Artificial Neural Networks
... – learning is accomplished by adjusting these strengths to cause network to output appropriate results – learn from experience (rather than being explicitly programmed with rules) – inspired by biological neural networks (ANN’s idea is not to replicate operation of bio systems, but use what’s known ...
... – learning is accomplished by adjusting these strengths to cause network to output appropriate results – learn from experience (rather than being explicitly programmed with rules) – inspired by biological neural networks (ANN’s idea is not to replicate operation of bio systems, but use what’s known ...
tutorial 1 - UniMAP Portal
... The mail delivery process can be automated by using optical recognition on the mail code. The letter can then be sorted and routed to the destination postal station, and even to the destination neighborhood, depending on the amount of geographical detail built into the mail code. 2b. Repeat part (a) ...
... The mail delivery process can be automated by using optical recognition on the mail code. The letter can then be sorted and routed to the destination postal station, and even to the destination neighborhood, depending on the amount of geographical detail built into the mail code. 2b. Repeat part (a) ...
Networking-1
... Scenario 1: If that IP address is local, the resolution of the IP address into MAC address takes place right away. Scenario 2: If that IP address is remote, the packet is routed to the remote network first. Then, once the packet gets to the remote network, it is resolved into a MAC address on that ...
... Scenario 1: If that IP address is local, the resolution of the IP address into MAC address takes place right away. Scenario 2: If that IP address is remote, the packet is routed to the remote network first. Then, once the packet gets to the remote network, it is resolved into a MAC address on that ...
ppt - Berkeley Database Research
... – Formally, each round, everyone who knows the data sends it to one of the n participants chosen at random – After O(log n) rounds, all n participants know the ...
... – Formally, each round, everyone who knows the data sends it to one of the n participants chosen at random – After O(log n) rounds, all n participants know the ...
Learning in Neural Networks and Defect Tolerant Classifiers
... - Nodes connect back to other nodes or themselves - Information flow is bidirectional • Fully recurrent network: there is a pair of directed connections between every pair of neurons in the network ...
... - Nodes connect back to other nodes or themselves - Information flow is bidirectional • Fully recurrent network: there is a pair of directed connections between every pair of neurons in the network ...
PPT - Pages
... Allows handing out arbitrary sized chunks of address space E.g., addresses 192.4.16 - 192.4.31 have the first 20 bits in common. Thus, we use these 20 bits as the network number ...
... Allows handing out arbitrary sized chunks of address space E.g., addresses 192.4.16 - 192.4.31 have the first 20 bits in common. Thus, we use these 20 bits as the network number ...
csp_07-08_net
... Layer 3 - network layer. Performs network routing, flow control, segmentation/desegmentation, and error control functions. The protocol that operates on this level is called Internet Protocol, or IP. – This is the layer at which router operates – makes Internet possible ...
... Layer 3 - network layer. Performs network routing, flow control, segmentation/desegmentation, and error control functions. The protocol that operates on this level is called Internet Protocol, or IP. – This is the layer at which router operates – makes Internet possible ...
comparisons of wired and wireless networks: a review
... Reliability, Mobility, Speed, Security etc. KEYWORDS: Cost, Reliability, Mobility, Speed, Security etc. ...
... Reliability, Mobility, Speed, Security etc. KEYWORDS: Cost, Reliability, Mobility, Speed, Security etc. ...
Introduction - McMaster University > ECE
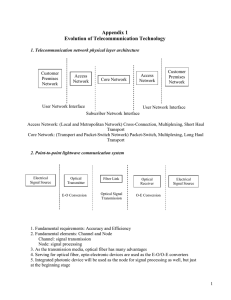
... part (channel) of the networks, but also be in the signal processing part (node). 3. Telecommunication technology evolution 1. Basic Technology and Services (Legacy Synchronous Communication Networks) Basic technology: Plain Old Telephony Service (POTS): Purely analog (acoustical) signal transmissio ...
... part (channel) of the networks, but also be in the signal processing part (node). 3. Telecommunication technology evolution 1. Basic Technology and Services (Legacy Synchronous Communication Networks) Basic technology: Plain Old Telephony Service (POTS): Purely analog (acoustical) signal transmissio ...
Spec Sheet - NetComm Wireless
... Create a WiFi network to share your connection with multiple WiFi devices at speeds of up to 300Mbps One USB 2.0 port that can support 3G/4G USB modems or external hard drives. Insert your compatible 3G/4G USB modem for an alternate Internet connection. Plug in your external hard drive and share ...
... Create a WiFi network to share your connection with multiple WiFi devices at speeds of up to 300Mbps One USB 2.0 port that can support 3G/4G USB modems or external hard drives. Insert your compatible 3G/4G USB modem for an alternate Internet connection. Plug in your external hard drive and share ...
Network Firewall Technologies By: David W Chadwick
... • Multiple hosts and gateways could be added to handle more traffic at a time • Two packet filtering routers are placed on each side of the DMZ • Very secure ...
... • Multiple hosts and gateways could be added to handle more traffic at a time • Two packet filtering routers are placed on each side of the DMZ • Very secure ...
THE BRITISH COMPUTER SOCIETY THE BCS PROFESSIONAL EXAMINATIONS
... c) Unlike the devices in section (a), a router is often described as a layer 3 device. Describe how a router meets the definition of a layer 3 device, contrasting it with the function of a switch. (7 marks) ANSWER POINTERS Nearly all candidates chose to answer the question, and in general the answer ...
... c) Unlike the devices in section (a), a router is often described as a layer 3 device. Describe how a router meets the definition of a layer 3 device, contrasting it with the function of a switch. (7 marks) ANSWER POINTERS Nearly all candidates chose to answer the question, and in general the answer ...
1)The concept of connected computers sharing resources is called
... 1) The concept of connected computers sharing resources is called……………. a) Internetworkin b) Intranetworking c)Networking d) None of the above 2) VPN stands for a) Virtual Private Networ b) Visual private network c) Virtual public network d) Visual public network 3) IMP stands for a) Internal messag ...
... 1) The concept of connected computers sharing resources is called……………. a) Internetworkin b) Intranetworking c)Networking d) None of the above 2) VPN stands for a) Virtual Private Networ b) Visual private network c) Virtual public network d) Visual public network 3) IMP stands for a) Internal messag ...
LEC5a_Network Visualization
... – When you open a large network, you will not get a view by default – To improve interactive performance, Cytoscape has the concept of “Levels of Detail” • Some visual attributes will only be apparent when you zoom in • The level of detail for various attributes can be changed in the preferences • T ...
... – When you open a large network, you will not get a view by default – To improve interactive performance, Cytoscape has the concept of “Levels of Detail” • Some visual attributes will only be apparent when you zoom in • The level of detail for various attributes can be changed in the preferences • T ...
Amit Shelawala
... Can’t really compete with pricing Want to provide services that are better than competition ...
... Can’t really compete with pricing Want to provide services that are better than competition ...
Chapter 2 Protocols and Architecture
... Research Project Agency (DARPA) for its packet switched network (ARPANET) • Used by the global Internet • No official model but a working one. —Application layer —Host to host or transport layer —Internet layer —Network access layer —Physical layer ...
... Research Project Agency (DARPA) for its packet switched network (ARPANET) • Used by the global Internet • No official model but a working one. —Application layer —Host to host or transport layer —Internet layer —Network access layer —Physical layer ...
Basic Networking
... Client/Server Networks • Server: central computer used to facilitate communication and resource sharing between other computers on the network (called clients) • Client/server network: uses a server to enable clients to share data, data storage space, and devices • To function as a server, a comput ...
... Client/Server Networks • Server: central computer used to facilitate communication and resource sharing between other computers on the network (called clients) • Client/server network: uses a server to enable clients to share data, data storage space, and devices • To function as a server, a comput ...
1. Server and mainframes are types of computers used for
... 22. To ensure that data is accessible on demand, an organisation must manage and protect its data. Thus, it is vital that the data has integrity and is kept secure. What is data integrity and why is it important? (2 marks) Data integrity identifies the quality of the data Garbage in, garbage out ...
... 22. To ensure that data is accessible on demand, an organisation must manage and protect its data. Thus, it is vital that the data has integrity and is kept secure. What is data integrity and why is it important? (2 marks) Data integrity identifies the quality of the data Garbage in, garbage out ...
Accessing Oakton`s Wireless Network
... including damage to computers resulting from software/hardware installation or Internet use. Please make sure that your computer is configured appropriately to prevent other users on the wireless network from accessing your laptop’s hard drive and files. Disk sharing should be turned off. Wireless n ...
... including damage to computers resulting from software/hardware installation or Internet use. Please make sure that your computer is configured appropriately to prevent other users on the wireless network from accessing your laptop’s hard drive and files. Disk sharing should be turned off. Wireless n ...
Aalborg Universitet
... the source in transmitting in order to increase the throughput. One approach is to let the source spread the data to all devices on its island via its fast local interface. All devices on the island can then transmit parts of the data simultaneously and thus speedup the transmission. On the receivin ...
... the source in transmitting in order to increase the throughput. One approach is to let the source spread the data to all devices on its island via its fast local interface. All devices on the island can then transmit parts of the data simultaneously and thus speedup the transmission. On the receivin ...
WRT600N Datasheet
... of multiple radios for each band, Wireless-N’s “Multiple In, Multiple Out” (MIMO) technology multiplies the effective data rate. Unlike ordinary wireless networking technologies that are confused by signal reflections, MIMO actually uses these reflections to increase the range and reduce “dead spots ...
... of multiple radios for each band, Wireless-N’s “Multiple In, Multiple Out” (MIMO) technology multiplies the effective data rate. Unlike ordinary wireless networking technologies that are confused by signal reflections, MIMO actually uses these reflections to increase the range and reduce “dead spots ...
Business Data Communications and Networking
... when a node is moved to a new subnet Devices: routers, firewalls ...
... when a node is moved to a new subnet Devices: routers, firewalls ...
Packet Tracer – Map a Network Using CDP
... of a recently installed switch that still needs an IP address to be configured. Your task is to create a map of the branch office network. You must record all of the network device names, IP addresses and subnet masks, and physical interfaces interconnecting the network devices, as well as the name ...
... of a recently installed switch that still needs an IP address to be configured. Your task is to create a map of the branch office network. You must record all of the network device names, IP addresses and subnet masks, and physical interfaces interconnecting the network devices, as well as the name ...
1 - University of South Carolina
... TCP and UDP identify applications by 16-bit port numbers Some servers are assigned well-known port number ...
... TCP and UDP identify applications by 16-bit port numbers Some servers are assigned well-known port number ...