Cisco ACS Radius Migration with Huawei
... This document is generated to explain how to migrate the Cisco Radius server (ACS) with Huawei network elements (routers, switches, and firewalls). The procedure focused on two main criteria: 1- Cisco ACS configuration 2- Network elements configuration These will be covered respectively. Notes: 1- T ...
... This document is generated to explain how to migrate the Cisco Radius server (ACS) with Huawei network elements (routers, switches, and firewalls). The procedure focused on two main criteria: 1- Cisco ACS configuration 2- Network elements configuration These will be covered respectively. Notes: 1- T ...
Document
... exponential growth of the Internet and the scalability of Internet routing tables. The IETF was also concerned with the eventual exhaustion of 32-bit IPv4 address space. Projections were that this problem would reach its critical state by 1994 or 1995. IETF’s response was the concept of Supernetting ...
... exponential growth of the Internet and the scalability of Internet routing tables. The IETF was also concerned with the eventual exhaustion of 32-bit IPv4 address space. Projections were that this problem would reach its critical state by 1994 or 1995. IETF’s response was the concept of Supernetting ...
Chapter 6 slides, Computer Networking, 3rd edition
... wired network relay - responsible for sending packets between wired network and wireless host(s) in its “area” e.g., cell towers, 802.11 access points ...
... wired network relay - responsible for sending packets between wired network and wireless host(s) in its “area” e.g., cell towers, 802.11 access points ...
"Providing a Bidirectional Abstraction for Unidirectional Ad Hoc Networks"
... Ad-hoc On-demand Distanve Vector routing (AODV) [1] is an on-demand routing protocol that has been designed for bidirectional networks. AODV broadcasts route requests (RREQs) and uses the bidirectional links (reverse routes) to transmit route replies (RREPs). In fact, since AODV is unaware of uni- o ...
... Ad-hoc On-demand Distanve Vector routing (AODV) [1] is an on-demand routing protocol that has been designed for bidirectional networks. AODV broadcasts route requests (RREQs) and uses the bidirectional links (reverse routes) to transmit route replies (RREPs). In fact, since AODV is unaware of uni- o ...
Computer and Networking Security
... accessed Web pages and provide them when requested from a client instead of accessing the real Web server. • To configure any proxy server, you need the following information: − IP address of the proxy server − Port number of the proxy server − Optionally a username and password, but some organizati ...
... accessed Web pages and provide them when requested from a client instead of accessing the real Web server. • To configure any proxy server, you need the following information: − IP address of the proxy server − Port number of the proxy server − Optionally a username and password, but some organizati ...
Design and Optimization of Wireless Remote Monitoring and Control System
... the Internet. On the other hand, the gateway also receives control commands from the web service. When the gateway receives the control command from the web service, it forwards the command to the network coordinator of the wireless sensor network. Moreover, the gateway also works as a local monitor ...
... the Internet. On the other hand, the gateway also receives control commands from the web service. When the gateway receives the control command from the web service, it forwards the command to the network coordinator of the wireless sensor network. Moreover, the gateway also works as a local monitor ...
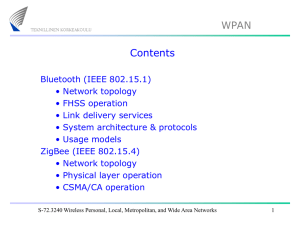
Lecture 2: WPAN
... Higher protocol layers (1) The operation of higher protocol layers is outside the scope of the IEEE 802.15.1 standard (but included in the Bluetooth SIG standards). The usage of these protocols depends on the specific Bluetooth profile in question. A large number of Bluetooth profiles have been defi ...
... Higher protocol layers (1) The operation of higher protocol layers is outside the scope of the IEEE 802.15.1 standard (but included in the Bluetooth SIG standards). The usage of these protocols depends on the specific Bluetooth profile in question. A large number of Bluetooth profiles have been defi ...
Operating manual for FMA21
... operating distance compared to previous models). With the integrated USB interface changes in software (FIE regulation updates, firmware updates, new functions etc.) can be updated at any time without chip changing. The FMA21 always adapts to the latest requirements. Together with the appropriate st ...
... operating distance compared to previous models). With the integrated USB interface changes in software (FIE regulation updates, firmware updates, new functions etc.) can be updated at any time without chip changing. The FMA21 always adapts to the latest requirements. Together with the appropriate st ...
Do SKU and Network Complexity Drive Inventory Levels?
... • How many stocking locations are used for each SKU • The more customer-facing locations for an SKU, the greater the forecast error for that SKU ...
... • How many stocking locations are used for each SKU • The more customer-facing locations for an SKU, the greater the forecast error for that SKU ...
Abstract - PG Embedded systems
... The first objective of a multicast protocol is to convey packets from a source to the members of a multicast group with an acceptable quality of service (QoS) [2], [3]. QoS is the performance level of a service offered by the network, in general [1]. Specifically, QoS in voice communications necessi ...
... The first objective of a multicast protocol is to convey packets from a source to the members of a multicast group with an acceptable quality of service (QoS) [2], [3]. QoS is the performance level of a service offered by the network, in general [1]. Specifically, QoS in voice communications necessi ...
Power Point Chapter 06 CCNA2
... • This table contains the learned networks and associated ports for those networks. • Routers use routing protocols to manage information received from other routers and its interfaces. • The routing protocol learns all available routes, places the best routes into the routing table, and removes rou ...
... • This table contains the learned networks and associated ports for those networks. • Routers use routing protocols to manage information received from other routers and its interfaces. • The routing protocol learns all available routes, places the best routes into the routing table, and removes rou ...
IT Management System Scalability for the Enterprise
... Most deployments are based on a single product instance that monitors the infrastructure or applications. As your IT environment grows, you may find that you are no longer able to monitor everything you would like at your desired polling frequency. In this case, you can deploy an Additional Polling ...
... Most deployments are based on a single product instance that monitors the infrastructure or applications. As your IT environment grows, you may find that you are no longer able to monitor everything you would like at your desired polling frequency. In this case, you can deploy an Additional Polling ...
20061004-IMSP2P
... • Network is unaware of the applications, this makes it scalable • Nothing should be done in the network that can be done in an end-system • Quality of Service (QoS) is a matter of bandwidth availability and not of central control ...
... • Network is unaware of the applications, this makes it scalable • Nothing should be done in the network that can be done in an end-system • Quality of Service (QoS) is a matter of bandwidth availability and not of central control ...
Energy and Latency Control in Low Duty Cycle MAC Protocols
... then proceed only on reinforced paths. With FPA, the fast path setup message would be piggybacked on the first data message sent on a reinforced path. The same approach would be used with one-phase push diffusion [3], even though that protocol omits interest messages. In one-phase pull diffusion, af ...
... then proceed only on reinforced paths. With FPA, the fast path setup message would be piggybacked on the first data message sent on a reinforced path. The same approach would be used with one-phase push diffusion [3], even though that protocol omits interest messages. In one-phase pull diffusion, af ...
SYSTEM ARCHITECTURE OF A WIRELESS BODY AREA SENSOR
... uploads when a link becomes available. This organization allows full mobility of users with secure and near real time health information uploads. A pivotal part of the telemedical system is tier 1 – wireless body area sensor network. It comprises a number of intelligent nodes, each capable of sensin ...
... uploads when a link becomes available. This organization allows full mobility of users with secure and near real time health information uploads. A pivotal part of the telemedical system is tier 1 – wireless body area sensor network. It comprises a number of intelligent nodes, each capable of sensin ...
Master
... MRP (Metro Ring Protocol). In the event of the loss of a network segment, MRP activates a redundant link within tenths of a second and restore connectivity. ...
... MRP (Metro Ring Protocol). In the event of the loss of a network segment, MRP activates a redundant link within tenths of a second and restore connectivity. ...
Chapter 6: Wireless and Mobile Networks
... Ad hoc mode ❒ no base stations ❒ nodes can only transmit to other nodes within link coverage ❒ nodes organize themselves into a network: route among themselves ...
... Ad hoc mode ❒ no base stations ❒ nodes can only transmit to other nodes within link coverage ❒ nodes organize themselves into a network: route among themselves ...
HP Networking guide to hardening Comware
... Filtering fragmented IP packets can pose a challenge to security devices. This is because the Layer 4 information that is used to filter TCP and UDP packets is only present in the initial fragment. HP Comware software uses a specific method to check non-initial fragments against configured access li ...
... Filtering fragmented IP packets can pose a challenge to security devices. This is because the Layer 4 information that is used to filter TCP and UDP packets is only present in the initial fragment. HP Comware software uses a specific method to check non-initial fragments against configured access li ...
Finite State Automata that Recurrent Cascade
... Section 6 also accounts for many other FSA which are not representable by RCC. In fact, the theorem identifies an inflnite number of other classes of non-representable FSA (for p = 3, P =4, P = 5, ... ). Each class itself of course contains an infinite number of machines. Careful examination of the ...
... Section 6 also accounts for many other FSA which are not representable by RCC. In fact, the theorem identifies an inflnite number of other classes of non-representable FSA (for p = 3, P =4, P = 5, ... ). Each class itself of course contains an infinite number of machines. Careful examination of the ...
Scoring functions for learning Bayesian networks
... Θ taking value 0, they do not need to appear in the description of Θ. The same distribution (or probability value) might occur several times in Θ leading to patterns that can be exploited to compress Θ significantly. ...
... Θ taking value 0, they do not need to appear in the description of Θ. The same distribution (or probability value) might occur several times in Θ leading to patterns that can be exploited to compress Θ significantly. ...
Ethernet frames - La Salle University
... • So before transmitting a large packet, Computer 1 issues a small control packet indicating it will transmit a larger packet. • The Computer 2 issues a reply packet which is read by all computers in its vicinity (including Computer 3) that it expects to receive a message from Computer 1. Computer 3 ...
... • So before transmitting a large packet, Computer 1 issues a small control packet indicating it will transmit a larger packet. • The Computer 2 issues a reply packet which is read by all computers in its vicinity (including Computer 3) that it expects to receive a message from Computer 1. Computer 3 ...
Dan's slide set
... What we get from UDP • NO guaranteed message delivery • NO guaranteed same order message delivery • NO ability to send arbitrarily large messages • NO flow control • Support multiple application processes on each host • NO network congestion control ...
... What we get from UDP • NO guaranteed message delivery • NO guaranteed same order message delivery • NO ability to send arbitrarily large messages • NO flow control • Support multiple application processes on each host • NO network congestion control ...