Reliable network solutions enabling Smart Grid Applications
... 100% QoS and constant delay ensures full WAMPAC. QoS and multicasting enables SCADA, WAM and video surveillance ...
... 100% QoS and constant delay ensures full WAMPAC. QoS and multicasting enables SCADA, WAM and video surveillance ...
A Robust and Adaptive Communication System for Intelligent
... Packet Delay: transmission delay + deterministic queuing delay ...
... Packet Delay: transmission delay + deterministic queuing delay ...
Name
... unique IP address. This address is referred to as its host address. TCP/IP is the most widely used protocol in the world. The Internet or World Wide Web only uses IP addressing. In order for a host to access the Internet, it must have an IP address. In its basic form, the IP address has two parts: ...
... unique IP address. This address is referred to as its host address. TCP/IP is the most widely used protocol in the world. The Internet or World Wide Web only uses IP addressing. In order for a host to access the Internet, it must have an IP address. In its basic form, the IP address has two parts: ...
SAQ D Compliance Scott St. Aubin Senior Security Consultant QSA, CISM, CISSP
... • Apply critical patches within one month of release • Process to identify newly discovered vulnerabilities AND update configuration standards • Change control process – Document impact – Management sign-off – Testing of operational funcationality – Back-out procedures ...
... • Apply critical patches within one month of release • Process to identify newly discovered vulnerabilities AND update configuration standards • Change control process – Document impact – Management sign-off – Testing of operational funcationality – Back-out procedures ...
Module 2: Assigning IP Addresses in a Multiple Subnet
... Routes packets to other networks Is used when the internal routing table on the host has no information on the destination subnet DHCP automatically delivers the IP address for the default gateway to the client To configure the client manually for the default gateway, use the General tab on the ...
... Routes packets to other networks Is used when the internal routing table on the host has no information on the destination subnet DHCP automatically delivers the IP address for the default gateway to the client To configure the client manually for the default gateway, use the General tab on the ...
ch3_OSI_2
... Figure 2.21 shows two computers communicating via the Internet. The sending computer is running three processes at this time with port addresses a, b, and c. The receiving computer is running two processes at this time with port addresses j and k. Process a in the sending computer needs to communica ...
... Figure 2.21 shows two computers communicating via the Internet. The sending computer is running three processes at this time with port addresses a, b, and c. The receiving computer is running two processes at this time with port addresses j and k. Process a in the sending computer needs to communica ...
CS412 Introduction to Computer Networking & Telecommunication
... distance: infinity best known path: unknown ...
... distance: infinity best known path: unknown ...
P7780
... concepts rarely change, these skills alone are insufficient to protect computer networks. As crackers hacked away at networks and systems, courses arose that emphasized the latest attacks. Currently, many educators believe that to train people to secure networks, they must also learn to think like a ...
... concepts rarely change, these skills alone are insufficient to protect computer networks. As crackers hacked away at networks and systems, courses arose that emphasized the latest attacks. Currently, many educators believe that to train people to secure networks, they must also learn to think like a ...
Router
... IP address different depending on who asks for it Address may be changed in the network IP address may not be reachable (even though destination is up and attached) ...
... IP address different depending on who asks for it Address may be changed in the network IP address may not be reachable (even though destination is up and attached) ...
Chapter. 01
... link, or the disabling of the file management system. DOS - Denial of Service Attacks have ...
... link, or the disabling of the file management system. DOS - Denial of Service Attacks have ...
Chapter 6 slides, Computer Networking, 3rd edition
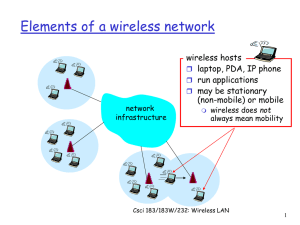
... to get packet from wireless host A to B may need to route through wireless hosts X,Y,Z Applications: “laptop” meeting in conference room, car interconnection of “personal” devices battlefield ...
... to get packet from wireless host A to B may need to route through wireless hosts X,Y,Z Applications: “laptop” meeting in conference room, car interconnection of “personal” devices battlefield ...
INTERNET
... network (ARPANet) created by the US military back in the 1960s. Over the years, as more and more computers and networks have connected to this network, it has grown into the Internet that we know. ...
... network (ARPANet) created by the US military back in the 1960s. Over the years, as more and more computers and networks have connected to this network, it has grown into the Internet that we know. ...
AirRouter User Guide
... the wireless mode, the basic wireless settings and the wireless security settings for the AirRouter. • Network The Network tab covers the configuration of the network operating mode, IP settings, packet filtering routines and network services. • Advanced The Advanced tab settings are available f ...
... the wireless mode, the basic wireless settings and the wireless security settings for the AirRouter. • Network The Network tab covers the configuration of the network operating mode, IP settings, packet filtering routines and network services. • Advanced The Advanced tab settings are available f ...
Interconnection networks 2, clusters
... • Cut-through routing or wormhole routing: switch examines the header, decides where to send the message, and then starts forwarding it immediately – In wormhole routing, when head of message is blocked, message stays strung out over the network, potentially blocking other messages (needs only buffe ...
... • Cut-through routing or wormhole routing: switch examines the header, decides where to send the message, and then starts forwarding it immediately – In wormhole routing, when head of message is blocked, message stays strung out over the network, potentially blocking other messages (needs only buffe ...
2.1 Chapter 2 Network Models
... processes at this time with port addresses a, b, and c. The receiving computer is running two processes at this time with port addresses j and k. Process a in the sending computer needs to communicate with process j in the receiving computer. Note that although physical addresses change from hop to ...
... processes at this time with port addresses a, b, and c. The receiving computer is running two processes at this time with port addresses j and k. Process a in the sending computer needs to communicate with process j in the receiving computer. Note that although physical addresses change from hop to ...
Network Models
... processes at this time with port addresses a, b, and c. The receiving computer is running two processes at this time with port addresses j and k. Process a in the sending computer needs to communicate with process j in the receiving computer. Note that although physical addresses change from hop to ...
... processes at this time with port addresses a, b, and c. The receiving computer is running two processes at this time with port addresses j and k. Process a in the sending computer needs to communicate with process j in the receiving computer. Note that although physical addresses change from hop to ...
Windows Server 2012 R2: Networking
... Multi-tenant VPN gateway in Windows Server 2012 R2 Integral multitenant edge gateway for seamless connectivity Guest clustering for high availability BGP for dynamic routes update Encaps/Decaps NVGRE packets Multitenant aware NAT for Internet access ...
... Multi-tenant VPN gateway in Windows Server 2012 R2 Integral multitenant edge gateway for seamless connectivity Guest clustering for high availability BGP for dynamic routes update Encaps/Decaps NVGRE packets Multitenant aware NAT for Internet access ...
Document
... processes at this time with port addresses a, b, and c. The receiving computer is running two processes at this time with port addresses j and k. Process a in the sending computer needs to communicate with process j in the receiving computer. Note that although physical addresses change from hop to ...
... processes at this time with port addresses a, b, and c. The receiving computer is running two processes at this time with port addresses j and k. Process a in the sending computer needs to communicate with process j in the receiving computer. Note that although physical addresses change from hop to ...
Networks
... packet-switching: with 35 ongoing calls, probability that 10 or more callers simultaneously active < 0.0004! ...
... packet-switching: with 35 ongoing calls, probability that 10 or more callers simultaneously active < 0.0004! ...
DumpsReview
... properly. How should you fix the problem? A. Configure the NAT to use dynamic DNS. B. Configure the NAT to route the 64.124.0.0/16 network to the Internet. C. Reconfigure the internal network to use an accepted private network address. D. Add a static route from the 64.124.0.0/16 network to the Syma ...
... properly. How should you fix the problem? A. Configure the NAT to use dynamic DNS. B. Configure the NAT to route the 64.124.0.0/16 network to the Internet. C. Reconfigure the internal network to use an accepted private network address. D. Add a static route from the 64.124.0.0/16 network to the Syma ...