網路與通信協定
... new message types, standardized multi-protocol support, enhanced security, new MIB objects, and a way to co-exist with SNMPv1. SNMPv2C is useful for the retrieval of large amounts of management information using fewer network resources. ...
... new message types, standardized multi-protocol support, enhanced security, new MIB objects, and a way to co-exist with SNMPv1. SNMPv2C is useful for the retrieval of large amounts of management information using fewer network resources. ...
IP Address - Department of Computing & Immersive Technologies
... Network Addressing: Analogy with telephone numbers ...
... Network Addressing: Analogy with telephone numbers ...
Backbone: the main connecting cable that runs from one end of the
... controlled by a particular entity. 5.A network of the public domain is called an open network; a network of the innovations owned and controlled by a particular entity such as an individual or a corporation is called a closed or sometimes a proprietary network. 6.Because a machine may be unable to d ...
... controlled by a particular entity. 5.A network of the public domain is called an open network; a network of the innovations owned and controlled by a particular entity such as an individual or a corporation is called a closed or sometimes a proprietary network. 6.Because a machine may be unable to d ...
10/100/1000 Mbps connectivity to workstations and servers and non
... FastIron II switches act as a backup to other routers in the network. In the event of a failure, a FastIron II switch automatically performs the tasks of the failed router. The resiliency features of FastIron II switches, combined with hot swappable modules and hot swappable redundant power, ensure ...
... FastIron II switches act as a backup to other routers in the network. In the event of a failure, a FastIron II switch automatically performs the tasks of the failed router. The resiliency features of FastIron II switches, combined with hot swappable modules and hot swappable redundant power, ensure ...
Computer Networks - Lynchburg College
... Gateways and Routers • A gateway is a host that belongs to more than one network • A gateway has more than one IP address, one for each network that includes it. • Gateways can also work as hosts, but more frequently gateways provide routing as their principal function. • The terms router and gatew ...
... Gateways and Routers • A gateway is a host that belongs to more than one network • A gateway has more than one IP address, one for each network that includes it. • Gateways can also work as hosts, but more frequently gateways provide routing as their principal function. • The terms router and gatew ...
Internet: A Fast Revision
... End-to-End Design: Based on the assumption that end-points can trust one another. To move the functionality away from the network, and, towards the edges of the system. Reduces the complexity of the network. Reduces the cost of future upgrades New applications can be added without modify ...
... End-to-End Design: Based on the assumption that end-points can trust one another. To move the functionality away from the network, and, towards the edges of the system. Reduces the complexity of the network. Reduces the cost of future upgrades New applications can be added without modify ...
Solution to test 2
... All nodes on subnet 1 will receive this ICMP request message and send reply messages to 158.132.2.100. Since the routers do not check the source addresses when forwarding, all the reply messages will be forwarded to subnet 2. If the number is large enough, the router that is responsible for forwardi ...
... All nodes on subnet 1 will receive this ICMP request message and send reply messages to 158.132.2.100. Since the routers do not check the source addresses when forwarding, all the reply messages will be forwarded to subnet 2. If the number is large enough, the router that is responsible for forwardi ...
Network - University of Surrey
... − A “thing” has the following properties: − It’s usually powered by battery. This implies limited source of energy. − It’s generally small in size and low in cost. This limits their computing capability. − It doesn’t usually perform complicated tasks. ...
... − A “thing” has the following properties: − It’s usually powered by battery. This implies limited source of energy. − It’s generally small in size and low in cost. This limits their computing capability. − It doesn’t usually perform complicated tasks. ...
CIS 1140 Network Fundamentals
... connection from the central router or switch to each network segment. Each hub is connected to the router or switch by more than one cable. The advantage of using a parallel backbone is that its redundant (duplicate) links ensure network connectivity to any area of the enterprise. Parallel backbones ...
... connection from the central router or switch to each network segment. Each hub is connected to the router or switch by more than one cable. The advantage of using a parallel backbone is that its redundant (duplicate) links ensure network connectivity to any area of the enterprise. Parallel backbones ...
Introduction to Data Communications
... Open Systems Interconnected Model – was created in the 70’s by the ISO (although the CCITT came up with their own model) • 10 different people got together and considered all functions of communications ...
... Open Systems Interconnected Model – was created in the 70’s by the ISO (although the CCITT came up with their own model) • 10 different people got together and considered all functions of communications ...
An Overview of MANET: History, Challenges and Applications
... We can characterized the life cycle of mobile ad hoc network into first, second and third generation. Present ad hoc network are considered the third generation [2][3]. The first generation of ad hoc network can be traced back to 1970’s. In 1970’s, these are called Packet Radio Network (PRNET) [4]. ...
... We can characterized the life cycle of mobile ad hoc network into first, second and third generation. Present ad hoc network are considered the third generation [2][3]. The first generation of ad hoc network can be traced back to 1970’s. In 1970’s, these are called Packet Radio Network (PRNET) [4]. ...
Routing
... 90% efficiency of bandwidth • Main advantage is that time is not wasted in transmitting whole packets when a collision ...
... 90% efficiency of bandwidth • Main advantage is that time is not wasted in transmitting whole packets when a collision ...
One-way Data Delivery Networks
... Cellular networks may use MMS, SMS, or other media delivery mechanism (typically these do not fall into the category of a one-way network, but SMS originators may be implemented in such a way as to not allow receivers to deliver messages back to the originator (e.g. in the case of network service an ...
... Cellular networks may use MMS, SMS, or other media delivery mechanism (typically these do not fall into the category of a one-way network, but SMS originators may be implemented in such a way as to not allow receivers to deliver messages back to the originator (e.g. in the case of network service an ...
ppt
... May only have coarse-grained information? Does port 22 always mean SSH? Who is the user accessing the SSH? ...
... May only have coarse-grained information? Does port 22 always mean SSH? Who is the user accessing the SSH? ...
VoIPpre
... NetMeeting, MSN, and HMP conferencing. 4. Use the Agilent SW Edition Advisor J1955A 5. Show the configurations used for the ...
... NetMeeting, MSN, and HMP conferencing. 4. Use the Agilent SW Edition Advisor J1955A 5. Show the configurations used for the ...
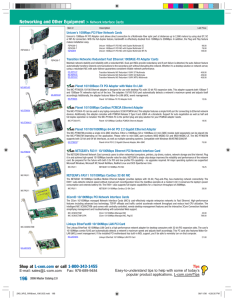
Networking and Other Equipment > Network Interface Cards - L-com
... automatically transfers network communications to the secondary port without disrupting the network. Whether it's a desktop solution or network server, using a redundant NIC with auto-failover guarantees consistent reliable network performance. NIC-NDFX-ST NIC-NDFX-ST NIC-NDFX-SC NIC-NDFX-SC NIC-NDF ...
... automatically transfers network communications to the secondary port without disrupting the network. Whether it's a desktop solution or network server, using a redundant NIC with auto-failover guarantees consistent reliable network performance. NIC-NDFX-ST NIC-NDFX-ST NIC-NDFX-SC NIC-NDFX-SC NIC-NDF ...
Darwin: Customizable Resource Management for Value
... Network access on every desktop and in every home Shockingly recent - 1989, caught on in ‘92 or so ...
... Network access on every desktop and in every home Shockingly recent - 1989, caught on in ‘92 or so ...
VoIPpresentation
... NetMeeting, MSN, and HMP conferencing. 4. Use the Agilent SW Edition Advisor J1955A 5. Show the configurations used for the ...
... NetMeeting, MSN, and HMP conferencing. 4. Use the Agilent SW Edition Advisor J1955A 5. Show the configurations used for the ...
What is Networking Hardware
... A router translates information from one network to another; it is similar to a superintelligent bridge. Routers select the best path to route a message, based on the destination address and origin. The router can direct traffic to prevent head-on collisions, and is smart enough to know when to dire ...
... A router translates information from one network to another; it is similar to a superintelligent bridge. Routers select the best path to route a message, based on the destination address and origin. The router can direct traffic to prevent head-on collisions, and is smart enough to know when to dire ...
Slide 1
... − Cells consist of several Subnets − Cell owner can define network policies • Security: define who can communicate with VMs • QoS: define bandwidth limits for VMs ...
... − Cells consist of several Subnets − Cell owner can define network policies • Security: define who can communicate with VMs • QoS: define bandwidth limits for VMs ...
MD-1377 Joint IP Modem Datasheet
... a DVB standards-based waveform with powerful encryption and government-specified transmission security (TRANSEC), JIPM is the Department of Defense (DoD) satellite modem standard for connecting all US forces. This system powers an IP networking backbone across the battlespace, enabling today's infor ...
... a DVB standards-based waveform with powerful encryption and government-specified transmission security (TRANSEC), JIPM is the Department of Defense (DoD) satellite modem standard for connecting all US forces. This system powers an IP networking backbone across the battlespace, enabling today's infor ...
Wireless Sensor Network Simulator
... researchers. This interest has largely been sparked by the dramatic drop in cost, size, and an increase in range and sensing capability of wireless sensor devices. These developments allow for a world where numerous, large, distributed networks of wireless sensors are a reality[3]. With this new rea ...
... researchers. This interest has largely been sparked by the dramatic drop in cost, size, and an increase in range and sensing capability of wireless sensor devices. These developments allow for a world where numerous, large, distributed networks of wireless sensors are a reality[3]. With this new rea ...
International Partners
... Support and participation from 5 national science funding agencies: the U.S. NSF, Panama ...
... Support and participation from 5 national science funding agencies: the U.S. NSF, Panama ...
Design Space for Interconnection Networks
... W = width, Tc = hop delay • Wormhole routing: • Twh = Tc • (D + L / W) • # of hops is an additive rather than multiplicative factor • Virtual Cut-Through routing: • Older and similar to wormhole. When blockage occurs, however, message is removed from network and buffered. • Deadlock are avoided thro ...
... W = width, Tc = hop delay • Wormhole routing: • Twh = Tc • (D + L / W) • # of hops is an additive rather than multiplicative factor • Virtual Cut-Through routing: • Older and similar to wormhole. When blockage occurs, however, message is removed from network and buffered. • Deadlock are avoided thro ...
ISCW642-825 - GogoTraining
... next-generation intelligent networks that deliver a wide variety of advanced, value-added services over a single infrastructure. MPLS can be integrated over existing infrastructures such as IP, Frame Relay, ATM, and Ethernet. As well, MPLS application components can be integrated with Layer 3 virtua ...
... next-generation intelligent networks that deliver a wide variety of advanced, value-added services over a single infrastructure. MPLS can be integrated over existing infrastructures such as IP, Frame Relay, ATM, and Ethernet. As well, MPLS application components can be integrated with Layer 3 virtua ...