Lecture 6 - Courses - University of British Columbia
... 3. Facilitates the detection and potential correction of design errors during normal ...
... 3. Facilitates the detection and potential correction of design errors during normal ...
Chapter 9 Questions06.doc
... Indicate whether the sentence or statement is true or false. 1. Although some cybercafés charge a per-hour or per-minute fee, most provide free Internet access. 2. The last and least used application of GPS (global positioning system) technology is to assist people with determining where they are lo ...
... Indicate whether the sentence or statement is true or false. 1. Although some cybercafés charge a per-hour or per-minute fee, most provide free Internet access. 2. The last and least used application of GPS (global positioning system) technology is to assist people with determining where they are lo ...
PHD Proposal Draft
... A key challenge in today’s Internet is to improve the network bandwidth and reliability for potentially vast numbers of heterogeneous clients. However, the network connections between two network nodes in current Internet are mostly single path connections. The single path connection model is simple ...
... A key challenge in today’s Internet is to improve the network bandwidth and reliability for potentially vast numbers of heterogeneous clients. However, the network connections between two network nodes in current Internet are mostly single path connections. The single path connection model is simple ...
Low Cost Ethernet and E1 Services
... Carrier-Class Reliability and Features The FLASHWAVE 4060 is a powerful, SDH-based, Multiservice Provisioning Platform that can be deployed in an access network with other SDH NEs. The FLASHWAVE 4060 is built to the same exacting standards of quality as all Fujitsu transmission products. Specific ca ...
... Carrier-Class Reliability and Features The FLASHWAVE 4060 is a powerful, SDH-based, Multiservice Provisioning Platform that can be deployed in an access network with other SDH NEs. The FLASHWAVE 4060 is built to the same exacting standards of quality as all Fujitsu transmission products. Specific ca ...
A Relative Positioning System for Co-located Mobile Devices Albert Krohn
... instrumentation of the environment are inhibiting. This paper describes the Relate system which we have designed to enable co-located mobile computing devices to directly establish their spatial relationships, without need for infrastructure in their environment. The system is based on wireless sens ...
... instrumentation of the environment are inhibiting. This paper describes the Relate system which we have designed to enable co-located mobile computing devices to directly establish their spatial relationships, without need for infrastructure in their environment. The system is based on wireless sens ...
ppt slides
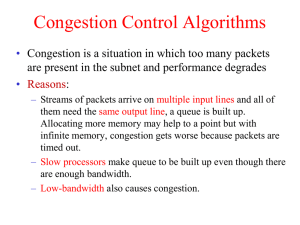
... Monitoring of the network edges Provides feedback to applications when they send too ...
... Monitoring of the network edges Provides feedback to applications when they send too ...
LANMAR-Implementatio..
... Routes within Fisheye scope are accurate. As hop distance increases routes accuracy decreases. ...
... Routes within Fisheye scope are accurate. As hop distance increases routes accuracy decreases. ...
pptx - University of Cambridge Computer Laboratory
... Internet routing protocols are responsible for constructing and updating the forwarding tables at routers ...
... Internet routing protocols are responsible for constructing and updating the forwarding tables at routers ...
WIRE07-slide
... and still maintain existing connections; Proposed enhancement of MIPv6, it is designed to reduce the amount of signaling required and to improve handoff speed for mobile connections; ...
... and still maintain existing connections; Proposed enhancement of MIPv6, it is designed to reduce the amount of signaling required and to improve handoff speed for mobile connections; ...
Lecture 10 - Lyle School of Engineering
... LSRs learn topology of network using existing routing protocols, eg, OSPF A label distribution protocol coordinates assignment of labels among routers, can be standardized LDP [RFC 3031] or extension of RSVP (RSVP-TE) ...
... LSRs learn topology of network using existing routing protocols, eg, OSPF A label distribution protocol coordinates assignment of labels among routers, can be standardized LDP [RFC 3031] or extension of RSVP (RSVP-TE) ...
Watermarking technique is a particular embodiment of multimedia
... wireless technology. After installing the card, your computer will become “wireless”. This means that you will be able to enjoy an Internet connection without the use of cables and cords. VoIP is the technology that allows the transmission of audio files by transmitting them into data packets across ...
... wireless technology. After installing the card, your computer will become “wireless”. This means that you will be able to enjoy an Internet connection without the use of cables and cords. VoIP is the technology that allows the transmission of audio files by transmitting them into data packets across ...
A Relative Positioning System for Co-located Mobile
... to directly establish their spatial relationships, without need for infrastructure in their environment. The system is based on wireless sensor devices implemented as USB peripherals (dongles) that can be readily used to extend mobile computers (hosts) with peer-to-peer sensing. The dongles are desi ...
... to directly establish their spatial relationships, without need for infrastructure in their environment. The system is based on wireless sensor devices implemented as USB peripherals (dongles) that can be readily used to extend mobile computers (hosts) with peer-to-peer sensing. The dongles are desi ...
Part I: Introduction - Rensselaer Polytechnic Institute
... Network (network portion): • get allocated portion of ISP’s address space: ISP's block ...
... Network (network portion): • get allocated portion of ISP’s address space: ISP's block ...
How-To Compare Performance of Data Plane Devices
... (FIB) of the data plane. End users rarely interact with the control plane. One exception is the ICMP ping, where a control plane protocol can be directly employed. [9] ...
... (FIB) of the data plane. End users rarely interact with the control plane. One exception is the ICMP ping, where a control plane protocol can be directly employed. [9] ...
Summit X670 Series
... ACLs are one of the most powerful components used in controlling network resource utilization as well as in protecting the network. Summit X670 series supports up to 2,048 ingress ACLs and 1,024 egress ...
... ACLs are one of the most powerful components used in controlling network resource utilization as well as in protecting the network. Summit X670 series supports up to 2,048 ingress ACLs and 1,024 egress ...
Chapter 5
... Architecture for streaming multimedia. Also called flow-based algorithms It was aimed at both unicast and multicast applications. Unicast Example :single user streaming a video clip from a news site ...
... Architecture for streaming multimedia. Also called flow-based algorithms It was aimed at both unicast and multicast applications. Unicast Example :single user streaming a video clip from a news site ...
Cisco RV110W Wireless
... The Cisco RV110W combines wired and wireless connectivity for small offices and remote workers with a highspeed, 802.11n wireless access point; a 4-port 10/100 Mbps Fast Ethernet switch; an intuitive, browser-based device manager; and support for the Cisco FindIT Network Discovery Utility, all at a ...
... The Cisco RV110W combines wired and wireless connectivity for small offices and remote workers with a highspeed, 802.11n wireless access point; a 4-port 10/100 Mbps Fast Ethernet switch; an intuitive, browser-based device manager; and support for the Cisco FindIT Network Discovery Utility, all at a ...
Inter-Process Communication Networks CS 217 • Mechanism by which two processes exchange
... Network Communication • What can go wrong in the network? Bit-level errors (electrical interference) Packet-level errors (congestion) Link and node failures Packets are delayed Packets are deliver out-of-order Third parties eavesdrop ...
... Network Communication • What can go wrong in the network? Bit-level errors (electrical interference) Packet-level errors (congestion) Link and node failures Packets are delayed Packets are deliver out-of-order Third parties eavesdrop ...
21-07-0429-00-0000-JSR
... Includes IP based as well as serial, Bluetooth, etc. Focus is on data-plane send/receive operations ...
... Includes IP based as well as serial, Bluetooth, etc. Focus is on data-plane send/receive operations ...
Exact Time Speaking System
... The paper shows that ETS is well designed and built in such a way that it can easily fulfill the present and future traffic demands. The significance of ETS lies in the fact that it is one of the rare completely domestic solutions in VoIP technology domain. It is one of the family of IMG devices bas ...
... The paper shows that ETS is well designed and built in such a way that it can easily fulfill the present and future traffic demands. The significance of ETS lies in the fact that it is one of the rare completely domestic solutions in VoIP technology domain. It is one of the family of IMG devices bas ...
ppt
... Source describes its desired flow rate and sends this information to the routers and the receiver Network admits requests and reserves resources Source must send at this rate (controlled by network) Provides a sort of “dedicated” connection within an IP packetswitched network Reservation o ...
... Source describes its desired flow rate and sends this information to the routers and the receiver Network admits requests and reserves resources Source must send at this rate (controlled by network) Provides a sort of “dedicated” connection within an IP packetswitched network Reservation o ...
Chapter 11 - Information Technology Gate
... default TCP/IP hosts, meaning that they have all of the software required for taking part in a TCP/IP network. ...
... default TCP/IP hosts, meaning that they have all of the software required for taking part in a TCP/IP network. ...
CISSP Common Body of Knowledge
... The Telecommunications and Network Security domain encompasses the structures, techniques, transport protocols, and security measures used to provide integrity, availability, confidentiality, and authentication for transmissions over private and public communication networks. The candidate is expect ...
... The Telecommunications and Network Security domain encompasses the structures, techniques, transport protocols, and security measures used to provide integrity, availability, confidentiality, and authentication for transmissions over private and public communication networks. The candidate is expect ...
Slide 1
... From Thm. we have short paths between super nodes We can turn this into a path in a real graph by adding at most 2 steps per hop Diameter of the model is O(2 log n) i.e. short paths exist! ...
... From Thm. we have short paths between super nodes We can turn this into a path in a real graph by adding at most 2 steps per hop Diameter of the model is O(2 log n) i.e. short paths exist! ...
NGN Architecture and main Elements
... convenient protocols will establish a path through an MPLS network and will reserve necessary resources to meet pre-defined service requirements for the data path. Manila , Philippines, June 2010 ...
... convenient protocols will establish a path through an MPLS network and will reserve necessary resources to meet pre-defined service requirements for the data path. Manila , Philippines, June 2010 ...