Chapter_5 - Eastern Illinois University
... Infrared light can also carry data signals, but for short distances with a clear line of sight Best for transmitting between notebook computers and a printer, or between a PDA and a desktop computer Laser light can also carry data signals, for a longer distance, but requires a clear line of si ...
... Infrared light can also carry data signals, but for short distances with a clear line of sight Best for transmitting between notebook computers and a printer, or between a PDA and a desktop computer Laser light can also carry data signals, for a longer distance, but requires a clear line of si ...
Introduction to Routing and Packet Forwarding
... table you must have directly connected networks ...
... table you must have directly connected networks ...
riku kaura-aho scalable iot traffic generation system
... [6]. Cloud is the environment for future networks [7; 8], where also massive amount of programmable things can be ran. And last but not the least, IoT contains massive amount of different networked devices with a need for new types of connectivity. These three technologies are combined and studied i ...
... [6]. Cloud is the environment for future networks [7; 8], where also massive amount of programmable things can be ran. And last but not the least, IoT contains massive amount of different networked devices with a need for new types of connectivity. These three technologies are combined and studied i ...
Intrusion Detection Techniques for Mobile Wireless
... gateways, the mobile ad-hoc environment does not have such traffic concentration points where the IDS can collect audit data for the entire network. Therefore, at any one time, the only available audit trace will be limited to communication activities taking place within the radio range, and the int ...
... gateways, the mobile ad-hoc environment does not have such traffic concentration points where the IDS can collect audit data for the entire network. Therefore, at any one time, the only available audit trace will be limited to communication activities taking place within the radio range, and the int ...
Slides
... • Can use the above techniques to also protect IP traffic • If a link fails all the traffic that would go through the link is sent over the backup LSP • Similar for node failures – But in this case, do I know the nnhop for IP? ...
... • Can use the above techniques to also protect IP traffic • If a link fails all the traffic that would go through the link is sent over the backup LSP • Similar for node failures – But in this case, do I know the nnhop for IP? ...
Compensation of Asymmetrical Latency for Ethernet Clock
... the link delay between the nodes remains constant once the physical connection is established, but varies with each new re-establishment. Although the delay is constant for an active link, it still induces asymmetry as the delay at which the PHY locks in is unknown. B. Cable Induced Asymmetry The ca ...
... the link delay between the nodes remains constant once the physical connection is established, but varies with each new re-establishment. Although the delay is constant for an active link, it still induces asymmetry as the delay at which the PHY locks in is unknown. B. Cable Induced Asymmetry The ca ...
Kein Folientitel
... nearly-optimal routes, under a variety of conditions. During stable periods: Little overhead, can reuse already-determined routes. Yields lowlatency, low-communication reliable message delivery. When network changes: Adapts reasonably quickly. Diagnoses broken routes and finds new ones. Discrete ...
... nearly-optimal routes, under a variety of conditions. During stable periods: Little overhead, can reuse already-determined routes. Yields lowlatency, low-communication reliable message delivery. When network changes: Adapts reasonably quickly. Diagnoses broken routes and finds new ones. Discrete ...
Notes on the course
... to know who hold it. If someone had it, it returned to the initial user all informations regarding the user that had the content: in this way the two hosts can exchanged the content using a direct connection. ...
... to know who hold it. If someone had it, it returned to the initial user all informations regarding the user that had the content: in this way the two hosts can exchanged the content using a direct connection. ...
Designing RS-485 Circuits
... RS-422 allows just one driver with multiple receivers whereas RS-485 supports multiple drivers and receivers. The specification document (TIA/ EIA-485-A) defines the electrical characteristics of the line and its drivers and receivers. There are brief suggestions relating to terminations and wiring, ...
... RS-422 allows just one driver with multiple receivers whereas RS-485 supports multiple drivers and receivers. The specification document (TIA/ EIA-485-A) defines the electrical characteristics of the line and its drivers and receivers. There are brief suggestions relating to terminations and wiring, ...
Integrated Voice and Data Network
... The Elite architecture allows different dispatching shifts to use different screen configurations (if so desired), depending upon their dispatch requirements. In the event that a dispatch center is inaccessible, due to an evacuation, etc., the inaccessible dispatch site’s screen configuration(s) can ...
... The Elite architecture allows different dispatching shifts to use different screen configurations (if so desired), depending upon their dispatch requirements. In the event that a dispatch center is inaccessible, due to an evacuation, etc., the inaccessible dispatch site’s screen configuration(s) can ...
Manual - Maxon Australia
... All data and information contained in or disclosed by this document are confidential and proprietary information of Maxon Australia, and all rights therein are expressly reserved. By accepting this material, the recipient agrees that this material and the information contained therein are held in co ...
... All data and information contained in or disclosed by this document are confidential and proprietary information of Maxon Australia, and all rights therein are expressly reserved. By accepting this material, the recipient agrees that this material and the information contained therein are held in co ...
flegkas layout - HMC Computer Science
... physical network resources and providing network provisionmany instances of policy consumers. Every instance of the PC is ing directives in order to accommodate the predicted traffic attached to the component that is influenced by the policies demands. The lower level of the traffic engineering part ...
... physical network resources and providing network provisionmany instances of policy consumers. Every instance of the PC is ing directives in order to accommodate the predicted traffic attached to the component that is influenced by the policies demands. The lower level of the traffic engineering part ...
Dual-Core SoC Design to Support Inter
... Distributed Satellite System (DSS) • Satellites that provide multi-point sensing • Low cost, redundancy, flexibility • Types of DSS: • Formation Flying: strict formation • Clustering Mission: satellites are loosely coupled around each other • Virtual Satellite Mission (fractioned mission): a satelli ...
... Distributed Satellite System (DSS) • Satellites that provide multi-point sensing • Low cost, redundancy, flexibility • Types of DSS: • Formation Flying: strict formation • Clustering Mission: satellites are loosely coupled around each other • Virtual Satellite Mission (fractioned mission): a satelli ...
Modern Accounting Information System Security
... network) environment, the accounting information system under B/S environment features the following characteristics: The Transmission Area of Accounting Information is Increased Sharply The accounting information system develops from local area network to wide area network which increases the trans ...
... network) environment, the accounting information system under B/S environment features the following characteristics: The Transmission Area of Accounting Information is Increased Sharply The accounting information system develops from local area network to wide area network which increases the trans ...
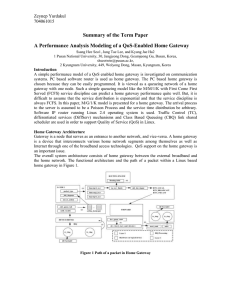
A performance analysis modeling of a QoS
... In order to QoS support, the different flows need different packet processing. And the rules have to be set on the home gateway. In this experiment, the classification is based on port number. Once the home gateway received a packet, it will extract the IP packet and will process differently accordi ...
... In order to QoS support, the different flows need different packet processing. And the rules have to be set on the home gateway. In this experiment, the classification is based on port number. Once the home gateway received a packet, it will extract the IP packet and will process differently accordi ...
Online Classification of Nonstationary Data Streams
... is trained on a batch of the most recent user transactions. However, the minimum batch size (80 examples) makes the system vulnerable to short-term cyber attacks. According to Fawcett and Provost [8], the most efficient method for detecting an intruder is the profiling approach, where a model of nor ...
... is trained on a batch of the most recent user transactions. However, the minimum batch size (80 examples) makes the system vulnerable to short-term cyber attacks. According to Fawcett and Provost [8], the most efficient method for detecting an intruder is the profiling approach, where a model of nor ...
An Efficient Quorum-based Fault-Tolerant Approach for Mobility
... To balance the backup load, the author uses quorum to achieve the goal Per-allocate the storage place with location by using quorum ...
... To balance the backup load, the author uses quorum to achieve the goal Per-allocate the storage place with location by using quorum ...
Yingwu Zhu
... In short: a peer-to-peer lookup service Solves problem of locating a data item in a collection of distributed nodes, considering frequent node arrivals and departures Core operation in most p2p systems is efficient location of data items Supports just one operation: given a key, it maps the key onto ...
... In short: a peer-to-peer lookup service Solves problem of locating a data item in a collection of distributed nodes, considering frequent node arrivals and departures Core operation in most p2p systems is efficient location of data items Supports just one operation: given a key, it maps the key onto ...
IPv6 in Greek School Network (GSN) - seeren-2
... – Monitoring of operation and further adoption of ΑΑΑΑ record for the same name ...
... – Monitoring of operation and further adoption of ΑΑΑΑ record for the same name ...
TE2331953204
... The following is a list of quantitative metrics that can be used to assess the performance of any routing protocol. (1) Average end-to-end delay of data packets —It is caused by buffering during route discovery latency, queuing at the interface queue, retransmission delays at the MAC, and propagatio ...
... The following is a list of quantitative metrics that can be used to assess the performance of any routing protocol. (1) Average end-to-end delay of data packets —It is caused by buffering during route discovery latency, queuing at the interface queue, retransmission delays at the MAC, and propagatio ...
PPPoE priekšrocības Interneta pakalpojumu sniedzējiem
... MikroTik Mission We create Intel (PC) based network solutions, because: ...
... MikroTik Mission We create Intel (PC) based network solutions, because: ...
Submitted version - QMRO Home
... application concept phase, IoT now encompasses access networks (such as sensor, RFID, and mobile devices), the backbone network structure (such as cloud computing, ubiquitous computing), as well as middleware techniques, embedded system control, IoT protocols, IoT signal processing, and IoT security ...
... application concept phase, IoT now encompasses access networks (such as sensor, RFID, and mobile devices), the backbone network structure (such as cloud computing, ubiquitous computing), as well as middleware techniques, embedded system control, IoT protocols, IoT signal processing, and IoT security ...
2-1 ATM MPLS
... Store-and-forward transmission Multiple packets may arrive at once Need buffer space for temporary storage Multiplexing on a link ...
... Store-and-forward transmission Multiple packets may arrive at once Need buffer space for temporary storage Multiplexing on a link ...
Slide 1 - Hot Interconnects
... Route around stalled or down links If a link goes down, adaptive routing mask updated in hardware to exclude it OS traffic uses adaptive routing only, recovers from finite loss of packets Quiesce and re-route to repair deterministic routes Congestion feedback to allow ...
... Route around stalled or down links If a link goes down, adaptive routing mask updated in hardware to exclude it OS traffic uses adaptive routing only, recovers from finite loss of packets Quiesce and re-route to repair deterministic routes Congestion feedback to allow ...