Part I: Introduction
... There exists a specific routing algorithm, s.t., for any sequence of connections and releases, Any unused input can be routed to any unused output, assuming all the sequence was served by the routing ...
... There exists a specific routing algorithm, s.t., for any sequence of connections and releases, Any unused input can be routed to any unused output, assuming all the sequence was served by the routing ...
Boguslawski, P., Mahdjoubi, L., Zverovich, V. and Fadli, F. (2016)
... The graph G together with VDN generated for individual spaces will be denoted by G+. It should be noted that the navigable network G+ consists of several graphs: G (logical network) and additional networks, GI – Gn, generated within some spaces. They do not form one connected graph: additional netwo ...
... The graph G together with VDN generated for individual spaces will be denoted by G+. It should be noted that the navigable network G+ consists of several graphs: G (logical network) and additional networks, GI – Gn, generated within some spaces. They do not form one connected graph: additional netwo ...
Basic Concepts
... Figure 1-24: Cryptographic Protections • Message-by-Message Protections – Encryption to provide confidentiality so that an eavesdropper cannot reach intercepted messages – Electronic signatures provide message-by-message authentication to prevent the insertion of messages by an impostor after initi ...
... Figure 1-24: Cryptographic Protections • Message-by-Message Protections – Encryption to provide confidentiality so that an eavesdropper cannot reach intercepted messages – Electronic signatures provide message-by-message authentication to prevent the insertion of messages by an impostor after initi ...
Some Sample Commercial Network Costs
... e-VLBI is one among many applications • HENP – high-energy physics community is currently heaviest user of international networks, mainly in dissemination of very large data files from major HENP facilities in Europe and U.S. • Astronomy in general – optical telescopes are now sending highresolutio ...
... e-VLBI is one among many applications • HENP – high-energy physics community is currently heaviest user of international networks, mainly in dissemination of very large data files from major HENP facilities in Europe and U.S. • Astronomy in general – optical telescopes are now sending highresolutio ...
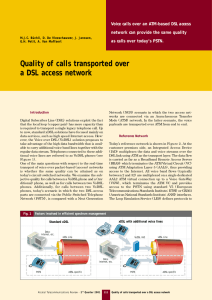
Quality of calls transported over a DSL access network
... Reference Network Today’s reference network is shown in Figure 2. At the customer premises side, an Integrated Access Device (IAD) multiplexes the data and voice streams over the DSL link using ATM as the transport layer. The data flow is carried as far as a Broadband Remote Access Server (BRAS) whi ...
... Reference Network Today’s reference network is shown in Figure 2. At the customer premises side, an Integrated Access Device (IAD) multiplexes the data and voice streams over the DSL link using ATM as the transport layer. The data flow is carried as far as a Broadband Remote Access Server (BRAS) whi ...
Bro: A System for Detecting NetwoRk Intruders in Real-Time
... Bro is specifically well-suited for scientific environments ...
... Bro is specifically well-suited for scientific environments ...
Ethernet - Gadjah Mada University
... provides the interface between the Ethernet MAC and the upper layers in the protocol stack of the end station. The LLC sublayer is defined by IEEE 802.2 standards. • Bridge entity, if the unit is a DCE. Bridge entities provide LAN-to-LAN interfaces between LANs that use the same protocol (for exampl ...
... provides the interface between the Ethernet MAC and the upper layers in the protocol stack of the end station. The LLC sublayer is defined by IEEE 802.2 standards. • Bridge entity, if the unit is a DCE. Bridge entities provide LAN-to-LAN interfaces between LANs that use the same protocol (for exampl ...
gz01-lecture08
... – Some loss of flexibility, but the gain in interoperability more than makes up for this – Because IP is embedded in applications and in interdomain routing, it is very hard to change – Having IP be universal made this mistake easier to ...
... – Some loss of flexibility, but the gain in interoperability more than makes up for this – Because IP is embedded in applications and in interdomain routing, it is very hard to change – Having IP be universal made this mistake easier to ...
Preliminary Works
... Recommended Resources for this Learning Activity No external resources are needed for this lab. All commands and functions are built into the Windows operating system. The commands that will be used are: IPCONFIG – IP addressing information (What IP address do I have? Subnet-Mask? Default Gateway? E ...
... Recommended Resources for this Learning Activity No external resources are needed for this lab. All commands and functions are built into the Windows operating system. The commands that will be used are: IPCONFIG – IP addressing information (What IP address do I have? Subnet-Mask? Default Gateway? E ...
The ID/LOC Split - UK Network Operators` Forum
... What does this MEAN? • Put this all together and your computers know roughly what they want. • They rely on the DNS to get them there most of the time • The DNS is the currently accepted way of getting from an IDENTIFIER to a LOCATOR • Or rather, put simply, we rely on the DNS to guide us through t ...
... What does this MEAN? • Put this all together and your computers know roughly what they want. • They rely on the DNS to get them there most of the time • The DNS is the currently accepted way of getting from an IDENTIFIER to a LOCATOR • Or rather, put simply, we rely on the DNS to guide us through t ...
Healthcare Monitoring System Using Wireless Sensor Network
... designs, sensor data are transmitted to remote server through access devices. Tasks like sensor data storage, patients’ health states determination, and notifications are conducted by a central server while gateway only acts as an intermediate device. The response delay includes network delay and ce ...
... designs, sensor data are transmitted to remote server through access devices. Tasks like sensor data storage, patients’ health states determination, and notifications are conducted by a central server while gateway only acts as an intermediate device. The response delay includes network delay and ce ...
UPnP & DLNA
... [1]network solutions", Int. J. Communication Systems, vol. 23, pp. 963–981, 2010. [4]G. Montenegro, N. Kushalnagar, J. Hui, and D. Culler, “Transmission of IPv6 Packets [1]Over IEEE 802.15.4 Networks,” RFC 4944 (Proposed Standard), September 2007. [5] S. Deering and R. Hinden, “Internet Protocol, Ve ...
... [1]network solutions", Int. J. Communication Systems, vol. 23, pp. 963–981, 2010. [4]G. Montenegro, N. Kushalnagar, J. Hui, and D. Culler, “Transmission of IPv6 Packets [1]Over IEEE 802.15.4 Networks,” RFC 4944 (Proposed Standard), September 2007. [5] S. Deering and R. Hinden, “Internet Protocol, Ve ...
Basic Concepts
... Figure 1-24: Cryptographic Protections • Message-by-Message Protections – Encryption to provide confidentiality so that an eavesdropper cannot reach intercepted messages – Electronic signatures provide message-by-message authentication to prevent the insertion of messages by an impostor after initi ...
... Figure 1-24: Cryptographic Protections • Message-by-Message Protections – Encryption to provide confidentiality so that an eavesdropper cannot reach intercepted messages – Electronic signatures provide message-by-message authentication to prevent the insertion of messages by an impostor after initi ...
Slides
... • Quota of 1 Gigabyte • Refill the quota at rate of 1 Gigabyte/month • Maximum speed: unlimited Assign IP: • Quota of 10 Mbytes • Refill the quota at rate of 5 Kilobytes/second • Maximum speed: 20 Kilobytes/sec ...
... • Quota of 1 Gigabyte • Refill the quota at rate of 1 Gigabyte/month • Maximum speed: unlimited Assign IP: • Quota of 10 Mbytes • Refill the quota at rate of 5 Kilobytes/second • Maximum speed: 20 Kilobytes/sec ...
F2329
... reached. When two nodes come in contact with each other, they may exchange the packets and such an opportunity is known as encounter. In case of traditional networks, the network is connected at any given point of time. Therefore there are no partitions in such a network. But the traditional network ...
... reached. When two nodes come in contact with each other, they may exchange the packets and such an opportunity is known as encounter. In case of traditional networks, the network is connected at any given point of time. Therefore there are no partitions in such a network. But the traditional network ...
Summit X670 Series
... ExtremeXOS supports IEEE Audio Video Bridging (AVB) standards to enable reliable real-time audio and video transmissions over Ethernet, for high-definition and timesensitive multimedia streams with assigned Quality of Service (QoS). ExtremeXOS leverages AVB to identify and reserve network resources ...
... ExtremeXOS supports IEEE Audio Video Bridging (AVB) standards to enable reliable real-time audio and video transmissions over Ethernet, for high-definition and timesensitive multimedia streams with assigned Quality of Service (QoS). ExtremeXOS leverages AVB to identify and reserve network resources ...
Introducing Network Design Concepts
... Network users generally do not think in terms of the complexity of the underlying network. They think of the network as a way to access the applications they need, when they need them. ...
... Network users generally do not think in terms of the complexity of the underlying network. They think of the network as a way to access the applications they need, when they need them. ...
Solution - Rab Nawaz Jadoon
... channel in time. Each station is allocated a time slot during which it can send data. Each station transmits its data in is assigned time slot. In TDMA, the bandwidth is just one channel that is timeshared between different stations. CDMA Code-division multiple access (CDMA) was conceived several de ...
... channel in time. Each station is allocated a time slot during which it can send data. Each station transmits its data in is assigned time slot. In TDMA, the bandwidth is just one channel that is timeshared between different stations. CDMA Code-division multiple access (CDMA) was conceived several de ...
Eng. Ashraf presentation for the academy exam
... As with a computer, a router or switch or other Cisco devices cannot function without an operating system “IOS:. Cisco “IOS” Internetwork Operating System is stored in the flash memory but can be over written”. The IOS is copied into RAM to run from there when the device is powered on . This functio ...
... As with a computer, a router or switch or other Cisco devices cannot function without an operating system “IOS:. Cisco “IOS” Internetwork Operating System is stored in the flash memory but can be over written”. The IOS is copied into RAM to run from there when the device is powered on . This functio ...
IP address of a network
... • The original classful address scheme had a number of problems – Problem 1. Too few network addresses for large networks • Class A and Class B addresses are gone – Problem 2. Two-layer hierarchy is not appropriate for large networks with Class A and Class B addresses. • Fix #1: Subnetting ...
... • The original classful address scheme had a number of problems – Problem 1. Too few network addresses for large networks • Class A and Class B addresses are gone – Problem 2. Two-layer hierarchy is not appropriate for large networks with Class A and Class B addresses. • Fix #1: Subnetting ...
Chapter 2 Powerpoint
... – Caching-only server - when it receives a request for information that is not stored in its DNS cache, it will first query the company’s authoritative name server – Name servers within a company might not have access to root servers – A TLD name server might be aware of an intermediate name server ...
... – Caching-only server - when it receives a request for information that is not stored in its DNS cache, it will first query the company’s authoritative name server – Name servers within a company might not have access to root servers – A TLD name server might be aware of an intermediate name server ...
slides - TNC2013
... • Why not just rely on “SNMP” interface stats for this sort of error detection? • not all error conditions show up in SNMP interface statistics • SNMP error statistics can be very noisy • some devices lump different error counters into the same bucket, so it can be very challenging to figure out wha ...
... • Why not just rely on “SNMP” interface stats for this sort of error detection? • not all error conditions show up in SNMP interface statistics • SNMP error statistics can be very noisy • some devices lump different error counters into the same bucket, so it can be very challenging to figure out wha ...
Hash Collision Attack Vectors on the eD2k P2P
... condition' to the attack where the critical chunk (the one containing the colliding block) might be distributed to a host either by the attacker, a host which already finished the download of the file or a host currently downloading the file (which already finished the transfer of the relevant chunk ...
... condition' to the attack where the critical chunk (the one containing the colliding block) might be distributed to a host either by the attacker, a host which already finished the download of the file or a host currently downloading the file (which already finished the transfer of the relevant chunk ...