The Application Layers :On Demand Lecture (Part I)
... just forward the packet along the LSP simplify the forwarding function greatly increase performance and scalability dramatically ...
... just forward the packet along the LSP simplify the forwarding function greatly increase performance and scalability dramatically ...
optical networks
... Optical Networking An optical network is composed of the fiber-optic cables that carry channels of light. The cables are combined with the optical components deployed along the fiber to process the light. The capabilities of an optical network are necessarily tied to the physics of light, and ...
... Optical Networking An optical network is composed of the fiber-optic cables that carry channels of light. The cables are combined with the optical components deployed along the fiber to process the light. The capabilities of an optical network are necessarily tied to the physics of light, and ...
Using port pairing to simplify transparent mode
... Using port pairing to simplify transparent mode When you create a port pair, all traffic accepted by one of the paired ports can only exit out the other port. Restricting traffic in this way simplifies your FortiGate configuration because security policies between these interfaces are preconfigured. ...
... Using port pairing to simplify transparent mode When you create a port pair, all traffic accepted by one of the paired ports can only exit out the other port. Restricting traffic in this way simplifies your FortiGate configuration because security policies between these interfaces are preconfigured. ...
Chapter 1 - Rahul`s
... Less Expensive, each device needs only one port and one link. Easy to install and reconfigure. Less cabling & additions, moves and deletions involve only one connection Is robust: If one link fails only that is affected, others remain active. As long as hub is working, it can be used to monitor link ...
... Less Expensive, each device needs only one port and one link. Easy to install and reconfigure. Less cabling & additions, moves and deletions involve only one connection Is robust: If one link fails only that is affected, others remain active. As long as hub is working, it can be used to monitor link ...
Tuesday, February 7, 2007 (Intro to the Network
... Multiple LANS may be connected to form one logical LAN ...
... Multiple LANS may be connected to form one logical LAN ...
Part I: Introduction
... Access networks and physical media Q: How to connect end systems to edge router? o residential access nets o institutional access networks ...
... Access networks and physical media Q: How to connect end systems to edge router? o residential access nets o institutional access networks ...
network1 - Warilla High School Intranet
... PCs. Each PC operates separately of the others, yet any PC can share files, printers and other resources with any other PC on the network. Referred to as Distributed Processing • An emerging technology is the attempt to combine the best of distributed computing and centralised computing (a hybrid of ...
... PCs. Each PC operates separately of the others, yet any PC can share files, printers and other resources with any other PC on the network. Referred to as Distributed Processing • An emerging technology is the attempt to combine the best of distributed computing and centralised computing (a hybrid of ...
papers/Win2K_1Gbps
... program, modified to work with Windows2000 multi-threading and asynchronous I/O facilities. The sending program has 12threads each of which drives one of 12 streams. The receiving program consumes the 12 streams with 12 threads, and continuously reports the observed data arrival rate. Threads in bot ...
... program, modified to work with Windows2000 multi-threading and asynchronous I/O facilities. The sending program has 12threads each of which drives one of 12 streams. The receiving program consumes the 12 streams with 12 threads, and continuously reports the observed data arrival rate. Threads in bot ...
OPEN INTERNET DISCLOSURE STATEMENT
... not target specific usages or applications (such as peer-to-peer) and instead focus in a contentneutral manner on bandwidth usage in real time, with the goal of providing reasonable and equitable access to the network for all similarly situated customers. In other words, to the extent that the use o ...
... not target specific usages or applications (such as peer-to-peer) and instead focus in a contentneutral manner on bandwidth usage in real time, with the goal of providing reasonable and equitable access to the network for all similarly situated customers. In other words, to the extent that the use o ...
NANOG - Washington, DC, USA
... GigaPort projects and organisation GigaPort-Management and Steering Committee ...
... GigaPort projects and organisation GigaPort-Management and Steering Committee ...
01_tcom5272_intro
... Description: The Microsoft Windows redirector is one example of the Application layer (Layer 7) at work. In this activity, you view computers, shared folders, and shared printers through a Microsoft-based network, which are made accessible, in part, through the redirector. Your network needs to ha ...
... Description: The Microsoft Windows redirector is one example of the Application layer (Layer 7) at work. In this activity, you view computers, shared folders, and shared printers through a Microsoft-based network, which are made accessible, in part, through the redirector. Your network needs to ha ...
NET for stjosephs
... The twisted form is used to reduce electrical interference to similar pairs close by The most common application of the twisted pair is the telephone system Twisted pairs can be used for either analog or digital transmission The technology and standards are mature and stable for voice commun ...
... The twisted form is used to reduce electrical interference to similar pairs close by The most common application of the twisted pair is the telephone system Twisted pairs can be used for either analog or digital transmission The technology and standards are mature and stable for voice commun ...
William Stallings Data and Computer Communications
... Research Project Agency (DARPA) for its packet switched network (ARPANET) • Used by the global Internet • No official model but a working one. ...
... Research Project Agency (DARPA) for its packet switched network (ARPANET) • Used by the global Internet • No official model but a working one. ...
Relationship between bandwidth and the transmission capacity of a
... • The VAN is set up by a firm that is in charge of managing the network. • The subscribers pay only for the amount of data they transmit plus a subscription fee. • Customers do not have to invest in network equipment and software or perform their own error checking, editing, routing, and protocol co ...
... • The VAN is set up by a firm that is in charge of managing the network. • The subscribers pay only for the amount of data they transmit plus a subscription fee. • Customers do not have to invest in network equipment and software or perform their own error checking, editing, routing, and protocol co ...
Data Transmission
... they are both ready to communicate 1st Device sends a handshake signal which is acknowledged by the other device This states that each is now ready for communication ...
... they are both ready to communicate 1st Device sends a handshake signal which is acknowledged by the other device This states that each is now ready for communication ...
Chapter 1
... The Routing and Remote Access service provides the ability to use a Windows Server 2008 computer as a router, which passes network traffic from one TCP/IP network to another, as well as remote access capabilities using either dial-up or VPN technology ...
... The Routing and Remote Access service provides the ability to use a Windows Server 2008 computer as a router, which passes network traffic from one TCP/IP network to another, as well as remote access capabilities using either dial-up or VPN technology ...
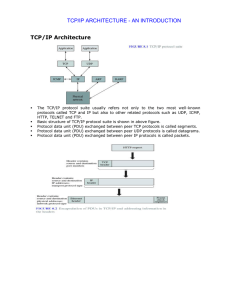
TCP/IP Architecture TCP/IP ARCHITECTURE
... Version: This field identifies the current IP version and it is 4. Internet header length (IHL): It specifies the length of the header in 32-bit words. If no options are used, IHL will have value of 5. Type of service (TOS): This field specifies the priority of packet based on delay, throughput, rel ...
... Version: This field identifies the current IP version and it is 4. Internet header length (IHL): It specifies the length of the header in 32-bit words. If no options are used, IHL will have value of 5. Type of service (TOS): This field specifies the priority of packet based on delay, throughput, rel ...
Network Security Topologies
... NAT is like the receptionist in a large office Let’s say you left instructions with the receptionist not to forward any calls to you unless you request it. Later on, you call a potential client and leave a message for that client to call you back. You tell the receptionist that you are expecting a ...
... NAT is like the receptionist in a large office Let’s say you left instructions with the receptionist not to forward any calls to you unless you request it. Later on, you call a potential client and leave a message for that client to call you back. You tell the receptionist that you are expecting a ...
chap01 - Ohio County Schools
... network and addressed networking specifications as they apply to connectivity, networking media, encryption, emerging technologies, and error-checking algorithms ISO created specifications that enabled computer platforms across the world to communicate openly, which resulted in the OSI model 802 sta ...
... network and addressed networking specifications as they apply to connectivity, networking media, encryption, emerging technologies, and error-checking algorithms ISO created specifications that enabled computer platforms across the world to communicate openly, which resulted in the OSI model 802 sta ...
Constraint-based routing
... L2VPNs - Allows networks based on link-layer technology to be interconnected via an MPLS backbone (huge parts of the provider networks are based on legacy technology like ATM, Frame Relay or Ethernet). The difference between L3 and L2 VPNs can be found in the relation between Provider Edge (PE) and ...
... L2VPNs - Allows networks based on link-layer technology to be interconnected via an MPLS backbone (huge parts of the provider networks are based on legacy technology like ATM, Frame Relay or Ethernet). The difference between L3 and L2 VPNs can be found in the relation between Provider Edge (PE) and ...
The Internet
... or over a wireless link 10s of routers on a department backbone 10s of department backbones connected to campus backbone 10s of campus backbones connected to regional service providers 100s of regional service providers connected by national backbone 10s of national backbones connected by internat ...
... or over a wireless link 10s of routers on a department backbone 10s of department backbones connected to campus backbone 10s of campus backbones connected to regional service providers 100s of regional service providers connected by national backbone 10s of national backbones connected by internat ...
Computer Networks
... In token Ring , hub is called Multistation Access Unit(MAU). 38. What is the difference between routable and non- routable protocols? Routable protocols can work with a router and can be used to build large networks. Non-Routable protocols are designed to work on small, local networks and cannot be ...
... In token Ring , hub is called Multistation Access Unit(MAU). 38. What is the difference between routable and non- routable protocols? Routable protocols can work with a router and can be used to build large networks. Non-Routable protocols are designed to work on small, local networks and cannot be ...
WEB LAWS
... The most popular formulation is of the doubling of the number of transistors on integrated circuits every 18 months However, it is also common to cite Moore's Law to refer to the rapidly continuing advance in computing power per unit cost, because increase in transistor count is also a rough measure ...
... The most popular formulation is of the doubling of the number of transistors on integrated circuits every 18 months However, it is also common to cite Moore's Law to refer to the rapidly continuing advance in computing power per unit cost, because increase in transistor count is also a rough measure ...