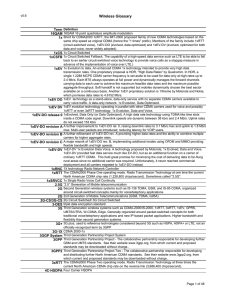
Application Note: How to Evaluate Network and Device Performance
... Mote join state machine timeouts - there is no user control over these timeouts in SmartMesh IP Downstream bandwidth - affects how quickly motes can move from synchronized to operational Number of motes - contention among many motes simultaneously trying to join for limited resources slows down join ...
... Mote join state machine timeouts - there is no user control over these timeouts in SmartMesh IP Downstream bandwidth - affects how quickly motes can move from synchronized to operational Number of motes - contention among many motes simultaneously trying to join for limited resources slows down join ...
static route
... ■ Floating static route • Floating static routes are static routes that are used to provide a backup path to a primary static or dynamic route, in the event of a link failure. The floating static route is only used when the primary route is not available. • To accomplish this, the floating static ro ...
... ■ Floating static route • Floating static routes are static routes that are used to provide a backup path to a primary static or dynamic route, in the event of a link failure. The floating static route is only used when the primary route is not available. • To accomplish this, the floating static ro ...
Chapter 2 Lecture Presentation
... Transfers frames across direct connections Groups bits into frames Detection of bit errors; Retransmission of frames Activation, maintenance, & deactivation of data link connections Medium access control for local area networks Flow control Data Link Layer ...
... Transfers frames across direct connections Groups bits into frames Detection of bit errors; Retransmission of frames Activation, maintenance, & deactivation of data link connections Medium access control for local area networks Flow control Data Link Layer ...
Routing Loops - Chabot College
... Hold – Time during which routes that have been marked invalid will be "held" and not replaced with a new route with a greater distance. This timer determines how long the route is "held" down (marked inaccessible and advertised as unreachable). While in holddown, the route is still used for forwardi ...
... Hold – Time during which routes that have been marked invalid will be "held" and not replaced with a new route with a greater distance. This timer determines how long the route is "held" down (marked inaccessible and advertised as unreachable). While in holddown, the route is still used for forwardi ...
MediaPack 1288
... • Supports short and long haul up to 7.5 Km • Support for emergency / elevator phones that require higher loop current and increased ring voltage • Rich and Powerful SIP normalization and routing mechanisms for seamless interoperability • SIP header manipulation • Extensive fax support includin ...
... • Supports short and long haul up to 7.5 Km • Support for emergency / elevator phones that require higher loop current and increased ring voltage • Rich and Powerful SIP normalization and routing mechanisms for seamless interoperability • SIP header manipulation • Extensive fax support includin ...
HotView Pro™ Mesh Management Software
... The MeshBridge feature is used to connect multiple mesh networks into a single, integrated mesh environment with up to 1000 nodes. The MeshBridge link can be established using a direct, wired connection, or made via any separate switched or routed LAN or WAN infrastructure. MeshBridge helps extend r ...
... The MeshBridge feature is used to connect multiple mesh networks into a single, integrated mesh environment with up to 1000 nodes. The MeshBridge link can be established using a direct, wired connection, or made via any separate switched or routed LAN or WAN infrastructure. MeshBridge helps extend r ...
OSPF & BGP
... The collection of all LSAs is called the linkstate database Each router has and identical link-state database Useful for debugging: Each router has a complete description of the network ...
... The collection of all LSAs is called the linkstate database Each router has and identical link-state database Useful for debugging: Each router has a complete description of the network ...
Secure Universal Mobility for Wireless Internet
... A user should be able to roam seamlessly between heterogeneous radio systems, such as public cellular networks (e.g., GPRS, cdma2000, WCDMA networks), public wire-line networks, enterprise (private) wireless local area networks (LANs) and public wireless LAN hotspot networks that may use IEEE 802.11 ...
... A user should be able to roam seamlessly between heterogeneous radio systems, such as public cellular networks (e.g., GPRS, cdma2000, WCDMA networks), public wire-line networks, enterprise (private) wireless local area networks (LANs) and public wireless LAN hotspot networks that may use IEEE 802.11 ...
Wireless Glossary
... BREW (Binary Runtime Environment for Wireless)—A runtime environment that allows applications to run on a mobile station. Broadband Access Some carrier's marketing name of 1xEV-DO rev. A. BS Bearer Services BS base station BSA Band Selective Amplifier board. BSB BTS Control Block BSC Base Station Co ...
... BREW (Binary Runtime Environment for Wireless)—A runtime environment that allows applications to run on a mobile station. Broadband Access Some carrier's marketing name of 1xEV-DO rev. A. BS Bearer Services BS base station BSA Band Selective Amplifier board. BSB BTS Control Block BSC Base Station Co ...
Dominating Biological Networks
... define as biologically central (BC) the genes that belong to one of the following four gene categories: aging (A) genes, cancer (C) genes, HIV-interacting (HIV) genes, and pathogen-interacting (PI) genes. Our hypothesis is that BC genes, i.e., their protein products (henceforth, we use terms ‘‘gene’ ...
... define as biologically central (BC) the genes that belong to one of the following four gene categories: aging (A) genes, cancer (C) genes, HIV-interacting (HIV) genes, and pathogen-interacting (PI) genes. Our hypothesis is that BC genes, i.e., their protein products (henceforth, we use terms ‘‘gene’ ...
Word
... transmit voice or data from either a VHF or UHF radio unit to other communications services (such as Telstra’s fixed or mobile services) if you have pre-arranged access; and ...
... transmit voice or data from either a VHF or UHF radio unit to other communications services (such as Telstra’s fixed or mobile services) if you have pre-arranged access; and ...
Military grade wireless ad hoc networks
... • A chain of trust can be used • Authenticity of every packet must be verified before using it • Impacts of hostile nodes shall be minimized, especially in the radio network • Decisions can be based on the trust level of the information and/or sending node ...
... • A chain of trust can be used • Authenticity of every packet must be verified before using it • Impacts of hostile nodes shall be minimized, especially in the radio network • Decisions can be based on the trust level of the information and/or sending node ...
Enterprise Council Comms overview
... Layer 2 Only Networks • Rarely deployed but for some environments they may make sense • No routing implemented across the infrastructure • A single broadcast domain for every user, Layer 2 broadcast traffic seen by every user across the campus • Multicast Filtering using IGMP Snooping can still be i ...
... Layer 2 Only Networks • Rarely deployed but for some environments they may make sense • No routing implemented across the infrastructure • A single broadcast domain for every user, Layer 2 broadcast traffic seen by every user across the campus • Multicast Filtering using IGMP Snooping can still be i ...
User influence based on social network and telecommunication
... A social network is a structure made up with individuals or organizations that are connected in some way. Today the most popular type of social networks are online social networks, such as Facebook, Twitter, LinkedIn and many more. With the creation and rising popularity of online social networks it ...
... A social network is a structure made up with individuals or organizations that are connected in some way. Today the most popular type of social networks are online social networks, such as Facebook, Twitter, LinkedIn and many more. With the creation and rising popularity of online social networks it ...
P2P networks course
... Data is replicated (unlike Chord) Finding an object requires limited multicast (request data from 4 super nodes, then 8 super nodes, then 16 etc.) Skype claims that any user that has been logged on in the last 72 hours can be found ...
... Data is replicated (unlike Chord) Finding an object requires limited multicast (request data from 4 super nodes, then 8 super nodes, then 16 etc.) Skype claims that any user that has been logged on in the last 72 hours can be found ...
SOHO Firewalls using Shorewall
... • A kernel that supports netfilter. I've tested with 2.4.2 2.4.20. 2.4.20 required for full functionality. • iptables 1.2 or later but beware version 1.2.3. Version 1.2.7a required for full functionality. • iproute ("ip" utility). The iproute package is included with most distributions but may not b ...
... • A kernel that supports netfilter. I've tested with 2.4.2 2.4.20. 2.4.20 required for full functionality. • iptables 1.2 or later but beware version 1.2.3. Version 1.2.7a required for full functionality. • iproute ("ip" utility). The iproute package is included with most distributions but may not b ...
Subtle Waves Template
... • IP traceback allows the victim to identify the attack sources even in the presence of IP spoofing • There are some traceback schemes have been proposed for Internet: ...
... • IP traceback allows the victim to identify the attack sources even in the presence of IP spoofing • There are some traceback schemes have been proposed for Internet: ...
node - Open Learning Environment
... • Clients interacts with Servers after finding useful information provided by Indexing services • No intelligence in the network ...
... • Clients interacts with Servers after finding useful information provided by Indexing services • No intelligence in the network ...
A 50-Gb/s IP Router
... Header whose destination misses in the route cache Headers with errors Header with IP options Datagrams that must be fragmented ...
... Header whose destination misses in the route cache Headers with errors Header with IP options Datagrams that must be fragmented ...
An Incentive Driven Lookup Protocol For Chord-Based Peer-to-Peer (P2P) Networks
... always hold good in large-scale open systems and have to be done away with in order to make P2P systems reliable, robust and realize their true commercial potential. Moreover, it has been pointed out that free-riding is one of the most significant problems being faced by today’s P2P networks [2]. We ...
... always hold good in large-scale open systems and have to be done away with in order to make P2P systems reliable, robust and realize their true commercial potential. Moreover, it has been pointed out that free-riding is one of the most significant problems being faced by today’s P2P networks [2]. We ...
Firewall - Gadjah Mada University
... • Firewalls are an effective start to securing a network. Not a finish. • Care must be taken to construct an appropriate set of rules that will enforce your policy. ...
... • Firewalls are an effective start to securing a network. Not a finish. • Care must be taken to construct an appropriate set of rules that will enforce your policy. ...
The Composition of the Output Layer Architecture in a
... structure of the Networks (Lippmann, 1987; Caudill, 1988; Pao, 1989; Widrow and Lehr, 1990; Paola and Schowengerdt, 1995; Fischer and Staufer, 1999), application of Networks (Miller, Kaminsky and Rana, 1994; Yang, Meer and Bakker, 1999; Atkinson and Tatnall, 1997), and improvements to Neural Network ...
... structure of the Networks (Lippmann, 1987; Caudill, 1988; Pao, 1989; Widrow and Lehr, 1990; Paola and Schowengerdt, 1995; Fischer and Staufer, 1999), application of Networks (Miller, Kaminsky and Rana, 1994; Yang, Meer and Bakker, 1999; Atkinson and Tatnall, 1997), and improvements to Neural Network ...
CEN 4500C Computer Networks Fundamentals
... [more: Technically speaking, UDP would provide a better trade-off since voice/video apps (especially interactive) tolerate loss (up to ~10%) but do not tolerate delay or jitter. TCP’s congestion control and reliability mechanisms lead to 100% delivery but lead to variable delays (i.e., increased jit ...
... [more: Technically speaking, UDP would provide a better trade-off since voice/video apps (especially interactive) tolerate loss (up to ~10%) but do not tolerate delay or jitter. TCP’s congestion control and reliability mechanisms lead to 100% delivery but lead to variable delays (i.e., increased jit ...
Heading towards 5G networks: market drivers
... › A modular optical solution is key to fulfil fiber plant constraints in 4G networks › High densification in 5G will require even more building blocks to implement bridged fronthaul Ericsson Internal | © Ericsson AB 2016 | 2016-09-17 | Page 11 ...
... › A modular optical solution is key to fulfil fiber plant constraints in 4G networks › High densification in 5G will require even more building blocks to implement bridged fronthaul Ericsson Internal | © Ericsson AB 2016 | 2016-09-17 | Page 11 ...