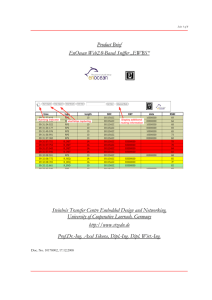
Classful IP Addresses
... • An IPv4 address is an address of the Internet Protocol Version 4. When the version is understood from the context we only say “IP address” • On the public Internet, an IP address is unique global address of a network interface • The IP address is used by hosts and routers for delivery of IP ...
... • An IPv4 address is an address of the Internet Protocol Version 4. When the version is understood from the context we only say “IP address” • On the public Internet, an IP address is unique global address of a network interface • The IP address is used by hosts and routers for delivery of IP ...
Cutting Edge VoIP Security Issues Color
... DHCP, DNS, TFTP, etc. DHCP exhaustion is an example, where a hacker uses up all the IP addresses, denying service to VoIP phones DNS cache poisoning involves tricking a DNS server into using a fake DNS response ...
... DHCP, DNS, TFTP, etc. DHCP exhaustion is an example, where a hacker uses up all the IP addresses, denying service to VoIP phones DNS cache poisoning involves tricking a DNS server into using a fake DNS response ...
TCP/IP Management
... TCP/IP Route Information • The Route Information detail display is valuable for determining whether a route exists in the AS/400 routing table. • For instance, PING is unsuccessful , you can examine the routing table to determine whether a route exists to the remote system .If the route is availabl ...
... TCP/IP Route Information • The Route Information detail display is valuable for determining whether a route exists in the AS/400 routing table. • For instance, PING is unsuccessful , you can examine the routing table to determine whether a route exists to the remote system .If the route is availabl ...
Designation of Network Resources
... to GTC as soon as reasonably practicable. The Network Customer shall promptly provide such notice for any resource it no longer owns or purchases under a non-interruptible contract. 28.4 Operation of Network Resources: The Network Customer shall not operate its designated Network Resources located i ...
... to GTC as soon as reasonably practicable. The Network Customer shall promptly provide such notice for any resource it no longer owns or purchases under a non-interruptible contract. 28.4 Operation of Network Resources: The Network Customer shall not operate its designated Network Resources located i ...
lecture01-introduction-and-logistics
... – then forward remaining bits directly – reduced latency, but may forward “bad” packets (why?) ...
... – then forward remaining bits directly – reduced latency, but may forward “bad” packets (why?) ...
Presentación de PowerPoint
... ARP spoofing is used to stage a MitM attack, where the attacker positions himself between the server and the victim to steal his private information ...
... ARP spoofing is used to stage a MitM attack, where the attacker positions himself between the server and the victim to steal his private information ...
09/24/04
... – Cannot expand network through daisy-chaining – Failure of the backbone cable is catastrophic – Failure of any single node is also catastrophic – No centralized management ...
... – Cannot expand network through daisy-chaining – Failure of the backbone cable is catastrophic – Failure of any single node is also catastrophic – No centralized management ...
MPV2
... produces output, then these two services can produce a very high number of packets UDP Packet Storm – By connecting a host's chargen service to the echo service on the same or another machine, all affected machines may be effectively taken out of service because of the excessively high number of pac ...
... produces output, then these two services can produce a very high number of packets UDP Packet Storm – By connecting a host's chargen service to the echo service on the same or another machine, all affected machines may be effectively taken out of service because of the excessively high number of pac ...
1 | I.C.T.C. “International Computer Training Center” www.ictc.gr info
... This class will immerse the student into an interactive environment where they will be shown how to scan, test, hack and secure their own systems. Students then learn how intruders escalate privileges and what steps can be taken to secure a system. Who Should Attend This course will significantly be ...
... This class will immerse the student into an interactive environment where they will be shown how to scan, test, hack and secure their own systems. Students then learn how intruders escalate privileges and what steps can be taken to secure a system. Who Should Attend This course will significantly be ...
A Virtual Honeypot Framework
... Personality Engine • Virtual Honeypots Personality: – The network stack behavior of a given operating system ...
... Personality Engine • Virtual Honeypots Personality: – The network stack behavior of a given operating system ...
Go back
... Internet or some other transmission system not accessible to the general public, but managed by more than one company's administrator(s). For example, military networks of different security levels may map onto a common military radio transmission system that never connects to the Internet. Similar ...
... Internet or some other transmission system not accessible to the general public, but managed by more than one company's administrator(s). For example, military networks of different security levels may map onto a common military radio transmission system that never connects to the Internet. Similar ...
Local Area Networks, 3rd Edition David A. Stamper
... (cont.) • An alarm can be an audio signal, a flashing light, a call to a pager, a FAX message, or a message to a remote system. An alert is less obvious than an alarm. An alert may indicate potential problems by using colors on a color monitor. • The report generator allows network administrators to ...
... (cont.) • An alarm can be an audio signal, a flashing light, a call to a pager, a FAX message, or a message to a remote system. An alert is less obvious than an alarm. An alert may indicate potential problems by using colors on a color monitor. • The report generator allows network administrators to ...
An Examination of Remote Access Help Desk Cases
... • Each Node: – Has (potentially) verifiable configuration parameters – Can be modeled as an agent ...
... • Each Node: – Has (potentially) verifiable configuration parameters – Can be modeled as an agent ...
Quick Tip: How to Use Real- Time Interface Statistics for Faster
... Troubleshooting network errors can be time-consuming without the right monitoring and diagnostic tools. Most network management systems poll device interface statistics via SNMP, which provides details on the amount of your link that is utilized, bytes transmitted, percent of utilization, etc. Netw ...
... Troubleshooting network errors can be time-consuming without the right monitoring and diagnostic tools. Most network management systems poll device interface statistics via SNMP, which provides details on the amount of your link that is utilized, bytes transmitted, percent of utilization, etc. Netw ...
15. - 건국대학교
... 16.1 Quality of Multimedia Data Transmission Quality of Service (QoS) depends on many parameters Data rate: a measure of transmission speed. Latency (maximum frame/packet delay): maximum time needed from transmission to reception. Packet loss or error rate: a measure (in percentage) of erro ...
... 16.1 Quality of Multimedia Data Transmission Quality of Service (QoS) depends on many parameters Data rate: a measure of transmission speed. Latency (maximum frame/packet delay): maximum time needed from transmission to reception. Packet loss or error rate: a measure (in percentage) of erro ...
The HOPI Testbed and the new Internet2 Network
... • Also, access to additional infrastructure has given rise to the “hybrid networking” idea - meaning operating networks at multiple layers in a coherent way • Three years ago, Internet2 created the Hybrid Optical and Packet Infrastructure (HOPI) project to examine this ...
... • Also, access to additional infrastructure has given rise to the “hybrid networking” idea - meaning operating networks at multiple layers in a coherent way • Three years ago, Internet2 created the Hybrid Optical and Packet Infrastructure (HOPI) project to examine this ...
technical summary 2011
... Business case for WSN 802.11p: New standard for wireless vehicular transmission WSN and power consumption: new techniques Diffusion of mobile technologies (1G, 2G, 3G,..) WSN technologies are ready for several applications : ehealth, geographical, etc… Vehicular applications fo 802.11p have been stu ...
... Business case for WSN 802.11p: New standard for wireless vehicular transmission WSN and power consumption: new techniques Diffusion of mobile technologies (1G, 2G, 3G,..) WSN technologies are ready for several applications : ehealth, geographical, etc… Vehicular applications fo 802.11p have been stu ...
Types of networks based on physical scope Local area network
... capabilities. STC provides national and international MPLS network connectivity for clients in Saudi Arabia as well as in foreign countries. STC MPLS Network:~ STC MPLS offers varying levels of access to STC’s MPLS network which has the capability to deliver voice, data and video traffic using QoS/C ...
... capabilities. STC provides national and international MPLS network connectivity for clients in Saudi Arabia as well as in foreign countries. STC MPLS Network:~ STC MPLS offers varying levels of access to STC’s MPLS network which has the capability to deliver voice, data and video traffic using QoS/C ...
Understanding How Networks Communicate
... • Must understand specialized networking vocabulary, including • Server — shares resources across network, typically with more central processing unit (CPU) power and storage capacity than other computers • Client — accesses shared resources • Request-response — client requests information; server r ...
... • Must understand specialized networking vocabulary, including • Server — shares resources across network, typically with more central processing unit (CPU) power and storage capacity than other computers • Client — accesses shared resources • Request-response — client requests information; server r ...
Addressing: IPv4, IPv6, and Beyond
... Payload Length (16 bits) – length of data, slightly different from total length Next Header (8 bits) – type of the next header, new idea Hop Limit (8 bits) – was time-to-live, renamed Source address (128 bits) Destination address (128 bits) ...
... Payload Length (16 bits) – length of data, slightly different from total length Next Header (8 bits) – type of the next header, new idea Hop Limit (8 bits) – was time-to-live, renamed Source address (128 bits) Destination address (128 bits) ...