Computer Networks II
... AKAY Others Course Objective The objective of this course is to introduce students to a set of basic topics in networking and lead them to the understanding of the networking architecture. Relationship Students who have completed the course successfully should be able to Net Effect Prog. Output ...
... AKAY Others Course Objective The objective of this course is to introduce students to a set of basic topics in networking and lead them to the understanding of the networking architecture. Relationship Students who have completed the course successfully should be able to Net Effect Prog. Output ...
Final Thesis - University of South Australia
... Chapter 1 - The thesis will be introduced, giving a brief overview of the expectations of the following research, as well as the Field of Thesis and the Significance and Contributions. The context for the research will be established and its purpose discussed. Chapter 2 - This chapter will commence ...
... Chapter 1 - The thesis will be introduced, giving a brief overview of the expectations of the following research, as well as the Field of Thesis and the Significance and Contributions. The context for the research will be established and its purpose discussed. Chapter 2 - This chapter will commence ...
installation manual
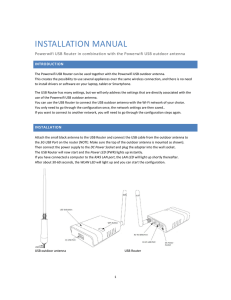
... The Powerwifi USB Router can be used together with the Powerwifi USB outdoor antenna. This creates the possibility to use several appliances over the same wireless connection, and there is no need to install drivers or software on your laptop, tablet or Smartphone. The USB Router has many settings, ...
... The Powerwifi USB Router can be used together with the Powerwifi USB outdoor antenna. This creates the possibility to use several appliances over the same wireless connection, and there is no need to install drivers or software on your laptop, tablet or Smartphone. The USB Router has many settings, ...
Distance Vector Routing Protocols
... Routing protocol characteristics (1/3) • Time to Convergence - Time to convergence defines how quickly the routers in the network topology share routing information and reach a state of consistent knowledge. – The faster the convergence, the more preferable the protocol. – Routing loops can occur w ...
... Routing protocol characteristics (1/3) • Time to Convergence - Time to convergence defines how quickly the routers in the network topology share routing information and reach a state of consistent knowledge. – The faster the convergence, the more preferable the protocol. – Routing loops can occur w ...
WHITE PAPER – Polycom: Video Conferencing
... of “Supporting Real-time Traffic, Preparing Your IP Network for Video Conferencing”, a separate white paper from Polycom ...
... of “Supporting Real-time Traffic, Preparing Your IP Network for Video Conferencing”, a separate white paper from Polycom ...
VLANs - Lansing School District
... switch via software Not standardized – proprietary software from vendor ...
... switch via software Not standardized – proprietary software from vendor ...
TC90: Presentation Title
... Using DVS with links [Li et al. 2003] Using on/off links [L. Peh et al. 2003] Router power throttling [Li et al. 2003] ...
... Using DVS with links [Li et al. 2003] Using on/off links [L. Peh et al. 2003] Router power throttling [Li et al. 2003] ...
The Announcement Layer: Beacon Coordination for
... – Nodes primarily use structured overlay network (SON) IDs as network endpoints. ...
... – Nodes primarily use structured overlay network (SON) IDs as network endpoints. ...
Data encapsulation
... 10Base-FL, but it limits the length of a cable segment to 412 meters • Gigabit Ethernet is the newest form of • Ethernet, raising network transmission speed to 1000 Mbps ...
... 10Base-FL, but it limits the length of a cable segment to 412 meters • Gigabit Ethernet is the newest form of • Ethernet, raising network transmission speed to 1000 Mbps ...
APPLICATION NOTE
... If the Envisalerts Status is OFFLINE but a valid IP address is shown, a firewall is blocking communications with the alerting server. The firewall may be within your router, or a separate appliance. Specific information on how to disable your firewall is out of the scope of technical support; howeve ...
... If the Envisalerts Status is OFFLINE but a valid IP address is shown, a firewall is blocking communications with the alerting server. The firewall may be within your router, or a separate appliance. Specific information on how to disable your firewall is out of the scope of technical support; howeve ...
Sphere of Influence Project owner: Mark Yarvis Intel
... Free nodes alternate between BT Inquiry & scan modes to discover other nodes Free nodes can join at different levels in the tree, depending on which node they connect to Connected nodes only scan to eliminate the possibility of creating loops Simple routing algorithm Intel Research ...
... Free nodes alternate between BT Inquiry & scan modes to discover other nodes Free nodes can join at different levels in the tree, depending on which node they connect to Connected nodes only scan to eliminate the possibility of creating loops Simple routing algorithm Intel Research ...
NETWORK MANAGEMENT
... At least one host in the network is designated as the network control host, or manager. In addition to the NME software, the network control host includes a collection of software called the network management application (NMA). The NMA includes an operator interface to allow an authorized user to m ...
... At least one host in the network is designated as the network control host, or manager. In addition to the NME software, the network control host includes a collection of software called the network management application (NMA). The NMA includes an operator interface to allow an authorized user to m ...
Example
... • Lower layers might handle things like how to turn electrical voltages into 1s and 0s. – You don’t want to be dealing with that when implementing the HTTP protocol. ...
... • Lower layers might handle things like how to turn electrical voltages into 1s and 0s. – You don’t want to be dealing with that when implementing the HTTP protocol. ...
IEEE C802.16ppc-10/0055r1 Project Title
... The analysis shown in the previous sections indicate the need for a significant reduction in signaling and protocol overhead incurred by M2M devices attempting to send short bursts of data while being forced to reside in the idle state. We suggest that the following functional requirements be added ...
... The analysis shown in the previous sections indicate the need for a significant reduction in signaling and protocol overhead incurred by M2M devices attempting to send short bursts of data while being forced to reside in the idle state. We suggest that the following functional requirements be added ...
Chapter 3: Internetworking - ¡Bienvenido a paloalto.unileon.es!
... A simple internetwork where H represents hosts and R represents routers ...
... A simple internetwork where H represents hosts and R represents routers ...
Chord: A Scalable Peer-to-peer Lookup Service for Internet
... function and storing (K,V) at the node in the zone containing P Retrieve entry (K,V) by applying the same hash function to map K to P and retrieve entry from node in zone containing P If P is not contained in the zone of the requesting node or its neighboring zones, route request to neighbor node in ...
... function and storing (K,V) at the node in the zone containing P Retrieve entry (K,V) by applying the same hash function to map K to P and retrieve entry from node in zone containing P If P is not contained in the zone of the requesting node or its neighboring zones, route request to neighbor node in ...
Fault Management
... For protected services, recovery may be accomplished via protection schemes if the failure event is not too extreme. Re-routing, (restoration), can recover services again provided that the failure event is not too extreme. Assuming that conventional methods succeed, the network may be vulnerab ...
... For protected services, recovery may be accomplished via protection schemes if the failure event is not too extreme. Re-routing, (restoration), can recover services again provided that the failure event is not too extreme. Assuming that conventional methods succeed, the network may be vulnerab ...
ROUTE10S02L05
... – How do you automatically configure EIGRP to advertise any additional network that is added to the router? – Can a secondary IP address be added to the router? Task 2: Configure EIGRP over a multipoint WAN interface – What steps did you take to configure the EIGRP routing protocol on multipoint W ...
... – How do you automatically configure EIGRP to advertise any additional network that is added to the router? – Can a secondary IP address be added to the router? Task 2: Configure EIGRP over a multipoint WAN interface – What steps did you take to configure the EIGRP routing protocol on multipoint W ...
ch2
... The first computer communication systems were connected by communication channels that connected exactly two computers. Called a mesh or point-to-point network Had three useful properties: – 1. Each connection was independent and different hardware could be used. (bandwidth, modems, etc. did n ...
... The first computer communication systems were connected by communication channels that connected exactly two computers. Called a mesh or point-to-point network Had three useful properties: – 1. Each connection was independent and different hardware could be used. (bandwidth, modems, etc. did n ...
Hot Topics
... Games” - Sachin Adlakha, Ramesh Johari, Andrea Goldsmith (still in peer review) »Demonstrates Nash equilibria for “interference games” with incomplete information. Shows a need for a regulatory protocol to avoid a suboptimal equilibrium. ‹#› - Michael Wilson - 5/25/2017 ...
... Games” - Sachin Adlakha, Ramesh Johari, Andrea Goldsmith (still in peer review) »Demonstrates Nash equilibria for “interference games” with incomplete information. Shows a need for a regulatory protocol to avoid a suboptimal equilibrium. ‹#› - Michael Wilson - 5/25/2017 ...
Use the following IP address
... – If blocks contain all zeros, they can be written as double colons. From IP address above: • 2001:0000:B80::D3:9C5A:CC • Only one set of double colons is used A+ Guide to IT Technical Support, 9th Edition ...
... – If blocks contain all zeros, they can be written as double colons. From IP address above: • 2001:0000:B80::D3:9C5A:CC • Only one set of double colons is used A+ Guide to IT Technical Support, 9th Edition ...
Small Network Equipment Energy Consumption in US Homes
... computers, and cable set-top boxes, little is known about the approximately 145 million small network devices we use to access the Internet and move digital content around our homes. To better understand the per model and national energy use of modems, routers, and other such devices—and how much co ...
... computers, and cable set-top boxes, little is known about the approximately 145 million small network devices we use to access the Internet and move digital content around our homes. To better understand the per model and national energy use of modems, routers, and other such devices—and how much co ...
Appendix B - Roaming
... the situation. Essentially this means that either the applications or intervening hardware has failed to get an acknowledgement from the destination to say the data has been received. When this happens then the sender could redo the ARP message in order to relearn the MAC address route or the switch ...
... the situation. Essentially this means that either the applications or intervening hardware has failed to get an acknowledgement from the destination to say the data has been received. When this happens then the sender could redo the ARP message in order to relearn the MAC address route or the switch ...