20061019-internet2intro
... bandwidths, for variable lengths of time • Capable of lightpath provisioning to the campus ...
... bandwidths, for variable lengths of time • Capable of lightpath provisioning to the campus ...
coverage
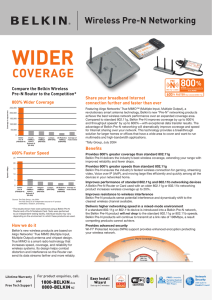
... Router and a Pre-N Notebook Card. Tests were performed by an independent testing facility, individual results may vary depending on the environment in which these products are used. ...
... Router and a Pre-N Notebook Card. Tests were performed by an independent testing facility, individual results may vary depending on the environment in which these products are used. ...
www.c-jump.com
... – Network Address Translation (NAT) • Hides the IP addresses of network devices from attackers • Private addresses • NAT removes the private IP address from the sender’s packet and replaces it with an alias IP address ...
... – Network Address Translation (NAT) • Hides the IP addresses of network devices from attackers • Private addresses • NAT removes the private IP address from the sender’s packet and replaces it with an alias IP address ...
Software Defined Network and Network Virtualization
... and an action associated with each flow entry – The control path consists of a controller which programs the flow entry in the flow table ...
... and an action associated with each flow entry – The control path consists of a controller which programs the flow entry in the flow table ...
Emergency Communication - dumbo-isif
... Please make sure the version is shown correctly. 3. Install JMF After that, run JMF Registry and click "Detect Capture Devices" 4. Setup ad hoc mode on wireless interface. Make sure that you use a correct given IP address. -To run software Double click MainStartup.bat in EasyDC folder -To run HQ sof ...
... Please make sure the version is shown correctly. 3. Install JMF After that, run JMF Registry and click "Detect Capture Devices" 4. Setup ad hoc mode on wireless interface. Make sure that you use a correct given IP address. -To run software Double click MainStartup.bat in EasyDC folder -To run HQ sof ...
A Comparative Study of Wireless Technologies: Zigbee, Bluetooth
... Signals and its frequency bands are licence free in most parts of the world. Synchronous and Asynchronous operations are depending upon network size and applications and support a variety of mesh networks from simple point to point connections to advanced tree structure with multiple repeaters. [1] ...
... Signals and its frequency bands are licence free in most parts of the world. Synchronous and Asynchronous operations are depending upon network size and applications and support a variety of mesh networks from simple point to point connections to advanced tree structure with multiple repeaters. [1] ...
Security Services Gateways
... involves dropping the packet and logging the action. Stateful inspection provides more security than other firewall technologies such as packet filtering because the traffic is examined under the context of the connection and not as a collection of various packets. By default, the Juniper Networks f ...
... involves dropping the packet and logging the action. Stateful inspection provides more security than other firewall technologies such as packet filtering because the traffic is examined under the context of the connection and not as a collection of various packets. By default, the Juniper Networks f ...
Brief Announcement: A Conjecture on
... In fact, the algorithm to trace odd rings does make use of this characteristic. In the algorithm, we begin by fixing a terminal node a and marking the nodes of one trace (a...b) randomly around the ring (clockwise or counterclockwise). Next, we place all remaining traces with terminal node a on the ...
... In fact, the algorithm to trace odd rings does make use of this characteristic. In the algorithm, we begin by fixing a terminal node a and marking the nodes of one trace (a...b) randomly around the ring (clockwise or counterclockwise). Next, we place all remaining traces with terminal node a on the ...
Heterogeneous Device Networking
... logic. For networking 4-20 ma sensor types, their output current is switched directly onto the FGI 4-20 ma signal line, and digitized at the controller. This maximizes network performance, since no packet protocol is needed for device selection or data measurement. Similarly, simple digital devices ...
... logic. For networking 4-20 ma sensor types, their output current is switched directly onto the FGI 4-20 ma signal line, and digitized at the controller. This maximizes network performance, since no packet protocol is needed for device selection or data measurement. Similarly, simple digital devices ...
ppt - Courses
... How Does the WWW Work? • How does the computer at Oski’s desk figure out where the i206 web pages are? • In order for him to use the WWW, Oski’s computer must be connected to another machine acting as a web server (via his ISP). • This machine is in turn connected to other computers, some of which ...
... How Does the WWW Work? • How does the computer at Oski’s desk figure out where the i206 web pages are? • In order for him to use the WWW, Oski’s computer must be connected to another machine acting as a web server (via his ISP). • This machine is in turn connected to other computers, some of which ...
Architektura software defined data center
... taking/restoring a checkpoint. Restoring a checkpoint is like restoring a clean backup of the server. Linux: Linux virtual machines flush their file system buffers to create a file system consistent checkpoint. Production as default: New virtual machines will use production checkpoints with a fallba ...
... taking/restoring a checkpoint. Restoring a checkpoint is like restoring a clean backup of the server. Linux: Linux virtual machines flush their file system buffers to create a file system consistent checkpoint. Production as default: New virtual machines will use production checkpoints with a fallba ...
Lightwave Communication Systems Laboratory - ITTC
... What we’ve done • Developed high fidelity model for fiber transport • Applied model to address WDM over DSF issues raised by Sprint • Model has also been used by Sprint’s Network Planning group ...
... What we’ve done • Developed high fidelity model for fiber transport • Applied model to address WDM over DSF issues raised by Sprint • Model has also been used by Sprint’s Network Planning group ...
CSIT560 Project Presentation
... authentication is initiated when a user associates with an access point. The AP blocks access to the network until the user can be authenticated. The user provides credentials which are communicated to the authentication server. The authentication process is enabled by the IEEE 802.1X/EAP framewor ...
... authentication is initiated when a user associates with an access point. The AP blocks access to the network until the user can be authenticated. The user provides credentials which are communicated to the authentication server. The authentication process is enabled by the IEEE 802.1X/EAP framewor ...
See through patterns, hidden relationships and
... Figure 1: Continuous monitoring technologies alone cannot perform long-term contextual analysis. When deployed in conjunction with the Deep Analysis Cyber Solution, new alerts from these technologies can be linked to historical behavior and attack patterns to identify persistent, “low and slow” atta ...
... Figure 1: Continuous monitoring technologies alone cannot perform long-term contextual analysis. When deployed in conjunction with the Deep Analysis Cyber Solution, new alerts from these technologies can be linked to historical behavior and attack patterns to identify persistent, “low and slow” atta ...
Configuring the switch port.
... One of the first things to consider is whether or not there will be VLANs (virtual local area networks). While switches may break up collision domains, they do not break up broadcast domains. VLANs, on the other hand, will. VLANs take a single network environment and create smaller network segments ...
... One of the first things to consider is whether or not there will be VLANs (virtual local area networks). While switches may break up collision domains, they do not break up broadcast domains. VLANs, on the other hand, will. VLANs take a single network environment and create smaller network segments ...
Chapter 1 - EECS User Home Pages
... time waiting at output link for transmission depends on congestion level of router Introduction 1-47 ...
... time waiting at output link for transmission depends on congestion level of router Introduction 1-47 ...
Introduction
... They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the ...
... They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the ...
Use of a WDM network
... – Is there a problem if the IP traffic delivered at the far-end router does not replicate burstiness? ...
... – Is there a problem if the IP traffic delivered at the far-end router does not replicate burstiness? ...
SAQ D Compliance Scott St. Aubin Senior Security Consultant QSA, CISM, CISSP
... Requirement 10: Track and monitor all access to network resources and CHD • Log Management Requirements – All critical system clocks and times are synchronized – Secure audit trails so they cannot be altered – Review logs at least daily (e.g. IDS, AAA). Tools may be used!! – Retain at least one yea ...
... Requirement 10: Track and monitor all access to network resources and CHD • Log Management Requirements – All critical system clocks and times are synchronized – Secure audit trails so they cannot be altered – Review logs at least daily (e.g. IDS, AAA). Tools may be used!! – Retain at least one yea ...
Multilayer Networks: An Architecture Framework
... • Layer 2 for L2SC (often Ethernet) • Layer 1.5 for TDM (often SONET/SDH) • Layer 1 for LSC (often WDM switch elements) • Layer 0 for FSC (often port switching devices based on optical or mechanical technologies) Each of these technology types includes unique features and capabilities. Furthermore, ...
... • Layer 2 for L2SC (often Ethernet) • Layer 1.5 for TDM (often SONET/SDH) • Layer 1 for LSC (often WDM switch elements) • Layer 0 for FSC (often port switching devices based on optical or mechanical technologies) Each of these technology types includes unique features and capabilities. Furthermore, ...
Mobile IP
... Does not scale with the number of mobile hosts and frequent changes in the location IP hierarchies can not be used. ...
... Does not scale with the number of mobile hosts and frequent changes in the location IP hierarchies can not be used. ...
Document
... Prototype system built in software (currently working on the hardware) Ran in 9 workstation network for a month ...
... Prototype system built in software (currently working on the hardware) Ran in 9 workstation network for a month ...