Bluetooth-an Enabler for Personal Area Networking Presentation
... than one piconet. These inter-piconet nodes might have a slave role in numerous piconets but can have the master role in only one of them. Irrespective of the roles, the inter-piconet node must schedule its presence in all the piconets it is a member of, hence, an inter-piconet scheduling (IPS) algo ...
... than one piconet. These inter-piconet nodes might have a slave role in numerous piconets but can have the master role in only one of them. Irrespective of the roles, the inter-piconet node must schedule its presence in all the piconets it is a member of, hence, an inter-piconet scheduling (IPS) algo ...
Service Electric Cablevision Broadband Internet Service
... electronic communications (e.g., e-mail, newsgroup postings, private electronic conversations, etc.) as assured by the United States Post Office. Customers should assume that other persons may be able to view any and all communications passed on or through SECV’s systems or systems directly accessib ...
... electronic communications (e.g., e-mail, newsgroup postings, private electronic conversations, etc.) as assured by the United States Post Office. Customers should assume that other persons may be able to view any and all communications passed on or through SECV’s systems or systems directly accessib ...
WIRELESS SENSOR NETWORKS: SECURITY ISSUES AND
... ensure that a particular technology will work. Unfortunately, the support is directly related to the lifetime of the company. The company goes out of business or changes direction in terms of technology and the supports will have an end of life. The following are a couple of examples of proprietary ...
... ensure that a particular technology will work. Unfortunately, the support is directly related to the lifetime of the company. The company goes out of business or changes direction in terms of technology and the supports will have an end of life. The following are a couple of examples of proprietary ...
Parallel Implementation of Back-Propagation
... tuned parallel programs can be easily scaled to large configurations because additional workstations can always be added to NOW. The NOW also offer much greater ...
... tuned parallel programs can be easily scaled to large configurations because additional workstations can always be added to NOW. The NOW also offer much greater ...
- TERENA
... – we ensure that the network can handle max allowed traffic from all clients at once, even in worst-case scenario re: links failing • Assigning the amount of allowable PIP traffic to each link is done via a complex algorithm.. but this allows us to – decide whether to admit a PIP request based solel ...
... – we ensure that the network can handle max allowed traffic from all clients at once, even in worst-case scenario re: links failing • Assigning the amount of allowable PIP traffic to each link is done via a complex algorithm.. but this allows us to – decide whether to admit a PIP request based solel ...
PPT_ch06
... following: reflection, diffraction, or scattering • Personal area networks (PANs) rarely exceed a few meters and usually only contain a few personal devices • Bluetooth technology unites mobile devices with PCs under a single communications standard Network+ Guide to Networks, 7th Edition ...
... following: reflection, diffraction, or scattering • Personal area networks (PANs) rarely exceed a few meters and usually only contain a few personal devices • Bluetooth technology unites mobile devices with PCs under a single communications standard Network+ Guide to Networks, 7th Edition ...
EVOLUTION OF COMMUNICATION - SMK Seksyen 5, Wangsa Maju
... Once we have got the necessary hardware set up for a network, we will need to have suitable software on the network computers that would be able to provide some basic functions, such as connecting to other computers on the network, sharing resources and files and providing for network security for u ...
... Once we have got the necessary hardware set up for a network, we will need to have suitable software on the network computers that would be able to provide some basic functions, such as connecting to other computers on the network, sharing resources and files and providing for network security for u ...
Paper
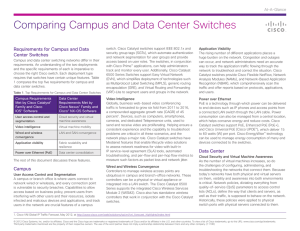
... withstand planned and unplanned downtime. The Cisco Nexus portfolio offers multidimensional scalability for the data center network in switch performance, system scalability, and geographic span, allowing your data center to support more servers and more applications when you need them. Through supp ...
... withstand planned and unplanned downtime. The Cisco Nexus portfolio offers multidimensional scalability for the data center network in switch performance, system scalability, and geographic span, allowing your data center to support more servers and more applications when you need them. Through supp ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... communication industry is larger and growing complex. Different modes as mobile, wired, wireless, adhoc, supports growth of the communication industry but with certain limits. Mobility plays a vital role in wireless networks, where it is necessary to satisfy the requirements of the modern world. It ...
... communication industry is larger and growing complex. Different modes as mobile, wired, wireless, adhoc, supports growth of the communication industry but with certain limits. Mobility plays a vital role in wireless networks, where it is necessary to satisfy the requirements of the modern world. It ...
Cloud Computing and Security
... Logical Separation: Implemented through the use of: • IEEE 802.1Q VLAN tagging of Ethernet frames; • VLAN-aware TCAMs for Ethernet switching. The IEEE 802.1Q standard establishes the common practice of encapsulating multiple logical Ethernet networks on shared infrastructure. Originally pioneered ...
... Logical Separation: Implemented through the use of: • IEEE 802.1Q VLAN tagging of Ethernet frames; • VLAN-aware TCAMs for Ethernet switching. The IEEE 802.1Q standard establishes the common practice of encapsulating multiple logical Ethernet networks on shared infrastructure. Originally pioneered ...
Ch. 3 - Application Layer Functionality and Protocols
... Developed in the early 1970’s – among the oldest of the application layer protocols and services in the TCP/IP protocol suite. Allows users to emulate text-based terminal devices over the network using software. A connection is known as a ‘virtual terminal (vty)’ session. Can be run from the ...
... Developed in the early 1970’s – among the oldest of the application layer protocols and services in the TCP/IP protocol suite. Allows users to emulate text-based terminal devices over the network using software. A connection is known as a ‘virtual terminal (vty)’ session. Can be run from the ...
ERouting Final Exam
... Refer to the exhibit. Routers R1 and R3 use different routing protocols with default administrative distance values. All devices are properly configured and the destination network is advertised by both protocols. Which path will be used to transmit the data packets between PC1 and PC2? The packets ...
... Refer to the exhibit. Routers R1 and R3 use different routing protocols with default administrative distance values. All devices are properly configured and the destination network is advertised by both protocols. Which path will be used to transmit the data packets between PC1 and PC2? The packets ...
cs591report
... resolving proxy selection for multipaths within its region. For example if a computer in C would like to communicate with a computer in E (as shown in figure 3), the lower level coordinators would check their cache (perhaps this has been solved recently). If the cache is not valid, the coordinators ...
... resolving proxy selection for multipaths within its region. For example if a computer in C would like to communicate with a computer in E (as shown in figure 3), the lower level coordinators would check their cache (perhaps this has been solved recently). If the cache is not valid, the coordinators ...
Application Layer Functionality and Protocols
... Developed in the early 1970’s – among the oldest of the application layer protocols and services in the TCP/IP protocol suite. Allows users to emulate text-based terminal devices over the network using software. A connection is known as a ‘virtual terminal (vty)’ session. Can be run from the ...
... Developed in the early 1970’s – among the oldest of the application layer protocols and services in the TCP/IP protocol suite. Allows users to emulate text-based terminal devices over the network using software. A connection is known as a ‘virtual terminal (vty)’ session. Can be run from the ...
PDF
... The wide range of security features on the IE 2000U protects mission-critical traffic, prevents unauthorized access, and maintains uninterrupted operation. The IE 2000U protects operational and nonoperational data by focusing on securing connectivity, defending against network threats, and providing ...
... The wide range of security features on the IE 2000U protects mission-critical traffic, prevents unauthorized access, and maintains uninterrupted operation. The IE 2000U protects operational and nonoperational data by focusing on securing connectivity, defending against network threats, and providing ...
Classification of Artificial Neural Networks
... The development of artificial neuron based on the understanding of the biological neural structure and learning mechanisms for required applications. This can be summarized as (a) development of neural models based on the understanding of biological neurons, (b) models of synaptic connections and st ...
... The development of artificial neuron based on the understanding of the biological neural structure and learning mechanisms for required applications. This can be summarized as (a) development of neural models based on the understanding of biological neurons, (b) models of synaptic connections and st ...
Ethernet Passive Optical Network (EPON)
... received by the OLT from all the ONUs becomes the same. ...
... received by the OLT from all the ONUs becomes the same. ...
A Model of Web Server Performance
... As is often the case in computer systems, Web servers typically process many simultaneous jobs (i.e., file requests), each of which contends for various shared resources: processor time, file access, and network bandwidth. Since only one job may use a resource at any time, all other jobs must wait i ...
... As is often the case in computer systems, Web servers typically process many simultaneous jobs (i.e., file requests), each of which contends for various shared resources: processor time, file access, and network bandwidth. Since only one job may use a resource at any time, all other jobs must wait i ...
IP_Suite - Virginia Tech
... •Network address: an address that defines the network itself, e.g., 123.0.0.0 (class A), 141.14.0.0 (class B), and 221.45.71.0 (class C) • Packets are routed to an organization based on the network address •To find the network address apply a netmask (default mask) AND netmask with address A net ...
... •Network address: an address that defines the network itself, e.g., 123.0.0.0 (class A), 141.14.0.0 (class B), and 221.45.71.0 (class C) • Packets are routed to an organization based on the network address •To find the network address apply a netmask (default mask) AND netmask with address A net ...
Hijacking Label Switched Networks in the Cloud
... Monitor for New Unexpected Route Advertisements – Know Your Network! Utilize Encryption over MPLS VPN Links; SP PE-PE IPSEC Whitelist the Network Trust Relationships including Routing Protocols Whitelist Trusted Information Flows in Monitoring Utilize Separate VRF for In-band Management Dedicated Ou ...
... Monitor for New Unexpected Route Advertisements – Know Your Network! Utilize Encryption over MPLS VPN Links; SP PE-PE IPSEC Whitelist the Network Trust Relationships including Routing Protocols Whitelist Trusted Information Flows in Monitoring Utilize Separate VRF for In-band Management Dedicated Ou ...
Information for Work-in-Progress version:This document is subject to
... such environments. The whitepaper also provides the analysis on applicability of the existing DMTF specifications, such as the OVF, CIMI, and NPP XML Schema. We achieve this by analyzing the gaps between the currently available OVF, CIMI, and NPP capabilities and the features and functions required ...
... such environments. The whitepaper also provides the analysis on applicability of the existing DMTF specifications, such as the OVF, CIMI, and NPP XML Schema. We achieve this by analyzing the gaps between the currently available OVF, CIMI, and NPP capabilities and the features and functions required ...
American Messaging Services Network Interface Guide
... Firewall and TCP/IP Ports..........................................................................................................................................................7 Benefits Over SNPP .................................................................................................... ...
... Firewall and TCP/IP Ports..........................................................................................................................................................7 Benefits Over SNPP .................................................................................................... ...
Ethernet Passive Optical Networks
... of copper telephone wires or coaxial cable television (CATV) cables. In metropolitan areas, where there is a high concentration of business customers, the access network often includes high-capacity synchronous optical network (SONET) rings, optical T3 lines, and copper-based T1s. Typically, only la ...
... of copper telephone wires or coaxial cable television (CATV) cables. In metropolitan areas, where there is a high concentration of business customers, the access network often includes high-capacity synchronous optical network (SONET) rings, optical T3 lines, and copper-based T1s. Typically, only la ...