DiBos Digital Video Recorders
... attached network camera or network video server. Users can connect up to 32 additional network video/audio sources. As many as 10 audio streams can be recorded on a 30-video channel unit, and every network video server can add one audio channel. ...
... attached network camera or network video server. Users can connect up to 32 additional network video/audio sources. As many as 10 audio streams can be recorded on a 30-video channel unit, and every network video server can add one audio channel. ...
here - Help Net Security
... Accurate assessment through hacker-like activities to closely assess the security status of a system. ...
... Accurate assessment through hacker-like activities to closely assess the security status of a system. ...
6 - Kuroski
... Commonly consists of two or more internal bastion hosts behind packet filtering router, with each host protecting trusted network: Connections from outside (untrusted network) routed through external filtering router Connections from outside (untrusted network) are routed into and out of routi ...
... Commonly consists of two or more internal bastion hosts behind packet filtering router, with each host protecting trusted network: Connections from outside (untrusted network) routed through external filtering router Connections from outside (untrusted network) are routed into and out of routi ...
SEMESTER 1 Chapter 5
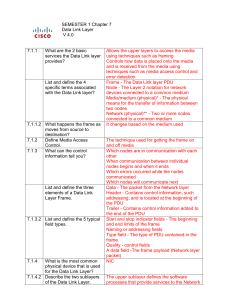
... - the size of the network – - the number of hosts - the geographic scope - the services to be provided over the network. * The Data Link layer provides a means for exchanging data over a common local media. The Data Link layer performs two basic services: – Allows the upper layers to access the me ...
... - the size of the network – - the number of hosts - the geographic scope - the services to be provided over the network. * The Data Link layer provides a means for exchanging data over a common local media. The Data Link layer performs two basic services: – Allows the upper layers to access the me ...
RFPWoodgroveBankJBHickmanmODFQ03
... subdivided into child zones and site administrators will be delegated their part of the domain name space (Microsoft TechNet). Multiple DNS servers at each site will provide redundancy in case a server fails. Wireless At each site there will be two wireless networks using an infrastructure topology. ...
... subdivided into child zones and site administrators will be delegated their part of the domain name space (Microsoft TechNet). Multiple DNS servers at each site will provide redundancy in case a server fails. Wireless At each site there will be two wireless networks using an infrastructure topology. ...
Chapter 1: Foundation
... Point-to-point: direct link between two nodes Multiple access: multiple nodes share the same link ...
... Point-to-point: direct link between two nodes Multiple access: multiple nodes share the same link ...
Chapter 2 Packet Switched Networks
... were reluctant to switch over to other LAN technologies when they came on the scene. Second, token ring, FDDI and ATM are more complex and expensive than Ethernet, which further discouraged network administrators from switching over. Third, the most compelling reason to switch to another LAN technol ...
... were reluctant to switch over to other LAN technologies when they came on the scene. Second, token ring, FDDI and ATM are more complex and expensive than Ethernet, which further discouraged network administrators from switching over. Third, the most compelling reason to switch to another LAN technol ...
No Slide Title
... Department of Computer Engineering, Kasetsart University 204421 Computer Networks ...
... Department of Computer Engineering, Kasetsart University 204421 Computer Networks ...
A Security Primer and Overview of Network Security Protocols
... System security, Biometrics, Application-specific security ...
... System security, Biometrics, Application-specific security ...
Containment of Fast Scanning Computer Network Worms
... the host is considered to be infected. Mahoney and Chan [14] developed the Packet Header Anomaly Detection (PHAD) technique, which learns the normal ranges of values for each datagram header field at the data link (Ethernet), network (IP), and transport/control layers (TCP, UDP, ICMP). PHAD uses the ...
... the host is considered to be infected. Mahoney and Chan [14] developed the Packet Header Anomaly Detection (PHAD) technique, which learns the normal ranges of values for each datagram header field at the data link (Ethernet), network (IP), and transport/control layers (TCP, UDP, ICMP). PHAD uses the ...
BF-450(M)/BF-430/431
... DHCP server, which means it can get IP address, an IP default gateway and DNS server. ► PPPoE Over Ethernet PPPoE is a protocol for connecting remote hosts to the Internet over DSL connection by simulating dial-up connection. ► Dynamic DNS With dynamic DNS support, you can have a static hostname ali ...
... DHCP server, which means it can get IP address, an IP default gateway and DNS server. ► PPPoE Over Ethernet PPPoE is a protocol for connecting remote hosts to the Internet over DSL connection by simulating dial-up connection. ► Dynamic DNS With dynamic DNS support, you can have a static hostname ali ...
Power Consumption and Conservation in WiFi Based Phones: A
... As discussed in section III, power save mode or doze state is the most effective way to save power. It is thus desirable that the VoWiFi phone stays in this state as long as possible without degradation in its functionality and quality of service. The time spent in doze state can be increased by min ...
... As discussed in section III, power save mode or doze state is the most effective way to save power. It is thus desirable that the VoWiFi phone stays in this state as long as possible without degradation in its functionality and quality of service. The time spent in doze state can be increased by min ...
Chapter 1
... • Binds an IP address to a MAC address. • Devices, (hosts, routers, servers, etc.) use IP addresses to reach other devices within their own network/subnet or across different networks/subnets. • The Layer 3 IP addresses in the packet consist of both the original source and the final destination addr ...
... • Binds an IP address to a MAC address. • Devices, (hosts, routers, servers, etc.) use IP addresses to reach other devices within their own network/subnet or across different networks/subnets. • The Layer 3 IP addresses in the packet consist of both the original source and the final destination addr ...
Introducing Wireless LANs
... Mesh networking employs a new protocol, Adaptive Wireless Path Protocol (AWP) to form and maintain the mesh. BCMSN 6 – 1 & 2 ...
... Mesh networking employs a new protocol, Adaptive Wireless Path Protocol (AWP) to form and maintain the mesh. BCMSN 6 – 1 & 2 ...
Network Layer Data Plane - CSE Labs User Home Pages
... • Fabric slower than input ports combined -> queueing may occur at input queues – queueing delay and loss due to input buffer overflow! ...
... • Fabric slower than input ports combined -> queueing may occur at input queues – queueing delay and loss due to input buffer overflow! ...
Bruno Nowak ICT 2006 11 10 - Docbox
... Designed to user needs; not profit based Extensive planning Additional capability beyond traditional network coverage “…I think the most salient point [of having your own system] is the ability to maintain a service level without a profit motive” Steve Jennings, CIO Harris County, TX ICT Worksh ...
... Designed to user needs; not profit based Extensive planning Additional capability beyond traditional network coverage “…I think the most salient point [of having your own system] is the ability to maintain a service level without a profit motive” Steve Jennings, CIO Harris County, TX ICT Worksh ...
Troubleshooting Networking Problems
... there is network activity from certain outlets when the lights flash. The numbers on the switch refer to switch ports, not outlet ports! ...
... there is network activity from certain outlets when the lights flash. The numbers on the switch refer to switch ports, not outlet ports! ...
Networking Topologies - Edupedia Publications
... intended recipient actually accepts and processes the message. Ethernet bus topologies are relatively easy to install and don't require much cabling compared to the alternatives. 10Base-2 ("Thin Net") and 10Base-5 ("Thick Net") both were popular Ethernet cabling options many years ago for bus topolo ...
... intended recipient actually accepts and processes the message. Ethernet bus topologies are relatively easy to install and don't require much cabling compared to the alternatives. 10Base-2 ("Thin Net") and 10Base-5 ("Thick Net") both were popular Ethernet cabling options many years ago for bus topolo ...
$doc.title
... – E.g., if client has not already started playing data – Data can be retransmiHed within $me constraint ...
... – E.g., if client has not already started playing data – Data can be retransmiHed within $me constraint ...
Import Settings:
... routing algorithms to decipher which route to send data packets. In packet-switched networks, a distance-vector routing protocol uses the Bellman-Ford algorithm to calculate where and how data will be transmitted. 2. What routing protocol is the most popular link-state protocol used within a large o ...
... routing algorithms to decipher which route to send data packets. In packet-switched networks, a distance-vector routing protocol uses the Bellman-Ford algorithm to calculate where and how data will be transmitted. 2. What routing protocol is the most popular link-state protocol used within a large o ...
3 What is the Internet?
... • The files of the user are shown on the browser • Files can be uploaded to or retrieved from the server by ...
... • The files of the user are shown on the browser • Files can be uploaded to or retrieved from the server by ...
ppt - Computer Science & Engineering
... each local iteration caused by: local link cost change DV update message from neighbor ...
... each local iteration caused by: local link cost change DV update message from neighbor ...