How To Set Up A Wireless Network Using A D-Link
... If you have multiple computers, it allows for all of them to access the internet without having wires all over the place If you have a laptop, you can get full use of its portability Allows computers to share files with each other ...
... If you have multiple computers, it allows for all of them to access the internet without having wires all over the place If you have a laptop, you can get full use of its portability Allows computers to share files with each other ...
Introduction CS 239 Security for Networks and System
... • Some serious, some not – “Serious” defined as attempting to gain ...
... • Some serious, some not – “Serious” defined as attempting to gain ...
CISCO 5
... the IP header is smaller. Transporting these smaller headers requires less overhead. Less overhead means less delay in delivery. This characteristic is desirable for a Layer 3 protocol. The mission of Layer 3 is to transport the packets between the hosts while placing as little burden on the network ...
... the IP header is smaller. Transporting these smaller headers requires less overhead. Less overhead means less delay in delivery. This characteristic is desirable for a Layer 3 protocol. The mission of Layer 3 is to transport the packets between the hosts while placing as little burden on the network ...
tia10e_ch12_pptM - Computer and Information Science
... – Sets and controls protocols for all devices – Internet uses open protocol (TCP/IP) – Modern NOSs support TCP/IP Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall ...
... – Sets and controls protocols for all devices – Internet uses open protocol (TCP/IP) – Modern NOSs support TCP/IP Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall ...
Communication Systems 11th lecture - uni
... Services must be independent from radio access technology and is not limited by the network infrastructure Support of multimedia and all of its components ...
... Services must be independent from radio access technology and is not limited by the network infrastructure Support of multimedia and all of its components ...
Slide 1
... • Future networked media applications will be multi-sourced, highly interactive distributed meshes of HD and 3D multi-sensory channels • Major challenges: – higher quantities of data throughout the network – additional pressure at the network edge for unprecedented upload capacity in wired and wirel ...
... • Future networked media applications will be multi-sourced, highly interactive distributed meshes of HD and 3D multi-sensory channels • Major challenges: – higher quantities of data throughout the network – additional pressure at the network edge for unprecedented upload capacity in wired and wirel ...
Hands-On Ethical Hacking and Network Security
... Both WPA and WPA-2 can run in either mode Pre-Shared Key uses a passphrase the user types into each device Less secure because the user might choose a guessable ...
... Both WPA and WPA-2 can run in either mode Pre-Shared Key uses a passphrase the user types into each device Less secure because the user might choose a guessable ...
PPT Version
... • Link Down, Packets Discarded too scary – Because notifications aren’t authenticated ...
... • Link Down, Packets Discarded too scary – Because notifications aren’t authenticated ...
Technical features - Huawei Enterprise
... Each logical cluster supports up to 128 physical servers, which is the industry best practice. FusionSphere reduces the number of redundant physical servers and is suitable for deploying large-scale service clusters requiring high performance. Each logical cluster supports up to 3,000 VMs, which mak ...
... Each logical cluster supports up to 128 physical servers, which is the industry best practice. FusionSphere reduces the number of redundant physical servers and is suitable for deploying large-scale service clusters requiring high performance. Each logical cluster supports up to 3,000 VMs, which mak ...
E43032231
... Able to meet increasing bandwidth demands from new mobile users and applications. Links in a certain area (e .g.., a hospital) might not be able to use some frequency channel because of spectrums etiquette or regulation[11]. Able to meet increasing bandwidth demands from new mobile users and applica ...
... Able to meet increasing bandwidth demands from new mobile users and applications. Links in a certain area (e .g.., a hospital) might not be able to use some frequency channel because of spectrums etiquette or regulation[11]. Able to meet increasing bandwidth demands from new mobile users and applica ...
Lecture 10 - Lyle School of Engineering
... packet forwarding (label = VPI/VCI fields) → ATM switches do not need changes in forwarding hardware to support MPLS IP+ATM refers to combination of ATM, MPLS, and IP technologies in ATM switches ATM switches do need changes in control plane ...
... packet forwarding (label = VPI/VCI fields) → ATM switches do not need changes in forwarding hardware to support MPLS IP+ATM refers to combination of ATM, MPLS, and IP technologies in ATM switches ATM switches do need changes in control plane ...
On Demand Network-wide VPN Deployment in GPRS
... including the header fields. Hence, AH integrity cannot be met when a NAT device processes a protected packet, and rewrites its IP addresses. As far as IPsec is concerned, the operation of NAT constitutes a violation of its security policy. Moreover, when TCP is involved in ESP protected data transf ...
... including the header fields. Hence, AH integrity cannot be met when a NAT device processes a protected packet, and rewrites its IP addresses. As far as IPsec is concerned, the operation of NAT constitutes a violation of its security policy. Moreover, when TCP is involved in ESP protected data transf ...
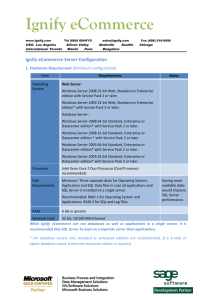
Ignify eCommerce Server Configuration
... Application and SQL Data files in case all applications and SQL Server is installed on a single server. Recommended: RAID 1 for Operating System and Applications. RAID 5 for SQL and Log Files. ...
... Application and SQL Data files in case all applications and SQL Server is installed on a single server. Recommended: RAID 1 for Operating System and Applications. RAID 5 for SQL and Log Files. ...
Document
... chatting between two users is P2P centralized service: client presence detection/location • user registers its IP address with central server when it comes online • user contacts central server to find IP addresses of buddies Network services ...
... chatting between two users is P2P centralized service: client presence detection/location • user registers its IP address with central server when it comes online • user contacts central server to find IP addresses of buddies Network services ...
Assessment of the Internet Protocol Routing in Space—Joint Capability Technology Demonstration
... IPR as a communications network node in space did not exist until IRIS. [Note that some of the IRIS capabilities resemble those of DoD’s Transformational Satellite Communications System (TSAT),3 which was cancelled in 2009; however, TSAT was conceived as a secure global communication system, whereas ...
... IPR as a communications network node in space did not exist until IRIS. [Note that some of the IRIS capabilities resemble those of DoD’s Transformational Satellite Communications System (TSAT),3 which was cancelled in 2009; however, TSAT was conceived as a secure global communication system, whereas ...
Lecture #22
... The client now decrypts the TGS response using the TGS session key. The client now has a session key for use with the new server, and a ticket to use with that server. The client can contact the new server using the same format used to access the TGS. ...
... The client now decrypts the TGS response using the TGS session key. The client now has a session key for use with the new server, and a ticket to use with that server. The client can contact the new server using the same format used to access the TGS. ...
NETWORK MANAGEMENT
... • A user or group of users may be abusing their access privileges and burdening the network at the expense of other users. • Users may be making inefficient use of the network, and the network manager can assist in changing procedures to improve performance. • The network manager is in a better posi ...
... • A user or group of users may be abusing their access privileges and burdening the network at the expense of other users. • Users may be making inefficient use of the network, and the network manager can assist in changing procedures to improve performance. • The network manager is in a better posi ...
Linux+ Guide to Linux Certification
... – Provides authentication security for TCP/IP applications – Used on many UNIX/Linux systems and in MAC OS X ...
... – Provides authentication security for TCP/IP applications – Used on many UNIX/Linux systems and in MAC OS X ...
Guide to Network Defense and Countermeasures
... • TCP and UDP map to the Transport layer and IPv4, IPv6, ICMP, and ICMPv6 map to the Network layer of the OSI model • IP addresses most commonly used on the Internet conform to IPv4 • You must understand the normal configuration of fields in IP, TCP, and UDP headers to recognize and filter unwanted ...
... • TCP and UDP map to the Transport layer and IPv4, IPv6, ICMP, and ICMPv6 map to the Network layer of the OSI model • IP addresses most commonly used on the Internet conform to IPv4 • You must understand the normal configuration of fields in IP, TCP, and UDP headers to recognize and filter unwanted ...
answer-sheet-031_heather-mclellan_isf-7765
... 2.4GHz. This standard can be interfered from microwaves, ovens, cordless phones and other applications using the same GHz. 802.11a- IEEE created a second extension to the original 802.11. 802.11a supports bandwidth up to 54mbps and signals in the frequency of around 5GHz however the higher frequency ...
... 2.4GHz. This standard can be interfered from microwaves, ovens, cordless phones and other applications using the same GHz. 802.11a- IEEE created a second extension to the original 802.11. 802.11a supports bandwidth up to 54mbps and signals in the frequency of around 5GHz however the higher frequency ...
The Internet and Its Uses
... –As individuals, businesses, and organizations have developed their own IP networks that link to the Internet. ...
... –As individuals, businesses, and organizations have developed their own IP networks that link to the Internet. ...
product catalog 02-17 v1 - SM
... Very often telecommunication network become layered as time goes by and managing many different, aging technologies can be challenging. SM Optics supports all phases of customer’s network lifecycle with its services: leveraging its deep understanding of transmission technology and a vast experience ...
... Very often telecommunication network become layered as time goes by and managing many different, aging technologies can be challenging. SM Optics supports all phases of customer’s network lifecycle with its services: leveraging its deep understanding of transmission technology and a vast experience ...
Overview of Nomadix` RADIUS Implementation Solution Outline
... Most network operators consider it important to implement short idle timeouts to improve network efficiency. Idle-timeouts can be effectively used to ensure accurate billing for users that either turn off their laptop or lose network access for any other reason (e.g. AP becomes inoperable). Alternat ...
... Most network operators consider it important to implement short idle timeouts to improve network efficiency. Idle-timeouts can be effectively used to ensure accurate billing for users that either turn off their laptop or lose network access for any other reason (e.g. AP becomes inoperable). Alternat ...