CPSC 463 Networks and Distributed Processing
... provides for returning the session entries back to the last known correct state. • Example: Session established and large file transmitted; receiving end has no storage and directly prints the incoming data. The printer dies and data is lost. • Session users could split the text into pages and inser ...
... provides for returning the session entries back to the last known correct state. • Example: Session established and large file transmitted; receiving end has no storage and directly prints the incoming data. The printer dies and data is lost. • Session users could split the text into pages and inser ...
EC310: Applications of Cyber Engineering Alpha: ____________________ Exam #2
... a. An IP address is a software address. ...
... a. An IP address is a software address. ...
Module 2 - Santa Fe College
... When you configure an access point, some configuration utilities use the term mixed mode to designate a network with both 802.11n and non-802.11n clients. In this configuration, one radio transmitter is used for legacy clients, and the remaining radio transmitters are used for 802.11n clients. Many ...
... When you configure an access point, some configuration utilities use the term mixed mode to designate a network with both 802.11n and non-802.11n clients. In this configuration, one radio transmitter is used for legacy clients, and the remaining radio transmitters are used for 802.11n clients. Many ...
Slide 1 - Department of Electrical Engineering & Computer Science
... The network uses its own address to transfer packets or frames to the appropriate destination IP address needs to be resolved to physical address at each IP network interface Example: Ethernet uses 48-bit addresses ...
... The network uses its own address to transfer packets or frames to the appropriate destination IP address needs to be resolved to physical address at each IP network interface Example: Ethernet uses 48-bit addresses ...
Automating Network Monitoring on Experimental Network Testbeds Michael Golightly, Jack Brassil
... can be used for a broad class of monitoring tools • Give user f lex ible con t r ol − monitoring resource consumption (cost) − Coverage − Data collection granularity − Impact on running experiment ...
... can be used for a broad class of monitoring tools • Give user f lex ible con t r ol − monitoring resource consumption (cost) − Coverage − Data collection granularity − Impact on running experiment ...
Cybrotech software tools
... in a running network, not affecting other modules. CyBro may also be connected and running. IEX Loader opens hex files only, binary files are not supported. Sending new program (or new NAD) will also set serial number, if the present value is not valid (zero for new devices, FFxxxxxx for older devic ...
... in a running network, not affecting other modules. CyBro may also be connected and running. IEX Loader opens hex files only, binary files are not supported. Sending new program (or new NAD) will also set serial number, if the present value is not valid (zero for new devices, FFxxxxxx for older devic ...
DBA 102:NOW WHAT
... Fibre channel dedicated hardware iSCSI over LAN Behaves more like on-board attached storage ...
... Fibre channel dedicated hardware iSCSI over LAN Behaves more like on-board attached storage ...
N44096972
... A NIDS will typically only pick up packets to which it is attached, traveling in the network segment. NIDS are generally placed in between an internal network and the firewall, to ensure that all inbound and outbound traffic is monitored. In addition, if the network-based IDS software is installed o ...
... A NIDS will typically only pick up packets to which it is attached, traveling in the network segment. NIDS are generally placed in between an internal network and the firewall, to ensure that all inbound and outbound traffic is monitored. In addition, if the network-based IDS software is installed o ...
Click here to free sample.
... 4. Traffic that can adjust to changes in delay and throughput across an internet and still meet the needs of its applications is ________ traffic. 5. Databases, information kiosks, hypertexts, electronic books, and multimedia expert systems are examples of multimedia ________ systems. 6. ________ pr ...
... 4. Traffic that can adjust to changes in delay and throughput across an internet and still meet the needs of its applications is ________ traffic. 5. Databases, information kiosks, hypertexts, electronic books, and multimedia expert systems are examples of multimedia ________ systems. 6. ________ pr ...
Optimizing Your Network Design
... – Allows a router to act as a surrogate for the service that is not available locally – Support a router performing tasks beyond its typical duties to minimize delay and bandwidth usage – Can convert a frame type to a new type that causes less traffic – Improve performance for applications that are ...
... – Allows a router to act as a surrogate for the service that is not available locally – Support a router performing tasks beyond its typical duties to minimize delay and bandwidth usage – Can convert a frame type to a new type that causes less traffic – Improve performance for applications that are ...
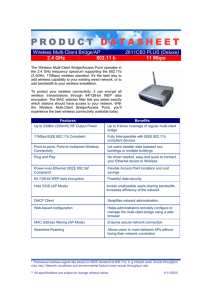
Wireless Multi-Client Bridge/AP 2611CB3 PLUS (Deluxe) 2.4 GHz
... To protect your wireless connectivity, it can encrypt all wireless transmissions through 64/128-bit WEP data encryption. The MAC address filter lets you select exactly which stations should have access to your network. With the Wireless Multi-Client Bridge/Access Point, you'll experience the best wi ...
... To protect your wireless connectivity, it can encrypt all wireless transmissions through 64/128-bit WEP data encryption. The MAC address filter lets you select exactly which stations should have access to your network. With the Wireless Multi-Client Bridge/Access Point, you'll experience the best wi ...
LAN BASICS
... • SCSI offers faster transfer rates than ATA/IDE, the interface most commonly used in desktop PCs. • In general, ATA/IDE is considered easier to implement and less expensive than SCSI but does not offer as many features. – For example, SCSI can support up to 16 devices on a single bus (IDE offers tw ...
... • SCSI offers faster transfer rates than ATA/IDE, the interface most commonly used in desktop PCs. • In general, ATA/IDE is considered easier to implement and less expensive than SCSI but does not offer as many features. – For example, SCSI can support up to 16 devices on a single bus (IDE offers tw ...
Networking Fundadmentals • What is Computer Network? A
... control of operation without endangering air travelers. ...
... control of operation without endangering air travelers. ...
SNMP Monitoring: One Critical Component to Network Management
... Make no mistake-SNMP monitoring should be a part of any network management solution. But effective administration of enterprise networks requires more than SNMP management. Only a comprehensive network analyzer can deliver both in-depth analysis along with the ability to manage and view statistics f ...
... Make no mistake-SNMP monitoring should be a part of any network management solution. But effective administration of enterprise networks requires more than SNMP management. Only a comprehensive network analyzer can deliver both in-depth analysis along with the ability to manage and view statistics f ...
Services and System Aspects (SA) LTE Africa 11.11.2014
... • Broadcast communications in physical layer (i.e. no feedback loop) and is connectionless • Works in complete absence of infrastructure as well. • The direct user plane communication service for transmission of IP packets is provided by the radio layer • Group security keys are derived from a share ...
... • Broadcast communications in physical layer (i.e. no feedback loop) and is connectionless • Works in complete absence of infrastructure as well. • The direct user plane communication service for transmission of IP packets is provided by the radio layer • Group security keys are derived from a share ...
Presentation
... Can we create a generic network data set that would be applicable across applications? We could create a generic motif (subnet) component for each network type and property set based on the framework categorization Then we can build larger networks from these motifs depending on the applicatio ...
... Can we create a generic network data set that would be applicable across applications? We could create a generic motif (subnet) component for each network type and property set based on the framework categorization Then we can build larger networks from these motifs depending on the applicatio ...
John V overview of architecure elements
... connections between ports on the network 2.A link is a resource which allocates resource to connections between ports on different networks ION and SDN are examples of a transport resource called a network. A Cross connect between ION and SDN in Chicago or NY is an example of a link. A more interest ...
... connections between ports on the network 2.A link is a resource which allocates resource to connections between ports on different networks ION and SDN are examples of a transport resource called a network. A Cross connect between ION and SDN in Chicago or NY is an example of a link. A more interest ...
Plugging the Leaks Without Unplugging Your Network in the Midst of
... of unauthorized equipment), or both. This scenario can easily lead to the intrusion of persons that are not trusted, at a time when authorized persons have evacuated the area. Furthermore, there may be either malicious or opportunistic cyberlooters who are trying to steal confidential material. Even ...
... of unauthorized equipment), or both. This scenario can easily lead to the intrusion of persons that are not trusted, at a time when authorized persons have evacuated the area. Furthermore, there may be either malicious or opportunistic cyberlooters who are trying to steal confidential material. Even ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... HDTRA 1-07-1-0004 and HDTRA-09-1-005. Generally the network reliability is considered. The setting of logical link failure can be co related even if physical link fail independently. So avoid this, light path algorithm was suggested in this paper. The purpose is approximately the failure polynomial ...
... HDTRA 1-07-1-0004 and HDTRA-09-1-005. Generally the network reliability is considered. The setting of logical link failure can be co related even if physical link fail independently. So avoid this, light path algorithm was suggested in this paper. The purpose is approximately the failure polynomial ...
SIFS
... doesn’t protect from traffic analysis. RC4 – symmetric stream cipher algorithm with variable key length is used (same key and algorithm for encryption and decryption) ...
... doesn’t protect from traffic analysis. RC4 – symmetric stream cipher algorithm with variable key length is used (same key and algorithm for encryption and decryption) ...
End of module
... • SCSI offers faster transfer rates than ATA/IDE, the interface most commonly used in desktop PCs. • In general, ATA/IDE is considered easier to implement and less expensive than SCSI but does not offer as many features. – For example, SCSI can support up to 16 devices on a single bus (IDE offers tw ...
... • SCSI offers faster transfer rates than ATA/IDE, the interface most commonly used in desktop PCs. • In general, ATA/IDE is considered easier to implement and less expensive than SCSI but does not offer as many features. – For example, SCSI can support up to 16 devices on a single bus (IDE offers tw ...
NGN of CMCC - 一般社団法人情報通信技術委員会
... Softswitch long-distance tandem network of China Mobile • On November 27, 2004, China Mobile completed the cut-off of the Softswitch network, the ever largest one in the world; • The network is expected to carry 17951 provincial internetwork traffic across 31 provinces in China, with the total traf ...
... Softswitch long-distance tandem network of China Mobile • On November 27, 2004, China Mobile completed the cut-off of the Softswitch network, the ever largest one in the world; • The network is expected to carry 17951 provincial internetwork traffic across 31 provinces in China, with the total traf ...