IOSR Journal of Computer Engineering (IOSR-JCE)
... Objective of the project The multicast group can be identified with the class D IP address so that the members can enter or leave the group with the management of Internet group management protocol. The trusted model gives a scope between the entities in a multicast security system. For secure group ...
... Objective of the project The multicast group can be identified with the class D IP address so that the members can enter or leave the group with the management of Internet group management protocol. The trusted model gives a scope between the entities in a multicast security system. For secure group ...
Governance Guidance
... Does management know where the enterprise is most vulnerable within the IT infrastructure? ...
... Does management know where the enterprise is most vulnerable within the IT infrastructure? ...
Packet-Hiding Methods for Preventing Selective Jamming Attacks
... storage bounded, although he can be far superior to normal nodes. In particular, he can be equipped with special purpose hardware for performing cryptanalysis or any other required computation. Solving well-known hard cryptographic problems is assumed to be time-consuming. For the purposes of analys ...
... storage bounded, although he can be far superior to normal nodes. In particular, he can be equipped with special purpose hardware for performing cryptanalysis or any other required computation. Solving well-known hard cryptographic problems is assumed to be time-consuming. For the purposes of analys ...
The Broadband Services Router 64000 (BSR 64000) provides
... CMTS functions and it scales economically to meet ever-increasing subscriber demands and the introduction of new services. The BSR 64000 design is based on centralized routing table calculations and distributed forwarding, and it provides the benefits of simple configuration (single router appearanc ...
... CMTS functions and it scales economically to meet ever-increasing subscriber demands and the introduction of new services. The BSR 64000 design is based on centralized routing table calculations and distributed forwarding, and it provides the benefits of simple configuration (single router appearanc ...
SurveyRoutingADHOC - start [kondor.etf.rs]
... the most widely used routing algorithms are such as distant vector or link state ...
... the most widely used routing algorithms are such as distant vector or link state ...
HotView Pro™ Mesh Management Software
... are then “dragged and dropped” to their real-world physical location. The resulting display shows the actual layout of the mesh topology, complete with lines indicating the many links or hops (wireless or wired) among all nodes. This powerful mesh-wide view is frequently used when adding new nodes o ...
... are then “dragged and dropped” to their real-world physical location. The resulting display shows the actual layout of the mesh topology, complete with lines indicating the many links or hops (wireless or wired) among all nodes. This powerful mesh-wide view is frequently used when adding new nodes o ...
TCP/IP - Austin Community College
... • Implements network policies, and provides many networking services – Such as Network Address Translation (NAT), firewall protection, and quality of service (QoS) ...
... • Implements network policies, and provides many networking services – Such as Network Address Translation (NAT), firewall protection, and quality of service (QoS) ...
Document
... Open Shortest Path First (OSPF) is a nonproprietary link-state routing protocol. • It is a link-state routing protocol. • Open standard routing protocol described in RFC 2328. • Uses the SPF algorithm to calculate the lowest cost to a destination. • Routing updates are flooded as topology changes oc ...
... Open Shortest Path First (OSPF) is a nonproprietary link-state routing protocol. • It is a link-state routing protocol. • Open standard routing protocol described in RFC 2328. • Uses the SPF algorithm to calculate the lowest cost to a destination. • Routing updates are flooded as topology changes oc ...
Corinex AV200 Powerline Ethernet Adapter
... of this EULA, do not download, install, copy or use the Software. 1. Licence Grant. CORINEX grants to you a personal, non-transferable and non-exclusive right to use the copy of the Software provided with this EULA. You agree you will not copy the Software except as necessary to use it on a single h ...
... of this EULA, do not download, install, copy or use the Software. 1. Licence Grant. CORINEX grants to you a personal, non-transferable and non-exclusive right to use the copy of the Software provided with this EULA. You agree you will not copy the Software except as necessary to use it on a single h ...
Document
... Management systems can also send configuration updates or controlling requests through the SET protocol operation to actively manage a system ...
... Management systems can also send configuration updates or controlling requests through the SET protocol operation to actively manage a system ...
Data encapsulation
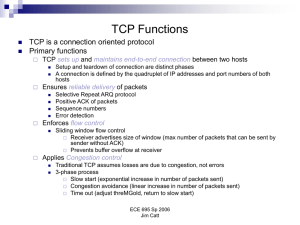
... recipient to verify the receipt of a packet or packets. A packet is the fundamental unit of data transmitted over a LAN. Segmentation. This is the division of a lengthy data stream into segments sufficiently small for transmission over the network inside packets. Flow control. This is the generation ...
... recipient to verify the receipt of a packet or packets. A packet is the fundamental unit of data transmitted over a LAN. Segmentation. This is the division of a lengthy data stream into segments sufficiently small for transmission over the network inside packets. Flow control. This is the generation ...
Data Center Monitoring Using Nagios Matti Taina
... for alerting the technicians of a problem, nothing will tell whether that single machine and its monitoring software is actually operational. For this reason it is imperative to have at least two independent machines dedicated for alerting staff of a problem. In addition to just being separated into ...
... for alerting the technicians of a problem, nothing will tell whether that single machine and its monitoring software is actually operational. For this reason it is imperative to have at least two independent machines dedicated for alerting staff of a problem. In addition to just being separated into ...
SoNIC: Precise Realtime Software Access and Control of Wired Networks
... do not provide nor allow an interface for users to access the PHY in any case. Consequently, operating systems cannot access the PHY either. Software access to the PHY is only enabled via special tools such as BiFocals [15] which uses physics equipment, including a laser and an oscilloscope. As a ne ...
... do not provide nor allow an interface for users to access the PHY in any case. Consequently, operating systems cannot access the PHY either. Software access to the PHY is only enabled via special tools such as BiFocals [15] which uses physics equipment, including a laser and an oscilloscope. As a ne ...
for a of Evolution
... efforts, the performance improvement in the new implementations, the experiences from our research, and finally the effects on the transaction processing in the context of an experimental distributed database system [8R89]. We observed that the address space paradigm can provide a natural platform f ...
... efforts, the performance improvement in the new implementations, the experiences from our research, and finally the effects on the transaction processing in the context of an experimental distributed database system [8R89]. We observed that the address space paradigm can provide a natural platform f ...
Taxonomy of communication networks
... Convergence after a single event can take up to tens of minutes ...
... Convergence after a single event can take up to tens of minutes ...
Document
... • Advice: use Cat 5, Cat 5e or Cat6 UTP (unshielded twisted pair) • Category 7 and higher marketing hype – Not official IEEE spec ...
... • Advice: use Cat 5, Cat 5e or Cat6 UTP (unshielded twisted pair) • Category 7 and higher marketing hype – Not official IEEE spec ...
Factors that influence TCP performance
... The MN to MG segment is basically a single hop – efficiencies can be obtained from this context ...
... The MN to MG segment is basically a single hop – efficiencies can be obtained from this context ...
Chapter 4: Network Layer
... routers establish virtual connection routers get involved network vs transport layer connection service: network: between two hosts (may also involve intervening routers in case of VCs) transport: between two processes ...
... routers establish virtual connection routers get involved network vs transport layer connection service: network: between two hosts (may also involve intervening routers in case of VCs) transport: between two processes ...
Linux+ Guide to Linux Certification
... be obtained from a router using ICMPv6, from a DHCP server, or autoconfigured by the system The /etc/sysconfig/network-scripts directory contains the configuration for NIC and PPP ...
... be obtained from a router using ICMPv6, from a DHCP server, or autoconfigured by the system The /etc/sysconfig/network-scripts directory contains the configuration for NIC and PPP ...
On-Demand Monitoring of Protocol
... IntServ/RSVP is only used at the edge instead and DiffServ in the core network. Per-flow state is pushed to the edge in order to avoid scalability and complexity problems associated with the IntServ/RSVP model. The DiffServ architecture – is tailored only to a set of "user plane" mechanisms of provi ...
... IntServ/RSVP is only used at the edge instead and DiffServ in the core network. Per-flow state is pushed to the edge in order to avoid scalability and complexity problems associated with the IntServ/RSVP model. The DiffServ architecture – is tailored only to a set of "user plane" mechanisms of provi ...
Memphis - Andrew.cmu.edu - Carnegie Mellon University
... Similar to the DEW line* – early indication that an attack may be coming facilitated by sensing the entire network Analysis for I&W • Hacking involves reverse engineering: the attacker must probe, examine and determine the “right” approach • Frequently precursors to attacks are buried in the “noise” ...
... Similar to the DEW line* – early indication that an attack may be coming facilitated by sensing the entire network Analysis for I&W • Hacking involves reverse engineering: the attacker must probe, examine and determine the “right” approach • Frequently precursors to attacks are buried in the “noise” ...
Improving Gnutella - Distributed Computing Group
... • The Ultra peer system has been found effective for this purpose. It is a scheme to have a hierarchical Gnutella network by categorizing the nodes on the network as leaves and ultra peers. A leaf keeps only a small number of connections open, and that is to ultra peers. An ultra peer acts as a prox ...
... • The Ultra peer system has been found effective for this purpose. It is a scheme to have a hierarchical Gnutella network by categorizing the nodes on the network as leaves and ultra peers. A leaf keeps only a small number of connections open, and that is to ultra peers. An ultra peer acts as a prox ...
APAN201202_FlowSpace_yamanaka
... • Diverse requirements to networks for application services – Network resources for application-specific performance – Functions of in-network processing ...
... • Diverse requirements to networks for application services – Network resources for application-specific performance – Functions of in-network processing ...




![SurveyRoutingADHOC - start [kondor.etf.rs]](http://s1.studyres.com/store/data/002358361_1-1eb8409683010799a87544900454d765-300x300.png)