Internet Protocols
... corresponding to a particular internetwork address. ARP is sufficiently generic to allow use of IP with virtually any type of underlying media-access mechanism. RARP uses broadcast messages to determine the Internet address associated with a particular hardware address. RARP is particularly importan ...
... corresponding to a particular internetwork address. ARP is sufficiently generic to allow use of IP with virtually any type of underlying media-access mechanism. RARP uses broadcast messages to determine the Internet address associated with a particular hardware address. RARP is particularly importan ...
Link Prediction using Supervised Learning
... arbitrary scientists x and y from the social network. The probability that x and y coauthor is, say p1. Then, we choose one scientist z, from the same network, who works mostly on multi-disciplinary research, thus has established a rich set of connections in the community. Now, if p2 is the probabil ...
... arbitrary scientists x and y from the social network. The probability that x and y coauthor is, say p1. Then, we choose one scientist z, from the same network, who works mostly on multi-disciplinary research, thus has established a rich set of connections in the community. Now, if p2 is the probabil ...
WAN Backbones
... Creating a VC, sending one cell (packet), and closing the VC is very inefficient and should be avoided The cell transport layer handles circuit management If a VC already exists and is open, the cell transport layer uses the existing VC for transmission If no VC is available to the node, a VC is cre ...
... Creating a VC, sending one cell (packet), and closing the VC is very inefficient and should be avoided The cell transport layer handles circuit management If a VC already exists and is open, the cell transport layer uses the existing VC for transmission If no VC is available to the node, a VC is cre ...
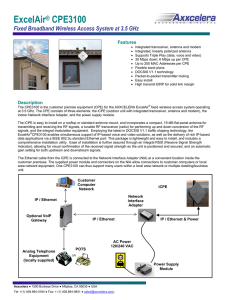
ExcelAir® CPE3100
... comprehensive installation utility. Ease of installation is further assured through an integral RSSI (Receive Signal Strength Indicator), allowing for visual confirmation of the received signal strength as the unit is positioned and secured, and an automatic gain setting for both upstream and downst ...
... comprehensive installation utility. Ease of installation is further assured through an integral RSSI (Receive Signal Strength Indicator), allowing for visual confirmation of the received signal strength as the unit is positioned and secured, and an automatic gain setting for both upstream and downst ...
Protocols
... A bridge is a combination of hardware and software that enables devices on similar networks to communicate © Paradigm Publishing Inc. ...
... A bridge is a combination of hardware and software that enables devices on similar networks to communicate © Paradigm Publishing Inc. ...
The OSI Model: Understanding the Seven Layers of Computer
... “Everybody says this is the right solution.” “I read in an airline magazine that this was the best way to do it so that is what we will do.” What these managers seem to forget is that they are paying a highly qualified staff to provide them with useful information. These managers bypass planning in ...
... “Everybody says this is the right solution.” “I read in an airline magazine that this was the best way to do it so that is what we will do.” What these managers seem to forget is that they are paying a highly qualified staff to provide them with useful information. These managers bypass planning in ...
Lecturing Notes 6
... Covers large geographical areas Circuits provided by a common carrier Consists of interconnected switching nodes Traditional WANs provide modest capacity ...
... Covers large geographical areas Circuits provided by a common carrier Consists of interconnected switching nodes Traditional WANs provide modest capacity ...
ppt
... WLAN for local and cellular for external connectivity The NEMO contains a Mobile Router (co-located FA with routing capabilities) “Hides” away mobility from the NEMO users (e.g. through Mobile IP tunneling) Nested mobility for MIP clients in the NEMO (tunnel in tunnel) ...
... WLAN for local and cellular for external connectivity The NEMO contains a Mobile Router (co-located FA with routing capabilities) “Hides” away mobility from the NEMO users (e.g. through Mobile IP tunneling) Nested mobility for MIP clients in the NEMO (tunnel in tunnel) ...
Linux+ Guide to Linux Certification
... configured. • Description: In this activity, you verify the Windows Firewall configuration in Windows XP. Service Pack 2 or higher should already be installed in Windows XP, or Service Pack 1 or higher in Windows Server 2003. You need to log on ...
... configured. • Description: In this activity, you verify the Windows Firewall configuration in Windows XP. Service Pack 2 or higher should already be installed in Windows XP, or Service Pack 1 or higher in Windows Server 2003. You need to log on ...
Chapter 5: STP * What is STP? How does STP work? * What would
... been disabled on those switches, a Layer 2 loop can occur. If STP is enabled on these switches, which is the default, a Layer 2 loop would not occur. Broadcast frames are forwarded out all switch ports, except the originating port. This ensures that all devices in the broadcast domain are able to re ...
... been disabled on those switches, a Layer 2 loop can occur. If STP is enabled on these switches, which is the default, a Layer 2 loop would not occur. Broadcast frames are forwarded out all switch ports, except the originating port. This ensures that all devices in the broadcast domain are able to re ...
HW1 Solution
... Consider an IPv4 subnet with private IP address space 166.111.8.0/24. If each IP interface in the subnet needs a distinct IP address, then how many IP interfaces can there be in the subnet? [Hint: to obtain the right answer, please look up what is a broadcast address online.] [Solution] There is a t ...
... Consider an IPv4 subnet with private IP address space 166.111.8.0/24. If each IP interface in the subnet needs a distinct IP address, then how many IP interfaces can there be in the subnet? [Hint: to obtain the right answer, please look up what is a broadcast address online.] [Solution] There is a t ...
Wireless LANS and PANS
... • WLANs are handy in areas affected by earthquakes or other disasters. • WLANs are good solutions in places where wiring may not be permitted. ...
... • WLANs are handy in areas affected by earthquakes or other disasters. • WLANs are good solutions in places where wiring may not be permitted. ...
Chapter II - Austin Community College
... data transmission session – independently of the actual data flow over the network Detects if the transmission has been cut off, notifies the client software, and restart its at the appropriate point Determines the order of communication, maximum duration of transmission, and provides clocking o ...
... data transmission session – independently of the actual data flow over the network Detects if the transmission has been cut off, notifies the client software, and restart its at the appropriate point Determines the order of communication, maximum duration of transmission, and provides clocking o ...
Connecting to IPv6 ...for Mac OS X
... Note: The following instructions require administrator or equivalent privileges on the computer that is being configured for IPv6. The following instructions cover both Mac OS X 10.4 (Tiger) and Mac OS X 10.5 (Leopard). The older Mac OS X versions 10.2 and 10.3 also include IPv6 support, and the pro ...
... Note: The following instructions require administrator or equivalent privileges on the computer that is being configured for IPv6. The following instructions cover both Mac OS X 10.4 (Tiger) and Mac OS X 10.5 (Leopard). The older Mac OS X versions 10.2 and 10.3 also include IPv6 support, and the pro ...
connection
... Connection-oriented packet-switched networks imitate circuit-switched network. In order for two users to communicate a virtual circuit or a connection has to be first established by the network. The following three phases are involved: – connection establishment, – data transfer, and – connection d ...
... Connection-oriented packet-switched networks imitate circuit-switched network. In order for two users to communicate a virtual circuit or a connection has to be first established by the network. The following three phases are involved: – connection establishment, – data transfer, and – connection d ...
MA-100 Media Adaptor
... single NetComplete server can connect to up to 10 separate ESAMs to manage a large number of MA-100s. ...
... single NetComplete server can connect to up to 10 separate ESAMs to manage a large number of MA-100s. ...
ppt
... – The host broadcasts a request: “What is the MAC address of 127.123.115.08?” – The host whose IP address is 127.123.115.08 replies back: “The MAC address for 127.123.115.08 is 8A-5F-3C-23-45-5616” ...
... – The host broadcasts a request: “What is the MAC address of 127.123.115.08?” – The host whose IP address is 127.123.115.08 replies back: “The MAC address for 127.123.115.08 is 8A-5F-3C-23-45-5616” ...
MV3621812185
... Shanasa Rahel et al Int. Journal of Engineering Research and Applications ISSN : 2248-9622, Vol. 3, Issue 6, Nov-Dec 2013, pp.2181-2185 link layer (LL), the interface queue (IFQ), the designed MAC layer (WiMAX module), and the PHY layer (Channel). First, the TGA is considered simply as an applicati ...
... Shanasa Rahel et al Int. Journal of Engineering Research and Applications ISSN : 2248-9622, Vol. 3, Issue 6, Nov-Dec 2013, pp.2181-2185 link layer (LL), the interface queue (IFQ), the designed MAC layer (WiMAX module), and the PHY layer (Channel). First, the TGA is considered simply as an applicati ...
The OSI Reference Model
... is a theoretical blueprint that helps us understand how data gets from one user’s computer to another. ...
... is a theoretical blueprint that helps us understand how data gets from one user’s computer to another. ...
Link Layer - Southern Adventist University
... • ATM Adaptation Layer (AAL): “adapts” upper layers (IP or native ATM applications) to ATM layer below • AAL present only in end systems, not in switches • AAL layer segment (header/trailer fields, data) fragmented ...
... • ATM Adaptation Layer (AAL): “adapts” upper layers (IP or native ATM applications) to ATM layer below • AAL present only in end systems, not in switches • AAL layer segment (header/trailer fields, data) fragmented ...
Chapter One
... Do not untwist twisted-pair cables more than one-half inch before inserting them Do not strip off more than one inch of insulation from copper wire in twisted-pair cables Watch bend radius limitations for cable ...
... Do not untwist twisted-pair cables more than one-half inch before inserting them Do not strip off more than one inch of insulation from copper wire in twisted-pair cables Watch bend radius limitations for cable ...
FCAPS - azimi.edu
... network device, storing and documenting that data, and subsequently utilizing that data to manage the operations of all network devices Includes the initial configuration of a device to bring it up, ...
... network device, storing and documenting that data, and subsequently utilizing that data to manage the operations of all network devices Includes the initial configuration of a device to bring it up, ...
Networks
... Chapter 6 Summary • Computer networks link two or more computers to exchange data and share resources. • Two types of computer networks: Local area network (LAN) Wide area network (WAN) • Computer networks: Reduce hardware costs Enable users to share applications Provide a means to pool an organizat ...
... Chapter 6 Summary • Computer networks link two or more computers to exchange data and share resources. • Two types of computer networks: Local area network (LAN) Wide area network (WAN) • Computer networks: Reduce hardware costs Enable users to share applications Provide a means to pool an organizat ...