Nokia Network Services Platform
... traffic flows and services onto alternate paths, will also free up assets to generate additional revenue for carriers. NRC-F works in conjunction with the NSP’s Assurance and Analytics functions that collect link utilization and flow statistics and automatically monitors for congestion. When a traff ...
... traffic flows and services onto alternate paths, will also free up assets to generate additional revenue for carriers. NRC-F works in conjunction with the NSP’s Assurance and Analytics functions that collect link utilization and flow statistics and automatically monitors for congestion. When a traff ...
IP-Forwarding
... Collision domain is the set of ethernet segments that can directly hear each others frames. Worst case is all inputs want to go out on the same output. Must have some buffering and some sort of fairness algorithm inside ...
... Collision domain is the set of ethernet segments that can directly hear each others frames. Worst case is all inputs want to go out on the same output. Must have some buffering and some sort of fairness algorithm inside ...
$doc.title
... Inside the ‘Net: A Different Story… • Closed equipment – So#ware bundled with hardware – Vendor-‐specific interfaces ...
... Inside the ‘Net: A Different Story… • Closed equipment – So#ware bundled with hardware – Vendor-‐specific interfaces ...
Systems Analysis and Design
... We own and operate NCREN (NC Research and Education Network) One of the most advanced statewide research and education networks in the country Provide Internet, video and related services to University of North Carolina’s 16 campus system, Duke, Wake Forest, etc. ...
... We own and operate NCREN (NC Research and Education Network) One of the most advanced statewide research and education networks in the country Provide Internet, video and related services to University of North Carolina’s 16 campus system, Duke, Wake Forest, etc. ...
PPT_ch10
... and sharing among virtual machines • Virtual switch allows VMs to communicate with each other and with nodes on a physical LAN or WAN • Different methods of remote user access exist • Cloud computing provides storage, applications, or services over a network Network+ Guide to Networks, 6th Edition ...
... and sharing among virtual machines • Virtual switch allows VMs to communicate with each other and with nodes on a physical LAN or WAN • Different methods of remote user access exist • Cloud computing provides storage, applications, or services over a network Network+ Guide to Networks, 6th Edition ...
3rd Edition: Chapter 4 - University of Balochistan
... 16-bit port-number field: 60,000 simultaneous connections with a single LAN-side address! NAT is controversial: routers should only process up to layer 3 violates end-to-end argument • NAT possibility must be taken into account by app designers, e.g., P2P applications ...
... 16-bit port-number field: 60,000 simultaneous connections with a single LAN-side address! NAT is controversial: routers should only process up to layer 3 violates end-to-end argument • NAT possibility must be taken into account by app designers, e.g., P2P applications ...
Document
... Autonomous Systems • Global Internet viewed as collection of autonomous systems. • Autonomous system (AS) is a set of routers or networks administered by a single organization • Same routing protocol need not be run within the AS • But, to the outside world, an AS should present a consistent pictur ...
... Autonomous Systems • Global Internet viewed as collection of autonomous systems. • Autonomous system (AS) is a set of routers or networks administered by a single organization • Same routing protocol need not be run within the AS • But, to the outside world, an AS should present a consistent pictur ...
Introduction - Adaptive Systems Lab
... Work Done by: Victor Li & Ji-Her Ju Consider a single channel TDMA network with N mobiles. The TDMA frame consists of q sub-frames each q slots long. Each user is allocated q slots, one in each sub-frame. Problem: Maximize the worst-case throughput of the network such that all users have at least 1 ...
... Work Done by: Victor Li & Ji-Her Ju Consider a single channel TDMA network with N mobiles. The TDMA frame consists of q sub-frames each q slots long. Each user is allocated q slots, one in each sub-frame. Problem: Maximize the worst-case throughput of the network such that all users have at least 1 ...
Network Architectures
... A BSS may be isolated or it may be connected to a backbone distribution system (DS) through an access point (AP). The access point functions as a bridge. The MAC protocol may be fully distributed or controlled by a central coordination function housed in the access point. The BSS generally correspon ...
... A BSS may be isolated or it may be connected to a backbone distribution system (DS) through an access point (AP). The access point functions as a bridge. The MAC protocol may be fully distributed or controlled by a central coordination function housed in the access point. The BSS generally correspon ...
Operational using Lighttours Cost Reduction in WDM Networks Solano*,
... Wavelength-Routing Switches (WRS) that route traffic demands by means of I. A lightpath is a wavelength circuit that connects a pair of WRS in order to transmit data all-optically between them. Most demands require sub-wavelength bandwidth. If each demand is routed through a unique lightpath, there ...
... Wavelength-Routing Switches (WRS) that route traffic demands by means of I. A lightpath is a wavelength circuit that connects a pair of WRS in order to transmit data all-optically between them. Most demands require sub-wavelength bandwidth. If each demand is routed through a unique lightpath, there ...
Product Key Features - D-Link
... The multi-protocol print server makes network connection easy through the use of a NWay connection which allows the print server to be used with either Ethernet or Fast Ethernet LAN. The multi-protocol print server is equipped with high-speed parallel port , and a NWay port, transmitting at either 1 ...
... The multi-protocol print server makes network connection easy through the use of a NWay connection which allows the print server to be used with either Ethernet or Fast Ethernet LAN. The multi-protocol print server is equipped with high-speed parallel port , and a NWay port, transmitting at either 1 ...
Load Balancing Performance in Content Delivery Networks (CDN`s)
... A CDN contains of a unique server called as back-end server comprising new data to be dispersed together with one or more dissemination servers called as surrogate servers. The surrogate servers are dynamically efficient by the back-end server. Surrogate servers are characteristically used to store ...
... A CDN contains of a unique server called as back-end server comprising new data to be dispersed together with one or more dissemination servers called as surrogate servers. The surrogate servers are dynamically efficient by the back-end server. Surrogate servers are characteristically used to store ...
RIVIERA TELEPHONE COMPANY, INC. Broadband
... RTC utilizes an underlying service provider and works with the provider to ensure that all of its customers experience a safe and secure broadband Internet environment that is fast, reliable and affordable. RTC wants its customers to indulge in all that the Internet has to offer, whether it is s ...
... RTC utilizes an underlying service provider and works with the provider to ensure that all of its customers experience a safe and secure broadband Internet environment that is fast, reliable and affordable. RTC wants its customers to indulge in all that the Internet has to offer, whether it is s ...
IOSR Journal of Computer Science (IOSR-JCE) e-ISSN: 2278-0661, p-ISSN: 2278-8727 PP 42-45 www.iosrjournals.org
... Many complicated key exchange or distribution protocols have been designed, but for MANET, they are restricted by a node’s available resources, dynamic network topology, and limited bandwidth. Efficient key agreement and distribution in MANET is an ongoing research area. Most of the current work is ...
... Many complicated key exchange or distribution protocols have been designed, but for MANET, they are restricted by a node’s available resources, dynamic network topology, and limited bandwidth. Efficient key agreement and distribution in MANET is an ongoing research area. Most of the current work is ...
computer networks - Technicalsymposium
... Network Interface Cards (NIC) are working as repeaters. No starting or ending point. Each node will repeat any signal that is on the network regardless its destination. The destination station recognizes its address and copies the frame into a local buffer. The frame continues to circulate until it ...
... Network Interface Cards (NIC) are working as repeaters. No starting or ending point. Each node will repeat any signal that is on the network regardless its destination. The destination station recognizes its address and copies the frame into a local buffer. The frame continues to circulate until it ...
IST Notes - The Bored of Studies Community
... Twisting reduces the amount of interference from other cabling. Unshielded twistedpair (UTP) is used on a network. There are two common standards for UTP called 10Base-T (10 Mbps Ethernet) and 100Base-T (100 Mbps Fast Ethernet). UTP is preferred as it is cheap and easy to install with a maximum dist ...
... Twisting reduces the amount of interference from other cabling. Unshielded twistedpair (UTP) is used on a network. There are two common standards for UTP called 10Base-T (10 Mbps Ethernet) and 100Base-T (100 Mbps Fast Ethernet). UTP is preferred as it is cheap and easy to install with a maximum dist ...
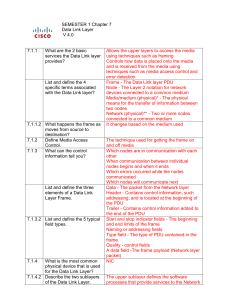
SEMESTER 1 Chapter 5
... A logical topology is the way a network transfers frames from one node to the next. This arrangement consists of virtual connections between the nodes of a network independent of their physical layout. * Regulating the placement of data frames onto the media is known as “media access control”. T ...
... A logical topology is the way a network transfers frames from one node to the next. This arrangement consists of virtual connections between the nodes of a network independent of their physical layout. * Regulating the placement of data frames onto the media is known as “media access control”. T ...
Client-server Systems - University of Manitoba
... The Network Layer sends its packet to the Data Link Layer, which encapsulates the data into a Data Link Layer packet. The Link Layer packet is sent across the network, going through routers, until it is received by the destination, Host B. Each layer of Host B’s protocol stack, starting from the ...
... The Network Layer sends its packet to the Data Link Layer, which encapsulates the data into a Data Link Layer packet. The Link Layer packet is sent across the network, going through routers, until it is received by the destination, Host B. Each layer of Host B’s protocol stack, starting from the ...
TR_BYU_NCL-2003-3
... been the focus of much recent research, but without security at the lower layers, computer networks are left vulnerable to attack. Security features for routing protocols such as the Border Gateway Protocol (BGP) [15] and the Open Shortest Path First (OSPF) protocol [11] have been proposed [12–14, 1 ...
... been the focus of much recent research, but without security at the lower layers, computer networks are left vulnerable to attack. Security features for routing protocols such as the Border Gateway Protocol (BGP) [15] and the Open Shortest Path First (OSPF) protocol [11] have been proposed [12–14, 1 ...
Basic Network Information Rate
... into fiber. Semiconductor and LEDs and laser diodes are used since light output can be modulated by simply varying bias current • At the receiver, a photodetector detects the weakened optical signal and convert it to electric current • The principle figure of merit for a receiver is minimum optical ...
... into fiber. Semiconductor and LEDs and laser diodes are used since light output can be modulated by simply varying bias current • At the receiver, a photodetector detects the weakened optical signal and convert it to electric current • The principle figure of merit for a receiver is minimum optical ...
Occupational Profile - Aurora Public Schools
... Knowledge, Skills, and Abilities There is no information about knowledge, skills and abilities. This may occur because data has not been collected or because this is a composite occupation (e.g., "All Other"). ...
... Knowledge, Skills, and Abilities There is no information about knowledge, skills and abilities. This may occur because data has not been collected or because this is a composite occupation (e.g., "All Other"). ...
Combining Feature Selection and Neural Networks for Solving
... The major criticisms of a neural network approach include the fact that because neural networks learn the classification rules by multiple passes over the training data set, the learning time, or the training time needed for a neural network to obtain a high classification rate, is usually long[1]. ...
... The major criticisms of a neural network approach include the fact that because neural networks learn the classification rules by multiple passes over the training data set, the learning time, or the training time needed for a neural network to obtain a high classification rate, is usually long[1]. ...
MPLS PPT
... MPLS is a highly scalable, protocol agnostic, data-carrying mechanism. In an MPLS network, data packets are assigned labels. Packetforwarding decisions are made solely on the contents of this label, without the need to examine the packet itself. This allows one to create end-to-end circuits across a ...
... MPLS is a highly scalable, protocol agnostic, data-carrying mechanism. In an MPLS network, data packets are assigned labels. Packetforwarding decisions are made solely on the contents of this label, without the need to examine the packet itself. This allows one to create end-to-end circuits across a ...
Part I: Introduction
... 1.2 Network edge 1.3 Network core 1.4 Network access and physical media 1.5 Internet structure and ISPs 1.6 Delay & loss in packet-switched networks 1.7 Protocol layers, service models 1.8 History Introduction ...
... 1.2 Network edge 1.3 Network core 1.4 Network access and physical media 1.5 Internet structure and ISPs 1.6 Delay & loss in packet-switched networks 1.7 Protocol layers, service models 1.8 History Introduction ...