Lecture 12 – MAC - UTK-EECS
... dest, Ethernet frame contains A-to-B IP datagram A’s data link layer sends Ethernet frame R’s data link layer receives Ethernet frame R removes IP datagram from Ethernet frame, sees its destined to B R uses ARP to get B’s physical layer address R creates frame containing A-to-B IP datagram sends to ...
... dest, Ethernet frame contains A-to-B IP datagram A’s data link layer sends Ethernet frame R’s data link layer receives Ethernet frame R removes IP datagram from Ethernet frame, sees its destined to B R uses ARP to get B’s physical layer address R creates frame containing A-to-B IP datagram sends to ...
Quick-Start Guide
... 2. Connect the other end of the straight-through Ethernet cable (RJ-45) to the Ethernet port on your computer. 3. Plug the DSL cable (RJ-11) into the DSL port on the SpeedStream® device (gray port). 4. Plug the other end of the DSL cable (RJ-11) into the phone jack. 5. Plug the power adapter into th ...
... 2. Connect the other end of the straight-through Ethernet cable (RJ-45) to the Ethernet port on your computer. 3. Plug the DSL cable (RJ-11) into the DSL port on the SpeedStream® device (gray port). 4. Plug the other end of the DSL cable (RJ-11) into the phone jack. 5. Plug the power adapter into th ...
HotView Pro™ Network Management Software
... to point wireless backhaul—for example, to connect two mesh networks. In the linear mode, both radios operate independently enabling sustained bandwidth levels over an unlimited number of hops. This enables long linear topologies, such as when networking a railway line, and provides a sustained leve ...
... to point wireless backhaul—for example, to connect two mesh networks. In the linear mode, both radios operate independently enabling sustained bandwidth levels over an unlimited number of hops. This enables long linear topologies, such as when networking a railway line, and provides a sustained leve ...
Upcoming Requirements from the US Law Enforcement Community
... Wiretaps Without CALEA • Traditionally, wiretapping has been a manual process: -- A court of competent jurisdiction would issue suitable an order authorizing a wiretap to occur, -- The local provider (whether that's a telephone company, Internet service provider, or other entity) would be contacted ...
... Wiretaps Without CALEA • Traditionally, wiretapping has been a manual process: -- A court of competent jurisdiction would issue suitable an order authorizing a wiretap to occur, -- The local provider (whether that's a telephone company, Internet service provider, or other entity) would be contacted ...
Wireless Embedded Roadway Health Monitoring System - May15-23
... Dr. Daji Qiao, Dr. Jiming Song, Tie Qui, Jeramie Vens ...
... Dr. Daji Qiao, Dr. Jiming Song, Tie Qui, Jeramie Vens ...
Lesson 2-3: Ethernet Basics
... Collision Detection means that a sending device can “detect” simultaneous transmission attempts. When two or more devices try to send data at the same time, the signals collide. The illustration above shows devices A, B, and C sending signals simultaneously, and a collision occurs. When this happens ...
... Collision Detection means that a sending device can “detect” simultaneous transmission attempts. When two or more devices try to send data at the same time, the signals collide. The illustration above shows devices A, B, and C sending signals simultaneously, and a collision occurs. When this happens ...
DiscJuggler - Padus, Inc.
... that do not contain a single disc drive; only a network connection is needed. Optical disc savings Your business gets higher quality CD and DVD production at a lower cost, thanks to centralized robotic hardware using the best drives the industry has to offer. DiscJuggler.NET not only offers a rich a ...
... that do not contain a single disc drive; only a network connection is needed. Optical disc savings Your business gets higher quality CD and DVD production at a lower cost, thanks to centralized robotic hardware using the best drives the industry has to offer. DiscJuggler.NET not only offers a rich a ...
The OSI Reference Model - Department of Computing
... Commonly referred to as the OSI reference model. ...
... Commonly referred to as the OSI reference model. ...
3GPP2 “Evolving to Future Wireless Technology”
... to a common packet-based core network Various access systems (e.g. 3G cellular, a new radio Interface, W-LAN, Short range radio, and wired access, etc.) will be connected via flexible core networks. User can be connected via a variety of different access systems to the networks. “Access Indepe ...
... to a common packet-based core network Various access systems (e.g. 3G cellular, a new radio Interface, W-LAN, Short range radio, and wired access, etc.) will be connected via flexible core networks. User can be connected via a variety of different access systems to the networks. “Access Indepe ...
07.ciulli - Future Internet Assembly
... SDN & NFV are broad and wild field; research is key to pioneer in the SDN farwest and validate intuitions before standards can regulate it ...
... SDN & NFV are broad and wild field; research is key to pioneer in the SDN farwest and validate intuitions before standards can regulate it ...
Topology
... • Does more than simply regenerate signals • Looks just like a hub, with several ports for connecting workstations in a star topology • Determines to which port the destination device is connected and forwards the message to that port – This capability allows a switch to handle several conversations ...
... • Does more than simply regenerate signals • Looks just like a hub, with several ports for connecting workstations in a star topology • Determines to which port the destination device is connected and forwards the message to that port – This capability allows a switch to handle several conversations ...
Windows Server 2008
... • FDDI uses dual ring – Data travels in both directions – One ring failure doesn’t break network – Operates using fiber-optic cable at 100 Mbps – Extended star topologies with Gigabit Ethernet have largely replaced FDDI ...
... • FDDI uses dual ring – Data travels in both directions – One ring failure doesn’t break network – Operates using fiber-optic cable at 100 Mbps – Extended star topologies with Gigabit Ethernet have largely replaced FDDI ...
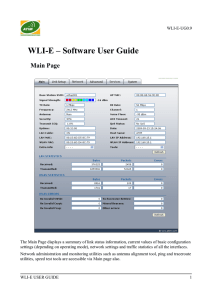
WLI-E – Software User Guide
... Tx/Rx Rate represents the data rates of the last transmitted and received packets; Tx/Rx Packets value represents the total amount of packets transmitted to and received from the Station during the connection uptime; Tx/Rx Packet Rate (packets per second) represents the mean value of the transmitted ...
... Tx/Rx Rate represents the data rates of the last transmitted and received packets; Tx/Rx Packets value represents the total amount of packets transmitted to and received from the Station during the connection uptime; Tx/Rx Packet Rate (packets per second) represents the mean value of the transmitted ...
Understanding Traceroute
... server’s OS can still process ICMP efficiently - even if the server is overloaded with disk-read requests or is switching between too many server processes. Many users assume that a request to download a Web page establishes some sort of two-way communication channel with its server. Traceroute’s ou ...
... server’s OS can still process ICMP efficiently - even if the server is overloaded with disk-read requests or is switching between too many server processes. Many users assume that a request to download a Web page establishes some sort of two-way communication channel with its server. Traceroute’s ou ...
行動多媒體通訊標準參考模式(Reference Models)
... and mobility layer across the whole system. • Recognise that the access network structure and capabilities will vary depending upon the environment that it is being served (e.g. domestic, business, satellite environments). • Support the different access networks by providing a common interface struc ...
... and mobility layer across the whole system. • Recognise that the access network structure and capabilities will vary depending upon the environment that it is being served (e.g. domestic, business, satellite environments). • Support the different access networks by providing a common interface struc ...
CS412 Introduction to Computer Networking & Telecommunication
... Node is either tentative or permanent Initially tentative As a path from source to that node discovered, label becomes permanent and never gets changed ...
... Node is either tentative or permanent Initially tentative As a path from source to that node discovered, label becomes permanent and never gets changed ...
Network Management Integration Options
... Heartbeat - Every Hotspot Controller in the network sends heartbeats to the Hotspot OSS Server. This information is used to monitor its health, status and user connections. Different filters are provided to easily locate and provide quick relief measures in case of a controller outage. Also, integ ...
... Heartbeat - Every Hotspot Controller in the network sends heartbeats to the Hotspot OSS Server. This information is used to monitor its health, status and user connections. Different filters are provided to easily locate and provide quick relief measures in case of a controller outage. Also, integ ...
Module 2: Networking Fundamentals
... Sneakernet created multiple copies of the data If two people modified the file and then tried to share it, what will happen ?. Businesses needed a solution to address the following problems: How to avoid duplication of equipment and resources How to communicate efficiently How to set up and ma ...
... Sneakernet created multiple copies of the data If two people modified the file and then tried to share it, what will happen ?. Businesses needed a solution to address the following problems: How to avoid duplication of equipment and resources How to communicate efficiently How to set up and ma ...
How to connect ALPHA signs to Profibus DP Technical support
... The ALPHA Gateway I/O interface is built with three distinct modules that are described in the tables that follow. Note that the CPU module and Power module are physically interchangeable. Either of them can be mounted next to the Gateway Interface Module. • CPU Module — serves as an interface betwe ...
... The ALPHA Gateway I/O interface is built with three distinct modules that are described in the tables that follow. Note that the CPU module and Power module are physically interchangeable. Either of them can be mounted next to the Gateway Interface Module. • CPU Module — serves as an interface betwe ...
How to Hack Your Mini Cooper: Reverse Engineering CAN Jason Staggs
... security of the underlying protocol is dubious at best. The Bosch CAN standard does not include inherent security mechanisms for authentication and validation of messages sent to various ECUs over a CAN network. Currently the only data security methods for CAN networks on passenger vehicles are the ...
... security of the underlying protocol is dubious at best. The Bosch CAN standard does not include inherent security mechanisms for authentication and validation of messages sent to various ECUs over a CAN network. Currently the only data security methods for CAN networks on passenger vehicles are the ...
Week6LectureNote
... communication from one end device to another end device. • Examine the most common Network layer protocol, Internet Protocol (IP), and its features for providing connectionless and best-effort service. • Understand the principles used to guide the division, or grouping, of devices into networks. • U ...
... communication from one end device to another end device. • Examine the most common Network layer protocol, Internet Protocol (IP), and its features for providing connectionless and best-effort service. • Understand the principles used to guide the division, or grouping, of devices into networks. • U ...