E10 Quick Reference
... appears on Setup window even if the IP address is from remote network range. l A user on the local network may access WebEye, when WebEye is assigned a pro per IP address of the local network, though if gateway address, broadcast address and network mask are not assigned properly. However remote use ...
... appears on Setup window even if the IP address is from remote network range. l A user on the local network may access WebEye, when WebEye is assigned a pro per IP address of the local network, though if gateway address, broadcast address and network mask are not assigned properly. However remote use ...
FTTH
... • What is FTTC? • Fiber to the Curb (FTTC) Network: An access network in which fiber is used for part, but not the entire link from the OLT to the end-user. An optical to electrical (O/E) conversion takes place somewhere near the end-user. The terminal network segment of a FTTC network is usually t ...
... • What is FTTC? • Fiber to the Curb (FTTC) Network: An access network in which fiber is used for part, but not the entire link from the OLT to the end-user. An optical to electrical (O/E) conversion takes place somewhere near the end-user. The terminal network segment of a FTTC network is usually t ...
PDF
... Broadcast protocols, of which P5 is a scalable variant, are the only other approach that offer comparable or stronger anonymity guarantees, but even P5 has never been implemented, partly because of the performance limitations and resource consumption of constant broadcast. The Herbivore prototype de ...
... Broadcast protocols, of which P5 is a scalable variant, are the only other approach that offer comparable or stronger anonymity guarantees, but even P5 has never been implemented, partly because of the performance limitations and resource consumption of constant broadcast. The Herbivore prototype de ...
PowerPoint version
... without notifying outside world can change ISP without changing addresses of devices in local network devices inside local net not explicitly addressable, visible by outside world (a security plus). ...
... without notifying outside world can change ISP without changing addresses of devices in local network devices inside local net not explicitly addressable, visible by outside world (a security plus). ...
VoIP Standards for CDMA
... X.S0013-005 IP Multimedia (IM) Subsystem Cx Interface; Signaling flows and message contents (based on TS 29.228) X.S0013-010 IP Multimedia Subsystem (IMS) Sh Interface signaling flows and message contents (based on TS 29.328) X.S0017 Open Service Access (OSA); Application Programming Interface (base ...
... X.S0013-005 IP Multimedia (IM) Subsystem Cx Interface; Signaling flows and message contents (based on TS 29.228) X.S0013-010 IP Multimedia Subsystem (IMS) Sh Interface signaling flows and message contents (based on TS 29.328) X.S0017 Open Service Access (OSA); Application Programming Interface (base ...
R7200 SDSL Routers
... inbound traffic originated from the Internet; preconfigured NetBIOS filters to optimize performance of DSL link. Includes IP & IPX (RIP and SAP) filtering; Filter packets on a per-connection profile basis for source/destination address, service, and protocol. Up to 255 rules in up to 8 filter sets. ...
... inbound traffic originated from the Internet; preconfigured NetBIOS filters to optimize performance of DSL link. Includes IP & IPX (RIP and SAP) filtering; Filter packets on a per-connection profile basis for source/destination address, service, and protocol. Up to 255 rules in up to 8 filter sets. ...
Introduction - Eastern Illinois University
... Which is the official address of a host? c) Does a server host need an IP address? d) Does your home PC need an IP address when you are on the Internet? e) Does a server host need a host name? f) Does your home PC need a host name when you are on the Internet? ...
... Which is the official address of a host? c) Does a server host need an IP address? d) Does your home PC need an IP address when you are on the Internet? e) Does a server host need a host name? f) Does your home PC need a host name when you are on the Internet? ...
network of networks - Department of Computer & Information
... relationship of complex system’s pieces layered reference model for discussion modularization eases maintenance, updating of system change of implementation of layer’s service transparent to rest of system layering is similar to modular design approach of software or hardware systems, added ...
... relationship of complex system’s pieces layered reference model for discussion modularization eases maintenance, updating of system change of implementation of layer’s service transparent to rest of system layering is similar to modular design approach of software or hardware systems, added ...
Mark Hutchinson 212 Wentworth Close S.W. Calgary, Alberta
... Change Management / Version control / Client communication and notification Performance tuning, redundancy / fail over, monitoring, automation, Disaster Recovery Server tuning, High availability, Printing, Plotting, Zeh administration Geological/Geophysical application installation, maintenance, tro ...
... Change Management / Version control / Client communication and notification Performance tuning, redundancy / fail over, monitoring, automation, Disaster Recovery Server tuning, High availability, Printing, Plotting, Zeh administration Geological/Geophysical application installation, maintenance, tro ...
WLI-E – Software User Guide
... TX Rate and RX Rate: displays the current 802.11 data transmission (TX) and data reception (RX) rate while operating in Station mode. Data rates at 1,2,5.5,11Mbps (802.11b) and 6, 9, 12, 18, 24, 36, 48, 54Mbps (802.11a) are possible. Typically, the higher the signal, the higher the data rate and con ...
... TX Rate and RX Rate: displays the current 802.11 data transmission (TX) and data reception (RX) rate while operating in Station mode. Data rates at 1,2,5.5,11Mbps (802.11b) and 6, 9, 12, 18, 24, 36, 48, 54Mbps (802.11a) are possible. Typically, the higher the signal, the higher the data rate and con ...
EC6802- Wireless Networks VIII semester ECE Two marks
... (MSRs) to transport layer communication between mobile hosts and fixed hosts. It uses the standard TCP for its connection over the wireless hop and like other spit connection protocols, attempts to separate loss recovery over the wireless link from the wired link. ...
... (MSRs) to transport layer communication between mobile hosts and fixed hosts. It uses the standard TCP for its connection over the wireless hop and like other spit connection protocols, attempts to separate loss recovery over the wireless link from the wired link. ...
slides
... • Identify the types of traffic that should be served by each layer and dimension it. Ideally, for each type of traffic, we would like to know: ...
... • Identify the types of traffic that should be served by each layer and dimension it. Ideally, for each type of traffic, we would like to know: ...
Fast Channel Change
... upgrades. This enables IPTV operators to attract new subscribers and reduce churn while reaching a larger part of its existing subscriber base with a premium HD quality pay-TV service. As operators increasingly deliver their video services over IP, guaranteeing pay-TV quality is essential. The Edgew ...
... upgrades. This enables IPTV operators to attract new subscribers and reduce churn while reaching a larger part of its existing subscriber base with a premium HD quality pay-TV service. As operators increasingly deliver their video services over IP, guaranteeing pay-TV quality is essential. The Edgew ...
Performance Diagnosis and Improvement in Data Center
... – Important: affects application throughput/delay – Difficult: Involves many parties in large scale ...
... – Important: affects application throughput/delay – Difficult: Involves many parties in large scale ...
Part I: Introduction
... relationship of complex system’s pieces layered reference model for discussion modularization eases maintenance, updating of system change of implementation of layer’s service transparent to rest of system layering is similar to modular design approach of software or hardware systems, added ...
... relationship of complex system’s pieces layered reference model for discussion modularization eases maintenance, updating of system change of implementation of layer’s service transparent to rest of system layering is similar to modular design approach of software or hardware systems, added ...
Security Assessment Questionnaire
... the entire system: how the application components are deployed, communicate or otherwise interact with both the user and server environments. Application scanning tools as well as manual testing with and without application credentials are used to perform this assessment. Typically some host, networ ...
... the entire system: how the application components are deployed, communicate or otherwise interact with both the user and server environments. Application scanning tools as well as manual testing with and without application credentials are used to perform this assessment. Typically some host, networ ...
Chapter 5 Protection of Information Assets
... whereby a user may be more inclined and motivated to select a stronger password • It improves an administrator’s ability to manage users’ accounts and authorizations to all associates systems • It reduces administrative overhead in resetting forgotten passwords over multiple platforms and applicatio ...
... whereby a user may be more inclined and motivated to select a stronger password • It improves an administrator’s ability to manage users’ accounts and authorizations to all associates systems • It reduces administrative overhead in resetting forgotten passwords over multiple platforms and applicatio ...
Load Management and High Availability in the Medusa Distributed
... High availability is an important goal for many Medusa applications. A multi-site deployment can improve the availability of a single-site system because sites can monitor and take over for each other [9, 11]. Wide-area queries, however, are also vulnerable to network failures and more importantly t ...
... High availability is an important goal for many Medusa applications. A multi-site deployment can improve the availability of a single-site system because sites can monitor and take over for each other [9, 11]. Wide-area queries, however, are also vulnerable to network failures and more importantly t ...
How to Build Complex, Large-Scale Emulated Networks Hung Nguyen Matthew Roughan Simon Knight
... networks are needed for a large-scale experiment. However, it is almost as hard to build large-scale, complex networks in emulation as it is in hardware. Emulation removes issues such as the need to physically place interconnecting wires, but still requires configuration of many devices, including r ...
... networks are needed for a large-scale experiment. However, it is almost as hard to build large-scale, complex networks in emulation as it is in hardware. Emulation removes issues such as the need to physically place interconnecting wires, but still requires configuration of many devices, including r ...
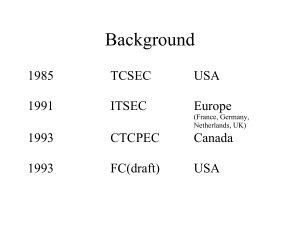
Common Criteria
... DefinitionsTarget of Evaluation (TOE) — An IT product or system and its associated administrator and user guidance documentation that is the subject of an evaluation. ...
... DefinitionsTarget of Evaluation (TOE) — An IT product or system and its associated administrator and user guidance documentation that is the subject of an evaluation. ...
No Slide Title
... Token passing. A unique message type, known as a token, continuously circulates in the system (usually a ring structure). A site that wants to transmit information must wait until the token arrives. When the site completes its round of message passing, it retransmits the token. A token-passing schem ...
... Token passing. A unique message type, known as a token, continuously circulates in the system (usually a ring structure). A site that wants to transmit information must wait until the token arrives. When the site completes its round of message passing, it retransmits the token. A token-passing schem ...