Gesture Based Glove For Multiple Applications
... This project presents an autonomous network reconfiguration system (ARS) that enables a multiradio WMN to autonomously recover from local link failures to preserve network performance. By using channel and radio ...
... This project presents an autonomous network reconfiguration system (ARS) that enables a multiradio WMN to autonomously recover from local link failures to preserve network performance. By using channel and radio ...
Slides - the Department of Computer and Information Science
... – common neighbors for arbitrary cell pairs – implications for degree distribution ...
... – common neighbors for arbitrary cell pairs – implications for degree distribution ...
William Stallings Data and Computer Communications
... Blocking/Nonblocking Networks Blocking: network is unable to connect two stations because all possible paths are already in use Nonblocking: permits all possible connection requests because any two stations can be connected ...
... Blocking/Nonblocking Networks Blocking: network is unable to connect two stations because all possible paths are already in use Nonblocking: permits all possible connection requests because any two stations can be connected ...
transparencies
... • Operational interface between EGEE and Geant/NRENs – SLA agreements processing, SLA monitoring – Trouble Ticket system & reporting procedures. – Aiming for a theoretical schema approved by the partners (M12) Mainly we work with the prospect of having a single user-support in EGEE (GGUS by FZK) a ...
... • Operational interface between EGEE and Geant/NRENs – SLA agreements processing, SLA monitoring – Trouble Ticket system & reporting procedures. – Aiming for a theoretical schema approved by the partners (M12) Mainly we work with the prospect of having a single user-support in EGEE (GGUS by FZK) a ...
09-0226 MBR1100 Data Sheet.ai
... transfer and tunnel modes and several Hash and Cipher algorithms. This securely encrypted protocol means your communications from one private network to another is secure from end-to-end. ...
... transfer and tunnel modes and several Hash and Cipher algorithms. This securely encrypted protocol means your communications from one private network to another is secure from end-to-end. ...
Teldat H1 Rail - BidNet Management
... Reliable LTE wireless-WAN broadband performance Cellular interfaces provide uninterrupted connectivity and application continuity when travelling through poor coverage areas. On longer trains, more than one H1 Rail can be deployed along the train, thereby providing higher bandwidth, better redundanc ...
... Reliable LTE wireless-WAN broadband performance Cellular interfaces provide uninterrupted connectivity and application continuity when travelling through poor coverage areas. On longer trains, more than one H1 Rail can be deployed along the train, thereby providing higher bandwidth, better redundanc ...
IST346: Services - Syracuse University
... Unify a set of workstations into a distributed computing environment, since they share common resources. Typical environments have several services, and services often depend on other services. Some services are simple, and have no interaction’s on the user’s part. (network time, or NTP for example) ...
... Unify a set of workstations into a distributed computing environment, since they share common resources. Typical environments have several services, and services often depend on other services. Some services are simple, and have no interaction’s on the user’s part. (network time, or NTP for example) ...
Management Information Systems
... Typically, each protocol uses a single TCP port (or perhaps a few). For example, HTTP usually uses port 80, and SSH usually uses port 22. Some more notes on layers and protocols The picture on P&A page 100 is quite instructive – as you move downwards in the protocol layer “stack”, more and more ...
... Typically, each protocol uses a single TCP port (or perhaps a few). For example, HTTP usually uses port 80, and SSH usually uses port 22. Some more notes on layers and protocols The picture on P&A page 100 is quite instructive – as you move downwards in the protocol layer “stack”, more and more ...
presentation source
... that a service is running on. Think of it as room in a house. The house has an address (IP), but each room (port) provides a certain function. Ports below 1024 are called “well known” ports. Only root has access to start services on these ports. Ports 1024 and above are called “ephemeral” ports. The ...
... that a service is running on. Think of it as room in a house. The house has an address (IP), but each room (port) provides a certain function. Ports below 1024 are called “well known” ports. Only root has access to start services on these ports. Ports 1024 and above are called “ephemeral” ports. The ...
Network Layer (3)
... Virtual Circuit • Circuit means a path between the source and the destination. • Real circuit switching has a physical path set up between the source and the destination, like telephone network – When you dial, a request is sent to the network, network finds if there are free links on the path and ...
... Virtual Circuit • Circuit means a path between the source and the destination. • Real circuit switching has a physical path set up between the source and the destination, like telephone network – When you dial, a request is sent to the network, network finds if there are free links on the path and ...
Follow this link to Network
... module 5 for further specifications. On a campus site, connecting buildings may not be possible using LAN technologies due to the distance involved. Very often a FDDI network is installed to provide a high-speed backbone. ...
... module 5 for further specifications. On a campus site, connecting buildings may not be possible using LAN technologies due to the distance involved. Very often a FDDI network is installed to provide a high-speed backbone. ...
Lecture 3
... • Run programs under special user id such as www and nobody if possible • Some applications such as httpd can change its user id from root to nobody after opening the ...
... • Run programs under special user id such as www and nobody if possible • Some applications such as httpd can change its user id from root to nobody after opening the ...
Fault Tolerance (continued)
... A virus bot is a virus that spreads automatically between systems Worms are not technically viruses A Trojan horse claims to do something useful but instead harms ...
... A virus bot is a virus that spreads automatically between systems Worms are not technically viruses A Trojan horse claims to do something useful but instead harms ...
The core layer of the hierarchical design is the high
... • Typically, access layer switches use multiple links to connect to a distribution layer switch to ensure adequate bandwidth to accommodate the traffic generated on the access layer, and provide fault tolerance in case a link is lost. • Because distribution layer switches accept incoming traffic fro ...
... • Typically, access layer switches use multiple links to connect to a distribution layer switch to ensure adequate bandwidth to accommodate the traffic generated on the access layer, and provide fault tolerance in case a link is lost. • Because distribution layer switches accept incoming traffic fro ...
Hardware Building Blocks and Encoding
... Real communication have some measure of noise. This theorem tells us the limits to a channel’s capacity (in bits per second) in the presence of noise. Shannon’s theorem uses the notion of signal-to-noise ratio (S/N), which is usually expressed in decibels (dB): ...
... Real communication have some measure of noise. This theorem tells us the limits to a channel’s capacity (in bits per second) in the presence of noise. Shannon’s theorem uses the notion of signal-to-noise ratio (S/N), which is usually expressed in decibels (dB): ...
Cross layer design for Wireless networks
... CLD is a way of achieving information sharing between all the layers in order to obtain highest possible adaptivity of any network. This is required to meet the challenging Data rates, higher performance gains and Quality of Services requirements for various real time and non real time applications. ...
... CLD is a way of achieving information sharing between all the layers in order to obtain highest possible adaptivity of any network. This is required to meet the challenging Data rates, higher performance gains and Quality of Services requirements for various real time and non real time applications. ...
Long Term Evolution: Simplify the Migration to 4G Networks
... EPC also supports standard interfaces and open protocols aimed at enabling operators to launch services and applications with Internet speed while also reducing the overall cost per packet through the inherent advantages of going all-IP. Standardized interfaces and protocols also enable operators to ...
... EPC also supports standard interfaces and open protocols aimed at enabling operators to launch services and applications with Internet speed while also reducing the overall cost per packet through the inherent advantages of going all-IP. Standardized interfaces and protocols also enable operators to ...
Nefflow based intrusion detection system
... packet is usually short. Thus, even the attacker try to distribute the scan to long period of time, it can still easily be identified. Longer term aggregation can also be used to uncover distributed TCPRTDP port scan to different hosts in our network. DOS detection The characteristic of DOS and its ...
... packet is usually short. Thus, even the attacker try to distribute the scan to long period of time, it can still easily be identified. Longer term aggregation can also be used to uncover distributed TCPRTDP port scan to different hosts in our network. DOS detection The characteristic of DOS and its ...
Top 100 Network Security Tools
... from a live network or from a capture file on disk. You can interactively browse the capture data, delving down into just the level of packet detail you need. Wireshark has several powerful features, including a rich display filter language and the ability to view the reconstructed stream of a TCP s ...
... from a live network or from a capture file on disk. You can interactively browse the capture data, delving down into just the level of packet detail you need. Wireshark has several powerful features, including a rich display filter language and the ability to view the reconstructed stream of a TCP s ...
Basic Ingredients of Network Management
... network, it makes the devices hard to reach Also hard to find out what it happen ...
... network, it makes the devices hard to reach Also hard to find out what it happen ...
SwitchWare
... Seek to allow new network services to be introduced rapidly. • Active networks are an appealing solution, but no convincing demonstration that they can work … ...
... Seek to allow new network services to be introduced rapidly. • Active networks are an appealing solution, but no convincing demonstration that they can work … ...
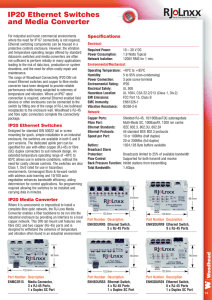
IP20 Ethernet Switches and Media Converter
... enclosure, the switches are available in both 5 and 9 port versions. The dedicated uplink port can be specified for use with either copper (RJ-45) or fibre (SC) duplex connecters to suit network design. An extended temperature operating range of -40ºC to 85ºC allows use in extreme conditions, withou ...
... enclosure, the switches are available in both 5 and 9 port versions. The dedicated uplink port can be specified for use with either copper (RJ-45) or fibre (SC) duplex connecters to suit network design. An extended temperature operating range of -40ºC to 85ºC allows use in extreme conditions, withou ...
level 3sm secure access - Level 3 Communications
... exists today. As IT budgets continue to get pinched and businesses continue to expand, searching for options that will increase accessibility and performance of business applications is critical. That is just what our Level 3 Secure Access Site solution will do for you. We can provide you with a low ...
... exists today. As IT budgets continue to get pinched and businesses continue to expand, searching for options that will increase accessibility and performance of business applications is critical. That is just what our Level 3 Secure Access Site solution will do for you. We can provide you with a low ...