different link-layer protocols, and different MTUs large IP datagram are divided (“fragmented”) within network one datagram becomes several datagrams “reassembled” only at final destin ...
- The CLOUDS Lab
... Supervised by distributed algorithms that respond online to global resource availability – transparently. Load-balancing - migrate process from over-loaded to underloaded nodes. Memory ushering - migrate processes from a node that has exhausted its memory, to prevent paging/swapping. ...
... Supervised by distributed algorithms that respond online to global resource availability – transparently. Load-balancing - migrate process from over-loaded to underloaded nodes. Memory ushering - migrate processes from a node that has exhausted its memory, to prevent paging/swapping. ...
Quality of Service (QoS) for Enterprise Networks
... traffic shaping retains excess packets in a queue and then schedules these excess packets for transmission depending on factors, such as available bandwidth or delay requirements of the receiving interface. The result of traffic shaping is a smoothed packet output rate. Scheduling (Queuing & Droppin ...
... traffic shaping retains excess packets in a queue and then schedules these excess packets for transmission depending on factors, such as available bandwidth or delay requirements of the receiving interface. The result of traffic shaping is a smoothed packet output rate. Scheduling (Queuing & Droppin ...
S_V07 - Raadio- ja sidetehnika instituut
... – New RTT = a (old RTT) + (1 - a) (new sample) – Recommended value for a: 0.8 - 0.9 • 0.875 for most TCP’s ...
... – New RTT = a (old RTT) + (1 - a) (new sample) – Recommended value for a: 0.8 - 0.9 • 0.875 for most TCP’s ...