Designing an LTE Network Using EDX SignalPro
... (the eNodeB’s) are known. This is not the case for uplink interference, which is based on the location and usage of the subscribers’ terminals (UE’s). Predictions of uplink interference can be made based on statistical studies or Monte Carlo simulations, but it is important to understand the advanta ...
... (the eNodeB’s) are known. This is not the case for uplink interference, which is based on the location and usage of the subscribers’ terminals (UE’s). Predictions of uplink interference can be made based on statistical studies or Monte Carlo simulations, but it is important to understand the advanta ...
Integrating Cisco Press Resources into the Academy Classroom
... Before the introduction of bridges, the LAN acted as a broadcast medium The term unicast MAC address identifies a single NIC or Ethernet interface Sometimes a computer needs to send a frame that will reach all devices on the LAN; it uses a broadcast address: FFFF.FFFF.FFFF All devices must process d ...
... Before the introduction of bridges, the LAN acted as a broadcast medium The term unicast MAC address identifies a single NIC or Ethernet interface Sometimes a computer needs to send a frame that will reach all devices on the LAN; it uses a broadcast address: FFFF.FFFF.FFFF All devices must process d ...
MPLS Forum Tutorials - Systems and Computer Engineering
... Network will deliver these packets whenever resources available Node should make sure that these packets don’t get ‘starved’ Packets with an unidentified DSCP should also receives this PHB ...
... Network will deliver these packets whenever resources available Node should make sure that these packets don’t get ‘starved’ Packets with an unidentified DSCP should also receives this PHB ...
Exam Topics in This Chapter
... OpenDNS, and CloudLock, to expand its security portfolio. The Cisco ASA FirePOWER module provides NGIPS, Application Visibility and Control (AVC), URL filtering, and Advanced Malware Protection (AMP). This module runs as a separate application from the classic Cisco ASA software. The Cisco ASA FireP ...
... OpenDNS, and CloudLock, to expand its security portfolio. The Cisco ASA FirePOWER module provides NGIPS, Application Visibility and Control (AVC), URL filtering, and Advanced Malware Protection (AMP). This module runs as a separate application from the classic Cisco ASA software. The Cisco ASA FireP ...
Intrusion Detection Techniques for Mobile Wireless
... vironment. Compared with wired networks where traffic monitoring is usually done at switches, routers and gateways, the mobile ad-hoc environment does not have such traffic concentration points where the IDS can collect audit data for the entire network. Therefore, at any one time, the only availabl ...
... vironment. Compared with wired networks where traffic monitoring is usually done at switches, routers and gateways, the mobile ad-hoc environment does not have such traffic concentration points where the IDS can collect audit data for the entire network. Therefore, at any one time, the only availabl ...
$doc.title
... of computers. The fundamental problem is that the most obvious way to build a computer network—by connecting each pair of computers with a dedicated link—is both prohibitively expensive (because of the sheer number of links required, a number that grows quadratically with the network size) and techn ...
... of computers. The fundamental problem is that the most obvious way to build a computer network—by connecting each pair of computers with a dedicated link—is both prohibitively expensive (because of the sheer number of links required, a number that grows quadratically with the network size) and techn ...
Socket Programming
... sock: integer, socket descriptor queuelen: integer, # of active participants that can “wait” for a connection listen is non-blocking: returns immediately int s = accept(sock, &name, &namelen); s: integer, the new socket (used for data-transfer) sock: integer, the original socket (being l ...
... sock: integer, socket descriptor queuelen: integer, # of active participants that can “wait” for a connection listen is non-blocking: returns immediately int s = accept(sock, &name, &namelen); s: integer, the new socket (used for data-transfer) sock: integer, the original socket (being l ...
Integrated Voice and Data Network
... (WAN) switch. The WAN Switch is a chassis-based device with redundant power supplies, redundant CPUs, network management, and back plane switching; all which increase availability. The switch will have 1:1 redundant cards and monitor itself for module failures. If a card failure is detected, it auto ...
... (WAN) switch. The WAN Switch is a chassis-based device with redundant power supplies, redundant CPUs, network management, and back plane switching; all which increase availability. The switch will have 1:1 redundant cards and monitor itself for module failures. If a card failure is detected, it auto ...
PPT
... • Technology did not match people’s experience with IP • deploying ATM in LAN is complex (e.g. broadcast) • supporting connection-less service model on connection-based technology • With IP over ATM, a lot of functionality is replicated • Currently used as a datalink layer supporting IP. Lecture #19 ...
... • Technology did not match people’s experience with IP • deploying ATM in LAN is complex (e.g. broadcast) • supporting connection-less service model on connection-based technology • With IP over ATM, a lot of functionality is replicated • Currently used as a datalink layer supporting IP. Lecture #19 ...
Growing University in Namibia Moves to Next-Generation
... years ago when the previous vendor stopped providing support. When Maartens came on board about three years ago, he recognized the growing security threats and the need for increased scalability. He began moving the university toward a virtualized solution with two Cisco® ASA 5585-X Series Next-Gene ...
... years ago when the previous vendor stopped providing support. When Maartens came on board about three years ago, he recognized the growing security threats and the need for increased scalability. He began moving the university toward a virtualized solution with two Cisco® ASA 5585-X Series Next-Gene ...
Patch Management Integration November 11, 2014 (Revision 20)
... Tenable’s Unified Security Monitoring (USM) product suite provides great flexibility in scanning methods to better serve our customers’ varying scanning requirements and restrictions. Customers can perform passive scanning, active network scans, or scan with credentials for more accurate results wit ...
... Tenable’s Unified Security Monitoring (USM) product suite provides great flexibility in scanning methods to better serve our customers’ varying scanning requirements and restrictions. Customers can perform passive scanning, active network scans, or scan with credentials for more accurate results wit ...
3. MAC Protocol Criteria - Working Group
... optimized. Since some proposals can be submitted as only a MAC or PHY, the proposals should estimate as much systems cost, typical MAC functions are shown in Figure 1. Block Diagram of MAC and while typical PHY functions are shown in Figure 2. Logical blocks in the transceiver PHY layer ...
... optimized. Since some proposals can be submitted as only a MAC or PHY, the proposals should estimate as much systems cost, typical MAC functions are shown in Figure 1. Block Diagram of MAC and while typical PHY functions are shown in Figure 2. Logical blocks in the transceiver PHY layer ...
Chapter09
... Core(config-router)#network 192.168.10.0 Core(config-router)#network 10.0.0.0 Core(config-router)#no auto-summary Core(config-router)#interface ethernet 0 Core(config-if)#ip summary-address eigrp 10 ...
... Core(config-router)#network 192.168.10.0 Core(config-router)#network 10.0.0.0 Core(config-router)#no auto-summary Core(config-router)#interface ethernet 0 Core(config-if)#ip summary-address eigrp 10 ...
Sample
... business and user applications will this network have to support? D) All of the above. Answer: D Diff: 1 Page Ref: 22 32) A network can fall into one of four categories. What are the categories? A) local area network; backbone network; metropolitan area network; wide area network B) LAN, BN, MAN, WA ...
... business and user applications will this network have to support? D) All of the above. Answer: D Diff: 1 Page Ref: 22 32) A network can fall into one of four categories. What are the categories? A) local area network; backbone network; metropolitan area network; wide area network B) LAN, BN, MAN, WA ...
Test_King_CompTIA_N1..
... All users in an office cannot access the WAN. The office system was up and running this morning. At 10 A.M. there was an installation of a new employee, including telephone and network connections. You gather detailed information about the problem from the office and determine that no other WAN conn ...
... All users in an office cannot access the WAN. The office system was up and running this morning. At 10 A.M. there was an installation of a new employee, including telephone and network connections. You gather detailed information about the problem from the office and determine that no other WAN conn ...
H.225 Call Signaling
... An H.323 zone is a collection of all terminals, gateways, and MCUs managed by a single gatekeeper (see Figure 2). A zone includes at least one terminal and may include gateways or MCUs. A zone has only one gatekeeper. A zone may be independent of network topology and may be comprised of multiple net ...
... An H.323 zone is a collection of all terminals, gateways, and MCUs managed by a single gatekeeper (see Figure 2). A zone includes at least one terminal and may include gateways or MCUs. A zone has only one gatekeeper. A zone may be independent of network topology and may be comprised of multiple net ...
IMC conference
... Select a basis set of k paths that fully describe O(n2) paths (k «O(n2)) • Monitor the loss rates of k paths, and infer the loss rates of all other paths • Applicable for any additive metrics, like latency ...
... Select a basis set of k paths that fully describe O(n2) paths (k «O(n2)) • Monitor the loss rates of k paths, and infer the loss rates of all other paths • Applicable for any additive metrics, like latency ...
UNI - MEF
... Frame Delay Variation is therefore the variation in this delay for a number of frames. This delay is an important factor in the transmission of unbuffered video and where variation occurs in the millisecond range can affect voice quality. For data can cause a number of undesirable effects such as pe ...
... Frame Delay Variation is therefore the variation in this delay for a number of frames. This delay is an important factor in the transmission of unbuffered video and where variation occurs in the millisecond range can affect voice quality. For data can cause a number of undesirable effects such as pe ...
INTERNET OF THINGS (IOT) RFID TEMPERATURE SMART SENSOR
... Internet of Things (IOT) can be defined as a network infrastructure connecting physical and virtual objects through the exploitation of data capture and communication capabilities. The infrastructure is made up of existing and evolving network and internet development which will offer specific objec ...
... Internet of Things (IOT) can be defined as a network infrastructure connecting physical and virtual objects through the exploitation of data capture and communication capabilities. The infrastructure is made up of existing and evolving network and internet development which will offer specific objec ...
Pre-Recover from a Node Failure in Ad hoc Network Using
... nodes to communicate without prior infrastructure. Due to limited range of each wireless node communication is built between two nodes are usually established through a number of intermediate nodes. The sensors serve as wireless data acquisition devices for the more powerful actor nodes that process ...
... nodes to communicate without prior infrastructure. Due to limited range of each wireless node communication is built between two nodes are usually established through a number of intermediate nodes. The sensors serve as wireless data acquisition devices for the more powerful actor nodes that process ...
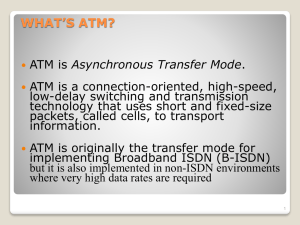
ATM
... A standard for transmitting voice, video and data at the same time over fiber optic telephone lines The goal of B-ISDN is to accommodate all existing services along with those that will come in the future. The services that BISDN will support include narrowband services, such as voice, voiceband dat ...
... A standard for transmitting voice, video and data at the same time over fiber optic telephone lines The goal of B-ISDN is to accommodate all existing services along with those that will come in the future. The services that BISDN will support include narrowband services, such as voice, voiceband dat ...