Hands-On Ethical Hacking and Network Security
... He lost his job, was sued, conference materials were confiscated, etc. – See links Ch 13 d, e, f, g ...
... He lost his job, was sued, conference materials were confiscated, etc. – See links Ch 13 d, e, f, g ...
Development of a Numerical Statistical Model for WCDMA Downlink
... as the main limiting factor for the performance of WCDMA networks. Interference statistics determine power consumption per user and thus sets network performance limits in terms of network capacity and coverage. The paper aims to develop a numerical statistical model that is going to perform power c ...
... as the main limiting factor for the performance of WCDMA networks. Interference statistics determine power consumption per user and thus sets network performance limits in terms of network capacity and coverage. The paper aims to develop a numerical statistical model that is going to perform power c ...
Basic Concepts
... Pricing is typically not distance sensitive Mostly it is based on requested data rate parameters ...
... Pricing is typically not distance sensitive Mostly it is based on requested data rate parameters ...
Telecommunication Transmission and Switching System
... •The source may be a simple telephone microphone, keyboard •The destination may be a simple telephone speaker, monitor ...
... •The source may be a simple telephone microphone, keyboard •The destination may be a simple telephone speaker, monitor ...
Slide 1 - Your Flash File
... – Ring network • One disadvantage of a ring network is that if a network device fails (such as a PC or a server), the devices downstream from the failed device cannot communicate with the network • Multistation Access Unit (MAU) – Manages data flow between connected devicesw ...
... – Ring network • One disadvantage of a ring network is that if a network device fails (such as a PC or a server), the devices downstream from the failed device cannot communicate with the network • Multistation Access Unit (MAU) – Manages data flow between connected devicesw ...
Acceptable Use of Electronic Networks - Tri-City
... promoting educational excellence by facilitating resource sharing, innovation, and communication. The Network is defined as all district owned hardware and software. These procedures do not attempt to state all required or proscribed behavior by users. However, some specific examples are provided. T ...
... promoting educational excellence by facilitating resource sharing, innovation, and communication. The Network is defined as all district owned hardware and software. These procedures do not attempt to state all required or proscribed behavior by users. However, some specific examples are provided. T ...
What are SNMP Messages
... 14. List three factors that can influence the choice of whether to implement a peer-to-peer or server-based network configuration. Three factors that can influence the choice of whether to implement a peer-to-peer or server-based network configuration are 1. the size of the organization, 2. the lev ...
... 14. List three factors that can influence the choice of whether to implement a peer-to-peer or server-based network configuration. Three factors that can influence the choice of whether to implement a peer-to-peer or server-based network configuration are 1. the size of the organization, 2. the lev ...
Full article
... The introduction of IP into public and enterprise networks points the way to holistic information processing. Differences between voice and data will disappear as the two types of information converge in new applications. This will produce synergy in terms of network operations, because the manageme ...
... The introduction of IP into public and enterprise networks points the way to holistic information processing. Differences between voice and data will disappear as the two types of information converge in new applications. This will produce synergy in terms of network operations, because the manageme ...
Global Network Function Virtualization Market
... optimizing the network operations and benefitting the service providers across the globe. Network function virtualization involves implementation of network functions in software suitable for different hardware and that can be moved to various locations without any need of installation of new equipm ...
... optimizing the network operations and benefitting the service providers across the globe. Network function virtualization involves implementation of network functions in software suitable for different hardware and that can be moved to various locations without any need of installation of new equipm ...
TMBroadcast Onda Cero English
... We use the satellite as the primary channel for sending audio (main program) and disconnection data. When necessary, a command is sent to change to main, regional, provincial or local program. Thanks to the data network, disconnection commands can be sent from any delegation as all the broadcast equ ...
... We use the satellite as the primary channel for sending audio (main program) and disconnection data. When necessary, a command is sent to change to main, regional, provincial or local program. Thanks to the data network, disconnection commands can be sent from any delegation as all the broadcast equ ...
CCDE "At a Glance" PDF
... a CCDE-certified professional must know how to make the design tradeoffs that realize the value of advanced technologies such as unified communications while maintaining high levels of network security and performance. With a solutions approach, the network designer can also successfully integrate a ...
... a CCDE-certified professional must know how to make the design tradeoffs that realize the value of advanced technologies such as unified communications while maintaining high levels of network security and performance. With a solutions approach, the network designer can also successfully integrate a ...
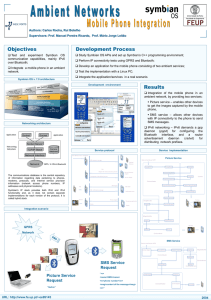
Slide 1
... ambient network, by providing two services: Picture service – enables other devices to get the images captured by the mobile phone, SMS service – allows other devices with IP connectivity to the phone to send SMS messages. ...
... ambient network, by providing two services: Picture service – enables other devices to get the images captured by the mobile phone, SMS service – allows other devices with IP connectivity to the phone to send SMS messages. ...
Network Concepts
... Now, due to faster technology LAN devices can be used over longer distances. ...
... Now, due to faster technology LAN devices can be used over longer distances. ...
Experience Summary
... J I T H E S H YAT H I N D R A N E-Mail: [email protected] OBJECTIVE Seeking a profession with a well-known organization for a dynamic learning experience and to contribute substantially to the development of the organization. EXPERIENCE SUMMARY ...
... J I T H E S H YAT H I N D R A N E-Mail: [email protected] OBJECTIVE Seeking a profession with a well-known organization for a dynamic learning experience and to contribute substantially to the development of the organization. EXPERIENCE SUMMARY ...
ECE 117-2426
... residential and commercial buildings. In this project, we design two electronic Nodes including Sensor Node, and Coordinator Node. In the application layer, user friendly software is designed to control and monitor all nodes in the wireless network through LAN with using C++ programming language. Ea ...
... residential and commercial buildings. In this project, we design two electronic Nodes including Sensor Node, and Coordinator Node. In the application layer, user friendly software is designed to control and monitor all nodes in the wireless network through LAN with using C++ programming language. Ea ...
Securing the Network - Austin Community College
... These attacks are mounted against a network backbone, exploit information in transit, electronically penetrate an enclave, or attack an authorized remote user during an attempt to connect to an enclave. Active attacks result in the disclosure or dissemination of data files, DoS, or modification of d ...
... These attacks are mounted against a network backbone, exploit information in transit, electronically penetrate an enclave, or attack an authorized remote user during an attempt to connect to an enclave. Active attacks result in the disclosure or dissemination of data files, DoS, or modification of d ...
OSI Model Pyramid - Redbird Internet Services
... Layer 2 Datalink Flow of data over single link btwn devices; controls communication channel access; organizes data in logical frames; ID’s specific computers on the network; error detection added at this layer; MAC addresses are resolved at this layer; sends data from network to physical layer; mana ...
... Layer 2 Datalink Flow of data over single link btwn devices; controls communication channel access; organizes data in logical frames; ID’s specific computers on the network; error detection added at this layer; MAC addresses are resolved at this layer; sends data from network to physical layer; mana ...
Powerpoint
... messages would be direct and straightforward. (e.g., the “hotline” between the White House and Kremlin) •Unfortunately, with hundreds, thousands or millions of computers on a network, they cannot all have direct links to each other. ...
... messages would be direct and straightforward. (e.g., the “hotline” between the White House and Kremlin) •Unfortunately, with hundreds, thousands or millions of computers on a network, they cannot all have direct links to each other. ...
Emergence of Homophily
... • Files can be imported directly from the internet as well. • Similarly, networks can be exported to other formats with ...
... • Files can be imported directly from the internet as well. • Similarly, networks can be exported to other formats with ...
Save the World!
... clients, cell phones, etc. • Can be VERY low bandwidth • Multiple radio systems can carry the information from a big transmitter to a large region. ...
... clients, cell phones, etc. • Can be VERY low bandwidth • Multiple radio systems can carry the information from a big transmitter to a large region. ...