ppt
... – Packet in reverse direction do not pass through load balancer – Greater scalability, particularly for traffic with assymmetric bandwidth (e.g., HTTP GETs) ...
... – Packet in reverse direction do not pass through load balancer – Greater scalability, particularly for traffic with assymmetric bandwidth (e.g., HTTP GETs) ...
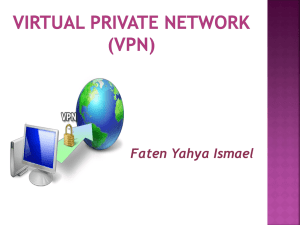
VPN: Virtual Private Network
... To establish security association (SA), the VPN( client & server) use the Internet Key Exchange IKE protocol to exchange computer certificates . Computer certificate ...
... To establish security association (SA), the VPN( client & server) use the Internet Key Exchange IKE protocol to exchange computer certificates . Computer certificate ...
Advanced Malware Detection
... Eliminate the distraction of False Positive results with AMD. This ...
... Eliminate the distraction of False Positive results with AMD. This ...
www.siskiyous.edu
... • Allow network users to connect to machines outside the network • Remote user – Computer user on different network or in different geographical location from LAN’s server ...
... • Allow network users to connect to machines outside the network • Remote user – Computer user on different network or in different geographical location from LAN’s server ...
Distance Vector Multicast Routing Protocol
... routing exchanges ( using DVRP) • Reverse Path Multicasting – Initially, assume that every host on the network is part of the Multicast group (TRPB) – Per Source-Group Multicast delivery tree – Reverse Path Forwarding check – Poison Reverse • Determine downstream interfaces to forward the packet on ...
... routing exchanges ( using DVRP) • Reverse Path Multicasting – Initially, assume that every host on the network is part of the Multicast group (TRPB) – Per Source-Group Multicast delivery tree – Reverse Path Forwarding check – Poison Reverse • Determine downstream interfaces to forward the packet on ...
FILE NO: TCT/MCA… - RGPV Question Paper
... Ethernet Cables 1. While the power is off on the DSL modem and wireless router, plug an Ethernet cable into the DSL modem and connect the other end of the cable into the "Internet" port of the wireless router. Take a separate Ethernet cable and plug it into port "1" of the router, then plug the ot ...
... Ethernet Cables 1. While the power is off on the DSL modem and wireless router, plug an Ethernet cable into the DSL modem and connect the other end of the cable into the "Internet" port of the wireless router. Take a separate Ethernet cable and plug it into port "1" of the router, then plug the ot ...
network terminology
... two or more physical routers can seamlessly backup each other in case of failover ...
... two or more physical routers can seamlessly backup each other in case of failover ...
The IP, TCP, UDP protocols - FSU Computer Science
... TCP SYN-flood attack • An adversarial client can spoof many IP addresses and send large numbers of SYN-packets, requesting new TCP connections to the server. • The server responds with SYN-ACK packets, and keeps record of the requested connections (in state SYN-received), waiting on each a period (t ...
... TCP SYN-flood attack • An adversarial client can spoof many IP addresses and send large numbers of SYN-packets, requesting new TCP connections to the server. • The server responds with SYN-ACK packets, and keeps record of the requested connections (in state SYN-received), waiting on each a period (t ...
PowerPoint Presentation - The IP, TCP, UDP protocols
... TCP SYN-flood attack • An adversarial client can spoof many IP addresses and send large numbers of SYN-packets, requesting new TCP connections to the server. • The server responds with SYN-ACK packets, and keeps record of the requested connections (in state SYN-received), waiting on each a period ( ...
... TCP SYN-flood attack • An adversarial client can spoof many IP addresses and send large numbers of SYN-packets, requesting new TCP connections to the server. • The server responds with SYN-ACK packets, and keeps record of the requested connections (in state SYN-received), waiting on each a period ( ...
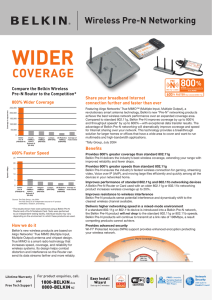
coverage
... Featuring Airgo Networks’ True MIMO™ (Multiple Input, Multiple Output), a revolutionary smart antenna technology, Belkin’s new “Pre-N” networking products achieve the best wireless network performance over an expanded coverage area. Compared to standard 802.11g, Belkin Pre-N improves coverage by up ...
... Featuring Airgo Networks’ True MIMO™ (Multiple Input, Multiple Output), a revolutionary smart antenna technology, Belkin’s new “Pre-N” networking products achieve the best wireless network performance over an expanded coverage area. Compared to standard 802.11g, Belkin Pre-N improves coverage by up ...
Implementation Of Voice Over Internet Protocol (VoIP) in Air Traffic
... These are ported over the data-centric IP infrastructure by digitizing, compressing, and converting voice and video into packets. These packets are transmitted over the network, along with the data and signalling packets. Signalling protocols are used to set up and tear down calls, and convey inform ...
... These are ported over the data-centric IP infrastructure by digitizing, compressing, and converting voice and video into packets. These packets are transmitted over the network, along with the data and signalling packets. Signalling protocols are used to set up and tear down calls, and convey inform ...
Aalborg Universitet Hybrid SDN Architecture for Resource Consolidation in MPLS Networks
... communicated by a separate control plane and would function as the “fabric controller”. This may lead to a more efficient packet switching within the core. The approach used is partially based on the model described in [12]. In order to benefit from the traffic forwarding capabilities of the MPLS te ...
... communicated by a separate control plane and would function as the “fabric controller”. This may lead to a more efficient packet switching within the core. The approach used is partially based on the model described in [12]. In order to benefit from the traffic forwarding capabilities of the MPLS te ...
ACNS PowerPoint - Universal Studios
... – “Penalty-Box”: Traffic-shapers already support very flexible rules such as: (i) block infringer’s P2P traffic for X hours; (ii) block outgoing P2P traffic; (iii) assign lower priority and bandwidth limit to infringer; etc. – Resistant to Encryption: Only need to identify the type of traffic, not t ...
... – “Penalty-Box”: Traffic-shapers already support very flexible rules such as: (i) block infringer’s P2P traffic for X hours; (ii) block outgoing P2P traffic; (iii) assign lower priority and bandwidth limit to infringer; etc. – Resistant to Encryption: Only need to identify the type of traffic, not t ...
Insight into the Gtalk Protocol
... data via Real-Time Transport Protocol (RTP) [11]. SIP is an application layer text based protocol for establishing multimedia session and adapts client-server architecture. Several major companies have chosen SIP for signaling VoIP traffic such as Microsoft and Yahoo. SIP message can be transmitted ...
... data via Real-Time Transport Protocol (RTP) [11]. SIP is an application layer text based protocol for establishing multimedia session and adapts client-server architecture. Several major companies have chosen SIP for signaling VoIP traffic such as Microsoft and Yahoo. SIP message can be transmitted ...
Robeks Juices up its WAN with IRG
... With new stores opening at a rapid rate and a new POS system being implemented, it was important to Robeks that they had a single company managing the broadband initiative. Previously, each store placed its own broadband request through the local phone company; using this approach Robeks Corporate h ...
... With new stores opening at a rapid rate and a new POS system being implemented, it was important to Robeks that they had a single company managing the broadband initiative. Previously, each store placed its own broadband request through the local phone company; using this approach Robeks Corporate h ...
Slides - Indico
... – Leased lines between routers pass through SONET circuit switches – Thus, packet and circuit switches – Leased-lines: CO mode – CO and CL modes – Some switches could be all-optical (metro rings) – Thus all-optical and electronic ...
... – Leased lines between routers pass through SONET circuit switches – Thus, packet and circuit switches – Leased-lines: CO mode – CO and CL modes – Some switches could be all-optical (metro rings) – Thus all-optical and electronic ...
Traffic Management Policy for Landlord Services
... Is traffic management used to manage congestion in particular locations? NO If so how? The same practices are applied during peak hours * This KFI gives an overview of typical traffic management practices undertaken on this product; it does not cover circumstances where exceptional external events m ...
... Is traffic management used to manage congestion in particular locations? NO If so how? The same practices are applied during peak hours * This KFI gives an overview of typical traffic management practices undertaken on this product; it does not cover circumstances where exceptional external events m ...
P.702 - How it works
... Do not consider ITU / ATM forum standards, thus ill suited to broader telco environments • Until MPLS is ratified by the IETF, they are proprietary solutions • Little opportunity for system administrator to control user access • Rely on point-point soft-state connections throughout a network, and di ...
... Do not consider ITU / ATM forum standards, thus ill suited to broader telco environments • Until MPLS is ratified by the IETF, they are proprietary solutions • Little opportunity for system administrator to control user access • Rely on point-point soft-state connections throughout a network, and di ...
Chapter
... • fiber-optic cabling is used all the way from the ISP to your home • Other providers can provide • fiber-optic cabling up to your neighborhood • then use coaxial cable (similar to that used in cable Internet connections) for the last leg of the connection to your business or residence • Upstream and ...
... • fiber-optic cabling is used all the way from the ISP to your home • Other providers can provide • fiber-optic cabling up to your neighborhood • then use coaxial cable (similar to that used in cable Internet connections) for the last leg of the connection to your business or residence • Upstream and ...
Computer Networks Sample Questions
... a. It requires centralized and dedicated server. b. It requires at least one administrator to provide centralized resources. c. it provide extensive user and resource security. d. it provides each user the ability to to manage his own shared resources. 10. Your company has several computers, which s ...
... a. It requires centralized and dedicated server. b. It requires at least one administrator to provide centralized resources. c. it provide extensive user and resource security. d. it provides each user the ability to to manage his own shared resources. 10. Your company has several computers, which s ...