Chapter 4
... bit combination. We like protocols to be transparent because they can be used to transfer binary data such as object programs as well as text data. LAN data link protocols ordinarily provide transparency. ...
... bit combination. We like protocols to be transparent because they can be used to transfer binary data such as object programs as well as text data. LAN data link protocols ordinarily provide transparency. ...
XORs in The Air: Practical Wireless Network Coding
... • Broadcast Ethernet packets at the 2Mbit/s rate for all protocol implementations • The size of the file we distributed was 6.1 MBytes, which at the 1.7 Mbit/s link rate of our testbed takes about 30 seconds to transfer.We limited the experiment run time to 300 seconds. ...
... • Broadcast Ethernet packets at the 2Mbit/s rate for all protocol implementations • The size of the file we distributed was 6.1 MBytes, which at the 1.7 Mbit/s link rate of our testbed takes about 30 seconds to transfer.We limited the experiment run time to 300 seconds. ...
Switching and Routing
... • Where should these functions be realized? – How does the Internet realize these functions? • No deadlock issue • Reliability/flow control/in-order delivery are done at the TCP layer? • The network layer (IP) provides best effort service. – IP is done in the software as well. ...
... • Where should these functions be realized? – How does the Internet realize these functions? • No deadlock issue • Reliability/flow control/in-order delivery are done at the TCP layer? • The network layer (IP) provides best effort service. – IP is done in the software as well. ...
Document
... network security engineers use it to examine security problems developers use it to debug protocol implementations people use it to learn network protocol internals Wireshark isn't an intrusion detection system. Wireshark will not manipulate things on the network, it will only "measure" th ...
... network security engineers use it to examine security problems developers use it to debug protocol implementations people use it to learn network protocol internals Wireshark isn't an intrusion detection system. Wireshark will not manipulate things on the network, it will only "measure" th ...
IEEE 1905.1
... A broad base of industry-leading chipmakers, equipment manufacturers and service providers are collaborating to bring IEEE 1905.1 to fruition. Great for the industry: Enhances user experience and enables next generation connected ...
... A broad base of industry-leading chipmakers, equipment manufacturers and service providers are collaborating to bring IEEE 1905.1 to fruition. Great for the industry: Enhances user experience and enables next generation connected ...
Troubleshooting Scenario Two
... Identify the affected areas of the network Establish if anything has changed Establish the most probable cause Determine if escalation is necessary Create an action plan and solution, identifying potential effects Implement and test the solution Identify the results and effects of the solution Docum ...
... Identify the affected areas of the network Establish if anything has changed Establish the most probable cause Determine if escalation is necessary Create an action plan and solution, identifying potential effects Implement and test the solution Identify the results and effects of the solution Docum ...
slides - network systems lab @ sfu
... protocols; Error detection and correction; Ethernet; Bridges and switches ...
... protocols; Error detection and correction; Ethernet; Bridges and switches ...
Service Assurance and Provisioning for IP Networks
... • Biggest OSS challenge to carriers is managing across multiple technologies and domains • Provisioning must be able to support new technologies from a common Order Management and Provisioning engine • The management of networks can no longer be based on traditional best effort methods • Service ass ...
... • Biggest OSS challenge to carriers is managing across multiple technologies and domains • Provisioning must be able to support new technologies from a common Order Management and Provisioning engine • The management of networks can no longer be based on traditional best effort methods • Service ass ...
Enabling Hitless Engineering of MPLS Networks
... Fragmentation is a problem for MPLS networks too In general, Network Management systems need to provide Network Engineering tools to address fragmentation – “Traffic Engineering puts traffic where the bandwidth is, Network Engineering creates bandwidth where the traffic will be..” – Relatively littl ...
... Fragmentation is a problem for MPLS networks too In general, Network Management systems need to provide Network Engineering tools to address fragmentation – “Traffic Engineering puts traffic where the bandwidth is, Network Engineering creates bandwidth where the traffic will be..” – Relatively littl ...
USER MANUAL microADSB-IP- receiver v.1 =BULLION=
... 2. Can support many modules to access 3. Need to set static IP It is a low cost, easy-to-use mode, you can directly connect module by laptop or mobile phone not depending on wireless router. Security Mechanisms This module supports multiple wireless encryption modes to make sure the user data safe. ...
... 2. Can support many modules to access 3. Need to set static IP It is a low cost, easy-to-use mode, you can directly connect module by laptop or mobile phone not depending on wireless router. Security Mechanisms This module supports multiple wireless encryption modes to make sure the user data safe. ...
William Stallings Data and Computer Communications
... 5/31/00: Vulnerability in the Windows Media Encoder 4.0 and 4.1 which allows a remote user to crash the encoder by connecting to the MSBD service. A bogus packet causes the encoder to attempt to allocate more memory than the computer has resulting in a crash. 6/1/99: OmniHTTPd Web Server comes with ...
... 5/31/00: Vulnerability in the Windows Media Encoder 4.0 and 4.1 which allows a remote user to crash the encoder by connecting to the MSBD service. A bogus packet causes the encoder to attempt to allocate more memory than the computer has resulting in a crash. 6/1/99: OmniHTTPd Web Server comes with ...
An overview of a network design system
... designed to provide a user with methodology for the statement of requirements of an information processing system. NSL, in a form compatible with PSL, allows a user to state design requirements for computer communication networks. The language provides an interface with a set of design models and is ...
... designed to provide a user with methodology for the statement of requirements of an information processing system. NSL, in a form compatible with PSL, allows a user to state design requirements for computer communication networks. The language provides an interface with a set of design models and is ...
1 - Cisco Support Community
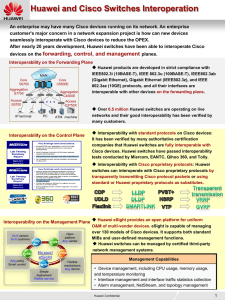
... over 130 models of Cisco devices. It supports both standard MIBs and user-defined management functions. Huawei switches can be managed by certified third-party network management systems. Management Capabilities ...
... over 130 models of Cisco devices. It supports both standard MIBs and user-defined management functions. Huawei switches can be managed by certified third-party network management systems. Management Capabilities ...
Ensuring Public Safety - Alcatel
... An advanced OSS/BSS also enables public safety organization to hold down costs, a crucial consideration in a time of sharply reduced budgets in the public sector as result of the recent global recession. Alcatel-Lucent has a strong background as the trusted partner of public safety organizations to ...
... An advanced OSS/BSS also enables public safety organization to hold down costs, a crucial consideration in a time of sharply reduced budgets in the public sector as result of the recent global recession. Alcatel-Lucent has a strong background as the trusted partner of public safety organizations to ...
TREND Big Picture on Energy-Efficient Backbone Networks Esther Le Rouzic, Raluca-Maria Indre
... bandwidth waste. In current networks the bandwidth of every wavelength channel is dynamically shared between several source-target pairs thanks to electronic switching. Subwavelength photonic switching technologies are also providing this capability. In its simplest form, sub-wavelength switching co ...
... bandwidth waste. In current networks the bandwidth of every wavelength channel is dynamically shared between several source-target pairs thanks to electronic switching. Subwavelength photonic switching technologies are also providing this capability. In its simplest form, sub-wavelength switching co ...
Network Layer
... identifier for host, router interface interface: connection between host/router and physical link ...
... identifier for host, router interface interface: connection between host/router and physical link ...
The Integration of Amateur Radio and 802.11
... addressing and routing of information on the network. On the transport layer, error correcting techniques are employed.3 The session layer allows provisions for data exchange between applications as explained by Tuma and Fajfar. Tuma and Fajfar explained the presentation layer as the layer that ensu ...
... addressing and routing of information on the network. On the transport layer, error correcting techniques are employed.3 The session layer allows provisions for data exchange between applications as explained by Tuma and Fajfar. Tuma and Fajfar explained the presentation layer as the layer that ensu ...
summary notes basic 6 (term 2)
... considerable savings compared to buying individual licensed copies. Its allows easier upgrading of the program. 6. Security. Files and programs on a network are more secure as the users do not have to worry about illegal copying of programs. Passwords can be applied for specific directories to restr ...
... considerable savings compared to buying individual licensed copies. Its allows easier upgrading of the program. 6. Security. Files and programs on a network are more secure as the users do not have to worry about illegal copying of programs. Passwords can be applied for specific directories to restr ...
Week 5
... Routing: calculate the best path to each destination Forwarding: move packets from input to output ...
... Routing: calculate the best path to each destination Forwarding: move packets from input to output ...
How The Internet Works - Directory | CS
... the machines of its research network (ARPANET) to use the new TCP/IP protocols. In 1983, the transition was completed and DARPA demanded that all computers willing to connect to its ...
... the machines of its research network (ARPANET) to use the new TCP/IP protocols. In 1983, the transition was completed and DARPA demanded that all computers willing to connect to its ...
Information Diffusion
... studies in information diffusion: Granovetter: the strength of weak ties J-P Onnela et al: strength of intermediate ties Kossinets et al: strength of backbone ties Davis: board interlocks and adoption of practices ...
... studies in information diffusion: Granovetter: the strength of weak ties J-P Onnela et al: strength of intermediate ties Kossinets et al: strength of backbone ties Davis: board interlocks and adoption of practices ...
Lecture 9 Analyzing Network Packets
... another problem. Because UDP does not guarantee data delivery, your application must perform that function if it is concerned about the data getting to its destination. Just because a device sends a UDP data packet doesn’t necessarily mean that the receiving device received it. You must ensure that ...
... another problem. Because UDP does not guarantee data delivery, your application must perform that function if it is concerned about the data getting to its destination. Just because a device sends a UDP data packet doesn’t necessarily mean that the receiving device received it. You must ensure that ...
24 FE + 4 GE Combo SFP L2 SNMP Switch
... H/W Version: 1 Products Overview LevelOne FGL-2870 is a cost-effective stackable Layer 2 SNMP Ethernet switch with 24 100Base-TX Fast Ethernet ports, 4 Gigabit Ethernet RJ-45 Combo ports which associated with SFP (Small Form Factor Pluggable) slots. It provides reliable and expandable solutions for ...
... H/W Version: 1 Products Overview LevelOne FGL-2870 is a cost-effective stackable Layer 2 SNMP Ethernet switch with 24 100Base-TX Fast Ethernet ports, 4 Gigabit Ethernet RJ-45 Combo ports which associated with SFP (Small Form Factor Pluggable) slots. It provides reliable and expandable solutions for ...
cross_ip - cs.wisc.edu
... n packets destined for a single output port. – Consider n = 8, l = 4 – Pair up packet and flip a coin to choose who “wins” and goes on to the next stage. – Each stage pairs “loosers” and “winners” in feedback format. – 4 packets will be dropped at the last stage – All “winners” emerge at the same ti ...
... n packets destined for a single output port. – Consider n = 8, l = 4 – Pair up packet and flip a coin to choose who “wins” and goes on to the next stage. – Each stage pairs “loosers” and “winners” in feedback format. – 4 packets will be dropped at the last stage – All “winners” emerge at the same ti ...