session4 - WordPress.com
... network can act both as clients and servers. For instance, many Microsoft Windows based computers will allow file and print sharing. Many networks are combination of peer-to-peer and server based networks. • The network operating system uses a network data protocol to communicate on the network to o ...
... network can act both as clients and servers. For instance, many Microsoft Windows based computers will allow file and print sharing. Many networks are combination of peer-to-peer and server based networks. • The network operating system uses a network data protocol to communicate on the network to o ...
Introduction to Queuing Networks MATH 35800/M5800 Problem Sheet 5 Autumn 2014
... (b) Use the trafic equations to find the effective arrival rates λ1 , λ2 and λ3 , and determine whether or not the network is stable. (c) Denote the state of the network by n = (n1 , n2 , . . . , nJ ) where nj is the number of customers in Qj , j = 1, . . . , J, and let X(t) denote the corresponding ...
... (b) Use the trafic equations to find the effective arrival rates λ1 , λ2 and λ3 , and determine whether or not the network is stable. (c) Denote the state of the network by n = (n1 , n2 , . . . , nJ ) where nj is the number of customers in Qj , j = 1, . . . , J, and let X(t) denote the corresponding ...
Designing a future Internet: Architecture and requirements
... Better tools for abstracting the manager’s job. ...
... Better tools for abstracting the manager’s job. ...
Boolean network (BN) has been a powerful tool for system biology
... neural network, social network, multiagent systems, and so on. These applications are based on the identification of the BNs. But it is difficult to identify the BNs directly due to the lack of tools for the logical system. ...
... neural network, social network, multiagent systems, and so on. These applications are based on the identification of the BNs. But it is difficult to identify the BNs directly due to the lack of tools for the logical system. ...
University of California at Berkeley CS168, Homework 2
... treerouters (or a shortest pathpackets tree, if all link costs are identical). By constructing a counterexample, show that the least-cost path tree is not always the same as a CIDR enables more efficient use of the IP address space minimum spanning tree ...
... treerouters (or a shortest pathpackets tree, if all link costs are identical). By constructing a counterexample, show that the least-cost path tree is not always the same as a CIDR enables more efficient use of the IP address space minimum spanning tree ...
6.2 Networks (AQA)
... This defines where a host computer is on the Internet Public (routable) or private (non-routable) addresses Internet Assigned Numbers Authority (IANA) responsible for IP addressing systems Two versions of IP addresses IPv4 most commonly used 32 bit e.g. 192.168.0.0 IPv6 128 bit numbers ISPs assign I ...
... This defines where a host computer is on the Internet Public (routable) or private (non-routable) addresses Internet Assigned Numbers Authority (IANA) responsible for IP addressing systems Two versions of IP addresses IPv4 most commonly used 32 bit e.g. 192.168.0.0 IPv6 128 bit numbers ISPs assign I ...
PDF
... advantages like scalability, flexibility, robustness, self configuration and self healing, etc. we must not forget it is a resource constrain network with limited bandwidth, energy and power supply and most importantly limited buffer space. Most probably reactive routing protocols are used for trans ...
... advantages like scalability, flexibility, robustness, self configuration and self healing, etc. we must not forget it is a resource constrain network with limited bandwidth, energy and power supply and most importantly limited buffer space. Most probably reactive routing protocols are used for trans ...
arp
... Find routing table entry matching destination IP address (128.243.22.35) gateway (if any) and interface ...
... Find routing table entry matching destination IP address (128.243.22.35) gateway (if any) and interface ...
chapter 10 - University of Windsor
... Operate IPSec only between the network boundary and the remote host or network. However, this requires a NAT box, that must establish its own security associations, and will not work satisfactory in a nested NAT environment in which the “outer” NAT is not controlled or trusted by the owner of the ...
... Operate IPSec only between the network boundary and the remote host or network. However, this requires a NAT box, that must establish its own security associations, and will not work satisfactory in a nested NAT environment in which the “outer” NAT is not controlled or trusted by the owner of the ...
K-1A Final exam study Guide * In relationship to the OSI layer model
... – When a router has only one other router to which it is connected. This condition is known as a stub router. S* 0.0.0.0/0 is directly connected, Serial0/0/0 – When no other routes in the routing table match the packet's destination IP address. A common use is when connecting a company's edge rout ...
... – When a router has only one other router to which it is connected. This condition is known as a stub router. S* 0.0.0.0/0 is directly connected, Serial0/0/0 – When no other routes in the routing table match the packet's destination IP address. A common use is when connecting a company's edge rout ...
dc9798.PDF
... Discuss the ISO 7-layered model and show how different network types, such as Ethernet, Token Ring and FDDI, fit with networking protocols, such as SPX/IPX, TCP/IP, and NetBEUI. Give some examples of practical networks and the protocols that they use. ...
... Discuss the ISO 7-layered model and show how different network types, such as Ethernet, Token Ring and FDDI, fit with networking protocols, such as SPX/IPX, TCP/IP, and NetBEUI. Give some examples of practical networks and the protocols that they use. ...
TCP/IP Concepts (Part 1)
... Destination port (16 bits) – a number that identifies the Application layer program the message is destined to. Sequence number (32 bits) – Tracks packets received. Helps reassemble packets. Hackers may guest SN to hijack conversations. Has a dual role If the SYN flag is set, then this is the ini ...
... Destination port (16 bits) – a number that identifies the Application layer program the message is destined to. Sequence number (32 bits) – Tracks packets received. Helps reassemble packets. Hackers may guest SN to hijack conversations. Has a dual role If the SYN flag is set, then this is the ini ...
General Overview of Attacks
... There are other sources of data such as real-time process lists, log files, processor loads etc. However, they are used rarely. ...
... There are other sources of data such as real-time process lists, log files, processor loads etc. However, they are used rarely. ...
Test Bank for Crypto..
... 8. The OSI security architecture was not developed as an international standard, therefore causing an obstacle for computer and communication vendors when developing security features. ...
... 8. The OSI security architecture was not developed as an international standard, therefore causing an obstacle for computer and communication vendors when developing security features. ...
Slide 1
... ESPOO, Finland & SANTA CLARA, Calif.--(BUSINESS WIRE)--June 10, 2005-Nokia and Intel Corporation today announced a cooperation to accelerate the development, adoption and deployment of WiMAX technology, helping to bring new capabilities and data services to mobile users over high-speed broadband net ...
... ESPOO, Finland & SANTA CLARA, Calif.--(BUSINESS WIRE)--June 10, 2005-Nokia and Intel Corporation today announced a cooperation to accelerate the development, adoption and deployment of WiMAX technology, helping to bring new capabilities and data services to mobile users over high-speed broadband net ...
Wireless Networks (continued)
... two nearest nodes so that the entire network forms a circle Data is transmitted clockwise, in one direction (unidirectional), around the ring The fact that all workstations participate in delivery makes the ring topology an active topology A ring topology also differs in that it has no “ends” and da ...
... two nearest nodes so that the entire network forms a circle Data is transmitted clockwise, in one direction (unidirectional), around the ring The fact that all workstations participate in delivery makes the ring topology an active topology A ring topology also differs in that it has no “ends” and da ...
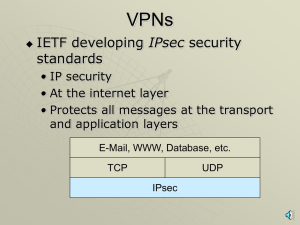
VPNs, PKIs, ISSs, SSLs with narration
... Another Security System for VPNs is the Point-to-Point Tunneling Protocol (PPTP) ...
... Another Security System for VPNs is the Point-to-Point Tunneling Protocol (PPTP) ...
PowerPoint Presentation - Lead
... – Use words or phrases that are easy for you to remember, but difficult for others to guess. ...
... – Use words or phrases that are easy for you to remember, but difficult for others to guess. ...