Exploration_Network_Chapter_6
... Binary patterns representing IPv4 addresses are expressed as dotted decimals by separating each byte of the binary pattern, called an octet, with a dot. It is called an octet because each decimal number represents one byte or 8 bits. ...
... Binary patterns representing IPv4 addresses are expressed as dotted decimals by separating each byte of the binary pattern, called an octet, with a dot. It is called an octet because each decimal number represents one byte or 8 bits. ...
Pros and Cons of TETRA vs. P25 and the Benefits of a
... different networks. EADS, Harris, Tait, Raytheon, and Etherstack also participated in the tests. Demonstrates adherence to standards and capacity of interconnection to 3rdparty P25 networks. ...
... different networks. EADS, Harris, Tait, Raytheon, and Etherstack also participated in the tests. Demonstrates adherence to standards and capacity of interconnection to 3rdparty P25 networks. ...
PDF
... ZigBee network layer provides functionality such as dynamic network formation, addressing, routing, and discovering 1 hop neighbors. The size of the network address is 16 bits, so ZigBee is capable to accept about 65535 devices in a network, and the network address is assigned in a hierarchical tree ...
... ZigBee network layer provides functionality such as dynamic network formation, addressing, routing, and discovering 1 hop neighbors. The size of the network address is 16 bits, so ZigBee is capable to accept about 65535 devices in a network, and the network address is assigned in a hierarchical tree ...
Electron Solution Datasheet
... include uplink ports for Gigabit or fiber connections so the Switches can be deployed at the edge of an existing network or used to provide network connectivity to remote offices or in the case of school campuses remote classrooms. Many of Electron Series PoE Switches can deliver up to 30 watts per ...
... include uplink ports for Gigabit or fiber connections so the Switches can be deployed at the edge of an existing network or used to provide network connectivity to remote offices or in the case of school campuses remote classrooms. Many of Electron Series PoE Switches can deliver up to 30 watts per ...
FS3610481053
... transport and higher-layer protocols and applications, since the IP address of the communicating nodes remains the same at all times. Therefore, the MN (Mobile Node) may easily continue communication with other nodes after moving to a new link. At least in theory. There are cases in which it is not ...
... transport and higher-layer protocols and applications, since the IP address of the communicating nodes remains the same at all times. Therefore, the MN (Mobile Node) may easily continue communication with other nodes after moving to a new link. At least in theory. There are cases in which it is not ...
Ethernet frames - La Salle University
... small control packet indicating it will transmit a larger packet. • The Computer 2 issues a reply packet which is read by all computers in its vicinity (including Computer 3) that it expects to receive a message from Computer 1. Computer 3 holds off transmitting its signal. • This is Collision Avoid ...
... small control packet indicating it will transmit a larger packet. • The Computer 2 issues a reply packet which is read by all computers in its vicinity (including Computer 3) that it expects to receive a message from Computer 1. Computer 3 holds off transmitting its signal. • This is Collision Avoid ...
pptx - University of Cambridge Computer Laboratory
... Addressing (at a conceptual level) • Assume all hosts have unique IDs • No particular structure to those IDs • Later in topic I will talk about real IP addressing • Do I route on location or identifier? • If a host moves, should its address change? – If not, how can you build scalable Internet? – I ...
... Addressing (at a conceptual level) • Assume all hosts have unique IDs • No particular structure to those IDs • Later in topic I will talk about real IP addressing • Do I route on location or identifier? • If a host moves, should its address change? – If not, how can you build scalable Internet? – I ...
OSI Seven Layers Model Explained with Examples DOCX Format
... automatically to hosts. Telnet— used to connect remote devices. HTTP (Hypertext Transfer Protocol) — Used to browse web pages. FTP (File Transfer Protocol) — Used to reliably sends/retrieves files. SMTP (Simple Mail Transfer Protocol) — Used to sends email. POP3 (Post Office Protocol v.3) — Used to ...
... automatically to hosts. Telnet— used to connect remote devices. HTTP (Hypertext Transfer Protocol) — Used to browse web pages. FTP (File Transfer Protocol) — Used to reliably sends/retrieves files. SMTP (Simple Mail Transfer Protocol) — Used to sends email. POP3 (Post Office Protocol v.3) — Used to ...
Building a Real
... • ISDN-based VTC is being replaced by highspeed Internet connections Copyright © 2015 by McGraw-Hill Education. All rights reserved. ...
... • ISDN-based VTC is being replaced by highspeed Internet connections Copyright © 2015 by McGraw-Hill Education. All rights reserved. ...
doc - Notifier (UK)
... Using standard RS-232 ports the system shall connect to and interpret status change data transmitted from the ports and provide graphic annunciation, control, history logging and reporting as specified herein. A supervised interface to NOTIFIER fire alarm control panels shall be made available. The ...
... Using standard RS-232 ports the system shall connect to and interpret status change data transmitted from the ports and provide graphic annunciation, control, history logging and reporting as specified herein. A supervised interface to NOTIFIER fire alarm control panels shall be made available. The ...
Multicast - s3.amazonaws.com
... Chapter 4 quiz 1. What is the 32-bit binary equivalent of the IP address 128.180.5.114? 2. Consider a router with three interfaces. Suppose all three interfaces use class C addresses. Will the IP address of the three interfaces necessarily have the same first eight bits? 3. Suppose an application g ...
... Chapter 4 quiz 1. What is the 32-bit binary equivalent of the IP address 128.180.5.114? 2. Consider a router with three interfaces. Suppose all three interfaces use class C addresses. Will the IP address of the three interfaces necessarily have the same first eight bits? 3. Suppose an application g ...
Module 1 IP/MAC Addresses and TCP/IP Suite
... programs. Consider two application programs that are developed to communicate over the network. To test these programs without running them on two different hosts, it is possible to run the two application programs on the same host and use the loopback address to communicate. When data from one appl ...
... programs. Consider two application programs that are developed to communicate over the network. To test these programs without running them on two different hosts, it is possible to run the two application programs on the same host and use the loopback address to communicate. When data from one appl ...
Avaya Virtual Services Platform 8404
... with integrated IP Multicast, enables Fabric Connect to deliver the Industry’s premium solution for simplified, scalable, and resilient IP Multicast-based applications. The Edge-only provisioning model delivers significant advances in how the network interacts with VM mobility. Layer 2 VLANs can be ...
... with integrated IP Multicast, enables Fabric Connect to deliver the Industry’s premium solution for simplified, scalable, and resilient IP Multicast-based applications. The Edge-only provisioning model delivers significant advances in how the network interacts with VM mobility. Layer 2 VLANs can be ...
Why MPLS multicast?
... No support for bandwidth reservation in protocol but can be achieved using network planning & Diffserv. ...
... No support for bandwidth reservation in protocol but can be achieved using network planning & Diffserv. ...
Cray XC Series Network
... connected with 18 × 108-port switches to construct systems with up to 1,944 nodes. However, if the system has 2,000 nodes then it requires 144 or 216 port switches to connect the chassis together. Many of the network ports will go unused. Upgrading a system from 1,500 to 2,000 nodes would require th ...
... connected with 18 × 108-port switches to construct systems with up to 1,944 nodes. However, if the system has 2,000 nodes then it requires 144 or 216 port switches to connect the chassis together. Many of the network ports will go unused. Upgrading a system from 1,500 to 2,000 nodes would require th ...
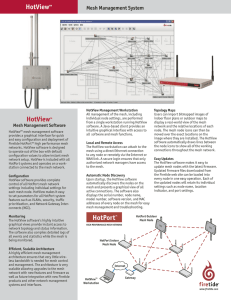
HotViewTM HotView™
... Add your own bitmapped background images of street maps, floor plans, or any other networking environments to provide a real world layout of the mesh network showing the relative location of each node. Graphical Device Management The main HotView screen provides a graphical view of the mesh network, ...
... Add your own bitmapped background images of street maps, floor plans, or any other networking environments to provide a real world layout of the mesh network showing the relative location of each node. Graphical Device Management The main HotView screen provides a graphical view of the mesh network, ...
Sockets
... ◦ To an application, a socket is a file descriptor that lets the application read/write from/to the network. In Unix all I/O devices, including networks, are modeled as files. ...
... ◦ To an application, a socket is a file descriptor that lets the application read/write from/to the network. In Unix all I/O devices, including networks, are modeled as files. ...
pptx - Cambridge Computer Lab
... Addressing (at a conceptual level) • Assume all hosts have unique IDs • No particular structure to those IDs • Later in topic I will talk about real IP addressing • Do I route on location or identifier? • If a host moves, should its address change? – If not, how can you build scalable Internet? – I ...
... Addressing (at a conceptual level) • Assume all hosts have unique IDs • No particular structure to those IDs • Later in topic I will talk about real IP addressing • Do I route on location or identifier? • If a host moves, should its address change? – If not, how can you build scalable Internet? – I ...
to a detailed description of the
... certified Installers no company really matches our standard. We insist on: • Quality – “Do it right the first time” • Cable for the future • On the importance of building cable networks that support high connectivity and advanced business applications – VoIP, streaming IP video and Audio, IP video c ...
... certified Installers no company really matches our standard. We insist on: • Quality – “Do it right the first time” • Cable for the future • On the importance of building cable networks that support high connectivity and advanced business applications – VoIP, streaming IP video and Audio, IP video c ...
Carrier Ethernet: The next generation network and service
... SDH ADMs / Transport replaced by Ethernet Transport Shortest possible Ethernet over E1 (PDH) loops CLE at customer premise enables converged Ethernet and IP services Local switching of locally attached subscribers reduces backhaul bandwidth © Copyright 2008 Turin Networks, Inc. All Rights Reserved ...
... SDH ADMs / Transport replaced by Ethernet Transport Shortest possible Ethernet over E1 (PDH) loops CLE at customer premise enables converged Ethernet and IP services Local switching of locally attached subscribers reduces backhaul bandwidth © Copyright 2008 Turin Networks, Inc. All Rights Reserved ...
Generalized versus non-generalized neural network model for multi
... combine representations of the parameters. While such models ignore the spatially distributed, time-varying and stochastic properties of the river flow process, they attempt to incorporate realistic representations of the major nonlinearity inherent in the river flow and climatic parameters relation ...
... combine representations of the parameters. While such models ignore the spatially distributed, time-varying and stochastic properties of the river flow process, they attempt to incorporate realistic representations of the major nonlinearity inherent in the river flow and climatic parameters relation ...
09-IP_pkts
... • Packets are THROWN AWAY!! This is where packet loss comes from Lecture 9: 2-8-05 ...
... • Packets are THROWN AWAY!! This is where packet loss comes from Lecture 9: 2-8-05 ...