Virtualization Group
... – Rich specification for optical network setup – Depends on how fast the setup/teardown needs – May hide changes in physical topology--e.g., delay ...
... – Rich specification for optical network setup – Depends on how fast the setup/teardown needs – May hide changes in physical topology--e.g., delay ...
Network Topology - Department of Computing
... hub/switch is restricted based on cable used. ◦ With UTP cable, distance limited to 100m. Popular topology for LAN (local area networks) Adv: Failure of any computer does not affect other communications in the network Disadv: Failure of hub/switch can bring the network down, also called SPF( Single ...
... hub/switch is restricted based on cable used. ◦ With UTP cable, distance limited to 100m. Popular topology for LAN (local area networks) Adv: Failure of any computer does not affect other communications in the network Disadv: Failure of hub/switch can bring the network down, also called SPF( Single ...
Gigamon - ForeScout
... platform lets you see and control what is connected to your network no matter the user or device. ForeScout’s real-time endpoint classification, policy assessment and threat remediation capabilities offer the means for organizations to apply strong access control policies, as well as find and fix en ...
... platform lets you see and control what is connected to your network no matter the user or device. ForeScout’s real-time endpoint classification, policy assessment and threat remediation capabilities offer the means for organizations to apply strong access control policies, as well as find and fix en ...
CST125 - Suffolk County Community College
... DNS services. Active Directory Service. User account and groups, and network printer setup and management. Chs. 812. Secure recourses with NTFS. Review Administer shared folders. Auditing resources and events. Configuring group policy and security policy. Managing data storage. Backup and restoring ...
... DNS services. Active Directory Service. User account and groups, and network printer setup and management. Chs. 812. Secure recourses with NTFS. Review Administer shared folders. Auditing resources and events. Configuring group policy and security policy. Managing data storage. Backup and restoring ...
Network-Coding Multicast Networks With QoS Guarantees
... the most significant benefit of network coding is that it allows us to treat a multicast connection with q destinations as q unicast connections in formulating the flow optimization problem. • we are able to prove two important results in this paper. Both results apply to explicit-routing and shorte ...
... the most significant benefit of network coding is that it allows us to treat a multicast connection with q destinations as q unicast connections in formulating the flow optimization problem. • we are able to prove two important results in this paper. Both results apply to explicit-routing and shorte ...
lecture 17
... system that runs a network, steering information between computers and managing security and users Packet-switching - Occurs when the sending computer divides a message into a number of efficiently sized units called packets, each of which contains the address of the destination computer Router - An ...
... system that runs a network, steering information between computers and managing security and users Packet-switching - Occurs when the sending computer divides a message into a number of efficiently sized units called packets, each of which contains the address of the destination computer Router - An ...
Chapter 1 solutions - CMPE150, Winter 17, Section 01
... E2. Circuit switching versus packet switching i. In a circuit switching network, when Alice wants to communicate with Bob, a physical "circuit" is established between Alice and Bob before any data can be sent. a. Why do you think this is necessary? This is necessary because in a circuit switching ne ...
... E2. Circuit switching versus packet switching i. In a circuit switching network, when Alice wants to communicate with Bob, a physical "circuit" is established between Alice and Bob before any data can be sent. a. Why do you think this is necessary? This is necessary because in a circuit switching ne ...
Assignment 3 - Network Components
... What is a Network Gateway? A network gateway is an internetworking system capable of joining together two networks that use different base protocols. A network gateway can be implemented completely in software, completely in hardware, or as a combination of both. Depending on the types of protocols ...
... What is a Network Gateway? A network gateway is an internetworking system capable of joining together two networks that use different base protocols. A network gateway can be implemented completely in software, completely in hardware, or as a combination of both. Depending on the types of protocols ...
1 - Portal UniMAP
... The advantages of distributed processing are security, access to distributed databases, collaborative processing, and faster problem solving. 2. What are the advantages of a multipoint connection over a point-to-point connection ? Advantages of a multipoint over a point-to-point configuration (type ...
... The advantages of distributed processing are security, access to distributed databases, collaborative processing, and faster problem solving. 2. What are the advantages of a multipoint connection over a point-to-point connection ? Advantages of a multipoint over a point-to-point configuration (type ...
LANs and WLANs
... Wi-Fi Setup • Enter an SSID for the network • Activate WEP, WPA, or WPA2 and create ...
... Wi-Fi Setup • Enter an SSID for the network • Activate WEP, WPA, or WPA2 and create ...
Networking - Institute of Mathematics and Informatics
... Host-to-host, or transport Application ...
... Host-to-host, or transport Application ...
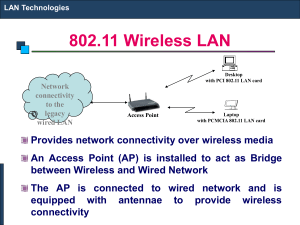
802.11 Wireless LAN
... A repeater receives a signal, regenerates it, and passes it on. It can regenerate and retime network signals at the bit level to allow them to travel a longer distance on the media. It operates at Physical Layer of OSI The Four Repeater Rule for 10-Mbps Ethernet should be used as a standard when ext ...
... A repeater receives a signal, regenerates it, and passes it on. It can regenerate and retime network signals at the bit level to allow them to travel a longer distance on the media. It operates at Physical Layer of OSI The Four Repeater Rule for 10-Mbps Ethernet should be used as a standard when ext ...
ITGS
... •File transfer (FTP) •These protocols use a standard port , and the ports can be blocked as well •For example, HTTP is port 80 •Application program - individual programs can be granted or denied network access •This is most important for programs that try automatically to update themselves or update ...
... •File transfer (FTP) •These protocols use a standard port , and the ports can be blocked as well •For example, HTTP is port 80 •Application program - individual programs can be granted or denied network access •This is most important for programs that try automatically to update themselves or update ...
What is a Network
... communications for an extranet community of buyers and suppliers, but VPNs are also used to secure many other types of communication – those internal to a company and links between different companies or agencies for information sharing, for example. The most common definition of an extranet is a ty ...
... communications for an extranet community of buyers and suppliers, but VPNs are also used to secure many other types of communication – those internal to a company and links between different companies or agencies for information sharing, for example. The most common definition of an extranet is a ty ...
Dark Matter and Dark Energy - Hitoshi Murayama Home Page
... • Fiber-optic backbone, machines attached through switches • Switches are smarter network device • Party where everybody talks over cell phone with head set • No “packet collisions,” a “sniffer” cannot steal passwords • Users allowed to install hubs, switches, routers for in-room network ...
... • Fiber-optic backbone, machines attached through switches • Switches are smarter network device • Party where everybody talks over cell phone with head set • No “packet collisions,” a “sniffer” cannot steal passwords • Users allowed to install hubs, switches, routers for in-room network ...
Chapter 8 Slides
... • Allows for subdivision of internets within an organization • Each LAN can have a subnet number, allowing routing among networks • Host portion is partitioned into subnet and host numbers ...
... • Allows for subdivision of internets within an organization • Each LAN can have a subnet number, allowing routing among networks • Host portion is partitioned into subnet and host numbers ...
PPP - Ivailo Chakarov
... service In the event of more higher speed being needed an additional server can be added to the SAN ...
... service In the event of more higher speed being needed an additional server can be added to the SAN ...
Security+ Guide to Network Security Fundamentals
... Broadcast domain within a switched network Uses encryption and other security mechanisms to ensure that ...
... Broadcast domain within a switched network Uses encryption and other security mechanisms to ensure that ...
NETWORKING LAB -
... The fundamental difference between a router and a Layer 3 switch is that Layer 3 switches have optimized hardware to pass data as fast as Layer 2 switches, yet they make decisions on how to transmit traffic at Layer 3, just like a router. Within the LAN environment, a Layer 3 switch is usually faste ...
... The fundamental difference between a router and a Layer 3 switch is that Layer 3 switches have optimized hardware to pass data as fast as Layer 2 switches, yet they make decisions on how to transmit traffic at Layer 3, just like a router. Within the LAN environment, a Layer 3 switch is usually faste ...
The final will be 1-2:50 PM on Wednesday, December 13... closed-book and closed-note, except for three sheets of paper with...
... Mulitprocessor basic organizations: Communication models (message passing vs. shared memory(UMA, NUMA) and physical connection (network vs. bus) Bus Connected Multiprocessors Single bus multiprocessor issues: cache coherency, process synchronization, spin locks Network Connected Multiprocessors Netw ...
... Mulitprocessor basic organizations: Communication models (message passing vs. shared memory(UMA, NUMA) and physical connection (network vs. bus) Bus Connected Multiprocessors Single bus multiprocessor issues: cache coherency, process synchronization, spin locks Network Connected Multiprocessors Netw ...
CIS6930: Advanced Topics in Networking
... – Select a node as the root – Build a spanning tree from the root – Nodes are partitioned into layers based on the position in the spanning tree – The channel from a lower layer node to a higher layer node is the up link, the channel from a higher layer node to a lower layer node is a down link, cha ...
... – Select a node as the root – Build a spanning tree from the root – Nodes are partitioned into layers based on the position in the spanning tree – The channel from a lower layer node to a higher layer node is the up link, the channel from a higher layer node to a lower layer node is a down link, cha ...
Wireless Security - Indiana University of Pennsylvania
... You want to pick the strongest form you can find All devices on your network must share the same ...
... You want to pick the strongest form you can find All devices on your network must share the same ...
Why Internetworking? - California State University, Long Beach
... Solution: Build an Internetwork • Begin with heterogeneous network technologies • Connect the physical networks • Create software to make the resulting system appear homogeneous The result is called an internetwork or internet. ...
... Solution: Build an Internetwork • Begin with heterogeneous network technologies • Connect the physical networks • Create software to make the resulting system appear homogeneous The result is called an internetwork or internet. ...